The book "Computer Networks. Principles, technologies, protocols "
Hi Habrozhiteli! We decided to write a review dedicated to the textbook about network technologies:
 The fifth edition of one of the best Russian textbooks on network technologies, translated into English, Spanish, Portuguese and Chinese, reflects the changes that have occurred in the field of computer networks for 6 years since the preparation of the previous edition: overcoming local and global networks of speed 100 Gbit / s and mastering terabit speeds; increasing the efficiency and flexibility of primary optical networks due to the appearance of reconfigurable input-output multiplexers (ROADM) and the use of DWDM superchannels operating on the basis of a flexible frequency plan; development of technology virtualization of network functions and services that led to the spread of cloud services; coming to the fore safety issues.
The fifth edition of one of the best Russian textbooks on network technologies, translated into English, Spanish, Portuguese and Chinese, reflects the changes that have occurred in the field of computer networks for 6 years since the preparation of the previous edition: overcoming local and global networks of speed 100 Gbit / s and mastering terabit speeds; increasing the efficiency and flexibility of primary optical networks due to the appearance of reconfigurable input-output multiplexers (ROADM) and the use of DWDM superchannels operating on the basis of a flexible frequency plan; development of technology virtualization of network functions and services that led to the spread of cloud services; coming to the fore safety issues.
The publication is intended for students, graduate students and technicians who would like to gain basic knowledge of the principles of building computer networks, understand the features of traditional and promising technologies of local and global networks, explore ways to create large composite networks and control such networks.
This book is the result of many years of experience teaching web-based courses in classrooms of public universities and various educational centers, as well as participation in scientific and technical developments, such as the Janet project, associated with the creation of a unifying network of university campuses and research centers in the UK, and pan-European projects GEANT2 and GEANT3.
')
The book is based on the materials of the courses “Problems of building corporate networks”, “Fundamentals of network technologies”, “Organization of remote access”, “TCP / IP networks”, “Strategic planning of enterprise-wide networks” and a number of others. These materials have been successfully tested in an uncompromising and complex audience consisting of students with significantly different levels of training and professional interests. Among them were undergraduate and graduate students of universities, network administrators and integrators, heads of automation departments and teachers. Taking into account the specifics of the audience, the lecture courses were structured so that the beginner received the basis for further study, and the specialist systematized and actualized his knowledge. In accordance with the same principles, this book is also written - it is a fundamental course on computer networks that combines the breadth of coverage of the main areas, problems and technologies of this rapidly developing field of knowledge with thorough consideration of the details of each technology.
The book is intended for students, graduate students and technical specialists who want to gain basic knowledge of the principles of building computer networks, to understand the features of traditional and promising technologies of local and global networks, to explore ways of creating large composite networks and managing such networks.
The textbook will be useful for beginners in the field of network technologies who have only a general understanding of the work of networks from the experience of communicating with personal computers and the Internet, but would like to gain fundamental knowledge to continue the study of networks on their own.
The book can help existing network specialists to get acquainted with the technologies they have never encountered in practical work, systematize their knowledge, become a reference book that allows them to find a description of a specific protocol, frame format, etc. In addition, the book provides the necessary theoretical basis for preparation for certification exams such as Cisco CCNA, CCNP, CCDP and CCIP.
University students enrolled in the direction of “220,000. Informatics and computer engineering ”and in the field of“ Computers, complexes, systems and networks ”,“ Automated machines, complexes, systems and networks ”,“ Software for computers and automated systems ”can use the book as recommended by the Ministry of Education of the Russian Federation study guide.
Chapter 25
Network management service
Functions of network management systems
Like any complex technical object, a computer network requires performing various actions to maintain it in working condition, analyze and optimize its performance, and protect against internal and external threats. Among the variety of funds raised to achieve these goals, an important place is occupied by network management services (systems).
Network Management System (NMS) is a complex hardware and software complex that controls network traffic and manages the communication equipment of a large computer network.
Network management systems work, as a rule, in an automated mode, performing the simplest actions automatically and leaving the person making difficult decisions based on the information prepared by the system.
The network management system is designed to solve the following groups of tasks:
- Network configuration and naming management consists in configuring the parameters of both individual network elements and the network as a whole. For network elements such as routers, multiplexers, etc., configuration consists in assigning network addresses, identifiers (names), geographic location, etc. For a network as a whole, configuration management usually begins with building a network map, that is, displaying real links between network elements and links between them.
- Error handling includes the identification, identification and elimination of the consequences of failures and failures.
- Analysis of performance and reliability associated with the assessment on the basis of the accumulated statistical information of such parameters as the response time of the system, the bandwidth of a real or virtual communication channel between two final subscribers of the network, traffic intensity in individual segments and channels of the network, as well as the probability of data corruption transfer through the network. The results of performance and reliability analysis allow you to control the service level agreement (SLA) concluded between the network user and its administrators (or the company selling the services). Without performance and reliability analysis tools, the public network service provider or the company's information technology department will not be able to control, much less provide the necessary level of service to the end users of the network.
- Security management involves controlling access to network resources (data and equipment) and preserving the integrity of data during storage and transmission through the network. The basic elements of security management are user authentication procedures, assignment and verification of access rights to network resources, distribution and support of encryption keys, authority management, etc. Often, the functions of this group are not included in network management systems, or are implemented as special software security, such as firewalls or centralized authorization systems, or are part of operating systems and system applications.
- Accounting of the network includes the registration of the time of use of various network resources (devices, channels and transport services) and maintenance of billing operations (payment for resources).
The control system standards do not distinguish between managed objects representing communication equipment (channels, LAN segments, switches and routers, modems and multiplexers), and objects representing computer hardware and software. However, in practice, the division of control systems by types of managed objects is widespread.
In cases where managed objects are computers, as well as their system and application software, then a special name is often used for the control system - the System Management System (SMS).
An SMS usually automatically collects information about computers installed on a network and creates entries in a special database about hardware and software resources. SMS can centrally install and administer applications that run from servers, as well as remotely measure the most important parameters of a computer, operating system, DBMS (for example, processor utilization or physical memory, page paging intensity, etc.). SMS allows the administrator to take over remote control of the computer in the emulation mode of the graphical interface of popular operating systems.
Network Management Systems Architecture
Agent managed object
To solve these problems, it is necessary to have the ability to control a separate device (object). Typically, each device that requires a fairly complex configuration, the manufacturer is accompanied by a stand-alone configuration and management program operating in the specialized OS environment installed on this device. We will call such a software component an agent . Agents can be embedded in managed equipment or work on a device connected to the control interface of such a device. A single agent can generally manage several devices of the same type.
The agent maintains an interface with an operator / administrator who sends him requests and commands to perform certain operations.
The agent can perform the following functions:
- store, retrieve and transmit, upon requests from outside, information about the technical and configuration parameters of the device, including the device model, number of ports, type of OS, type of OS, communication with other devices, etc .;
- perform, store and transmit, upon request from outside, measurements (counts) of the device operation characteristics, such as the number of received packets, the number of dropped packets, the degree of buffer filling, the port state (operational or inoperative);
- change the configuration parameters by commands received from the outside.
In the described scheme, the agent plays the role of a server accessed by the client administrator with requests for the values of the characteristics or for setting the configuration parameters of the controlled device.
To obtain the required data on the object, as well as to issue control actions to it, the agent must be able to interact with it. The variety of types of managed objects does not allow to standardize the way the agent interacts with the object. This task is solved by the developers when the agents are embedded in communication equipment or in the operating system. The agent can be equipped with special sensors for obtaining information, such as temperature sensors. Agents can differ in different levels of intelligence: from the minimum, sufficient only to count personnel and packets passing through equipment, to very high, allowing them to perform sequences of control commands in emergency situations, build time dependencies, filter emergency messages, etc.
Two-link and three-link control schemes
Among the tasks defined for network management systems, there are relatively rare operations, such as configuring a device, and there are those that require frequent system intervention (analysis of the performance of each of the network devices, collecting statistics on device load). In the first case, “manual” control is used when the administrator sends commands to the agent from his console. It is clear that this option is not at all suitable for the global monitoring of all devices on the network.
Consider first the option of manual two - tier control (Fig. 25.1). For example, the telnet remote control protocol can be used as a client and server interaction protocol, the client part of which should be installed on the administrator’s computer and the server part on the device. The telnet server part must also support an interface with an agent, from which information about the state of the managed object and the value of its characteristics will be received. On the client side, the telnet protocol can be associated with a graphical user interface support program, which, for example, displays the requested characteristic to the administrator in a graphical form. In general, an administrator can work with multiple agents.
The protocol for the interaction between the client and server parts often uses the HTTP web service protocol.
For tasks that require frequent operations to control individual devices, as well as with an increase in the number of controlled devices, the considered scheme can no longer solve the problem. The scheme introduces a new intermediate link, called the manager. The manager is designed to automate the interaction of the operator with a variety of agents. Shown in fig. 25.2 the network management service scheme is implemented as a three-tier distributed application in which the functions between the links are distributed as follows.
The first link - the client of the control system, installed on the operator’s computer, supports the user interface with an intermediate server.
The second link, an intermediate server, serves as a manager , is installed either on the operator’s computer or on a dedicated computer. The manager usually interacts with several clients and agents, providing dispatching of client requests to servers and processing the data received from agents in accordance with the tasks assigned to the management system. In order to increase reliability and productivity, several managers may be provided in the control system.
The third link, the agent , is installed on the managed object or its associated computer.
Manager, agent and managed object interaction
Let us dwell on that part of the management system, which relates to the interaction of the manager, agent and managed object (Fig. 25.3).
For each managed object on the network, an object model is created. It represents all the characteristics of the object that are needed to control it. For example, the router model usually includes such characteristics as the number of ports, their type, the routing table, the number of frames and packets of the link, network and transport protocols that have passed through these ports. Network object models are used by the manager as a source of knowledge about which set of characteristics a particular object has.
The model of the object coincides with the logical scheme of the database (DB) of the object storing the values of its characteristics. This database is stored on the device and is constantly updated with the results of measurements of the characteristics carried out by the agent.
In network management systems based on the SNMP protocol, this database is called the Management Information Base ( MIB ).
The manager does not have direct access to the MIB database; he must contact his agent via the network to obtain specific values of the characteristics of the object. Thus, the agent is an intermediary between the managed object and the manager. The manager and agent communicate using a standard protocol . This protocol allows the manager to query the values of parameters stored in the MIB, and the agent to transmit information on the basis of which the manager must manage the object.
There are in-band control (In-band), when control commands go through the same channel through which user data is transmitted, and out-of-band control (Out-band), that is, carried out outside the transmission channel of user data.
In-band management is more economical since it does not require the creation of a separate infrastructure for the transmission of control data. However, out-of-band management is more reliable, since the corresponding equipment can perform its functions even when certain network elements fail and the main data transmission channels become unavailable.
The scheme "manager - agent - managed object" allows you to build quite complex structurally management systems.
The presence of several managers allows you to distribute between them the load on the processing of control data, ensuring the scalability of the system. As a rule, two types of relations between managers are used: peer-to-peer (fig. 25.4) and hierarchical (fig. 25.5). Each agent shown in the figures controls one or more network elements (Network Element, NE), the parameters of which it places in the corresponding MIB database. Managers retrieve data from their agents' MIB databases, process

they are stored in their own databases. Operators working at workstations can connect with any of the managers and use the graphical interface to view information about the managed network and also give the manager some guidelines for managing the network or its elements.
In the case of peer-to-peer connections, each manager manages his part of the network based on information received from the underlying agents. The central manager is missing. Coordination of the work of managers is achieved through the exchange of information between the databases of managers. The peer-to-peer management system is today considered inefficient and outdated.
Much more flexible is the hierarchical construction of relations between managers. Each lower level manager also acts as an agent for the top level manager. This agent works with the enlarged MIB model of its part of the network. In such a MIB database, it is the information that the top-level manager needs to manage the network as a whole.
Network Management Systems Based on SNMP Protocol
SNMP protocol
SNMP (Simple Management Network Protocol) is used as the standard protocol for manager and agent interaction.
The SNMP protocol refers to the TCP / IP stack application layer. To transport its messages, it uses UDP datagram transport protocol, which, as we know, does not provide reliable delivery. TCP, which provides reliable connection-based messaging, loads up quite a bit on managed devices, which were not very powerful at the time SNMP was developed, so it was decided to refuse TCP services.
SNMP is a request-response protocol, that is, for each request received from the manager, the agent must transmit a response. A feature of the protocol is its extreme simplicity - it includes only a few commands.
- The GetRequest command is used by the manager to query the agent about the value of a variable by its standard name.
- The GetNextRequest command is used by the manager to retrieve the value of the next object (without specifying its name) when viewing the table of objects sequentially.
- Using the Response command, the SNMP agent sends the manager a response to the GetRequest or GetNextRrequest command.
- The SetRequest command allows the manager to change the values of a variable or list of variables. Using the SetRequest command, the device itself is controlled. The agent must “understand” the meaning of the values of the variable that is used to control the device, and on the basis of these values, perform a real control action: disable the port, assign the port to a specific VLAN line, etc. The Set command is also suitable for setting a condition under which the SNMP The agent should send a message to the manager. , , , , , . , .
— Trap .
— GetBulk .
SNMP-, , . SNMP- : , .
(community string) , . , , SNMP, ( «public»). «» , .
, . , SNMP. . , , GetRequest, :
— ;
— ( );
— ( , );
— SNMP MIB, .
MIB
MIB , . (MIB-I) 114 . . 8 , :
System — (, , );
Interfaces — (, , , , );
Address Translation Table — (, ARP);
Internet Protocol — , IP ( IP-, , IP-);
ICMP — , ICMP;
TCP — , TCP ( , TCP-);
UDP — , UDP ( , UPD-);
EGP — , EGP ( ).
. Interfaces , :
ifType — , ( );
‰‰ifMtu — , ;
‰‰ifSpeed — ;
‰‰ifPhysAddress — (MAC-);
‰‰ifAdminStatus — (up — , down — , testing — );
‰‰ifOperStatus — , , ifAdminStatus;
‰‰ifInOctets — , , , SNMP-;
‰‰ifInUcastPkts — , ;
‰‰ifInNUcastPkts — , ;
ifInDiscards — , , , , - ;
‰‰ifInErrors — , - .
, , , . SNMP — RMON (Remote Network MONitoring — ). , RMON, , , . , SNMP- , , , RMON- — . RMON-, , . , , , . .
telnet
, , , , .
, 70- , . PAD X.25 , , - .
, , . , , . IP- telnet (RFC 854).
telnet -, - , .
telnet, TCP- , . TCP- telnet . telnet . , TCP- . telnet , .
telnet Unix FTP- . telnet , , , , telnet , . telnet SSH (Secure SHell), , telnet, Unix1. SSH, telnet, . SSH .
telnet , : , . , , , SNMP.
telnet SNMP . Telnet , , , , . SNMP, , , . , , . , , , .
findings
— - , .
, , , .
. , .
MIB, . , .
SNMP — TCP/IP, «-».
, , , , .
, , . IP- telnet, - , .
:
« » « » , ( );
. . , . . ., « »
. . . ;
. . , . . ., «
»
More information about the book can be found on the publisher's website.
Table of contents
Excerpt
15% —
 The fifth edition of one of the best Russian textbooks on network technologies, translated into English, Spanish, Portuguese and Chinese, reflects the changes that have occurred in the field of computer networks for 6 years since the preparation of the previous edition: overcoming local and global networks of speed 100 Gbit / s and mastering terabit speeds; increasing the efficiency and flexibility of primary optical networks due to the appearance of reconfigurable input-output multiplexers (ROADM) and the use of DWDM superchannels operating on the basis of a flexible frequency plan; development of technology virtualization of network functions and services that led to the spread of cloud services; coming to the fore safety issues.
The fifth edition of one of the best Russian textbooks on network technologies, translated into English, Spanish, Portuguese and Chinese, reflects the changes that have occurred in the field of computer networks for 6 years since the preparation of the previous edition: overcoming local and global networks of speed 100 Gbit / s and mastering terabit speeds; increasing the efficiency and flexibility of primary optical networks due to the appearance of reconfigurable input-output multiplexers (ROADM) and the use of DWDM superchannels operating on the basis of a flexible frequency plan; development of technology virtualization of network functions and services that led to the spread of cloud services; coming to the fore safety issues.The publication is intended for students, graduate students and technicians who would like to gain basic knowledge of the principles of building computer networks, understand the features of traditional and promising technologies of local and global networks, explore ways to create large composite networks and control such networks.
From the authors
This book is the result of many years of experience teaching web-based courses in classrooms of public universities and various educational centers, as well as participation in scientific and technical developments, such as the Janet project, associated with the creation of a unifying network of university campuses and research centers in the UK, and pan-European projects GEANT2 and GEANT3.
')
The book is based on the materials of the courses “Problems of building corporate networks”, “Fundamentals of network technologies”, “Organization of remote access”, “TCP / IP networks”, “Strategic planning of enterprise-wide networks” and a number of others. These materials have been successfully tested in an uncompromising and complex audience consisting of students with significantly different levels of training and professional interests. Among them were undergraduate and graduate students of universities, network administrators and integrators, heads of automation departments and teachers. Taking into account the specifics of the audience, the lecture courses were structured so that the beginner received the basis for further study, and the specialist systematized and actualized his knowledge. In accordance with the same principles, this book is also written - it is a fundamental course on computer networks that combines the breadth of coverage of the main areas, problems and technologies of this rapidly developing field of knowledge with thorough consideration of the details of each technology.
Who is this book for?
The book is intended for students, graduate students and technical specialists who want to gain basic knowledge of the principles of building computer networks, to understand the features of traditional and promising technologies of local and global networks, to explore ways of creating large composite networks and managing such networks.
The textbook will be useful for beginners in the field of network technologies who have only a general understanding of the work of networks from the experience of communicating with personal computers and the Internet, but would like to gain fundamental knowledge to continue the study of networks on their own.
The book can help existing network specialists to get acquainted with the technologies they have never encountered in practical work, systematize their knowledge, become a reference book that allows them to find a description of a specific protocol, frame format, etc. In addition, the book provides the necessary theoretical basis for preparation for certification exams such as Cisco CCNA, CCNP, CCDP and CCIP.
University students enrolled in the direction of “220,000. Informatics and computer engineering ”and in the field of“ Computers, complexes, systems and networks ”,“ Automated machines, complexes, systems and networks ”,“ Software for computers and automated systems ”can use the book as recommended by the Ministry of Education of the Russian Federation study guide.
Chapter 25
Network management service
Functions of network management systems
Like any complex technical object, a computer network requires performing various actions to maintain it in working condition, analyze and optimize its performance, and protect against internal and external threats. Among the variety of funds raised to achieve these goals, an important place is occupied by network management services (systems).
Network Management System (NMS) is a complex hardware and software complex that controls network traffic and manages the communication equipment of a large computer network.
Network management systems work, as a rule, in an automated mode, performing the simplest actions automatically and leaving the person making difficult decisions based on the information prepared by the system.
The network management system is designed to solve the following groups of tasks:
- Network configuration and naming management consists in configuring the parameters of both individual network elements and the network as a whole. For network elements such as routers, multiplexers, etc., configuration consists in assigning network addresses, identifiers (names), geographic location, etc. For a network as a whole, configuration management usually begins with building a network map, that is, displaying real links between network elements and links between them.
- Error handling includes the identification, identification and elimination of the consequences of failures and failures.
- Analysis of performance and reliability associated with the assessment on the basis of the accumulated statistical information of such parameters as the response time of the system, the bandwidth of a real or virtual communication channel between two final subscribers of the network, traffic intensity in individual segments and channels of the network, as well as the probability of data corruption transfer through the network. The results of performance and reliability analysis allow you to control the service level agreement (SLA) concluded between the network user and its administrators (or the company selling the services). Without performance and reliability analysis tools, the public network service provider or the company's information technology department will not be able to control, much less provide the necessary level of service to the end users of the network.
- Security management involves controlling access to network resources (data and equipment) and preserving the integrity of data during storage and transmission through the network. The basic elements of security management are user authentication procedures, assignment and verification of access rights to network resources, distribution and support of encryption keys, authority management, etc. Often, the functions of this group are not included in network management systems, or are implemented as special software security, such as firewalls or centralized authorization systems, or are part of operating systems and system applications.
- Accounting of the network includes the registration of the time of use of various network resources (devices, channels and transport services) and maintenance of billing operations (payment for resources).
The control system standards do not distinguish between managed objects representing communication equipment (channels, LAN segments, switches and routers, modems and multiplexers), and objects representing computer hardware and software. However, in practice, the division of control systems by types of managed objects is widespread.
In cases where managed objects are computers, as well as their system and application software, then a special name is often used for the control system - the System Management System (SMS).
An SMS usually automatically collects information about computers installed on a network and creates entries in a special database about hardware and software resources. SMS can centrally install and administer applications that run from servers, as well as remotely measure the most important parameters of a computer, operating system, DBMS (for example, processor utilization or physical memory, page paging intensity, etc.). SMS allows the administrator to take over remote control of the computer in the emulation mode of the graphical interface of popular operating systems.
Network Management Systems Architecture
Agent managed object
To solve these problems, it is necessary to have the ability to control a separate device (object). Typically, each device that requires a fairly complex configuration, the manufacturer is accompanied by a stand-alone configuration and management program operating in the specialized OS environment installed on this device. We will call such a software component an agent . Agents can be embedded in managed equipment or work on a device connected to the control interface of such a device. A single agent can generally manage several devices of the same type.
The agent maintains an interface with an operator / administrator who sends him requests and commands to perform certain operations.
The agent can perform the following functions:
- store, retrieve and transmit, upon requests from outside, information about the technical and configuration parameters of the device, including the device model, number of ports, type of OS, type of OS, communication with other devices, etc .;
- perform, store and transmit, upon request from outside, measurements (counts) of the device operation characteristics, such as the number of received packets, the number of dropped packets, the degree of buffer filling, the port state (operational or inoperative);
- change the configuration parameters by commands received from the outside.
In the described scheme, the agent plays the role of a server accessed by the client administrator with requests for the values of the characteristics or for setting the configuration parameters of the controlled device.
To obtain the required data on the object, as well as to issue control actions to it, the agent must be able to interact with it. The variety of types of managed objects does not allow to standardize the way the agent interacts with the object. This task is solved by the developers when the agents are embedded in communication equipment or in the operating system. The agent can be equipped with special sensors for obtaining information, such as temperature sensors. Agents can differ in different levels of intelligence: from the minimum, sufficient only to count personnel and packets passing through equipment, to very high, allowing them to perform sequences of control commands in emergency situations, build time dependencies, filter emergency messages, etc.
Two-link and three-link control schemes
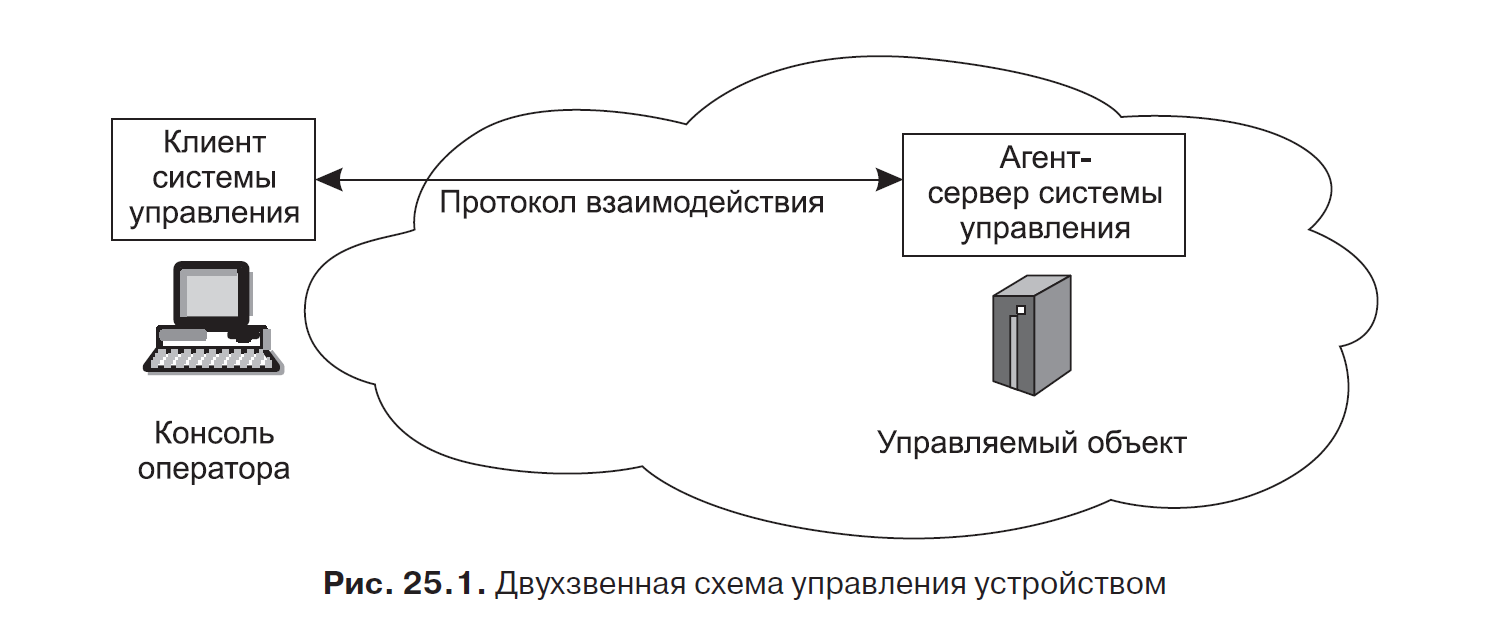
Among the tasks defined for network management systems, there are relatively rare operations, such as configuring a device, and there are those that require frequent system intervention (analysis of the performance of each of the network devices, collecting statistics on device load). In the first case, “manual” control is used when the administrator sends commands to the agent from his console. It is clear that this option is not at all suitable for the global monitoring of all devices on the network.
Consider first the option of manual two - tier control (Fig. 25.1). For example, the telnet remote control protocol can be used as a client and server interaction protocol, the client part of which should be installed on the administrator’s computer and the server part on the device. The telnet server part must also support an interface with an agent, from which information about the state of the managed object and the value of its characteristics will be received. On the client side, the telnet protocol can be associated with a graphical user interface support program, which, for example, displays the requested characteristic to the administrator in a graphical form. In general, an administrator can work with multiple agents.
The protocol for the interaction between the client and server parts often uses the HTTP web service protocol.
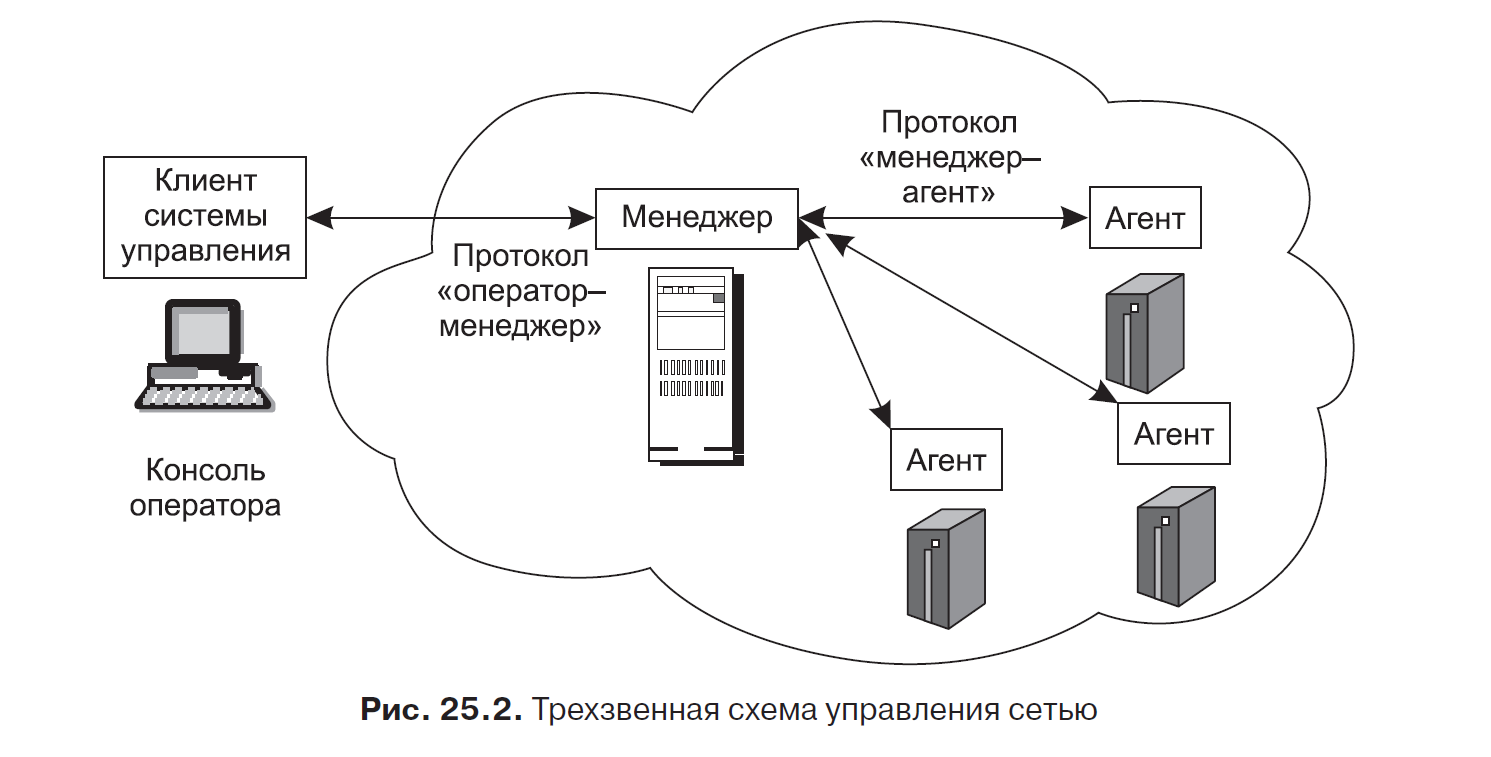
For tasks that require frequent operations to control individual devices, as well as with an increase in the number of controlled devices, the considered scheme can no longer solve the problem. The scheme introduces a new intermediate link, called the manager. The manager is designed to automate the interaction of the operator with a variety of agents. Shown in fig. 25.2 the network management service scheme is implemented as a three-tier distributed application in which the functions between the links are distributed as follows.
The first link - the client of the control system, installed on the operator’s computer, supports the user interface with an intermediate server.
The second link, an intermediate server, serves as a manager , is installed either on the operator’s computer or on a dedicated computer. The manager usually interacts with several clients and agents, providing dispatching of client requests to servers and processing the data received from agents in accordance with the tasks assigned to the management system. In order to increase reliability and productivity, several managers may be provided in the control system.
The third link, the agent , is installed on the managed object or its associated computer.
Manager, agent and managed object interaction
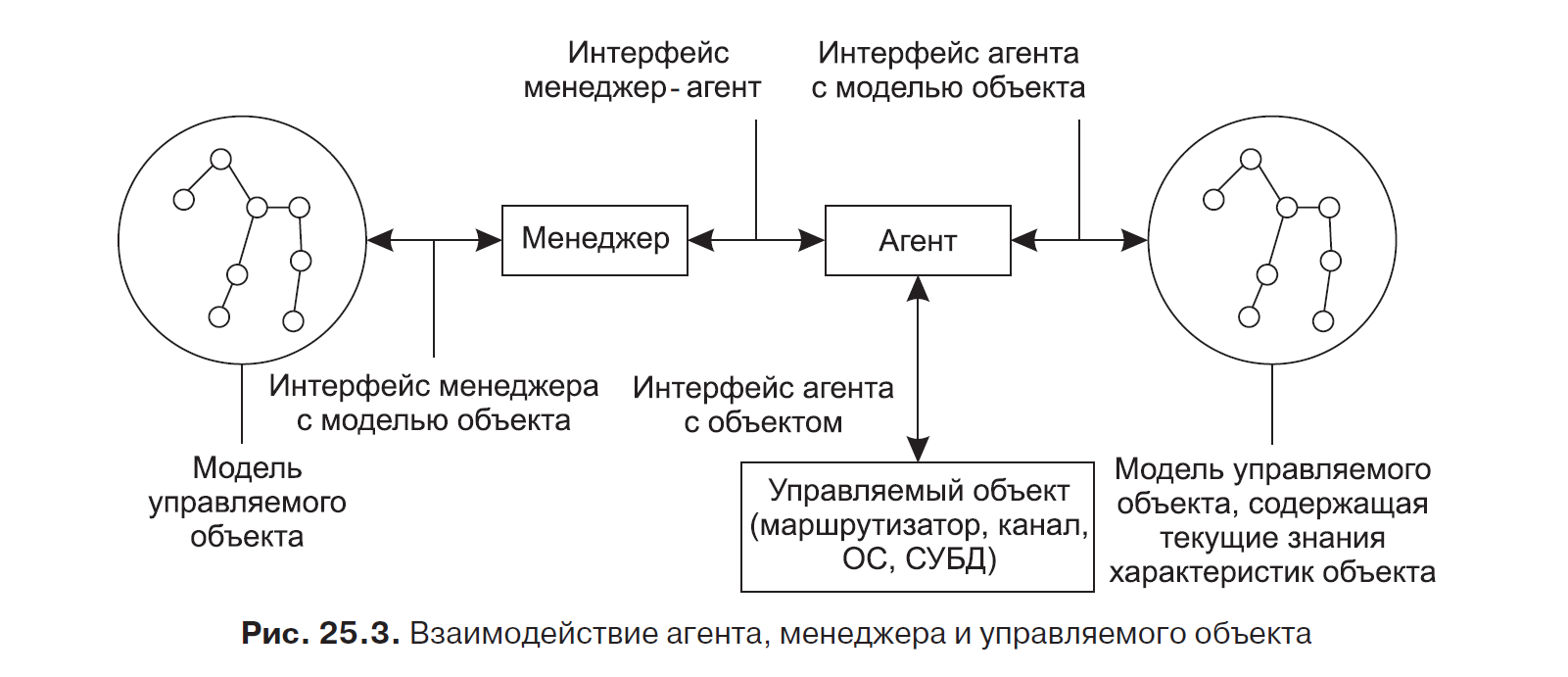
Let us dwell on that part of the management system, which relates to the interaction of the manager, agent and managed object (Fig. 25.3).
For each managed object on the network, an object model is created. It represents all the characteristics of the object that are needed to control it. For example, the router model usually includes such characteristics as the number of ports, their type, the routing table, the number of frames and packets of the link, network and transport protocols that have passed through these ports. Network object models are used by the manager as a source of knowledge about which set of characteristics a particular object has.
The model of the object coincides with the logical scheme of the database (DB) of the object storing the values of its characteristics. This database is stored on the device and is constantly updated with the results of measurements of the characteristics carried out by the agent.
In network management systems based on the SNMP protocol, this database is called the Management Information Base ( MIB ).
The manager does not have direct access to the MIB database; he must contact his agent via the network to obtain specific values of the characteristics of the object. Thus, the agent is an intermediary between the managed object and the manager. The manager and agent communicate using a standard protocol . This protocol allows the manager to query the values of parameters stored in the MIB, and the agent to transmit information on the basis of which the manager must manage the object.
There are in-band control (In-band), when control commands go through the same channel through which user data is transmitted, and out-of-band control (Out-band), that is, carried out outside the transmission channel of user data.
In-band management is more economical since it does not require the creation of a separate infrastructure for the transmission of control data. However, out-of-band management is more reliable, since the corresponding equipment can perform its functions even when certain network elements fail and the main data transmission channels become unavailable.
The scheme "manager - agent - managed object" allows you to build quite complex structurally management systems.
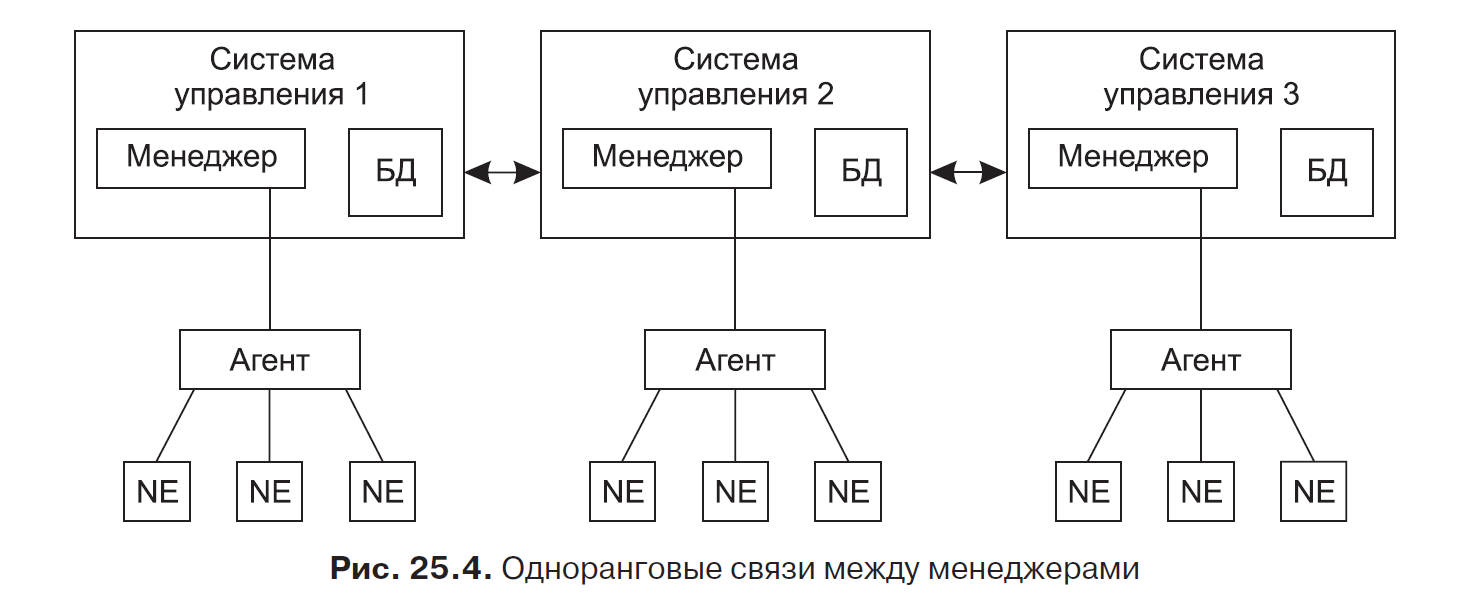
The presence of several managers allows you to distribute between them the load on the processing of control data, ensuring the scalability of the system. As a rule, two types of relations between managers are used: peer-to-peer (fig. 25.4) and hierarchical (fig. 25.5). Each agent shown in the figures controls one or more network elements (Network Element, NE), the parameters of which it places in the corresponding MIB database. Managers retrieve data from their agents' MIB databases, process
they are stored in their own databases. Operators working at workstations can connect with any of the managers and use the graphical interface to view information about the managed network and also give the manager some guidelines for managing the network or its elements.
In the case of peer-to-peer connections, each manager manages his part of the network based on information received from the underlying agents. The central manager is missing. Coordination of the work of managers is achieved through the exchange of information between the databases of managers. The peer-to-peer management system is today considered inefficient and outdated.
Much more flexible is the hierarchical construction of relations between managers. Each lower level manager also acts as an agent for the top level manager. This agent works with the enlarged MIB model of its part of the network. In such a MIB database, it is the information that the top-level manager needs to manage the network as a whole.
Network Management Systems Based on SNMP Protocol
SNMP protocol
SNMP (Simple Management Network Protocol) is used as the standard protocol for manager and agent interaction.
The SNMP protocol refers to the TCP / IP stack application layer. To transport its messages, it uses UDP datagram transport protocol, which, as we know, does not provide reliable delivery. TCP, which provides reliable connection-based messaging, loads up quite a bit on managed devices, which were not very powerful at the time SNMP was developed, so it was decided to refuse TCP services.
SNMP is a request-response protocol, that is, for each request received from the manager, the agent must transmit a response. A feature of the protocol is its extreme simplicity - it includes only a few commands.
- The GetRequest command is used by the manager to query the agent about the value of a variable by its standard name.
- The GetNextRequest command is used by the manager to retrieve the value of the next object (without specifying its name) when viewing the table of objects sequentially.
- Using the Response command, the SNMP agent sends the manager a response to the GetRequest or GetNextRrequest command.
- The SetRequest command allows the manager to change the values of a variable or list of variables. Using the SetRequest command, the device itself is controlled. The agent must “understand” the meaning of the values of the variable that is used to control the device, and on the basis of these values, perform a real control action: disable the port, assign the port to a specific VLAN line, etc. The Set command is also suitable for setting a condition under which the SNMP The agent should send a message to the manager. , , , , , . , .
— Trap .
— GetBulk .
SNMP-, , . SNMP- : , .
(community string) , . , , SNMP, ( «public»). «» , .
, . , SNMP. . , , GetRequest, :
— ;
— ( );
— ( , );
— SNMP MIB, .
MIB
MIB , . (MIB-I) 114 . . 8 , :
System — (, , );
Interfaces — (, , , , );
Address Translation Table — (, ARP);
Internet Protocol — , IP ( IP-, , IP-);
ICMP — , ICMP;
TCP — , TCP ( , TCP-);
UDP — , UDP ( , UPD-);
EGP — , EGP ( ).
. Interfaces , :
ifType — , ( );
‰‰ifMtu — , ;
‰‰ifSpeed — ;
‰‰ifPhysAddress — (MAC-);
‰‰ifAdminStatus — (up — , down — , testing — );
‰‰ifOperStatus — , , ifAdminStatus;
‰‰ifInOctets — , , , SNMP-;
‰‰ifInUcastPkts — , ;
‰‰ifInNUcastPkts — , ;
ifInDiscards — , , , , - ;
‰‰ifInErrors — , - .
, , , . SNMP — RMON (Remote Network MONitoring — ). , RMON, , , . , SNMP- , , , RMON- — . RMON-, , . , , , . .
telnet
, , , , .
, 70- , . PAD X.25 , , - .
, , . , , . IP- telnet (RFC 854).
telnet -, - , .
telnet, TCP- , . TCP- telnet . telnet . , TCP- . telnet , .
telnet Unix FTP- . telnet , , , , telnet , . telnet SSH (Secure SHell), , telnet, Unix1. SSH, telnet, . SSH .
telnet , : , . , , , SNMP.
telnet SNMP . Telnet , , , , . SNMP, , , . , , . , , , .
findings
— - , .
, , , .
. , .
MIB, . , .
SNMP — TCP/IP, «-».
, , , , .
, , . IP- telnet, - , .
:
« » « » , ( );
. . , . . ., « »
. . . ;
. . , . . ., «
»
More information about the book can be found on the publisher's website.
Table of contents
Excerpt
15% —
Source: https://habr.com/ru/post/280354/
All Articles