First extortionist discovered for Apple OS X
Experts from Palo Alto Networks discovered the first real extortionist (ransomware) for Apple OS X. The malware was named KeRanger and is detected by our anti-virus products as OSX / Filecoder.KeRanger.A . KeRanger is a crypto-ransomware or filecoder type that specializes in encrypting user files with a further demand for decryption.

To spread a malicious program, attackers chose an effective way to compromise software distributions called Transmission for OS X. This program is a simple, freely available BitTorrent client. A few days ago, two Transmission v2.90 distributions were compromised by KeRanger and distributed on the client’s official website. Since Transmission is free software, attackers could simply compile a special backdoored version and replace it with the developer’s server. In addition, the compromised distribution was signed by a legitimate digital developer certificate for Mac.
')
Fig. Compromised Transmission distribution on the official website. (Palo Alto Networks data)
Since the file is provided with a legitimate digital signature, malware can successfully bypass the Apple Gatekeeper security software check. After installing the compromised application, malicious code is activated on the user's computer. After that, KeRanger waits for three whole days before the first connection with its C & C server manager, using an anonymous Tor network. Such a trick masks the presence of the extortioner after the direct compromise of the user.
After connecting to C & C, KeRanger initiates the process of encrypting certain types of user files on the computer. To decrypt files, attackers require a one-bitcoin ransom (about $ 400). In addition to this, KeRanger tries to encrypt backup files to prevent the user from being able to recover his data from them.
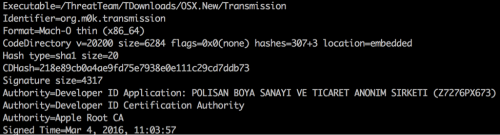
Fig. Information about the digital signature of the malicious distribution. The files were signed on March 4th. (Palo Alto Networks data)
As we already mentioned, both of the compromised distributions were signed with a legitimate digital certificate issued by Apple. The developer ID in this digital certificate is "POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI (Z7276PX673)", which differs from the similar identifier used to sign previous legitimate versions of Transmission.
The compromised distribution kit contains an additional file called General.rtf, located on the Transmission.app/Contents/Resources path. This file is an executable Mach-O format, but to hide it, it uses the RTF document icon. The executable file is packaged using UPX version 3.91. When a user launches infected distributions for execution, the built-in legitimate Transmission.app/Content/MacOS/Transmission application copies the General.rtf file to the ~ / Library / kernel_service location and executes the “kernel_service” file before the user starts using the GUI.

Fig. Badges of malicious objects in the distribution. (Palo Alto Networks data)
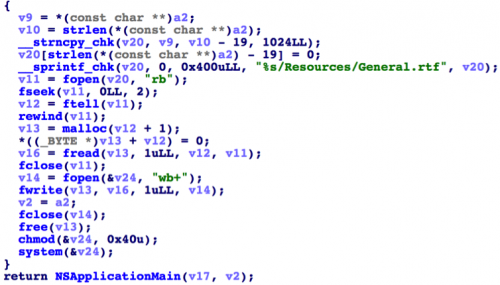
Fig. The KeRanger code executes referred to General.rtf, which specializes in file encryption and ransom requests. (Palo Alto Networks data)
The malware specializes in encrypting more than three hundred file types, including the following:

Fig. Request for ransom, which was received by the extortionist from the C & C server. (Palo Alto Networks data)
Encrypted KeRanger files receive the additional extension .encrypted to the already existing name. To encrypt files, a procedure similar to Windows encryption is used; that is, it uses symmetric AES and asymmetric RSA encryption algorithms. The encryption function is listed below. To decrypt files, you need to get a private RSA key, with which you can decrypt the symmetric AES key stored in the body of each file.
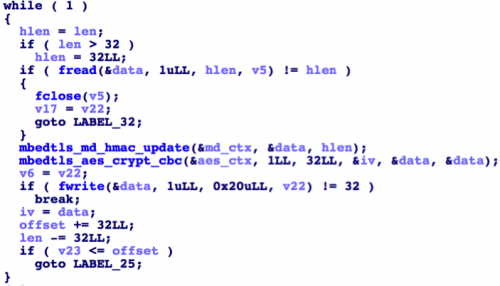
Fig. File encryption feature using AES.
Conclusion
The digital certificate that was used to sign the malicious files has already been revoked by Apple, and the security software Gatekeeper already detects the KeRanger files. The authors of the Transmission Project were also notified of the incident and the compromised distributions were deleted from the server. Apple added KeRanger signatures to its XProtect security tool, with the corresponding updates automatically received by Macs.

To spread a malicious program, attackers chose an effective way to compromise software distributions called Transmission for OS X. This program is a simple, freely available BitTorrent client. A few days ago, two Transmission v2.90 distributions were compromised by KeRanger and distributed on the client’s official website. Since Transmission is free software, attackers could simply compile a special backdoored version and replace it with the developer’s server. In addition, the compromised distribution was signed by a legitimate digital developer certificate for Mac.
')

Fig. Compromised Transmission distribution on the official website. (Palo Alto Networks data)
Since the file is provided with a legitimate digital signature, malware can successfully bypass the Apple Gatekeeper security software check. After installing the compromised application, malicious code is activated on the user's computer. After that, KeRanger waits for three whole days before the first connection with its C & C server manager, using an anonymous Tor network. Such a trick masks the presence of the extortioner after the direct compromise of the user.
After connecting to C & C, KeRanger initiates the process of encrypting certain types of user files on the computer. To decrypt files, attackers require a one-bitcoin ransom (about $ 400). In addition to this, KeRanger tries to encrypt backup files to prevent the user from being able to recover his data from them.

Fig. Information about the digital signature of the malicious distribution. The files were signed on March 4th. (Palo Alto Networks data)
As we already mentioned, both of the compromised distributions were signed with a legitimate digital certificate issued by Apple. The developer ID in this digital certificate is "POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI (Z7276PX673)", which differs from the similar identifier used to sign previous legitimate versions of Transmission.
The compromised distribution kit contains an additional file called General.rtf, located on the Transmission.app/Contents/Resources path. This file is an executable Mach-O format, but to hide it, it uses the RTF document icon. The executable file is packaged using UPX version 3.91. When a user launches infected distributions for execution, the built-in legitimate Transmission.app/Content/MacOS/Transmission application copies the General.rtf file to the ~ / Library / kernel_service location and executes the “kernel_service” file before the user starts using the GUI.

Fig. Badges of malicious objects in the distribution. (Palo Alto Networks data)

Fig. The KeRanger code executes referred to General.rtf, which specializes in file encryption and ransom requests. (Palo Alto Networks data)
The malware specializes in encrypting more than three hundred file types, including the following:
- Documents: .doc, .docx, .docm, .dot, .dotm, .ppt, .pptx, .pptm, .pot, .potx, .potm, .pps, .ppsm, .ppsx, .xls, .xlsx, .xlsm, .xlt, .xltm, .xltx, .txt, .csv, .rtf, .tex
- Images: .jpg, .jpeg
- Audio and video: .mp3, .mp4, .avi, .mpg, .wav, .flac
- Archives: .zip, .rar., .Tar, .gzip
- Source code: .cpp, .asp, .csh, .class, .java, .lua
- Databases: .db, .sql
- Emails: .eml
- Certificates: .pem.

Fig. Request for ransom, which was received by the extortionist from the C & C server. (Palo Alto Networks data)
Encrypted KeRanger files receive the additional extension .encrypted to the already existing name. To encrypt files, a procedure similar to Windows encryption is used; that is, it uses symmetric AES and asymmetric RSA encryption algorithms. The encryption function is listed below. To decrypt files, you need to get a private RSA key, with which you can decrypt the symmetric AES key stored in the body of each file.

Fig. File encryption feature using AES.
Conclusion
The digital certificate that was used to sign the malicious files has already been revoked by Apple, and the security software Gatekeeper already detects the KeRanger files. The authors of the Transmission Project were also notified of the incident and the compromised distributions were deleted from the server. Apple added KeRanger signatures to its XProtect security tool, with the corresponding updates automatically received by Macs.
Source: https://habr.com/ru/post/278725/
All Articles