Security Receivers demonstrate full-featured exploit for Android
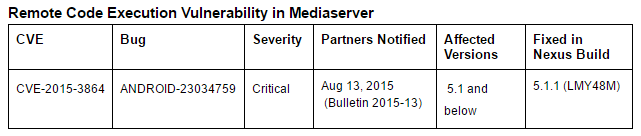
Researchers at the Israeli company NorthBit demonstrated one of the first experimental full-featured exploits for Android of all versions up to 5.1. The exploit is based on the already closed update of the Nexus Security Bulletin - September 2015 vulnerability identifier CVE-2015-3864 (Stagefright), which caused a lot of noise last year. The vulnerability was present in the Android library called Stagefright, which is used in the system component mediaserver. It allowed attackers to get full access to the device by sending a specially crafted MMS message to the user.

Exploit NorthBit called Metaphor. In addition to a detailed description of the exploitation mechanism of the vulnerability, the researchers presented vulnerabilities in Android to bypass the DEP & ASLR defense mechanisms that are used to protect against exploits relying on the location of the shell-code in the data area, and also rely on fixed addresses in Android memory for stable operation vulnerabilities. As in Windows, the traversal is performed using the well-known ROP and heap-spray methods.
')
Attack using exploit is divided into several steps.
Fig. Demonstration of the exploit Metaphor. The victim follows the link to the animal web page, where the malicious video content with the exploit is located.
According to market analysts, hundreds of millions of devices running Android work on versions of this mobile OS that are vulnerable to Metaphor. Installing Android updates for your devices is the best measure to protect against this kind of vulnerabilities, but what should users of smartphones whose manufacturers do not adapt for them are new firmware released by Google. Well, there is no definitive answer to this question yet ... We recommend users not to follow phishing links (as it was shown in the video) and use antivirus software as one of the main measures to protect their device.
A full description of the functioning of Metaphor can be found at this link .
The described vulnerability was closed by Google last September with the update of Nexus Security Bulletin - September 2015 .

Exploit NorthBit called Metaphor. In addition to a detailed description of the exploitation mechanism of the vulnerability, the researchers presented vulnerabilities in Android to bypass the DEP & ASLR defense mechanisms that are used to protect against exploits relying on the location of the shell-code in the data area, and also rely on fixed addresses in Android memory for stable operation vulnerabilities. As in Windows, the traversal is performed using the well-known ROP and heap-spray methods.
')
Attack using exploit is divided into several steps.
- At the first stage, an attack vector is selected, for example, a malicious MitM or XSS redirection, a malicious link in the message, and malicious HTTP content.
- Part of the exploit on a web page in the form of JavaScript code creates a so-called. the attack session and gets the device ID Device ID, and then sends this information to the attacker's server. This code specializes in conducting the entire subsequent operation process involving several malicious MPEG4 files.
- If the ID is necessary for the attackers, the MPEG4 video file (crash.mp4) is sent to the victim in a special way.
- Android uses the mediaserver process to play this video file, which causes the mediaserver system process to crash. Such a step is necessary for setting the process to the initial state, which will allow to correctly perform the exploitation of the vulnerability. After a crash, the process will automatically start again.
- Next, the exploit code sends a request to the remote server of the attackers to get another MPEG4 file called leak.mp4. It is required for the disclosure of Android system memory pointers and the ASLR bypass.
- The remote server, based on the device ID information sent to it by the exploit in the previous step, returns to it leak.mp4, as well as a relative offset in the system libc.so file to form the ROP gadgets and DEP bypass.
- To play leak.mp4, Android again draws on the mediaserver process, which parses fake file metadata and is used by the exploit to bypass ASLR. To bypass the ASLR, the universal method of calculating the delta through the vulnerable place of its initial formation is used on the Android-based Linux algorithm for ARM 32-bit. The result of the ASLR bypass is the successful detection in memory of the header of the executable ELF file, on the basis of which a delta is formed to calculate the absolute addresses in the process.
- At this stage, all the preparatory actions are completed and the JavaScript code queries the remote server itself for the RCE exploit for the CVE-2015-3864 vulnerability, providing it with the device ID mentioned and some additional information about the location of the Android modules in memory.
- The remote server sends the malicious code JavaScript file rce.mp4, as well as all the information about the addresses in memory necessary for successful exploitation of the vulnerability. Addresses were calculated in advance with leak.mp4.
- At the last stage, malicious JavaScript code launches rce.mp4 for execution, which leads to the triggering of a vulnerability and remote code execution. Since the exploit is performed in the context of the mediaserver system process, it gets extended privileges on Android.
Fig. Demonstration of the exploit Metaphor. The victim follows the link to the animal web page, where the malicious video content with the exploit is located.
According to market analysts, hundreds of millions of devices running Android work on versions of this mobile OS that are vulnerable to Metaphor. Installing Android updates for your devices is the best measure to protect against this kind of vulnerabilities, but what should users of smartphones whose manufacturers do not adapt for them are new firmware released by Google. Well, there is no definitive answer to this question yet ... We recommend users not to follow phishing links (as it was shown in the video) and use antivirus software as one of the main measures to protect their device.
A full description of the functioning of Metaphor can be found at this link .
The described vulnerability was closed by Google last September with the update of Nexus Security Bulletin - September 2015 .

Source: https://habr.com/ru/post/279699/
All Articles