Comprehensive Information Security: a Binary Overview of the Fortinet Line
Hello! Below, there will be an educational program for one specific line of equipment, which allows you to understand what it is, why you need (and if necessary) and what tasks are being solved (overall protection of the ICT infrastructure, implementation of locks, compliance with the Federal Law on PD).
So, today protection components usually look like a real “zoo”:
')
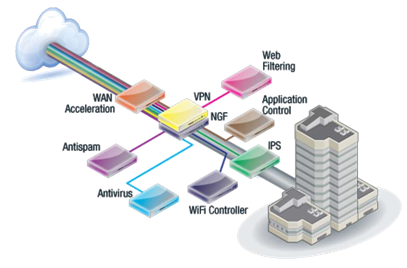
These are streaming antivirus, firewall, antispam and antididos, as well as intrusion detection systems, etc., located at the entrance to your data center. The Fortinet (as well as a number of other manufacturers) combines these devices into one piece of hardware, plus reviews the concept of protection in principle. They have been leading Gartner for 7 years in the UTM segment (FW + IPS + VPN + Application Control + WebFiltering + Antispam + Antivirus and other functions).
Their idea is that the perimeter is not on the border with the public Internet. If earlier protective hardware was installed at the output, then these guys think that it is necessary to put devices closer to the local network - work with WLAN and in the data center right between the machines. Naturally, this requires completely different streaming capacities, but, on the other hand, it gives a couple of huge advantages.
Solutions Fortinet is a complete complex to protect the network infrastructure, built into a single piece of hardware.
Here are the applications:
- General protection of the network, internal segment and operator's clients from network, content and application-level threats.
- Filtering requests to the Internet, including to meet the requirements of federal laws and government regulations on blocking.
- Disposal of the "zoo" subsystems.
- Protection of PD (FZ-152) in accordance with the norms of the Russian Federation.
- Integration of detection and prevention of targeted attacks.
- Protection of the PCS.
The “core” of the solution is a hardware-software complex with multiple network ports. It has three types of processors: for processing traffic (network processors), control and content processors. Managing processors distribute tasks between network and content processors, balance and generally perform system tasks. Large glands have several processors, so the tasks are fairly evenly parallelized. At the network processor level, the session is also distributed to the network coprocessors each time. All the "chips" such as email filtering, sandboxes and other things are on the content processors. If to use a piece of iron as usual NGFW, it is close to the declared synthetic results. If you begin to load with rules (especially difficult ones, such as “not allowing employees to disclose confidential information on the forum”), content processors will predictably consume power.
The security approach is systemic: all network events are collected, correlated and treated as a chain of interactions. For example, one of the most interesting practical tasks - banning torrents in banks - is done on the basis of the decisions of the Fortinet very quickly and very funny.
The story is this: we had one bank in which sly users downloaded torrents. At first they used their standard proxy mechanics, but there were several problems. Starting from the need to disassemble SSL (which is not very real) and ending with the fact that the very same TCP over DNS was not taken by any proxy. And from time to time, letters from American copyright holders came to the bank (they say, what are you, bastards, create, this was our film).
A year later, UTM was installed there and NLFW blocking torrent sessions was set up as a test for NGFW. FortiGate is able to block P2P client traffic by establishing relationships between user behavior and subsequent h2k signs of P2P. Here, for example, is about how to solve this issue for the company once and for all. By the way, another traditional way of circumventing proxies and classic user control solutions is being worked out - Translate. Google, the best anonymizer.
So, in order to process the entire flow inside the data center, the first thing that is required is hardware with a much higher performance than the usual “outgoing” ones. The claimed synthetic characteristics of their iron are simply enormous. Naturally, there is a nuance here about synthetics (will be lower), and not one.
In general, the infrastructure uses a distributed approach to security. At each node (more precisely, the final machine) put the client. Clients process data and send events to the main server with UTM, which handles traffic. Suspicious objects from client machines automatically go into the sandbox, clients integrate themselves with the same anti-spam (they follow the links themselves, give themselves attachments to the antivirus and into the sandbox, and so on) - in general, they do everything that they should do ideally.

Types of protection, then we will talk mainly about the left version of the architecture
While the main thing - the Fortinet quickly grinds good flows. For example, UDP is “milled” at speeds of 52 Gb / s at mid-range quite normally, while the closest analogues are the same boxes at approximately the same prices, only working at 2 Gb / s.
The second feature is that this manufacturer has everything to protect. That is, they close everything at once, if you need. Here is their complete set of solutions:

All your: antivirus, VPN, database protection solution, access points, routers, switches
They even have their phone gateways. From the latter, it turned out that it was very successful that they could have their own external 3G / LTE extenders attached to their glands. Actually, one Fortigate firewall can be the controller of access points, and already it is the module of an external antenna, which is defined as a normal interface.
Previously, when banks dropped the main channel, the reserve often in remote regions was a “whistle” of one of the operators - with appropriate dances with a tambourine for integration into security or specifically a sagging level of protection for the time of the channel change (without input filtering, for example). And here everything is in one box, and do not bother with compatibility. This is also a plus, because, for example, Huawei (where Tsisk used to be) takes everything to small branches, and not everything works exactly as it should (the difference in realizations makes itself felt).
First of all, the Fortinet line is viewed either by companies that are regularly attacked, or by various traffic operators, for example, solutions of this group are deployed by Amazon and LTE operators to clear traffic. In general, the "zoo" introductions like this:

Plus, another 50 carriers from Verizon and T-Mobile to China Telecom and Vodafone.
Despite these "monsters", more than a third of Fortinet sales in 2015 are SMB and low-end hardware. Small and medium business is also interesting due to the fact that a lot of different hardware, such as routers, NGFW, WLC, etc., can now be on the same piece of hardware. It makes sense to take those who open new branches, for example.
Here are their Gartner counterparts:

The differences "on the fingers" from the analogs are that the FortyNet gives a generally high standard for the market in terms of channel protection, is only licensed for the device and allows you to distribute the power as you please. When new functions are connected, performance of all these solutions decreases, while Fortinet’s behavior when using additional functions is more predictable due to load optimization by hardware coprocessors.
Fortinet offers quite cost-effective solutions compared to similar equipment from other manufacturers. For large businesses, the main “point” of comparison is the price per unit of traffic, for small and medium ones, functionality. Other vendors often have the same feature set that requires a very expensive piece of hardware.
Until I became quite happy, I’ll tell you what you need to know in advance about the features of this architecture and specific solutions:
This is a high end iron that pays off at the expense of better cost of ownership on large infrastructures. It has predictable performance (compared to competitors), has extensive support for virtual infrastructures (ESXi, Xen, KVM, Hyper-V, as well as cloud Azure and AWS), a large number of supported hypervisors, a bunch of different types of protection. However, I note: when determining the budget or setting up the rules, mandatory tests are required prior to implementation.
On March 30, we will have a webinar on information security based on Fortinet solutions. Who cares - connect .
So, today protection components usually look like a real “zoo”:

')
These are streaming antivirus, firewall, antispam and antididos, as well as intrusion detection systems, etc., located at the entrance to your data center. The Fortinet (as well as a number of other manufacturers) combines these devices into one piece of hardware, plus reviews the concept of protection in principle. They have been leading Gartner for 7 years in the UTM segment (FW + IPS + VPN + Application Control + WebFiltering + Antispam + Antivirus and other functions).
Their idea is that the perimeter is not on the border with the public Internet. If earlier protective hardware was installed at the output, then these guys think that it is necessary to put devices closer to the local network - work with WLAN and in the data center right between the machines. Naturally, this requires completely different streaming capacities, but, on the other hand, it gives a couple of huge advantages.
Solvable tasks
Solutions Fortinet is a complete complex to protect the network infrastructure, built into a single piece of hardware.
Here are the applications:
- General protection of the network, internal segment and operator's clients from network, content and application-level threats.
- Filtering requests to the Internet, including to meet the requirements of federal laws and government regulations on blocking.
- Disposal of the "zoo" subsystems.
- Protection of PD (FZ-152) in accordance with the norms of the Russian Federation.
- Integration of detection and prevention of targeted attacks.
- Protection of the PCS.
Architectural opportunities
The “core” of the solution is a hardware-software complex with multiple network ports. It has three types of processors: for processing traffic (network processors), control and content processors. Managing processors distribute tasks between network and content processors, balance and generally perform system tasks. Large glands have several processors, so the tasks are fairly evenly parallelized. At the network processor level, the session is also distributed to the network coprocessors each time. All the "chips" such as email filtering, sandboxes and other things are on the content processors. If to use a piece of iron as usual NGFW, it is close to the declared synthetic results. If you begin to load with rules (especially difficult ones, such as “not allowing employees to disclose confidential information on the forum”), content processors will predictably consume power.
The security approach is systemic: all network events are collected, correlated and treated as a chain of interactions. For example, one of the most interesting practical tasks - banning torrents in banks - is done on the basis of the decisions of the Fortinet very quickly and very funny.
The story is this: we had one bank in which sly users downloaded torrents. At first they used their standard proxy mechanics, but there were several problems. Starting from the need to disassemble SSL (which is not very real) and ending with the fact that the very same TCP over DNS was not taken by any proxy. And from time to time, letters from American copyright holders came to the bank (they say, what are you, bastards, create, this was our film).
A year later, UTM was installed there and NLFW blocking torrent sessions was set up as a test for NGFW. FortiGate is able to block P2P client traffic by establishing relationships between user behavior and subsequent h2k signs of P2P. Here, for example, is about how to solve this issue for the company once and for all. By the way, another traditional way of circumventing proxies and classic user control solutions is being worked out - Translate. Google, the best anonymizer.
Deep integration into the data center
So, in order to process the entire flow inside the data center, the first thing that is required is hardware with a much higher performance than the usual “outgoing” ones. The claimed synthetic characteristics of their iron are simply enormous. Naturally, there is a nuance here about synthetics (will be lower), and not one.
In general, the infrastructure uses a distributed approach to security. At each node (more precisely, the final machine) put the client. Clients process data and send events to the main server with UTM, which handles traffic. Suspicious objects from client machines automatically go into the sandbox, clients integrate themselves with the same anti-spam (they follow the links themselves, give themselves attachments to the antivirus and into the sandbox, and so on) - in general, they do everything that they should do ideally.

Types of protection, then we will talk mainly about the left version of the architecture
While the main thing - the Fortinet quickly grinds good flows. For example, UDP is “milled” at speeds of 52 Gb / s at mid-range quite normally, while the closest analogues are the same boxes at approximately the same prices, only working at 2 Gb / s.
The second feature is that this manufacturer has everything to protect. That is, they close everything at once, if you need. Here is their complete set of solutions:

All your: antivirus, VPN, database protection solution, access points, routers, switches
They even have their phone gateways. From the latter, it turned out that it was very successful that they could have their own external 3G / LTE extenders attached to their glands. Actually, one Fortigate firewall can be the controller of access points, and already it is the module of an external antenna, which is defined as a normal interface.
Previously, when banks dropped the main channel, the reserve often in remote regions was a “whistle” of one of the operators - with appropriate dances with a tambourine for integration into security or specifically a sagging level of protection for the time of the channel change (without input filtering, for example). And here everything is in one box, and do not bother with compatibility. This is also a plus, because, for example, Huawei (where Tsisk used to be) takes everything to small branches, and not everything works exactly as it should (the difference in realizations makes itself felt).
Who needs
First of all, the Fortinet line is viewed either by companies that are regularly attacked, or by various traffic operators, for example, solutions of this group are deployed by Amazon and LTE operators to clear traffic. In general, the "zoo" introductions like this:

Plus, another 50 carriers from Verizon and T-Mobile to China Telecom and Vodafone.
Despite these "monsters", more than a third of Fortinet sales in 2015 are SMB and low-end hardware. Small and medium business is also interesting due to the fact that a lot of different hardware, such as routers, NGFW, WLC, etc., can now be on the same piece of hardware. It makes sense to take those who open new branches, for example.
Here are their Gartner counterparts:

The differences "on the fingers" from the analogs are that the FortyNet gives a generally high standard for the market in terms of channel protection, is only licensed for the device and allows you to distribute the power as you please. When new functions are connected, performance of all these solutions decreases, while Fortinet’s behavior when using additional functions is more predictable due to load optimization by hardware coprocessors.
What is profitable
Fortinet offers quite cost-effective solutions compared to similar equipment from other manufacturers. For large businesses, the main “point” of comparison is the price per unit of traffic, for small and medium ones, functionality. Other vendors often have the same feature set that requires a very expensive piece of hardware.
Underwater rocks
Until I became quite happy, I’ll tell you what you need to know in advance about the features of this architecture and specific solutions:
- Licensing for glands, that is, you buy power (processors) and do what you want. Naturally, there is a desire to load the security server with a bunch of functions - and at the time of implementation it will grind everything. With the growth of traffic and requirements, performance will fall, and you will need to disable some of the functionality. Therefore, it is very important to test the device on real tasks and take stock with an understanding of its traffic growth, the growth of their signature base, and so on. A typical story known to me: at first admins include everything at once (as in that joke about a Finnish chainsaw), then they wait for the piece of iron to gobble up everything. And load more. When the saw says "hrrr", disable some of the functions. So they live.
- Scaling - by purchasing new pieces of iron (new models) or building a cluster of old ones. Immediately calculate these options for three years in advance, so that prices do not come as a surprise. The old piece of iron does not upgrade, only sold, thrown out or placed in a cluster.
- There is a valid FSTEC certificate, as well as a decision to certify a new line of devices. The second ambush for those working with PDs is to update the signature database. The power of the solution is to constantly receive data, so “filling up and leaving” will not work, this is not suitable for all banks.
- Complete hardware bypass made a separate decision. True, other vendors usually have none at all.
- There is an SSL parsing according to the MitM scheme with the import of “native” certificates (with the possibility of traffic signing) or setting up self-signed on the device. After decryption, all the same is checked as usual. SSL strip loads processors, so, despite the fact that no additional devices are needed, this separate process in FortiOS will eat quite a lot of resources. However, you can do SSL-Offload to an external descrambler, if you do not want to use the firewall itself for these tasks.
- Naturally, we should not forget that regular mode implies sending suspicious traffic to their analysis centers, but neither the vednor nor the integrator has the right to enable this option without direct coordination with you if you do not want to share your SSL content.
Summary
This is a high end iron that pays off at the expense of better cost of ownership on large infrastructures. It has predictable performance (compared to competitors), has extensive support for virtual infrastructures (ESXi, Xen, KVM, Hyper-V, as well as cloud Azure and AWS), a large number of supported hypervisors, a bunch of different types of protection. However, I note: when determining the budget or setting up the rules, mandatory tests are required prior to implementation.
On March 30, we will have a webinar on information security based on Fortinet solutions. Who cares - connect .
Links
- You can try their hardware in the form of virtual machines (they provide an image 1–2 days after the application) - russia@fortinet.com, documentation - docs.fortinet.com. We, as their official partner, can help with the pilot implementation of real equipment.
- Basic solution architecture description
- Presentation about the company and its strategy; presentation on solutions ; speech at the UCLR webinar on Fortinet solutions; speech about telecoms operators ; all aspects of replacing Microsoft TMG .
- Ponty: certification against targeted attacks - ATP certification from NSS Labs (best rating - Recommended) and ICSA ; NSS Labs recommended status by NGFW ; Virus Bulletin ranked antispam as one of the best ; Virus Bulletin ranked antivirus streaming as one of the best ; IPS has the highest rating from NSS Labs.
- Implementations , MSSP knowledge base (a huge amount of materials for starting a business for telecom operators), filtering url solution according to Roskomnadzor lists. And a couple of examples: here and here .
- Product Matrix ( PDF )
- Write to my AVrublevsky@croc.ru mail with questions (in particular, I can help with experience with sizing or a 3-year forecast for performance, but please send specific, specific questions).
- Yes, and I remind you once again, join the webinar on March 30.
Source: https://habr.com/ru/post/280135/
All Articles