We solve the problem of interception and substitution of DNS queries. DNSCrypt in Yandex Browser
When it comes to protecting web traffic from interception and spoofing, the HTTPS protocol or even your own VPN server comes first to your mind. Unfortunately, many people forget about another unprotected side, namely DNS queries. Today, I will once again draw attention to this problem and tell you how we solve it in Yandex Browser using the DNSCrypt technology.
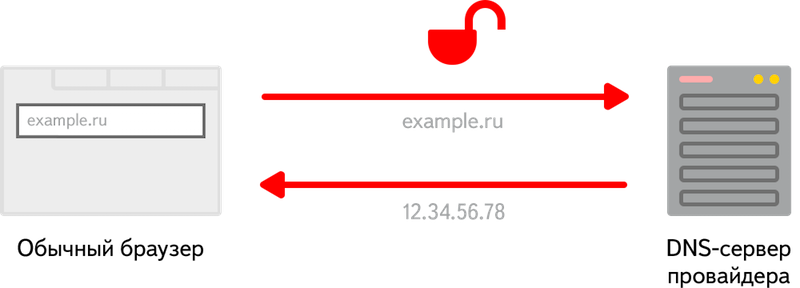
The architecture of the domain name system (DNS) with rare exceptions has remained unchanged since 1983. Every time you want to open a website, the browser sends a request indicating the domain to the DNS server, which in response sends the required IP address. Both the request and the response to it are transmitted in the clear, without any encryption. This means that your provider, network administrator or attacker with MITM can not only keep the history of all the sites you requested, but also replace the answers to these requests. It sounds unpleasant, is not it?
')
I propose to recall a few real stories of interception and substitution of DNS queries.
DNS hijacking
Intercepting DNS queries (DNS hijacking) is not a rare horror story, but a common practice. For example, among providers . This usually works as follows. If the user tries to go to a non-existent site, the provider redirects him to his page with advertising. And maybe not on his own.
The American provider Earthlink in 2006 began to redirect users and information about their requests to the advertising partner Barefruit. It looked especially bad if the user requested a non-existent domain of a well-known site, for example, webmale.google.com. The user saw ads and content that had nothing to do with google.com in the address bar.
This practice clearly violates the RFC standard for DNS responses and makes users vulnerable to XSS attacks. For example, researcher Dan Kaminsky demonstrated a vulnerability that allowed fraudulent frames to be built into Facebook or PayPal.

Of course, you can refuse to use the provider’s DNS server and add third-party solutions (for example, Google Public DNS or Yandex.DNS) in the settings of the router. But in the absence of encryption, this does not solve the problem. The provider may well intervene here, replacing the answer with your own.
If providers have already learned how to earn money by replacing DNS responses, then what about fraudsters? In 2007, a group of enterprising people from Estonia created the DNSChanger Trojan, which in a few years infected 4 million computers worldwide. Trojan changed the DNS system settings, which led to the appearance of advertising on web pages. This brought the creators $ 14 million and a prison sentence. And the most surprising thing about this story is that, according to the court decision, it was necessary to maintain temporary DNS servers for 7 months at the addresses where the scam servers were located. If they had not done this, the users of the infected devices would have instantly lost access to the network.
The scale of the DNSChanger Trojan is impressive, but the Brazilians outdid it. 4.5 million DSL modems were cracked in Brazil alone in 2011-2012. To do this, it was enough to send spam with reference to a malicious page that cracked a modem and registered a new address of the DNS server. And this time the fraudsters did not begin to waste time with advertising. On their fake DNS servers, they replaced the addresses for all the major banks in Brazil.
With home and office WiFi routers, the situation is just as sad as with Brazilian modems. Users often leave the factory login and password for the admin panel, and almost no one follows the release of fresh firmware with fixed vulnerabilities (except for Habr's readers, of course). Last year, researchers from Sentrant in their report told about new cases of hacking routers. Fraudsters intercepted appeals to Google Analytics and thanks to this they built ads on sites.
I think with examples of interception you can finish. The conclusion here is simple: DNS intercepts a lot, at different stages and for different purposes.
DNSCrypt
The developers of the popular OpenDNS service offered a solution to the problem several years ago. They created the open-source utility DNSCrypt and the protocol of the same name, which plays the same role for DNS queries as SSL for HTTP.
First, DNSCrypt encrypts messages between your computer and the DNS server using strong elliptical cryptography . This will protect them from interception and MITM.
Secondly, you are no longer tied to the server of the provider or the settings of your router. DNSCrypt addresses addresses directly to the server you specify.
Until now, to use DNSCrypt, users had to install a separate utility on their computer. This is not difficult, but without a wide dissemination of knowledge about the threat and how to solve it, one can hardly count on the massive use of technology.
DNSCrypt support in Yandex Browser
Our team considers DNS encryption to be no less important than switching to HTTPS, so we decided to support DNSCrypt at the Yandex browser level. And today we are starting to test the new beta version of Yandex. Browser 16.4, whose users can enable DNS request protection in their settings.

In this case, all requests in encrypted form will be sent to a fast Yandex DNS server , which also received support for the DNSCrypt protocol. We do not want to restrict users to only one server, so in the near future we will add the possibility to choose an alternative DNS server (for example, the same OpenDNS) in this place.

And something else. You can replace the phishing IP address not only by intercepting the request, but also through the most common system host file. Therefore, we are now experimenting with the prohibition to use the system resolver in case of unavailability of the DNS server. We understand that the inclusion of this option by default can harm users of corporate and local resources, so for the time being we are only watching and collecting reviews.
You can install the beta with browser.yandex.ru/beta . We would be interested to know the opinion of the community.

The architecture of the domain name system (DNS) with rare exceptions has remained unchanged since 1983. Every time you want to open a website, the browser sends a request indicating the domain to the DNS server, which in response sends the required IP address. Both the request and the response to it are transmitted in the clear, without any encryption. This means that your provider, network administrator or attacker with MITM can not only keep the history of all the sites you requested, but also replace the answers to these requests. It sounds unpleasant, is not it?
')
I propose to recall a few real stories of interception and substitution of DNS queries.
DNS hijacking
Intercepting DNS queries (DNS hijacking) is not a rare horror story, but a common practice. For example, among providers . This usually works as follows. If the user tries to go to a non-existent site, the provider redirects him to his page with advertising. And maybe not on his own.
The American provider Earthlink in 2006 began to redirect users and information about their requests to the advertising partner Barefruit. It looked especially bad if the user requested a non-existent domain of a well-known site, for example, webmale.google.com. The user saw ads and content that had nothing to do with google.com in the address bar.
This practice clearly violates the RFC standard for DNS responses and makes users vulnerable to XSS attacks. For example, researcher Dan Kaminsky demonstrated a vulnerability that allowed fraudulent frames to be built into Facebook or PayPal.

Of course, you can refuse to use the provider’s DNS server and add third-party solutions (for example, Google Public DNS or Yandex.DNS) in the settings of the router. But in the absence of encryption, this does not solve the problem. The provider may well intervene here, replacing the answer with your own.
If providers have already learned how to earn money by replacing DNS responses, then what about fraudsters? In 2007, a group of enterprising people from Estonia created the DNSChanger Trojan, which in a few years infected 4 million computers worldwide. Trojan changed the DNS system settings, which led to the appearance of advertising on web pages. This brought the creators $ 14 million and a prison sentence. And the most surprising thing about this story is that, according to the court decision, it was necessary to maintain temporary DNS servers for 7 months at the addresses where the scam servers were located. If they had not done this, the users of the infected devices would have instantly lost access to the network.
The scale of the DNSChanger Trojan is impressive, but the Brazilians outdid it. 4.5 million DSL modems were cracked in Brazil alone in 2011-2012. To do this, it was enough to send spam with reference to a malicious page that cracked a modem and registered a new address of the DNS server. And this time the fraudsters did not begin to waste time with advertising. On their fake DNS servers, they replaced the addresses for all the major banks in Brazil.
With home and office WiFi routers, the situation is just as sad as with Brazilian modems. Users often leave the factory login and password for the admin panel, and almost no one follows the release of fresh firmware with fixed vulnerabilities (except for Habr's readers, of course). Last year, researchers from Sentrant in their report told about new cases of hacking routers. Fraudsters intercepted appeals to Google Analytics and thanks to this they built ads on sites.
I think with examples of interception you can finish. The conclusion here is simple: DNS intercepts a lot, at different stages and for different purposes.
DNSCrypt
The developers of the popular OpenDNS service offered a solution to the problem several years ago. They created the open-source utility DNSCrypt and the protocol of the same name, which plays the same role for DNS queries as SSL for HTTP.
First, DNSCrypt encrypts messages between your computer and the DNS server using strong elliptical cryptography . This will protect them from interception and MITM.
Secondly, you are no longer tied to the server of the provider or the settings of your router. DNSCrypt addresses addresses directly to the server you specify.
Until now, to use DNSCrypt, users had to install a separate utility on their computer. This is not difficult, but without a wide dissemination of knowledge about the threat and how to solve it, one can hardly count on the massive use of technology.
DNSCrypt support in Yandex Browser
Our team considers DNS encryption to be no less important than switching to HTTPS, so we decided to support DNSCrypt at the Yandex browser level. And today we are starting to test the new beta version of Yandex. Browser 16.4, whose users can enable DNS request protection in their settings.

In this case, all requests in encrypted form will be sent to a fast Yandex DNS server , which also received support for the DNSCrypt protocol. We do not want to restrict users to only one server, so in the near future we will add the possibility to choose an alternative DNS server (for example, the same OpenDNS) in this place.

And something else. You can replace the phishing IP address not only by intercepting the request, but also through the most common system host file. Therefore, we are now experimenting with the prohibition to use the system resolver in case of unavailability of the DNS server. We understand that the inclusion of this option by default can harm users of corporate and local resources, so for the time being we are only watching and collecting reviews.
You can install the beta with browser.yandex.ru/beta . We would be interested to know the opinion of the community.
Source: https://habr.com/ru/post/280380/
All Articles