VCloud Tools: IT GRAD Experience

The essence of cloud services is that the user is given a choice of server capacities, such as a processor, memory, amount of disk space, type of network adapter and others. Cloud computing itself can be divided into three levels, namely:
- Infrastructure as a Service (IaaS);
- Platform as a Service (PaaS);
- Software as a Service (SaaS).
For providing Infrastructure as a service (IaaS), the vCloud family is responsible. The two main components of vCloud are VMware vSphere and vCloud Director. VMware vSphere is the virtualization platform itself, where cloud infrastructure services are deployed, and vCloud Director is the cloud infrastructure management center with which the administrator manages these services.
')
Using VMware vCloud Director, you can create and manage virtual machines, migrate them from another cloud, flexibly manage access rights to a pool of virtual resources, create VPN connections, configure load balancing between virtual machines and much more.
However, often the company-customer, transferring its IT infrastructure to the cloud, gets to the existing functionality a number of tools, the existence and functionality of which is not always known. An example would be VMware vShield Edge, part of VMware vCloud Director.
For a start, it is worth noting that VMware vShield Edge is an integral part of any cloud infrastructure built on VMware vCloud. As a security product, vShield Edge acts as a network gateway. Depending on custom policies, vShield Edge can allow or deny certain connections, monitor VPN sessions, perform network address translation, inspect data by source or destination port, and load balancing.
In other words, VMware vShield Edge allows you to configure services such as Stateful Firewall, VPN, DHCP, NAT, Web Load Balancing, etc. For example, here is one of the real situations: you need to combine several remote sites into a single routed network. To do this, you need to configure the VPN-tunnel, and this will help VMware vShield Edge.
The scenario is as follows: client companies need access to virtual machines in the IT-GRAD cloud using Site-to-Site VPN. Each site has a VMware EDGE server with direct Internet access.

Site A is a client company: it uses the subnet 10.64.20.0/24.
Site B is the site of IT-GRAD company: subnet 172.16.16.0/24.
In order to raise the tunnel, we will use the vCloud Director web console, which is accessible when the IaaS provider is connected to the cloud. In the settings, activate the VPN, set the name of the tunnel and its description. Then we indicate the option of connecting to the network (in our case, remote), set the subnets to which you need to organize a tunnel, and write the IP addresses of the EDGE interfaces.
An important point when configuring Site-to-Site VPN is the choice of encryption protocol. Recall that to ensure secure communication in private virtual networks, the IPSec protocol suite is used.
IPSec allows authentication and provides integrity checking and encryption of IP packets. The IKE protocol included in it is the link that unites all IPSec components into a single system, and implements the initial authentication of the parties and the exchange of their common keys.
Installation and maintenance of a VPN tunnel takes place in two stages (in two phases of IKE operation). IKE first creates a secure channel between the two nodes, called the IKE Security Association (IKE SA), and the first phase begins.
Here IKE works in the main mode - these are three bilateral exchanges between the sender and receiver. During the first exchange, the encryption algorithms and hashing functions are matched by matching the IKE SA of each node. During the second exchange, the Deffie-Hellman algorithm is used when the parties pass each other a common secret key.
Also at this stage, the nodes check each other by sending and confirming a sequence of pseudo-random numbers. During the third exchange on the encrypted IP address, the identity of the opposite side is verified.
Then the second phase begins, during which key data is generated, and the nodes agree on the policy used. This mode is set only after the first stage, when all packets of the second phase are encrypted. If the second phase is completed correctly, we can assume that the tunnel is established.
This is just one of the additional features of VMware vShield Edge. In addition, vShield Edge allows you to “raise” the software firewall, which, like any other, checks the traffic and, depending on the parameters set in the corresponding rules, blocks or allows its transmission. The order of applying the rules can be changed by simply dragging the corresponding rule with the mouse in the vCloud Director console.
The vShield Edge feature also integrates the dynamic node configuration protocol functionality. It allows you to automate the mechanism for assigning IP addresses to virtual machines connected to virtual organization networks. You can configure and manage ranges of IP addresses directly through the vCloud Director console.
Another worth noting is the DHCP service, which seriously simplifies the process of assigning IP addresses and minimizes administrative costs and errors. In the DHCP console, it is possible to create a so-called address pool, which is a container with IP addresses stored in it for issuing to virtual machines.
IP addresses are issued for a certain period: there are two parameters in the vShield Edge settings: the default lease time is 3600 seconds and the maximum time is 7200 seconds by default. If the IP address was leased to a virtual machine, it is considered busy and cannot be assigned to another node until the lease expires.
All these functions are managed from a single vCloud Director console. Detailed guides on configuring Site-to-Site IPsec VPN, Firewall, NAT, DHCP, static routing and network load balancing can be found in our blog.
Another useful VMware product is VMware vSphere Power CLI - this tool automates the routine tasks of an administrator when working with ESX servers and virtual machines. There are a lot of examples of using Power CLI: from searching for a user who deleted a virtual machine to full-featured diagnostic programs for VMware vSphere virtual infrastructure. For example, it can be used to track processor performance problems.
One of the important performance parameters is the intensity of consumption of processor resources. Suppose that in the vSphere environment too many virtual machines are running with high-load applications running on them — all of which can lead to insufficient processor resources. Sometimes the reason for this shortage is another point, connected, for example, with inefficient use or non-optimal configuration of virtual machines.
And so, the lack of CPU resources leads to serious performance problems and affects the operation of business-critical services. For example, a high Co-stoptime indicator indicates the presence of more vCPU than necessary, and this often causes additional resource consumption and reduces the performance of the virtual machine.
The Guest CPU Saturation parameter indicates the CPU load of the virtual machine: if the virtual machine application uses 90% or more CPU resources, there is a performance problem. These and many other parameters VMware vSphere Power CLI allows you to track.
When investigating problems with CPU performance, you should pay attention to the following counters:
- Demand - the number of virtual machine CPUs required for operation.
- Ready - an indicator of the time during which the virtual machine is ready to start, but cannot due to lack of physical resources.
- Usage - the number of virtual machine processors allowed for use at the moment.
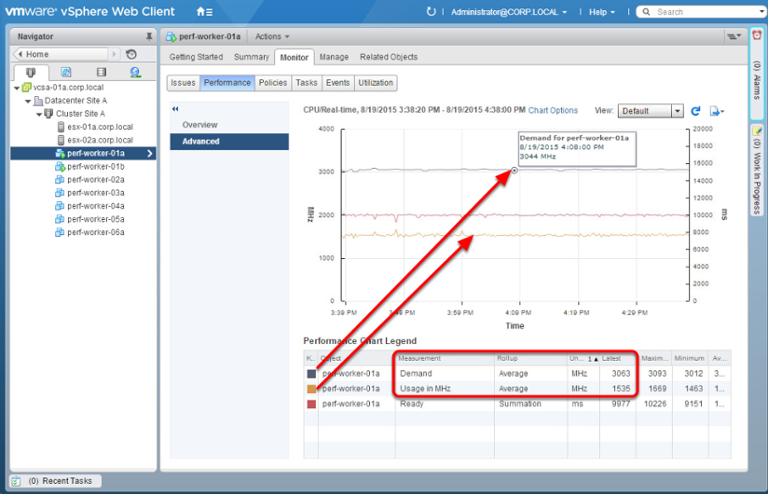
The image above shows how much CPU resources are required to run the virtual machine and how much is actually used. In this particular case, it is required (Demand) significantly more than is used (Use).
Also pay attention to the Ready Time indicator, equal to 9977 ms - this is another indicator that you should pay attention to when looking for performance problems. If this value is greater than 10%, then there is a high probability of performance problems. To convert values from milliseconds to percents, you can use the following formula:

It is important to remember that setting up virtual machines with a large number of virtual CPUs can lead to an increase in resource utilization, potentially affecting the performance of heavily loaded systems. And even if the guest operating system does not use all the dedicated virtual processors, such a machine will consume the host resources at the physical level. Detailed guidance on monitoring processor performance can be found in our corporate blog ( 1 , 2 ).
In this article, I would like to touch on another tool that has (albeit indirectly) related to the vCloud Director. It's about Veeam Backup. With it, the administrator can make backup copies of metadata and attributes of virtual services and restore virtual services and virtual machines directly in vCD.
The topic of backup was, is and will be relevant at all times. Every year, the amount of data stored on both physical and cloud platforms of various companies is constantly increasing, and this drastically changes the appearance of the backup systems market.
Veeam Cloud Connect offers a fast and reliable way to transfer backups to remote cloud sites, as well as data recovery. This decision is subject to the so-called rule "3-2-1", according to which to ensure reliable data storage , these conditions must be met:
- Have three backups;
- Use two types of storage media;
- Store one copy remotely.
Veeam Cloud Connect technology provides reliable storage of backups at remote sites of cloud service providers, comprehensive monitoring with guaranteed ability to recover data stored at remote sites directly from the backup console, the ability to use backup archiving tasks using built-in WAN acceleration and long-term policies storage.
To start using the benefits of Veeam Cloud Connect, you first need to decide on the cloud service provider Veeam, whose platform will be used as a reliable backup storage of virtual machines - such providers have the competence of Veeam Cloud Provider (VCP). In this case, any customer who has opted for backup to the cloud will need a subscription to the services from the cloud provider.
The second stage is the client-side deployment of Veeam Backup & Replication, infrastructure planning and configuration, selection and connection to remote sites of Veeam cloud providers, and so on. You can see the whole process in detail in our blog .
Source: https://habr.com/ru/post/279225/
All Articles