Security Week 08: Mice theft through a whistle, Blockbuster operation, Linux Mint with backdoor
 In addition to the news items of the week indicated in the title, the story continues with the opposition of Apple and the FBI, or more precisely, the struggle between vendors and the state in the field of legislation. I wrote about this in more detail in the previous digest , in the comments to which one significant doubt was noted about the importance of this topic. Say, what's the difference, Apple will be forced to write a backdoor to its own device or not? The CIA (NSA, other three-letter combinations) will break anyway, and so on, without a trial.
In addition to the news items of the week indicated in the title, the story continues with the opposition of Apple and the FBI, or more precisely, the struggle between vendors and the state in the field of legislation. I wrote about this in more detail in the previous digest , in the comments to which one significant doubt was noted about the importance of this topic. Say, what's the difference, Apple will be forced to write a backdoor to its own device or not? The CIA (NSA, other three-letter combinations) will break anyway, and so on, without a trial.Can the CIA (NSA, etc.) hack iPhones or not — we don’t know and never know for certain. But the essence of the conflict lies in the fact that Apple is trying to get to "break" their own smartphone on their own. The company resists, speaking (not directly, of course) for the division of labor: Apple’s task is to protect the personal data of its customers (from anyone) as much as possible, the task of special services is to ensure that the defense does not interfere with the investigation of crimes. This is stated in the Apple petition filed yesterday - the previously publicly stated claims are legalized there. Most importantly: according to Apple, the FBI is asking for too much. A typical court action is to require the company to give what it already has (data from iCloud, logs, software source codes). But in this case, Apple is demanding the creation of something new - a tool for hacking the phone, which the company had not previously. Apple called this backdoor GovtOS (or GosA if you want).
The situation was also determined with possible consequences for the industry. On the one hand, if Apple is forced to make a backdoor, it will set a precedent for other similar requests, and not only in the United States. As it turned out, requests for at least ten Apple devices are already under consideration, where the court requires Apple to break its defense. On the other hand, regardless of the outcome of legal battles, this case may force Apple to solve the problem with the help of technology, namely, to change the software and hardware of future devices so that the manufacturer in principle will not be able to obtain user data. Not at all. The New York Times writes , citing anonymous sources, that work has already begun.
')
And now to the other news. All issues of digest - here .
Multiple vulnerabilities in wireless mice allow you to gain complete control over a computer remotely
News Details of the research on the Bastille Networks website.
We are stitching news to the case in two categories: “Trouble came, from where it was not expected” and “Never has happened before, and here again.” In short, seven different manufacturers, including Lenovo, Dell, Microsoft and Logitech, found a series of vulnerabilities in wireless mice. In combination, they allow you to remotely connect to a computer without the user's permission, transfer keystrokes and mouse movements, and thus, potentially, gain complete control over the system. In a sense, there is no need to infect a computer with a virus, if the virus code can be remotely “dialed” and executed directly on the victim's system, without demand and at a very fast pace. Vulnerabilities are not susceptible to Bluetooth mice, but devices with their own receiver and proprietary wireless data transfer protocol. This means that it is not limited to mice: if you have a wireless keyboard with a USB receiver, and you can theoretically connect a mouse to the receiver too, then you have problems. The list of susceptible devices has also been posted by investigators.

How did that happen? Very simple. Requirements for the safety of data transfer to mice were lower than to keyboards. Specialists from Bastille Networks have found that the traffic between the keyboard and the computer is almost always encrypted, while the data exchange between the computer and the mouse is not encrypted. Apparently because the interception of keystrokes gives very dangerous information, and the mouse movements themselves do not reveal anything. Then it turned out that you can connect to the receivers without any demand. In theory, adding new devices should occur only in a special pairing mode, but in fact this restriction can be circumvented. Finally, by marking your device with a mouse, you can transfer keystrokes to the computer, and the receiver will accept these presses, despite the oddity of this situation.
Well, then it is clear. We find a vulnerable receiver nearby (up to one hundred meters), connect, pass Ctrl-Esc, cmd, and so on and so forth. It turns out extremely dangerous thing, which, although it does not allow to monitor the user, but in the "write only" mode can be a way to gain complete control over the system. The study notes that not all devices can in principle be “repaired”. And only Logitech has provided a solution to the problem.
Operation Blockbuster helped uncover the activities of the Lazar Group, including those responsible for the attack on Sony Pictures Entertainment
News Research "Laboratories". Joint report of all companies participating in the investigation.
Hacking Sony Pictures Entertainment has become one of the most discussed information security news of 2014, and is still a kind of reference case for demonstrating the consequences of an attack: huge monetary losses, loss of reputation, leakage of a huge array of private data, inaccessibility of services, external and internal, for a long time. Naturally, the question immediately arose about who was involved in the hacking. But in the security industry, this issue is not the most pressing. It is more important to understand how a) to defend against such attacks b) how to minimize the damage from future attacks of the same group.

To reduce damage, it is required to go beyond a specific attack and analyze the work of the threat actor as a whole. And this is not easy: cybercriminals do not issue press releases about the involvement in the attack, they confuse the traces, change and update the hacking tools. Operation Blockbuster is a rare example of the interaction of several companies with the aim of collecting and publishing complete information about the activities of a specific group of cybercriminals. The group was called "Lazar". The joint work of many researchers allowed this grouping to attribute dozens of attacks around the world, including the breaking of Sony Pictures.

How can you combine different attacks? In our study we have one curious example: in the user agent line of one of the modules used in the attack, there is a typo: Mozilla r instead of Mozilla. On it you can easily identify the affiliation. But usually, analyzing the links between attacks is time consuming. That is why this research was made possible through the cooperation of several companies. As a result, the researchers were able to identify the group as belonging to attacks in various countries, including South Korea, Russia and the United States, from 2010 to the present. Who is really behind these attacks? Facts: a significant part of the modules was created in the locale of Korean, metadata speaks of finding a group in GMT + 8 or 9 (North and South Korea, a significant part of Asia), many attacks on South Korean resources.
Hacking the site allowed to build the backdoor into the official Linux Mint distributions
News Post blogging maintainers. Research "Laboratories".
Remember the story about one of the most ancient bugs? Then I mentioned a bug from the Red Hat tracker from 1999, which discussed checking for downloadable updates for Linux. That bug, with reservations, was closed, but the problem remained: if the developer of the operating system does not control its distribution, sooner or later this can lead to the appearance of versions of the system with malicious functionality. That is why it is advisable to download Linux distributions from the official site, since there is no bookmarks guaranteed.
Or not guaranteed? Sooner or later, this should have happened: the site of a fairly popular Linux Mint distribution was hacked, and one of the official images of the system was replaced. The victims turned out to be a little bit: they noticed in time, it was possible to download the distribution kit with backdoor only on February 20, and only one image was spoiled on one site. However, the case is significant. He allowed to assess the consequences of such hacking. Infected systems connected to the channel in IRC, from where they could give commands.
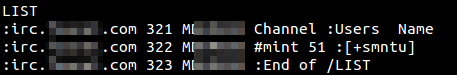
At the time of the backdoor analysis, the experts of “Laboratories” lit about 50 systems in the channel. An attacker can download arbitrary files from the victim’s computer or server; available network folders and passwords to access the Linux Mint forum have received particular attention. In addition, the infected system can be used for DDoS attacks. In general, do not forget to compare the checksum of distributions with the reference, right? Not really, it can also be replaced if the developer's site is hacked. So far this is a one-time incident, but it clearly requires a more complex system for monitoring the purity of distributions.
What else happened:
Nissan had to turn off the remote control system of the car, which allowed using the telephone application to control the climate control, check the status of the battery, etc. For a simple reason: access to the system was open to anyone, it is enough to know the “secret” URL and the last digits of the serial number (also known as VIN) of the car. We must pay tribute to Nissan: responded quickly, the system turned off until better times. About 200 thousand Nissan Leaf cars were affected.
 Antiquities:
Antiquities:Datacrime Family
Non-resident very dangerous viruses. When you run an infected file, it is standard to infect no more than one COM or EXE file in all current directories of all available disks. Depending on the timer and its internal counters, the text is displayed on the screen:
"Datacrime-1168, -1280" - "DATACRIME VIRUS RELEASED 1 MARCH 1989"
"Datacrime-1480, -1514" - "DATACRIME II VIRUS"
and after that they try to format several tracks of the hard drive.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 28.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/278025/
All Articles