Banking Android Trojan disguises as a Flash player and bypasses 2FA authentication
Our experts have discovered a new malicious campaign to spread the banking Trojan for Android. Troyan specializes in compromising users of large banks in Australia, New Zealand and Turkey by stealing account credentials of twenty mobile banking applications. It is detected by our anti-virus products like Android / Spy.Agent.SI .

The list of banks for which the Trojan is designed to compromise users includes the largest banks of the aforementioned countries. Thanks to the SMS interception feature, malware can bypass the two-factor authentication protection mechanism. The Trojan application itself is disguised as a Flash Player, and uses the same icon for this.
')
The trojan was available for download from several servers that were publicly registered at the end of January and February 2016. It is interesting to note that URL paths to malicious APK files are generated every hour, which postpones the possibility of their detection by antivirus products.

Fig. 1. Directory with malicious program files.
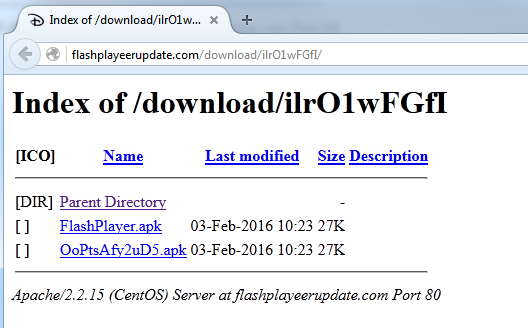
Fig. 2. Directory with malicious program files (new link).
As in some other cases of malware for Android, this banking Trojan asks to grant it administrator rights in the system during its installation. This self-defense mechanism prevents attempts to remove malware from the device. After successful installation into the system, the malware hides the Flash Player icon from the user's eyes, but continues to work in the background itself.
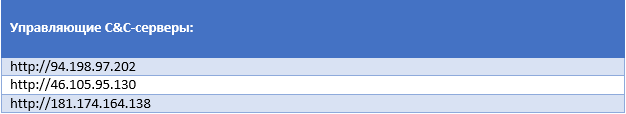
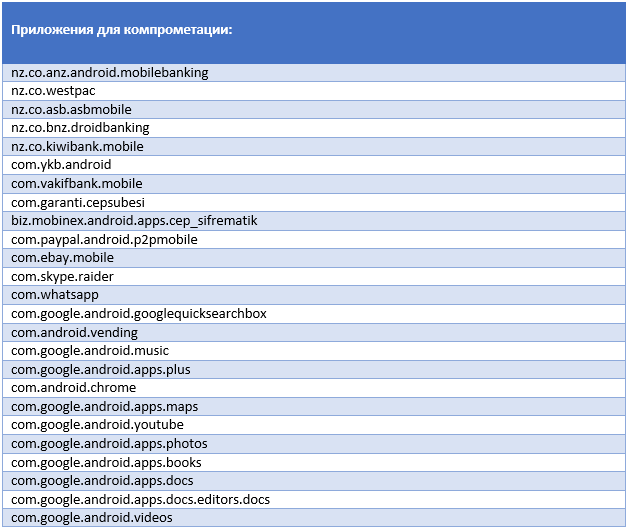
Next, the malware interacts with its remote C & C server. To hide transmitted data from prying eyes, the bot and server use base64 encoding. The malicious program sends to the server such device data as its model type, IMEI identifier, language, SDK version, and information about the activation time of device administrator rights in Android. Such information is sent to the server every 25 seconds of the malware. Then the trojan collects a list of applications installed on the device (including banking applications) and sends this list to a remote server. If a bot is configured to compromise applications, the C & C server sends it a list of 49 different applications that the attackers expect to compromise.
Troyan fulfills its functions of stealing online banking data by creating a special window that overlaps the window of a legitimate application for working with a bank account. Such phishing activity of the Trojan is similar to the activity of the extortionist, who blocks the screen of the user's device without being able to unlock it. After receiving user input, the trojan sends them to a remote server. The attackers are interested in obtaining not only the credentials of online banking accounts, but also data from Google accounts.
The first versions of the Trojan looked quite simple, while its true goals could be calculated quickly. Later versions of the malware received obfuscation and encryption mechanisms, which complicated their analysis.
When an application of malicious attackers is launched on Android, the malicious program is activated and shows the user a fake window that overlaps the banking application window.

Fig. 3. Interaction of the malicious program with the C & C server manager.
After the user types in the fake window field the login and password of the bank account, the fake window of the Trojan is closed, which causes the window of the real banking application to appear. As mentioned above, all the information sent between the bot and the server is base64 encoded, with the exception of stolen credentials, which are transmitted in clear text.
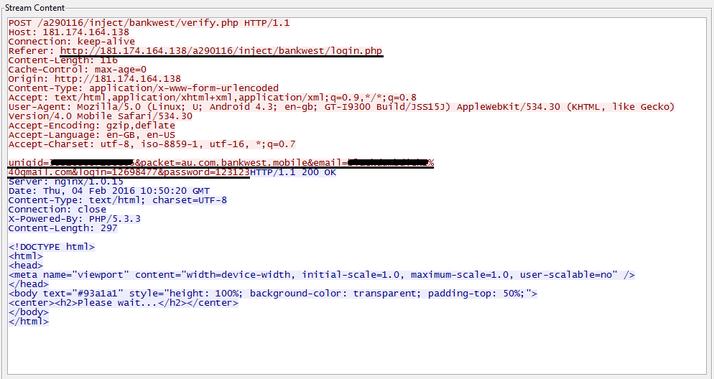
Fig. Trojan sends stolen credentials in clear text.
The malicious program can also bypass two-factor 2FA authentication by sending text SMS messages received by the device to a remote server. This allows attackers to intercept all messages from the bank in a timely manner and immediately delete them on the compromised device to hide malicious activity from the user.
Malware removal
When a user tries to remove a trojan from the system, two different scenarios are possible. First, the user can deny admin rights for the application, and then remove the fake Flash Player from the device. Deactivating admin rights for a trojan can be done in two ways. The easiest is to use the built-in Android settings Settings-> Security-> Device Administrators-> Flash Player-> Deactivate, then ignore the Trojan window that appears and click OK.
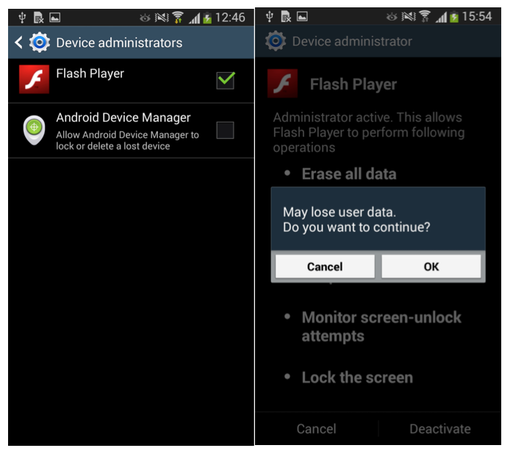
Fig. Disable device admin mode for trojan.
After that, the user has the opportunity to remove the trojan through Settings-> Application Manager-> Flash Player-> Delete.
The removal procedure can be more complicated if the bot received from the server a command to prevent the deactivation of administrator rights on the device. In this case, as soon as the user attempts to deactivate them, the malicious program will create a special overlapping window that will not allow the user to confirm the disabling of the rights.
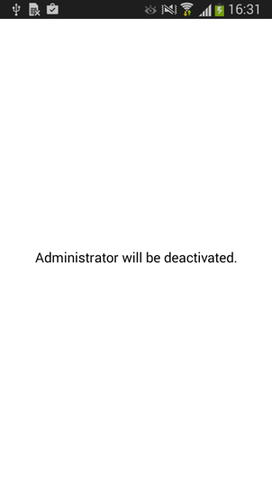
Fig. A special window that does not allow the user to confirm the revocation of administrator rights.
Another way to safely deactivate administrator rights is to use Safe Mode. When loading in safe mode, Android disables the download of third-party applications. In this case, the user can safely disable them, as in the first case. ESET antivirus products detect Trojans like Android / Spy.Agent.SI .
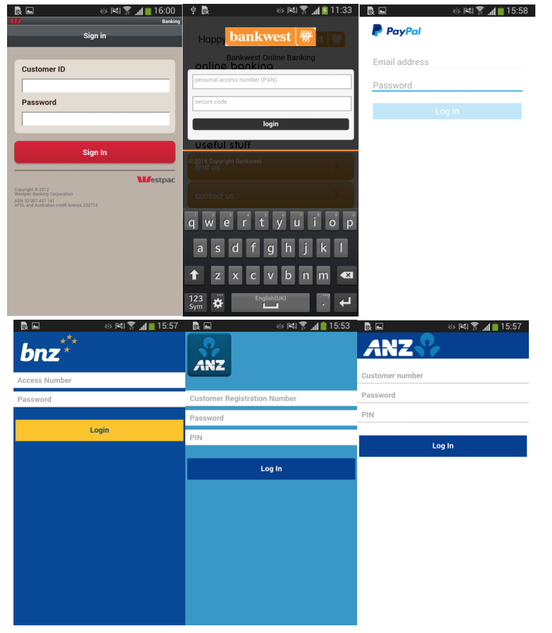
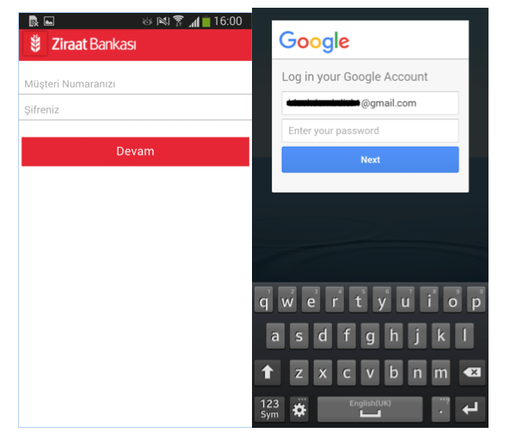
Below are the layouts of fake windows banking applications that are used by the Trojan.


Additional Information
ESET Detection:
Android / Spy.Agent.SI.

Banks whose Trojan targets compromise:
Westpac, Bendigo Bank, Commonwealth Bank, St. George Bank, National Bank of Australia, Bank of New Zealand, Bank of New Zealand, Bank of New Zealand, Wells Fargo, Halkbank, Bankruptcy Bank, Bankruptcy Bank, Bank of Aktau, Finansbank, Türkiye İş Bankası and Ziraat Bankası.


The list of banks for which the Trojan is designed to compromise users includes the largest banks of the aforementioned countries. Thanks to the SMS interception feature, malware can bypass the two-factor authentication protection mechanism. The Trojan application itself is disguised as a Flash Player, and uses the same icon for this.
')
The trojan was available for download from several servers that were publicly registered at the end of January and February 2016. It is interesting to note that URL paths to malicious APK files are generated every hour, which postpones the possibility of their detection by antivirus products.

Fig. 1. Directory with malicious program files.

Fig. 2. Directory with malicious program files (new link).
As in some other cases of malware for Android, this banking Trojan asks to grant it administrator rights in the system during its installation. This self-defense mechanism prevents attempts to remove malware from the device. After successful installation into the system, the malware hides the Flash Player icon from the user's eyes, but continues to work in the background itself.
Next, the malware interacts with its remote C & C server. To hide transmitted data from prying eyes, the bot and server use base64 encoding. The malicious program sends to the server such device data as its model type, IMEI identifier, language, SDK version, and information about the activation time of device administrator rights in Android. Such information is sent to the server every 25 seconds of the malware. Then the trojan collects a list of applications installed on the device (including banking applications) and sends this list to a remote server. If a bot is configured to compromise applications, the C & C server sends it a list of 49 different applications that the attackers expect to compromise.
Troyan fulfills its functions of stealing online banking data by creating a special window that overlaps the window of a legitimate application for working with a bank account. Such phishing activity of the Trojan is similar to the activity of the extortionist, who blocks the screen of the user's device without being able to unlock it. After receiving user input, the trojan sends them to a remote server. The attackers are interested in obtaining not only the credentials of online banking accounts, but also data from Google accounts.
The first versions of the Trojan looked quite simple, while its true goals could be calculated quickly. Later versions of the malware received obfuscation and encryption mechanisms, which complicated their analysis.
When an application of malicious attackers is launched on Android, the malicious program is activated and shows the user a fake window that overlaps the banking application window.

Fig. 3. Interaction of the malicious program with the C & C server manager.
After the user types in the fake window field the login and password of the bank account, the fake window of the Trojan is closed, which causes the window of the real banking application to appear. As mentioned above, all the information sent between the bot and the server is base64 encoded, with the exception of stolen credentials, which are transmitted in clear text.

Fig. Trojan sends stolen credentials in clear text.
The malicious program can also bypass two-factor 2FA authentication by sending text SMS messages received by the device to a remote server. This allows attackers to intercept all messages from the bank in a timely manner and immediately delete them on the compromised device to hide malicious activity from the user.
Malware removal
When a user tries to remove a trojan from the system, two different scenarios are possible. First, the user can deny admin rights for the application, and then remove the fake Flash Player from the device. Deactivating admin rights for a trojan can be done in two ways. The easiest is to use the built-in Android settings Settings-> Security-> Device Administrators-> Flash Player-> Deactivate, then ignore the Trojan window that appears and click OK.

Fig. Disable device admin mode for trojan.
After that, the user has the opportunity to remove the trojan through Settings-> Application Manager-> Flash Player-> Delete.
The removal procedure can be more complicated if the bot received from the server a command to prevent the deactivation of administrator rights on the device. In this case, as soon as the user attempts to deactivate them, the malicious program will create a special overlapping window that will not allow the user to confirm the disabling of the rights.

Fig. A special window that does not allow the user to confirm the revocation of administrator rights.
Another way to safely deactivate administrator rights is to use Safe Mode. When loading in safe mode, Android disables the download of third-party applications. In this case, the user can safely disable them, as in the first case. ESET antivirus products detect Trojans like Android / Spy.Agent.SI .
Below are the layouts of fake windows banking applications that are used by the Trojan.




Additional Information
ESET Detection:
Android / Spy.Agent.SI.


Banks whose Trojan targets compromise:
Westpac, Bendigo Bank, Commonwealth Bank, St. George Bank, National Bank of Australia, Bank of New Zealand, Bank of New Zealand, Bank of New Zealand, Wells Fargo, Halkbank, Bankruptcy Bank, Bankruptcy Bank, Bank of Aktau, Finansbank, Türkiye İş Bankası and Ziraat Bankası.



Source: https://habr.com/ru/post/279309/
All Articles