Hacker has published data of SIM-cards and accounts of 3 million subscribers of a major African operator
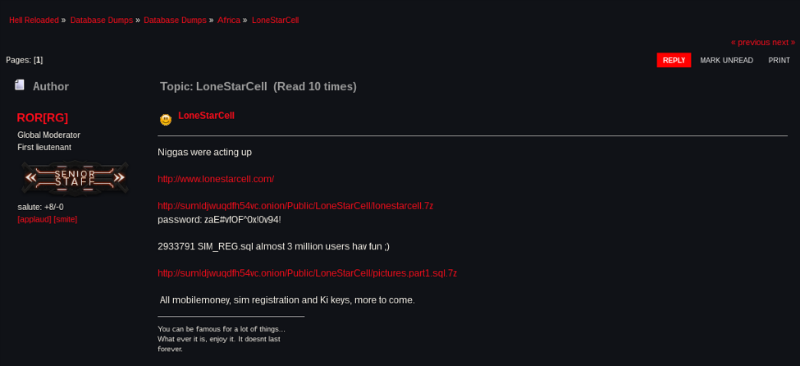
The Tor network has a link to an archive containing registration data and financial information of 3 million subscribers of Liberia’s largest telecommunications operator Lonestar Cell.
A hacker under the nickname ROR [RG] posted on one of the forums a link and a password to access the archive - according to him, using this data, you can access the mobile accounts of the operator’s users, as well as their individual identification keys and SIM card credentials. ROR [RG] clarified that the archive does not contain all the information that he managed to steal from the operator’s network.
')
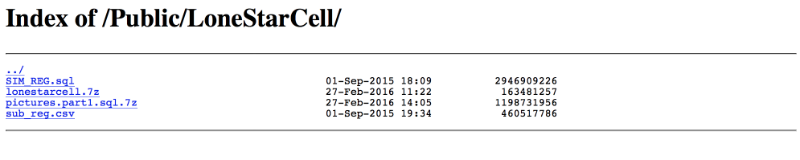
Lonestar Cell, headquartered in Monrovia, is Liberia’s largest telecom operator. The company is a subsidiary of the South African MTN Group. Representatives of Lonestar Cell have not yet commented on the situation.
Information about hacking is distributed not only on the Tor network, but also, for example, on Reddit , whose users have expressed interest in getting an invite to the forum, where the data stolen from the operator is posted.
Hacker ROR [RG] is not the first to be in the center of a scandal with a massive hacking and data theft. In the spring of last year, he put up a database with data of 4 million adult dating service users Adult Friend Finder - the hacker estimated this information at 70 bitcoins (approximately $ 16,800 at the exchange rate for May 2015).
In the same announcement, ROR [RG], who stated that he lives in Thailand, offered his services in hacking corporate resources to anyone for 750 Bitcoins ($ 180 thousand at the exchange rate at that time).
Hacking Lonestar Cell is not the first incident involving an attack on subscribers of large cellular operators. Earlier in the press got information that the hacking of mobile communication was engaged, in particular, the NSA. We also published technical details of the history of tapping Ukrainian subscribers, allegedly carried out from the territory of Russia. At the Positive Hack Days forum in Moscow, held in May 2015, a competition on mobile phone hacking was also published - you can read more about it here ( click here for the webinar recording on this topic).
At conferences on information security, Positive Technologies researchers also demonstrated the results of a study on the security of 4G communications and SIM cards (they can also be hacked ).
The network of the mobile operator, like any other, is potentially vulnerable. Due to the specificity of mobile networks, attacks in them may be more sophisticated than attacks on the Internet.
Mobile Technologies experts recommend Positive Technologies to conduct events to protect their systems according to the traditional scenario: pentest with the identification of problem areas, security audits with the installation of recommended settings, periodic testing of security settings in accordance with the template. This is the necessary minimum amount of work that will help raise the level of security of the operator’s network. In turn, subscribers who suspect that their SIM card has been cloned should immediately contact the communications salon to replace it with a new one.
Source: https://habr.com/ru/post/278221/
All Articles