Pwn2Own 2016: first results
The first day of the famous contest Pwn2Own 2016, which takes place in Vancouver, has ended. The competition is a platform where security resellers can demonstrate their exploits for various products, including web browsers and plugins for them. This time, the system of conducting Pwn2Own was slightly changed and the system of points for successful exploitation of vulnerabilities was introduced, and the well-known VMware Workstation virtualization software appeared in the product list.
As it is not difficult to guess, in the case of VMware Workstation, participants are invited to demonstrate a successful “escape” from a virtual machine (VM escape) and launching an exploit on a virtual machine, its code must be executed on the host. The rules stipulate that all running software, as well as the OS, must be fully updated (up-to-date).
')

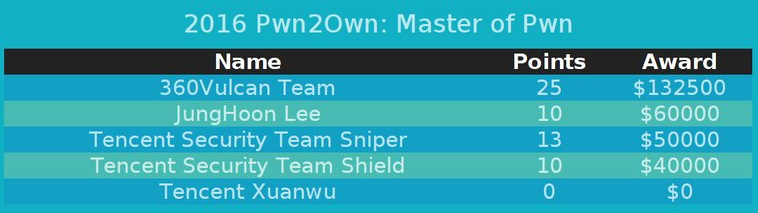
Fig. The number of points that is accrued for successful hacking of one or another software.
The points system works as follows. For example, a participant successfully demonstrated remote code execution (RCE) twice: once for Google Chrome with a sandbox bypass, and the second for Microsoft Edge with a sandbox bypass by obtaining maximum SYSTEM rights. In this case, he will be credited with 10 + 3 + 10 + 5 = 28 points. The participant with the most points is awarded the title “Master of Pwn”.
This year, the pricing for successful operation was as follows (64-bit web browsers up-to-date versions of Microsoft Windows 10, Apple OS X El Capitan). Like last time, the plug-ins did not include well-known Oracle Java software. In addition, web browsers such as Microsoft Internet Explorer 11 and Mozilla Firefox, as well as the Adobe Reader plugin were removed from the contest.
Exploits should freely bypass the mechanisms used by web browsers and their plugins to counter Windows and OS X exploits, such as DEP and ASLR, as well as sandboxing.
During the first day of the competition, exploits were successfully demonstrated for Google Chrome, Flash Player on Edge with getting SYSTEM rights in Windows 10, as well as Safari. No exploit for VMware Workstation has been demonstrated.
The rules stipulate that the exploits shown must use unknown 0day vulnerabilities that will be reported to vendors after they are demonstrated. After the release of relevant updates, vulnerability information may be publicly disclosed.

As it is not difficult to guess, in the case of VMware Workstation, participants are invited to demonstrate a successful “escape” from a virtual machine (VM escape) and launching an exploit on a virtual machine, its code must be executed on the host. The rules stipulate that all running software, as well as the OS, must be fully updated (up-to-date).
')

Fig. The number of points that is accrued for successful hacking of one or another software.
The points system works as follows. For example, a participant successfully demonstrated remote code execution (RCE) twice: once for Google Chrome with a sandbox bypass, and the second for Microsoft Edge with a sandbox bypass by obtaining maximum SYSTEM rights. In this case, he will be credited with 10 + 3 + 10 + 5 = 28 points. The participant with the most points is awarded the title “Master of Pwn”.
This year, the pricing for successful operation was as follows (64-bit web browsers up-to-date versions of Microsoft Windows 10, Apple OS X El Capitan). Like last time, the plug-ins did not include well-known Oracle Java software. In addition, web browsers such as Microsoft Internet Explorer 11 and Mozilla Firefox, as well as the Adobe Reader plugin were removed from the contest.
- Google Chrome: $ 65,000.
- Microsoft Edge: $ 65,000.
- Adobe Flash on Edge: $ 60,000.
- Apple Safari: $ 50,000.
- Getting SYSTEM or root rights: $ 20,000.
- VMware Workstation escape: $ 75,000.
Exploits should freely bypass the mechanisms used by web browsers and their plugins to counter Windows and OS X exploits, such as DEP and ASLR, as well as sandboxing.
In the case of a court of law, it is recommended that There are also ways to ensure that there is a need for data such as Data Execution Prevention (DEP), Address Space Layout Randomization (ASLR) and application sandboxing. The resulting payload should be executing in an elevated context (for example, on Windows-based targets, Medium integrity level or higher).
During the first day of the competition, exploits were successfully demonstrated for Google Chrome, Flash Player on Edge with getting SYSTEM rights in Windows 10, as well as Safari. No exploit for VMware Workstation has been demonstrated.
The rules stipulate that the exploits shown must use unknown 0day vulnerabilities that will be reported to vendors after they are demonstrated. After the release of relevant updates, vulnerability information may be publicly disclosed.
Source: https://habr.com/ru/post/279497/
All Articles