EC Council site infected visitors with extortionate TeslaCrypt software
The website of the well-known certification company in the field of information security EC Council since Monday, March 21, 2016 infected visitors with extortionate software TeslaCrypt .
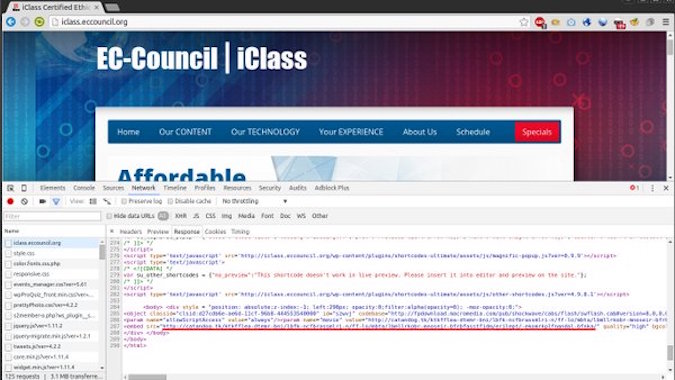
As a source in his blog ( Yonathan Klijnsma ) describes , certain users from certain countries were attacked, namely:
After redirecting from the pages of the site, the victim ended up at the Angler exploit kit page, where flash or silverlight components are used to exploit the vulnerability. Angler exploit kit first launches the Bedep Trojan on the victim's machine, which loads the last payload payload.
As described in the source, the EC Council website most likely uses the well-known CMS Wordpress with a vulnerable module, which turned out to be full of holes and led to infection.
After infection, TeslaCrypt requires the victim 1.5 BTC or $ 622 to decrypt files.
')
For more information, Yonathan left the addresses of Malvari management and distribution servers, so in corporate networks you can add this list to the blacklist:
Bedep C & C:
TeslaCrypt C & C:

As a source in his blog ( Yonathan Klijnsma ) describes , certain users from certain countries were attacked, namely:
- Visitors using Microsoft Internet Explorer as a browser (or using an Internet Explorer user agent)
- Visitors referred by Google or Bing search engines.
- Used IP block list and geolocation by IP.
After redirecting from the pages of the site, the victim ended up at the Angler exploit kit page, where flash or silverlight components are used to exploit the vulnerability. Angler exploit kit first launches the Bedep Trojan on the victim's machine, which loads the last payload payload.
As described in the source, the EC Council website most likely uses the well-known CMS Wordpress with a vulnerable module, which turned out to be full of holes and led to infection.
After infection, TeslaCrypt requires the victim 1.5 BTC or $ 622 to decrypt files.
')
For more information, Yonathan left the addresses of Malvari management and distribution servers, so in corporate networks you can add this list to the blacklist:
Bedep C & C:
- 89.163.240.118 / kjnoa9sdi3mrlsdnfi [.] Com
- 85.25.41.95 / moregoodstafsforus [.] Com
- 89.163.241.90 / jimmymorisonguitars [.] Com
- 162.244.32.121 / bookersmartest [.] Xyz
TeslaCrypt C & C:
- 50.87.127.96 / mkis [.] Org
- 213.186.33.104 / tradinbow [.] Com
Source: https://habr.com/ru/post/280139/
All Articles