Palantir and money laundering
Together with Edison, we continue to investigate the capabilities of the Palantir system.
Palantir -
[ Content removed on Wikipedia request ]
')
There is a video on the official Palantir channel demonstrating the work of an analyst using the Palantir system during a money laundering investigation. In my opinion, somehow, the founding fathers of information technology, Vanivar Bush (“As We May Think”) , Douglas Engelbart (“The Mother of All Demos”) and Joseph Liclader (“Intergalactic computer network” and “ The symbiosis of man and computer ") , about which I wrote a little earlier.
(For help with the translation, thanks to Vorsin Alexey)

0:10 This video demonstrates how Palantir can be used to track money laundering and other financial crimes.
0:15 Palantir is already being used in law enforcement and financial institutions to help analysts find important in a huge data stream.
At the bottom of the screen is the inscription: “All the data used in this video is imaginary or randomly generated. All coincidences with real people, organizations, or investigations are random. ”
0:25 This video will demonstrate a typical analyst workflow.
0:30 We received information that these ten bills receive illegal and laundered money.

0:35 We see that all accounts have similar names and are open in the same bank.
0:40 They belong to subsidiaries of Sunset Systems.
0:43 Using Palantir, we can understand the nature of this money laundering scheme.

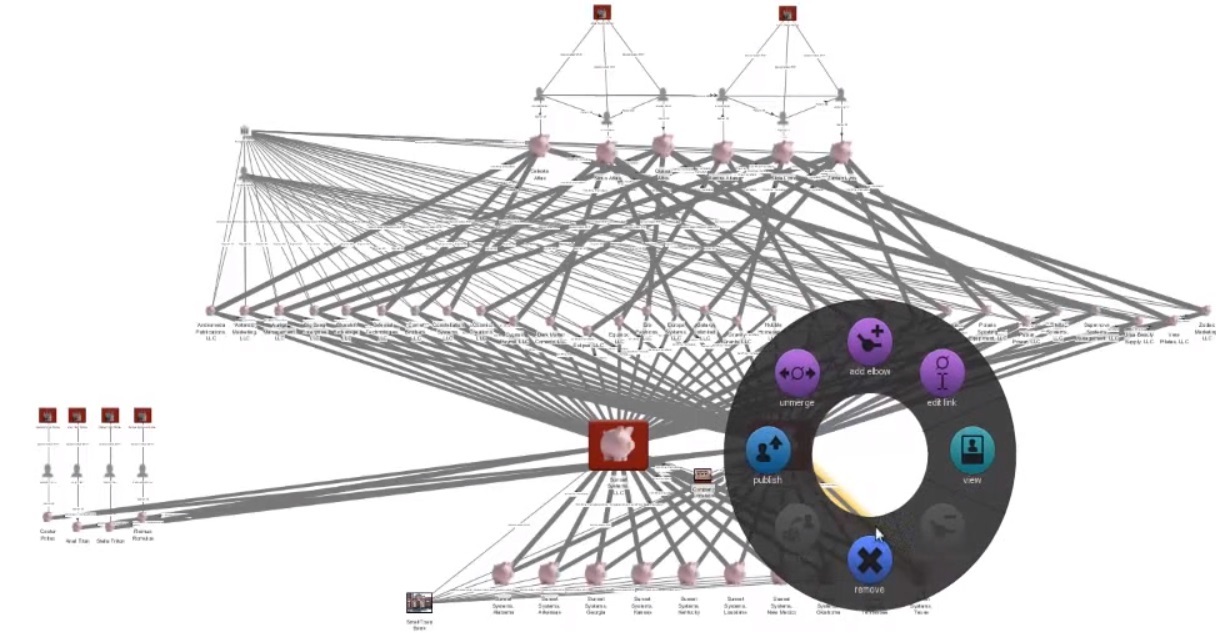
0:49 If we “look around” (we use the “Search around” tool) for the account-related transactions, we will see that they are associated with two new accounts: “Sunset Systems LLC” and “Twilight Technologies LLC”.

0:57 We can analyze each of the resulting groups of links separately, but to understand the big picture, we use the “flows” tool (flows).

01:06 As expected, we see cash flows from ten accounts from which we started to two current accounts.
01:13 The “Flows” assistant allows comparing cash flows. The more circles, the greater the flow.

01:20 Sunset Systems, it seems, gets more money than Twilight, just on the basis of the value of the streams.
01:27 But, right now, to see the picture that comes out of the total amount of our data over the past six years, we use the Timeline tool.
01:36 Here we see that at the beginning all cash flows went to Sunset Systems LLC.
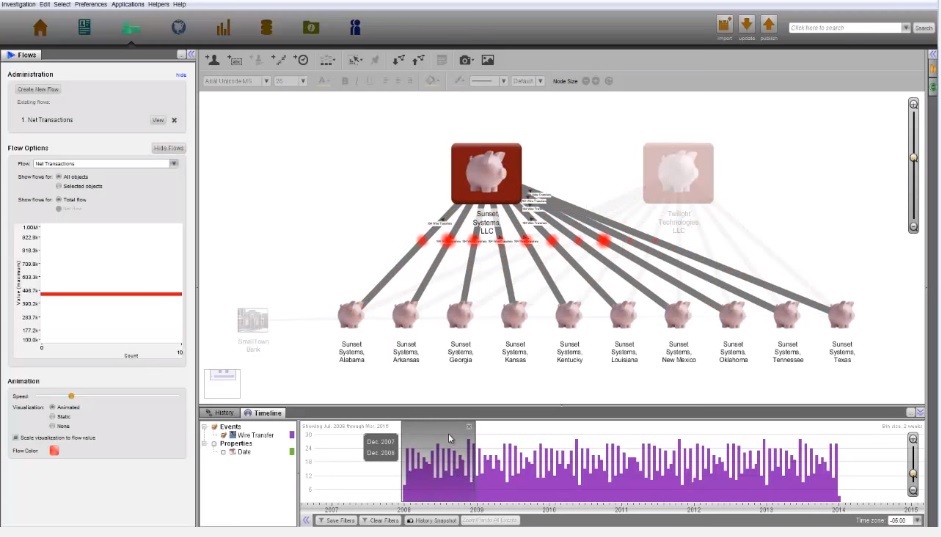
01:42 By the end of 2011, Sunset Systems, apparently, ceased to exist and all streams were redirected to Twilight Technologies LLC.
01:50 Hypothetically, it can be assumed that both of these accounts are part of the same scheme.
01:57 To test the hypothesis, we “look around” among related objects.

02:02 We found that both organizations are registered at the same business address.
02:08 If we “look around” among related events, we will see a lot of new accounts that look like intermediate ones.

02:18 Using a histogram ("Histogram"), we can divide these accounts by type, into those who receive remittances and those that receive checks.
02:22 I chose check transfers, since we assume that the rest are related to doing business.
02:30 Check transfers sometimes give the keys to understanding what the company does.
02:38 These four seem to be serving organizations. And, since they do not arouse suspicion, we will simply remove them from the graph.
02:45 The data is still stored in Palantir, and we can return it at any time.
02:47 Now, look at the remaining four accounts. They look like people.
02:51 We will “look around” among related objects and see that these accounts belong to four people, as well as the addresses of these people.
02:59 Sunset Systems and Twilight Technologies seem to pay these people, so they look like employees.
03:05 We’ll put them aside from everything else as far as possible.

03:11 If we go back to accounts receiving money transfers
03:15 We can continue our investigation by using “search around” a few more times.
03:22 First, we will see that they are associated with six new accounts that look like people belong.

03:36 Another “search around” reveals that all accounts are open in one bank and one applicant (the signer is the person who signs) by a person named Quasar Atlas

03:54 The last “search around” reveals the relationship between account holders and their addresses.


04:08 Now, when we see the big picture, we will again turn to the assistant “Streams”.

04:11 Money moves from ten accounts from which we started, through two current accounts, then we will see the movement of funds through intermediate accounts and some overhead costs, and, finally, to two families.
04:22 A study of the work we did in these few minutes shows that here we used the results of an analysis conducted several weeks earlier. We have about fifty accounts and more than ten thousand transactions, more than thirty million dollars.
04:34 And now we can see not only the general picture, but also consider the details.
04:40 For a better understanding of the relationship between the two accounts, we can disconnect the connection that connects them and look at each of the transactions separately, determining the day, amount, and type of payment in the transaction, as well as the source of the data.

04:58 We can explore not only the connections, but also the objects themselves. For example, if we open the account of Celeste Atlas, we will get a brief description of the activity of her account, and raise the documents associated with it.

05:09 For example, we can open the latest bank report and see that she owns about three million dollars, and is engaged in alteration of residential premises.

05:17 Now that we have a better idea of how the circuit looks, we can request information from field offices in order to continue the investigation.

05:24 We can drag our data onto a map, and thus see two zones of activity: one in Mars, Pennsylvania and the other in Jupiter, Florida.
05:33 In Pennsylvania, we see the location of companies that are under suspicion, and the homes of four workers, whose interior we want to look at, as well as the bank, where the first ten accounts were opened.

05 :: 45 We can request information about the interior design from the Pennsylvania field office.

05:47 In Florida, we see a bank where interim accounts were opened. We also see the homes of those two families, right by the water. We can ask the field offices for information on the interior and surroundings of houses.
06:03 Using the “collaboration” application, we can connect with field offices and exchange ideas and insights, as well as graphs and objects of Palantir (meaning objects from the system).

06:16 The Florida office has already shared a field report.

06:23 Agent 27 reports that Zabian Lynx, one of the beneficiaries (beneficiaries) of this money laundering scheme, owns an extensive collection of luxury cars.

06:34 This report is a typical example of unstructured data. The field agent creates a report and uploads it to Palantir.
06:40 To structure the report, we assign tags to important information.
06:43 When we did this, new objects automatically fall on the graph, and can be used by anyone who will look for something related to Zabian Lynx.

06:52 This saves a lot of time spent on viewing reports from the moment the first analyst notes and publishes information. Information becomes available to everyone else instantly.


More about Palantir:
Palantir, PayPal Mafia, special services, world government
Palantir 101. What is allowed to ordinary mortals to know about the second most abrupt private company in Silicon Valley
Together with the company Edison we continue the spring marathon of publications.
I will try to get to the primary sources of IT-technologies, to understand how they thought and what concepts were in the minds of the pioneers, what they dreamed about, how they saw the world of the future. Why did you think “computer”, “network”, “hypertext”, “intelligence amplifiers”, “collective problem solving system”, what meaning did they put into these concepts, what tools they wanted to achieve a result.
I hope that these materials will serve as an inspiration for those who are wondering how to go “from Zero to Unit” (to create something that had never happened before). I would like IT and “programming” to stop being just “coding for the sake of dough”, and recall that they were conceived as a lever to change themethods of warfare, education, a way of working together, thinking and communication, as an attempt to solve world problems and answer facing humanity. Something like this.
0 March. Seymour papert
March 1. Xerox alto
March 2, "Call Jake." NIC and RFC history
March 3, Grace "Grandma COBOL" Hopper
March 4 Margaret Hamilton: "Guys, I'll send you to the moon"
March 5, Hedy Lamarr. And in the movie naked to play and torpedo the bullet into the enemy
March 7 Gorgeous Six: girls who had a thermonuclear explosion calculated
March 8, "Video Games, I'm your father!"
March 9th Happy Birthday to Jeff Raskin
March 14 Joseph "Lick" Liclider: "Intergalactic computer network" and "Symbiosis of man and computer"
March 15 Vanivar Bush: “How We Can Think” (As We May Think)
March 16th Happy birthday, Richard Stallman
March 21 Douglas Engelbart: "The Mother of All Demos". Part 1

Palantir -
[ Content removed on Wikipedia request ]
')
There is a video on the official Palantir channel demonstrating the work of an analyst using the Palantir system during a money laundering investigation. In my opinion, somehow, the founding fathers of information technology, Vanivar Bush (“As We May Think”) , Douglas Engelbart (“The Mother of All Demos”) and Joseph Liclader (“Intergalactic computer network” and “ The symbiosis of man and computer ") , about which I wrote a little earlier.
(For help with the translation, thanks to Vorsin Alexey)

0:10 This video demonstrates how Palantir can be used to track money laundering and other financial crimes.
0:15 Palantir is already being used in law enforcement and financial institutions to help analysts find important in a huge data stream.
At the bottom of the screen is the inscription: “All the data used in this video is imaginary or randomly generated. All coincidences with real people, organizations, or investigations are random. ”
0:25 This video will demonstrate a typical analyst workflow.
0:30 We received information that these ten bills receive illegal and laundered money.

0:35 We see that all accounts have similar names and are open in the same bank.
0:40 They belong to subsidiaries of Sunset Systems.
0:43 Using Palantir, we can understand the nature of this money laundering scheme.

0:49 If we “look around” (we use the “Search around” tool) for the account-related transactions, we will see that they are associated with two new accounts: “Sunset Systems LLC” and “Twilight Technologies LLC”.

0:57 We can analyze each of the resulting groups of links separately, but to understand the big picture, we use the “flows” tool (flows).

01:06 As expected, we see cash flows from ten accounts from which we started to two current accounts.
01:13 The “Flows” assistant allows comparing cash flows. The more circles, the greater the flow.

01:20 Sunset Systems, it seems, gets more money than Twilight, just on the basis of the value of the streams.
01:27 But, right now, to see the picture that comes out of the total amount of our data over the past six years, we use the Timeline tool.
01:36 Here we see that at the beginning all cash flows went to Sunset Systems LLC.

01:42 By the end of 2011, Sunset Systems, apparently, ceased to exist and all streams were redirected to Twilight Technologies LLC.
01:50 Hypothetically, it can be assumed that both of these accounts are part of the same scheme.
01:57 To test the hypothesis, we “look around” among related objects.

02:02 We found that both organizations are registered at the same business address.
02:08 If we “look around” among related events, we will see a lot of new accounts that look like intermediate ones.

02:18 Using a histogram ("Histogram"), we can divide these accounts by type, into those who receive remittances and those that receive checks.
02:22 I chose check transfers, since we assume that the rest are related to doing business.
02:30 Check transfers sometimes give the keys to understanding what the company does.
02:38 These four seem to be serving organizations. And, since they do not arouse suspicion, we will simply remove them from the graph.
02:45 The data is still stored in Palantir, and we can return it at any time.
02:47 Now, look at the remaining four accounts. They look like people.
02:51 We will “look around” among related objects and see that these accounts belong to four people, as well as the addresses of these people.
02:59 Sunset Systems and Twilight Technologies seem to pay these people, so they look like employees.
03:05 We’ll put them aside from everything else as far as possible.

03:11 If we go back to accounts receiving money transfers
03:15 We can continue our investigation by using “search around” a few more times.
03:22 First, we will see that they are associated with six new accounts that look like people belong.

03:36 Another “search around” reveals that all accounts are open in one bank and one applicant (the signer is the person who signs) by a person named Quasar Atlas

03:54 The last “search around” reveals the relationship between account holders and their addresses.


04:08 Now, when we see the big picture, we will again turn to the assistant “Streams”.

04:11 Money moves from ten accounts from which we started, through two current accounts, then we will see the movement of funds through intermediate accounts and some overhead costs, and, finally, to two families.
04:22 A study of the work we did in these few minutes shows that here we used the results of an analysis conducted several weeks earlier. We have about fifty accounts and more than ten thousand transactions, more than thirty million dollars.
04:34 And now we can see not only the general picture, but also consider the details.
04:40 For a better understanding of the relationship between the two accounts, we can disconnect the connection that connects them and look at each of the transactions separately, determining the day, amount, and type of payment in the transaction, as well as the source of the data.

04:58 We can explore not only the connections, but also the objects themselves. For example, if we open the account of Celeste Atlas, we will get a brief description of the activity of her account, and raise the documents associated with it.

05:09 For example, we can open the latest bank report and see that she owns about three million dollars, and is engaged in alteration of residential premises.

05:17 Now that we have a better idea of how the circuit looks, we can request information from field offices in order to continue the investigation.

05:24 We can drag our data onto a map, and thus see two zones of activity: one in Mars, Pennsylvania and the other in Jupiter, Florida.
05:33 In Pennsylvania, we see the location of companies that are under suspicion, and the homes of four workers, whose interior we want to look at, as well as the bank, where the first ten accounts were opened.

05 :: 45 We can request information about the interior design from the Pennsylvania field office.

05:47 In Florida, we see a bank where interim accounts were opened. We also see the homes of those two families, right by the water. We can ask the field offices for information on the interior and surroundings of houses.
06:03 Using the “collaboration” application, we can connect with field offices and exchange ideas and insights, as well as graphs and objects of Palantir (meaning objects from the system).

06:16 The Florida office has already shared a field report.

06:23 Agent 27 reports that Zabian Lynx, one of the beneficiaries (beneficiaries) of this money laundering scheme, owns an extensive collection of luxury cars.

06:34 This report is a typical example of unstructured data. The field agent creates a report and uploads it to Palantir.
06:40 To structure the report, we assign tags to important information.
06:43 When we did this, new objects automatically fall on the graph, and can be used by anyone who will look for something related to Zabian Lynx.

06:52 This saves a lot of time spent on viewing reports from the moment the first analyst notes and publishes information. Information becomes available to everyone else instantly.


More about Palantir:
Palantir, PayPal Mafia, special services, world government
Palantir 101. What is allowed to ordinary mortals to know about the second most abrupt private company in Silicon Valley
Together with the company Edison we continue the spring marathon of publications.
I will try to get to the primary sources of IT-technologies, to understand how they thought and what concepts were in the minds of the pioneers, what they dreamed about, how they saw the world of the future. Why did you think “computer”, “network”, “hypertext”, “intelligence amplifiers”, “collective problem solving system”, what meaning did they put into these concepts, what tools they wanted to achieve a result.
I hope that these materials will serve as an inspiration for those who are wondering how to go “from Zero to Unit” (to create something that had never happened before). I would like IT and “programming” to stop being just “coding for the sake of dough”, and recall that they were conceived as a lever to change the
0 March. Seymour papert
March 1. Xerox alto
March 2, "Call Jake." NIC and RFC history
March 3, Grace "Grandma COBOL" Hopper
March 4 Margaret Hamilton: "Guys, I'll send you to the moon"
March 5, Hedy Lamarr. And in the movie naked to play and torpedo the bullet into the enemy
March 7 Gorgeous Six: girls who had a thermonuclear explosion calculated
March 8, "Video Games, I'm your father!"
March 9th Happy Birthday to Jeff Raskin
March 14 Joseph "Lick" Liclider: "Intergalactic computer network" and "Symbiosis of man and computer"
March 15 Vanivar Bush: “How We Can Think” (As We May Think)
March 16th Happy birthday, Richard Stallman
March 21 Douglas Engelbart: "The Mother of All Demos". Part 1
Source: https://habr.com/ru/post/280434/
All Articles