Extortionist KeRanger for OS X: our analysis
In our previous corporate blog post, we presented information about an extortionist for OS X called KeRanger. The KeRanger data was taken from the report of the Palo Alto Networks company, which experts were the first to report on this threat. Our analyst Anton Cherepanov also analyzed KeRanger, however, he did not have time to publish this data before the aforementioned specialists.

In this post, we will present information from the first extortioner's own research for OS X, and also describe the features of KeRanger detection using our anti-virus products. Since the authors of Transmission have released a new version of their application with the identifier 2.91, we recommend that all users of this software upgrade to this version.
')
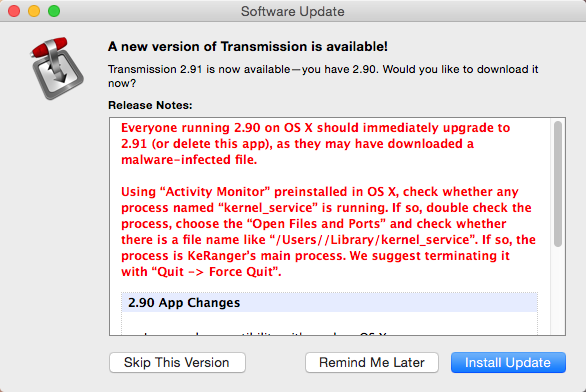
Fig. An update alert that displays an already outdated version of Transmission on OS X.
According to the above warning, which is displayed by the Transmission application itself, and is also present on the official website, version 2.90 of the application was compromised by the extortionist, so all users are invited to upgrade to the latest version 2.91.
Answers to the following questions will help users quickly understand the situation.
1. Is the KeRanger malware just an experimental version or is it designed for in-the-wild distribution?
Attackers use KeRanger for mass distribution.
2. How do attackers spread extortionist?
For distribution, the attackers chose an effective way to compromise the legitimate distributions of the Transmission application, which is a free BitTorrent client. The malicious version of the distribution was available for download from the official website between March 4 and 5, 2016. It was also signed with a legitimate digital certificate.
3. Are malicious Transmission distributions now distributed?
On March 5, a malicious version of the program was removed from the website. In addition, Apple has revoked the digital certificate used to sign it. This measure will help OS X users protect themselves from the threat of infected distributions that can be downloaded from other places.
4. I did not receive the ransom request message. Does this mean that my poppy was not compromised?
Not necessary. The in-the-wild version of KeRanger performs its destructive actions three days after the initial infection. To detect the infection of poppies in manual mode, you should check the presence of the following files on your system. If they are present, they should be removed, just like the application itself.
/Applications/Transmission.app/Contents/Resources/ General.rtf
/Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf
% HOME_DIR% / Library / kernel_service
% HOME_DIR% / Library / .kernel_pid
% HOME_DIR% / Library / .kernel_time
5. Is it possible to decrypt files without paying the ransom?
Unfortunately not. The extorter uses a pair of RSA-2048 and AES-256 cryptographic algorithms that make this process impossible.
6. How can I protect my data?
To do this, use an antivirus program. Users of ESET anti-virus products are protected from this threat, KeRanger shows up as OSX / Filecoder.KeRanger.A. We also strongly recommend that users regularly back up their data.
As we have written repeatedly, the malicious distribution kit of the application is supplied with a legitimate digital signature with the date of signing on March 4, 2016.

Fig. Information about the digital signature of a malicious application.
The signature identifier corresponds to the “POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI” line, while the legitimate application was signed with a certificate with the Digital Ignition LLC certificate identifier.
After its launch on the system, the malicious application Transmission checks the module's activity with the name kernel_service . In the absence of a file, the malicious code copies the executable file called General.rtf to the location % HOME_DIR% / Library / kernel_service and executes it.

Fig. Decompiled code of a malicious application.
The executable kernel_service file is the main part of the ransomware, which encrypts the user's files using the symmetric AES algorithm and an asymmetric RSA, and then requests a ransom for decryption. After its execution in the system, KeRanger postpones the execution of its malicious functions for three days. The time counter is located in the .kernel_time file. At the end of the time, the extortioner connects to one of the six sites hosted on the anonymous TOR network to download a text message with a ransom request, as well as a public RSA key for encrypting the AES file encryption key. Connection to the TOR is performed using the TOR2WEB public interface.
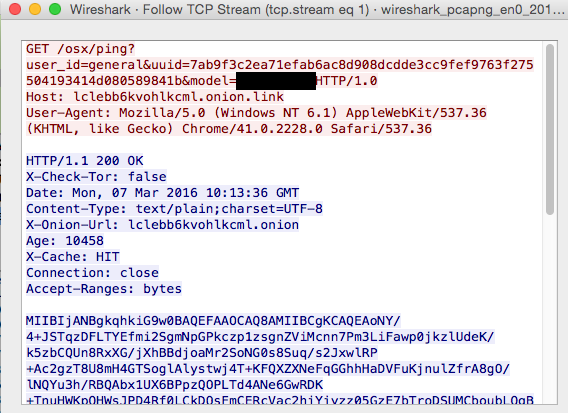
Fig. Captured ransomware OSX / Filecoder.KeRanger.A request to the managing C & C server.
The extortioner gets a list of all the files in the / Users and / Volumes directories and tries to encrypt them. For this operation, strong encryption is used — the malicious program generates a random 256-bit AES key, with which it encrypts files, then the key is encrypted using the RSA public key, after which it is stored in the body of an already encrypted file. Thus, for each file its own encryption key is generated.
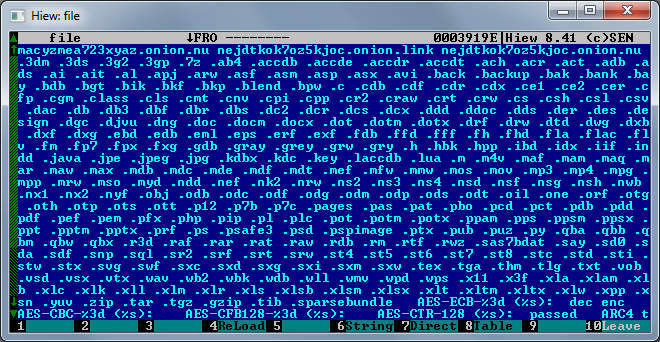
Fig. A list of file extensions that the extortionist aims to encrypt.
Extortionist specializes in encrypting more than 300 different file types, including documents, photos, videos, archives, etc. After encryption, the extension .encrypted is added to the original file name. KeRanger creates a text file with a ransom demand in each directory with encrypted files. The information for the text file is downloaded by the extortioner from the C & C server. This means that the text can be modified by attackers at any time, allowing them to change the requested ransom amount or other features. Extortionist does not block the user's desktop with such a message.

Fig. A message demanding redemption.
In order to prevent the ransomware infection, you should use the ESET Cyber Security and ESET Cyber Security Pro antivirus products, which have a regular virus signature database update mechanism to quickly respond to emerging threats. For maximum speed in response to the detection of new threats, you must enable the ESET Live Grid setting. Read more about this here . We recommend that users regularly back up their data on OS X.
Compromise identifiers
SHA-1:
5F8AE46AE82E346000F366C3EABDAFBEC76E99E9
FD1F246EE9EFFAFBA0811FD692E2E76947E82687
Addresses of C & C Servers Managers:
lclebb6kvohlkcml.onion [.] link
lclebb6kvohlkcml.onion [.] nu
bmacyzmea723xyaz.onion [.] link
bmacyzmea723xyaz.onion [.] nu
nejdtkok7oz5kjoc.onion [.] link
nejdtkok7oz5kjoc.onion [.] nu

In this post, we will present information from the first extortioner's own research for OS X, and also describe the features of KeRanger detection using our anti-virus products. Since the authors of Transmission have released a new version of their application with the identifier 2.91, we recommend that all users of this software upgrade to this version.
')

Fig. An update alert that displays an already outdated version of Transmission on OS X.
According to the above warning, which is displayed by the Transmission application itself, and is also present on the official website, version 2.90 of the application was compromised by the extortionist, so all users are invited to upgrade to the latest version 2.91.
Answers to the following questions will help users quickly understand the situation.
1. Is the KeRanger malware just an experimental version or is it designed for in-the-wild distribution?
Attackers use KeRanger for mass distribution.
2. How do attackers spread extortionist?
For distribution, the attackers chose an effective way to compromise the legitimate distributions of the Transmission application, which is a free BitTorrent client. The malicious version of the distribution was available for download from the official website between March 4 and 5, 2016. It was also signed with a legitimate digital certificate.
3. Are malicious Transmission distributions now distributed?
On March 5, a malicious version of the program was removed from the website. In addition, Apple has revoked the digital certificate used to sign it. This measure will help OS X users protect themselves from the threat of infected distributions that can be downloaded from other places.
4. I did not receive the ransom request message. Does this mean that my poppy was not compromised?
Not necessary. The in-the-wild version of KeRanger performs its destructive actions three days after the initial infection. To detect the infection of poppies in manual mode, you should check the presence of the following files on your system. If they are present, they should be removed, just like the application itself.
/Applications/Transmission.app/Contents/Resources/ General.rtf
/Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf
% HOME_DIR% / Library / kernel_service
% HOME_DIR% / Library / .kernel_pid
% HOME_DIR% / Library / .kernel_time
5. Is it possible to decrypt files without paying the ransom?
Unfortunately not. The extorter uses a pair of RSA-2048 and AES-256 cryptographic algorithms that make this process impossible.
6. How can I protect my data?
To do this, use an antivirus program. Users of ESET anti-virus products are protected from this threat, KeRanger shows up as OSX / Filecoder.KeRanger.A. We also strongly recommend that users regularly back up their data.
As we have written repeatedly, the malicious distribution kit of the application is supplied with a legitimate digital signature with the date of signing on March 4, 2016.

Fig. Information about the digital signature of a malicious application.
The signature identifier corresponds to the “POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI” line, while the legitimate application was signed with a certificate with the Digital Ignition LLC certificate identifier.
After its launch on the system, the malicious application Transmission checks the module's activity with the name kernel_service . In the absence of a file, the malicious code copies the executable file called General.rtf to the location % HOME_DIR% / Library / kernel_service and executes it.

Fig. Decompiled code of a malicious application.
The executable kernel_service file is the main part of the ransomware, which encrypts the user's files using the symmetric AES algorithm and an asymmetric RSA, and then requests a ransom for decryption. After its execution in the system, KeRanger postpones the execution of its malicious functions for three days. The time counter is located in the .kernel_time file. At the end of the time, the extortioner connects to one of the six sites hosted on the anonymous TOR network to download a text message with a ransom request, as well as a public RSA key for encrypting the AES file encryption key. Connection to the TOR is performed using the TOR2WEB public interface.

Fig. Captured ransomware OSX / Filecoder.KeRanger.A request to the managing C & C server.
The extortioner gets a list of all the files in the / Users and / Volumes directories and tries to encrypt them. For this operation, strong encryption is used — the malicious program generates a random 256-bit AES key, with which it encrypts files, then the key is encrypted using the RSA public key, after which it is stored in the body of an already encrypted file. Thus, for each file its own encryption key is generated.

Fig. A list of file extensions that the extortionist aims to encrypt.
Extortionist specializes in encrypting more than 300 different file types, including documents, photos, videos, archives, etc. After encryption, the extension .encrypted is added to the original file name. KeRanger creates a text file with a ransom demand in each directory with encrypted files. The information for the text file is downloaded by the extortioner from the C & C server. This means that the text can be modified by attackers at any time, allowing them to change the requested ransom amount or other features. Extortionist does not block the user's desktop with such a message.

Fig. A message demanding redemption.
In order to prevent the ransomware infection, you should use the ESET Cyber Security and ESET Cyber Security Pro antivirus products, which have a regular virus signature database update mechanism to quickly respond to emerging threats. For maximum speed in response to the detection of new threats, you must enable the ESET Live Grid setting. Read more about this here . We recommend that users regularly back up their data on OS X.
Compromise identifiers
SHA-1:
5F8AE46AE82E346000F366C3EABDAFBEC76E99E9
FD1F246EE9EFFAFBA0811FD692E2E76947E82687
Addresses of C & C Servers Managers:
lclebb6kvohlkcml.onion [.] link
lclebb6kvohlkcml.onion [.] nu
bmacyzmea723xyaz.onion [.] link
bmacyzmea723xyaz.onion [.] nu
nejdtkok7oz5kjoc.onion [.] link
nejdtkok7oz5kjoc.onion [.] nu
Source: https://habr.com/ru/post/278749/
All Articles