Software Internet gateway for a company not already small (Shorewall, QoS in full width). Part 3
I present the third article in the series, aimed at "continuing" system administrators, for experienced ones, I can hardly discover something new.
In these articles, we will look at building an Internet gateway on linux, allowing you to link several company offices, and provide limited access to the network, traffic prioritization (QoS) and simple load balancing with redundancy between two providers.
Specifically in this part:
And in the first part were considered:
And in the second :
In the fourth part :
Everything that is described further is just my vision of the question, your opinion may (and for good should be) different.
')
So, let's highlight several types of traffic:
In turn, user traffic, within each class, we will divide between some services.
You can realize the whole difficult configuration by looking at the picture (upper left corner: parent class, upper right: priority, lower corners: minimum and maximum speed):
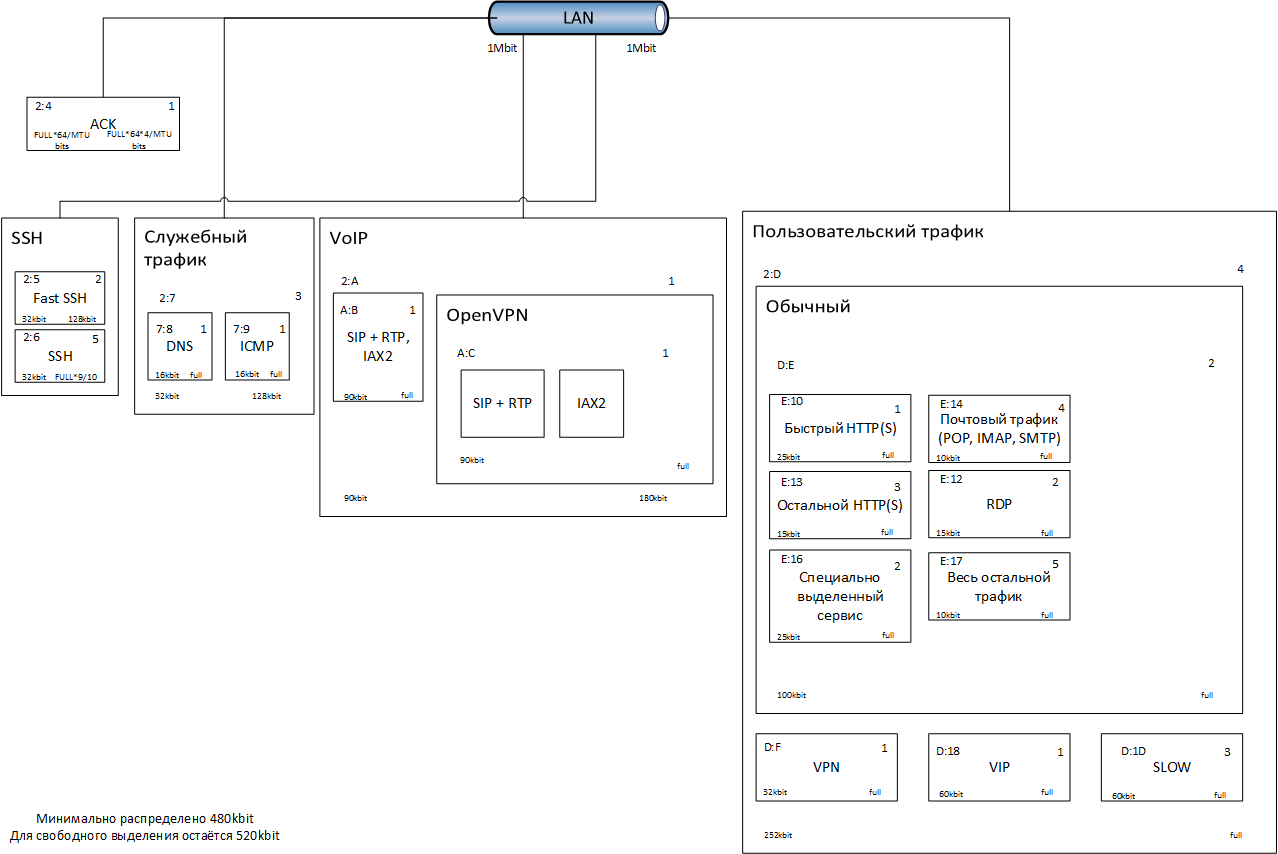
We will razrulivat traffic on not very fast channel and 1 Mbps (just think, not so long ago, 128 kbps was cool), more precisely on two (to make it more interesting)!
The rules work this way: if a class has several child classes with the same priority, then when calculating how much band to give over the limit, the proportion of the minimum speeds of these classes will be used. If the priorities are not the same, they will be included in the calculation as an additional weight factor. Above the minimum band allocated to the class, there is still some unallocated band, it can be used if the channel is sufficiently free. In most cases, I specified the key value full for this band (maximum of the parent class).
To improve the efficiency of channel use, it is not necessary to divide it between all classes at the minimum available speed. In this configuration, the redistribution of speed will go with a very large delay (SIP, or rather, RTP will be overjoyed). In any case, the speed is redistributed with some delay, and it is most dependent on the types of protocols used by users. For example, torrent, which watered the available maximum, very slowly comes down from the occupied band (up to minutes), the problem is due to the large number of traffic sources to our server (until they all react to a reduction in speed ...).
But enough of the lyrics, let's begin (we use part of the configs from past articles, if something is not set up by me here, you know where to look):
Declare variables:
Let's announce providers:
What do we do during startup:
Let's add the routing policy (I will reveal the need for this step below):
Let's declare a bunch of classes for traffic:
If you look at the descriptions, you will notice that there is a lot of the same. A slight difference in the use of flow (grouping traffic into streams) The streams themselves allow you to deal with such a phenomenon: one user establishes a bunch of connections with different addresses, and without streams, he squeezes traffic from everyone else within the class. The whole topic is that without the flows, the carve-up goes through the direct connections, who have more of them, he generally takes the blanket over himself and drags him away.
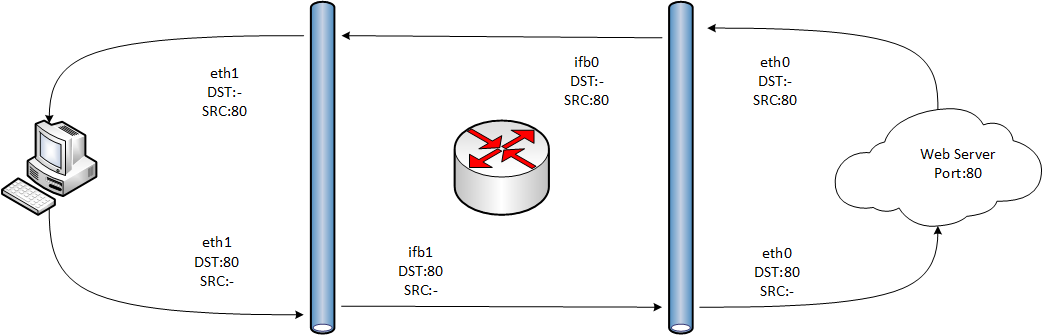
Another small feature, the external interface (both physical and IFB), does not know anything about the structure of the internal network (if NAT is used), so part of the detailed classification is missing.
Now we will classify traffic (for classes with ACK and MARK, we will not describe anything, the corresponding traffic will fall there itself) and filter.
Gather tips:
After restarting, shaping will work!
OSPF , ! VoIP . VPN , , ( OSPF), VoIP, , - , , , , ( Cisco )? VoIP , ( IAX2 ). VoIP ! OSPF, ( ), , ( , ).
:
, OSPF , , , - , OSPF. Shorewall . - , .
policy routing :
, ( ), ( ).
cron:
PS
:
In these articles, we will look at building an Internet gateway on linux, allowing you to link several company offices, and provide limited access to the network, traffic prioritization (QoS) and simple load balancing with redundancy between two providers.
Specifically in this part:
- Full QoS in Shorewall
- More detailed setting Shorewall
- Channel traffic scaling according to protocols
- Crutches, without them, nowhere
And in the first part were considered:
- The simplest setting is Shorewall
- Awfully tricky dnsmasq setup
- No less complicated setting OpenVPN
- And for many continuing admins atypical, dynamic routing, for example, OSPF
And in the second :
- More detailed setting Shorewall
- Terrible and not clear QoS
- Load balancing and redundancy
In the fourth part :
- Automatic events
- Macros
Traffic classification planning
Everything that is described further is just my vision of the question, your opinion may (and for good should be) different.
')
So, let's highlight several types of traffic:
- Service Traffic (DNS, ICMP, TCP / ACK)
- Tunnel traffic
- Voip traffic
- Administrative (SSH, etc.)
- Custom
- High priority
- Usual
- Low priority
- VPN traffic
In turn, user traffic, within each class, we will divide between some services.
You can realize the whole difficult configuration by looking at the picture (upper left corner: parent class, upper right: priority, lower corners: minimum and maximum speed):

We will razrulivat traffic on not very fast channel and 1 Mbps (just think, not so long ago, 128 kbps was cool), more precisely on two (to make it more interesting)!
The rules work this way: if a class has several child classes with the same priority, then when calculating how much band to give over the limit, the proportion of the minimum speeds of these classes will be used. If the priorities are not the same, they will be included in the calculation as an additional weight factor. Above the minimum band allocated to the class, there is still some unallocated band, it can be used if the channel is sufficiently free. In most cases, I specified the key value full for this band (maximum of the parent class).
To improve the efficiency of channel use, it is not necessary to divide it between all classes at the minimum available speed. In this configuration, the redistribution of speed will go with a very large delay (SIP, or rather, RTP will be overjoyed). In any case, the speed is redistributed with some delay, and it is most dependent on the types of protocols used by users. For example, torrent, which watered the available maximum, very slowly comes down from the occupied band (up to minutes), the problem is due to the large number of traffic sources to our server (until they all react to a reduction in speed ...).
But enough of the lyrics, let's begin (we use part of the configs from past articles, if something is not set up by me here, you know where to look):
Declare variables:
params
# # Shorewall -- /etc/shorewall/params # # Assign any variables that you need here. # # It is suggested that variable names begin with an upper case letter # to distinguish them from variables used internally within the # Shorewall programs # # Example: # # NET_IF=eth0 # NET_BCAST=130.252.100.255 # NET_OPTIONS=routefilter,norfc1918 # # Example (/etc/shorewall/interfaces record): # # net $NET_IF $NET_BCAST $NET_OPTIONS # # The result will be the same as if the record had been written # # net eth0 130.252.100.255 routefilter,norfc1918 # ############################################################################### IF_RED1=eth0 # , , GW_RED1=192.168.10.1 IF_RED2=eth2 GW_RED2=192.168.10.1 IF_GRN=eth1 NET_GRN=172.16.0.0/23 IF_TUN=tap+ # - ipset , IP_SLOW=172.16.0.45 IP_SLOW_SPEC=172.16.0.45 IP_VIP=172.16.0.46 IP_VIP_SPEC=172.16.0.46 IP_NORMAL=$NET_GRN IP_NORMAL_SPEC=172.16.0.47 #LAST LINE -- DO NOT REMOVE Let's announce providers:
providers
# # Shorewall -- /etc/shorewall/providers # # For information about entries in this file, type "man shorewall-providers" # # For additional information, see http://shorewall.net/MultiISP.html # ############################################################################################ #NAME NUMBER MARK DUPLICATE INTERFACE GATEWAY OPTIONS COPY pr1 1 0x10000 - $IF_RED1 GW_RED1 track,balance=1 pr2 2 0x20000 - $IF_RED2 GW_RED2 track,balance=1 # . :) tap0 4 0x30000 - tap0 - loose tap1 3 0x40000 - tap1 - loose interfaces
# # Shorewall -- /etc/shorewall/interfaces # # For information about entries in this file, type "man shorewall-interfaces" # # The manpage is also online at # http://www.shorewall.net/manpages/shorewall-interfaces.html # ############################################################################### ?FORMAT 2 ############################################################################### #ZONE INTERFACE OPTIONS red $IF_RED1 dhcp,routeback,optional red $IF_RED2 dhcp,routeback,optional grn $IF_GRN dhcp,routeback,optional tun tap0 dhcp,routeback,optional tun tap1 dhcp,routeback,optional What do we do during startup:
init
# # Shorewall -- /etc/shorewall/init # # Add commands below that you want to be executed at the beginning of # a "shorewall start", "shorewall-reload" or "shorewall restart" command. # # For additional information, see # http://shorewall.net/shorewall_extension_scripts.htm # ############################################################################### modprobe ifb numifbs=3 ip link set ifb0 up ip link set ifb1 up ip link set ifb2 up ipset -N ip_vip iphash ipset -N ip_vip_spec iphash ipset -N ip_normal iphash ipset -A ip_normal $NET_GRN ipset -N ip_normal_spec iphash ipset -N ip_slow iphash ipset -N ip_slow_spec iphash started
# # Shorewall -- /etc/shorewall/started # # Add commands below that you want to be executed after shorewall has # been completely started, reloaded or restarted. The difference between # this extension script and /etc/shorewall/start is that this one is # invoked after the 'shorewall' chain has been created (thus # signaling that the firewall is completely up). # # This script should not change the firewall configuration directly but # may do so indirectly by running /sbin/shorewall with the 'nolock' # option. # # See http://shorewall.net/shorewall_extension_scripts.htm for additional # information. # ############################################################################### IPROUTE='/usr/sbin/ip' IFS=$'\n' for line in $(grep tap /etc/shorewall/providers | grep loose);do IFS=$' \t\n' read -r -a line_ <<< "$line" $IPROUTE route del default table ${line_[1]} >/dev/null 2>&1 done Let's add the routing policy (I will reveal the need for this step below):
rtrules
# # Shorewall -- /etc/shorewall/rtrules # # For information about entries in this file, type "man shorewall-rtrules" # # For additional information, see http://www.shorewall.net/MultiISP.html # #################################################################################### #SOURCE DEST PROVIDER PRIORITY MASK 0.0.0.0/0 0.0.0.0/0 tap0 19001 0.0.0.0/0 0.0.0.0/0 tap1 19002 Let's declare a bunch of classes for traffic:
tcclasses
# # Shorewall -- /etc/shorewall/tcclasses # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX INCLUDE tcclasses.1 INCLUDE tcclasses.2 INCLUDE tcclasses.3 INCLUDE tcclasses.4 INCLUDE tcclasses.5 INCLUDE tcclasses.6 tcclasses.1
# # Shorewall -- /etc/shorewall/tcclasses # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # , # 1:1:2 - 1mbit 2mbit 1 # 1:1:3 - 998mbit 999mbit 2 # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 1:2:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH , , ( ) 1:2:5 - 32kbit 128kbit 2 # ( ) 1:2:6 - 32kbit full*9/10 5 flow=dst # DNS ICMP, 1:2:7 - 32kbit 128kbit 3 # DNS 1:7:8 - 16kbit full 1 # PING 1:7:9 - 16kbit full 1 # VoIP 1:2:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 1:A:B 1 90kbit full 1 # SIP VPN ( ) 1:A:C - 90kbit full 1 # 1:2:D - 252kbit full 4 # 1:D:E - 100kbit full 2 # VPN ( ) 1:D:F - 32kbit full 1 # HTTP(S) , ( , # ) 1:E:10 - 25kbit full 1 flow=dst # RDP 1:E:12 - 15kbit full 2 flow=dst # HTTP(S) , 1:E:13 - 15kbit full 3 flow=dst # 1:E:14 - 10kbit full 4 flow=dst # ( , Webinar) 1:E:16 - 25kbit full 2 flow=dst # , 1:E:17 - 10kbit full 5 default,flow=dst # VIP (VIP- ), 1:D:18 - 60kbit full 1 # HTTP(S) , ( , # ) 1:18:19 - 20kbit full 1 # HTTP(S) , 1:18:1A - 10kbit full 3 # 1:18:1B - 10kbit full 4 # VIP 1:18:1C - 20kbit full 2 # 1:D:1D - 60kbit full 3 # HTTP(S) , ( , # ) 1:1D:1E - 20kbit full 1 # HTTP(S) , 1:1D:1F - 10kbit full 3 # 1:1D:20 - 10kbit full 4 # , 1:1D:21 - 20kbit full 2 tcclasses.2
# # Shorewall -- /etc/shorewall/tcclasses.2 # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # , # 2:1:2 - 1mbit 1mbit 1 # 2:1:3 - 999mbit 999mbit 2 # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 2:2:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH , , ( ) 2:2:5 - 32kbit 128kbit 2 # ( ) 2:2:6 - 32kbit full*9/10 5 flow=nfct-src # DNS ICMP, 2:2:7 - 32kbit 128kbit 3 # DNS 2:7:8 - 16kbit full 1 # PING 2:7:9 - 16kbit full 1 # VoIP 2:2:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 2:A:B 1 90kbit full 1 # SIP VPN ( ) 2:A:C - 90kbit full 1 # 2:2:D - 252kbit full 4 # 2:D:E - 100kbit full 2 # VPN ( ) 2:D:F - 32kbit full 1 # HTTP(S) , ( , # ) 2:E:10 - 25kbit full 1 flow=nfct-src # RDP 2:E:12 - 15kbit full 2 flow=nfct-src # HTTP(S) , 2:E:13 - 15kbit full 3 flow=nfct-src # 2:E:14 - 10kbit full 4 flow=nfct-src # ( , Webinar) 2:E:16 - 25kbit full 2 flow=nfct-src # , 2:E:17 - 10kbit full 5 default,flow=nfct-src # VIP (VIP- ), 2:D:18 - 60kbit full 1 # HTTP(S) , ( , # ) 2:18:19 - 20kbit full 1 # HTTP(S) , 2:18:1A - 10kbit full 3 # 2:18:1B - 10kbit full 4 # VIP 2:18:1C - 20kbit full 2 # 2:D:1D - 60kbit full 3 # HTTP(S) , ( , # ) 2:1D:1E - 20kbit full 1 # HTTP(S) , 2:1D:1F - 10kbit full 3 # 2:1D:20 - 10kbit full 4 # , 2:1D:21 - 20kbit full 2 tcclasses.3
# # Shorewall -- /etc/shorewall/tcclasses.3 # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 3:1:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH , , ( ) 3:1:5 - 32kbit 128kbit 2 # ( ) 3:1:6 - 32kbit full*9/10 5 flow=dst # DNS ICMP, 3:1:7 - 32kbit 128kbit 3 # DNS 3:7:8 - 16kbit full 1 # PING 3:7:9 - 16kbit full 1 # VoIP 3:1:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 3:A:B 1 90kbit full 1 # SIP VPN ( ) 3:A:C - 90kbit full 1 # 3:1:D - 252kbit full 4 # 3:D:E - 100kbit full 2 # VPN ( ) 3:D:F - 32kbit full 1 # HTTP(S) , ( , # ) 3:E:10 - 25kbit full 1 flow=dst # RDP 3:E:12 - 15kbit full 2 flow=dst # HTTP(S) , 3:E:13 - 15kbit full 3 flow=dst # 3:E:14 - 10kbit full 4 flow=dst # ( , Webinar) 3:E:16 - 25kbit full 2 flow=dst # , 3:E:17 - 10kbit full 5 default,flow=dst tcclasses.4
# # Shorewall -- /etc/shorewall/tcclasses.4 # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 4:1:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH 4:1:6 - 32kbit full*9/10 5 flow=nfct-src # DNS ICMP, 4:1:7 - 32kbit 128kbit 3 # DNS 4:7:8 - 16kbit full 1 # PING 4:7:9 - 16kbit full 1 # VoIP 4:1:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 4:A:B 1 90kbit full 1 # SIP VPN ( ) 4:A:C - 90kbit full 1 # 4:1:D - 252kbit full 4 # , . 4:D:E - 100kbit full 2 # VPN ( ) 4:D:F - 32kbit full 1 # RDP 4:E:12 - 15kbit full 2 flow=nfct-src # HTTP(S) 4:E:13 - 25kbit full 3 flow=nfct-src # 4:E:14 - 15kbit full 4 flow=nfct-src # ( , Webinar) 4:E:16 - 25kbit full 2 flow=nfct-src # , 4:E:17 - 10kbit full 5 default,flow=nfct-src tcclasses.5
# # Shorewall -- /etc/shorewall/tcclasses.5 # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 5:1:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH , , ( ) 5:1:5 - 32kbit 128kbit 2 # ( ) 5:1:6 - 32kbit full*9/10 5 flow=dst # DNS ICMP, 5:1:7 - 32kbit 128kbit 3 # DNS 5:7:8 - 16kbit full 1 # PING 5:7:9 - 16kbit full 1 # VoIP 5:1:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 5:A:B 1 90kbit full 1 # SIP VPN ( ) 5:A:C - 90kbit full 1 # 5:1:D - 252kbit full 4 # 5:D:E - 100kbit full 2 # VPN ( ) 5:D:F - 32kbit full 1 # HTTP(S) , ( , # ) 5:E:10 - 25kbit full 1 flow=dst # RDP 5:E:12 - 15kbit full 2 flow=dst # HTTP(S) , 5:E:13 - 15kbit full 3 flow=dst # 5:E:14 - 10kbit full 4 flow=dst # ( , Webinar) 5:E:16 - 25kbit full 2 flow=dst # , 5:E:17 - 10kbit full 5 default,flow=dst tcclasses.6
# # Shorewall -- /etc/shorewall/tcclasses.6 # # For information about entries in this file, type "man shorewall-tcclasses" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ############################################################################### #INTERFACE:CLASS MARK RATE: CEIL PRIORITY OPTIONS # DMAX:UMAX # ACK . , # TCP MTU ( ACK), # , MTU ( ACK ), # 6:1:4 - full*64/1500 full*64*4/1500 1 tcp-ack # SSH 6:1:6 - 32kbit full*9/10 5 flow=nfct-src # DNS ICMP, 6:1:7 - 32kbit 128kbit 3 # DNS 6:7:8 - 16kbit full 1 # PING 6:7:9 - 16kbit full 1 # VoIP 6:1:A - 180kbit 180kbit 1 # SIP ( u(a)law), nf_conntrack_sip 6:A:B 1 90kbit full 1 # SIP VPN ( ) 6:A:C - 90kbit full 1 # 6:1:D - 252kbit full 4 # , . 6:D:E - 100kbit full 2 # VPN ( ) 6:D:F - 32kbit full 1 # RDP 6:E:12 - 15kbit full 2 flow=nfct-src # HTTP(S) 6:E:13 - 25kbit full 3 flow=nfct-src # 6:E:14 - 15kbit full 4 flow=nfct-src # ( , Webinar) 6:E:16 - 25kbit full 2 flow=nfct-src # , 6:E:17 - 10kbit full 5 default,flow=nfct-src If you look at the descriptions, you will notice that there is a lot of the same. A slight difference in the use of flow (grouping traffic into streams) The streams themselves allow you to deal with such a phenomenon: one user establishes a bunch of connections with different addresses, and without streams, he squeezes traffic from everyone else within the class. The whole topic is that without the flows, the carve-up goes through the direct connections, who have more of them, he generally takes the blanket over himself and drags him away.
Another small feature, the external interface (both physical and IFB), does not know anything about the structure of the internal network (if NAT is used), so part of the detailed classification is missing.
Now we will classify traffic (for classes with ACK and MARK, we will not describe anything, the corresponding traffic will fall there itself) and filter.
Gather tips:

mangle
# # Shorewall -- /etc/shorewall/mangle # # For information about entries in this file, type "man shorewall-mangle" # # See http://shorewall.net/traffic_shaping.htm for additional information. # For usage in selecting among multiple ISPs, see # http://shorewall.net/MultiISP.html # # See http://shorewall.net/PacketMarking.html for a detailed description of # the Netfilter/Shorewall packet marking mechanism. # #################################################################################################################################################### #ACTION SOURCE DEST PROTO DEST SOURCE USER TEST LENGTH TOS CONNBYTES HELPER PROBABILITY DSCP # PORT(S) PORT(S) # , ! # ( 0) RESTORE 0.0.0.0/0 0.0.0.0/0 all - - - 0 # , CONTINUE 0.0.0.0/0 0.0.0.0/0 all - - - !0 # SIP , RTP MARK(1) 0.0.0.0/0 0.0.0.0/0 all - - - - - - - sip # SIP ( ), MARK(|0x40000) 172.16.0.0/12 172.16.0.0/12 all - - - - - - - sip MARK(|0x40000) 172.16.0.0/12 172.16.0.0/12 udp 4569 SAVE 0.0.0.0/0 0.0.0.0/0 all - - - !0 INCLUDE mangle.1 INCLUDE mangle.3 INCLUDE mangle.5 mangle.1
# # Shorewall -- /etc/shorewall/mangle.1 # # For information about entries in this file, type "man shorewall-mangle" # # See http://shorewall.net/traffic_shaping.htm for additional information. # For usage in selecting among multiple ISPs, see # http://shorewall.net/MultiISP.html # # See http://shorewall.net/PacketMarking.html for a detailed description of # the Netfilter/Shorewall packet marking mechanism. # #################################################################################################################################################### #ACTION SOURCE DEST PROTO DEST SOURCE USER TEST LENGTH TOS CONNBYTES HELPER PROBABILITY DSCP # PORT(S) PORT(S) # , ! # # HTTP(S) , ( , # ), , 0 256kb CLASSIFY(1:10) - +ip_normal tcp - 80,443 - - - - 0:262144 # HTTP(S) , , # , 256kb CLASSIFY(1:13) - +ip_normal tcp - 80,443 - - - - 262145: # CLASSIFY(1:14) - +ip_normal tcp - 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) CLASSIFY(1:16) - +ip_normal_spec tcp - 32765 # VIP (VIP- ), # HTTP(S) , ( , # ) CLASSIFY(1:19) - +ip_vip tcp - 80,443 - - - - 0:262144 # HTTP(S) , CLASSIFY(1:1A) - +ip_vip tcp - 80,443 - - - - 262145: # CLASSIFY(1:1B) - +ip_vip tcp - 25,110,143,465,587,993,995,2525,4190 # VIP CLASSIFY(1:1C) - +ip_vip_spec tcp - 32765 # # HTTP(S) , ( , # ) CLASSIFY(1:1E) - +ip_slow tcp - 80,443 - - - - 0:262144 # HTTP(S) , CLASSIFY(1:1F) - +ip_slow tcp - 80,443 - - - - 262145: # CLASSIFY(1:20) - +ip_slow tcp - 25,110,143,465,587,993,995,2525,4190 # , CLASSIFY(1:21) - +ip_slow_spec tcp - 32765 # VPN ( ) CLASSIFY(1:F) - - udp - 1194 # IAX2 CLASSIFY(1:B) - - udp - 4569 # SIP VPN ( ) CLASSIFY(1:C) - - udp - 40032 # RDP CLASSIFY(1:12) - - tcp - 3389 CLASSIFY(1:12) - - udp - 3389 # DNS CLASSIFY(1:8) - - udp - 53 CLASSIFY(1:8) - - tcp - 53 # PING CLASSIFY(1:9) - - icmp echo-request,echo-reply # SSH , , ( ) CLASSIFY(1:5) - - tcp - 22 - - 0:512 # ( ) CLASSIFY(1:6) - - tcp - 22 - - 513: CLASSIFY(1:3) $NET_GRN $NET_GRN mangle.3
# # Shorewall -- /etc/shorewall/mangle.3 # # For information about entries in this file, type "man shorewall-mangle" # # See http://shorewall.net/traffic_shaping.htm for additional information. # For usage in selecting among multiple ISPs, see # http://shorewall.net/MultiISP.html # # See http://shorewall.net/PacketMarking.html for a detailed description of # the Netfilter/Shorewall packet marking mechanism. # #################################################################################################################################################### #ACTION SOURCE DEST PROTO DEST SOURCE USER TEST LENGTH TOS CONNBYTES HELPER PROBABILITY DSCP # PORT(S) PORT(S) # , ! # # HTTP(S) , ( , # ), , 0 256kb CLASSIFY(3:10) - - tcp 80,443 - - - - - 0:262144 # HTTP(S) , , # , 256kb CLASSIFY(3:13) - - tcp 80,443 - - - - - 262145: # CLASSIFY(3:14) - - tcp 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) CLASSIFY(3:16) - - tcp 32765 # VPN ( ) CLASSIFY(3:F) - - udp 1194 # IAX2 CLASSIFY(3:B) - - udp 4569 # SIP VPN ( ) CLASSIFY(3:C) - - udp 40032 # RDP CLASSIFY(3:12) - - tcp 3389 CLASSIFY(3:12) - - udp 3389 # DNS CLASSIFY(3:8) - - udp 53 CLASSIFY(3:8) - - tcp 53 # PING CLASSIFY(3:9) - - icmp echo-request,echo-reply # SSH , , ( ) CLASSIFY(3:5) - - tcp 22 - - - 0:512 # ( ) CLASSIFY(3:6) - - tcp 22 - - - 513: mangle.5
# # Shorewall -- /etc/shorewall/mangle.5 # # For information about entries in this file, type "man shorewall-mangle" # # See http://shorewall.net/traffic_shaping.htm for additional information. # For usage in selecting among multiple ISPs, see # http://shorewall.net/MultiISP.html # # See http://shorewall.net/PacketMarking.html for a detailed description of # the Netfilter/Shorewall packet marking mechanism. # #################################################################################################################################################### #ACTION SOURCE DEST PROTO DEST SOURCE USER TEST LENGTH TOS CONNBYTES HELPER PROBABILITY DSCP # PORT(S) PORT(S) # , ! # # HTTP(S) , ( , # ), , 0 256kb CLASSIFY(5:10) - - tcp 80,443 - - - - - 0:262144 # HTTP(S) , , # , 256kb CLASSIFY(5:13) - - tcp 80,443 - - - - - 262145: # CLASSIFY(5:14) - - tcp 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) CLASSIFY(5:16) - - tcp 32765 # VPN ( ) CLASSIFY(5:F) - - udp 1194 # IAX2 CLASSIFY(5:B) - - udp 4569 # SIP VPN ( ) CLASSIFY(5:C) - - udp 40032 # RDP CLASSIFY(5:12) - - tcp 3389 CLASSIFY(5:12) - - udp 3389 # DNS CLASSIFY(5:8) - - udp 53 CLASSIFY(5:8) - - tcp 53 # PING CLASSIFY(5:9) - - icmp echo-request,echo-reply # SSH , , ( ) CLASSIFY(5:5) - - tcp 22 - - - 0:512 # ( ) CLASSIFY(5:6) - - tcp 22 - - - 513: tcfilters
# # Shorewall -- /etc/shorewall/tcfilters # # For information about entries in this file, type "man shorewall-tcfilters" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ######################################################################################################## #INTERFACE: SOURCE DEST PROTO DEST SOURCE TOS LENGTH PRIORITY #CLASS PORT(S) PORT(S) # , ! INCLUDE tcfilters.2 INCLUDE tcfilters.4 INCLUDE tcfilters.6 tcfilters.2
# # Shorewall -- /etc/shorewall/tcfilters.2 # # For information about entries in this file, type "man shorewall-tcfilters" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ######################################################################################################## #INTERFACE: SOURCE DEST PROTO DEST SOURCE TOS LENGTH PRIORITY #CLASS PORT(S) PORT(S) # , ! 2:3 $NET_GRN $NET_GRN # SSH 2:6 - - tcp 22 # DNS 2:8 - - udp 53 2:8 - - tcp 53 # PING 2:9 - - icmp echo-request,echo-reply # RDP 2:12 - - tcp 3389 2:12 - - udp 3389 # IAX2 2:B - - udp 4569 # SIP VPN ( ) 2:C - - udp 40032 # VPN ( ) 2:F - - udp 1194 # # HTTP(S) 2:1F $IP_SLOW 0.0.0.0/0 tcp 80,443 # 2:20 $IP_SLOW - tcp 25,110,143,465,587,993,995,2525,4190 # , 2:21 $IP_SLOW_SPEC - tcp 32765 # VIP (VIP- ), # HTTP(S) 2:1A $IP_VIP - tcp 80,443 # 2:1B $IP_VIP - tcp 25,110,143,465,587,993,995,2525,4190 # VIP 2:1C $IP_VIP_SPEC - tcp 32765 # # HTTP(S) 2:13 $IP_NORMAL - tcp 80,443 # 2:14 $IP_NORMAL - tcp 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) 2:16 $IP_NORMAL_SPEC - tcp 32765 tcfilters.4
# # Shorewall -- /etc/shorewall/tcfilters.4 # # For information about entries in this file, type "man shorewall-tcfilters" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ######################################################################################################## #INTERFACE: SOURCE DEST PROTO DEST SOURCE TOS LENGTH PRIORITY #CLASS PORT(S) PORT(S) # , ! # tcfilters , 4:6 - - tcp - 22 # DNS 4:8 - - udp - 53 4:8 - - tcp - 53 # PING 4:9 - - icmp echo-request,echo-reply # RDP 4:12 - - tcp - 3389 4:12 - - udp - 3389 # IAX2 4:B - - udp - 4569 # SIP VPN ( ) 4:C - - udp - 40032 # VPN ( ) 4:F - - udp - 1194 # , -, , # . HTTP(S) 4:13 - - tcp - 80,443 # 4:14 - - tcp - 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) 4:16 - - tcp - 32765 tcfilters.6
# # Shorewall -- /etc/shorewall/tcfilters.6 # # For information about entries in this file, type "man shorewall-tcfilters" # # See http://shorewall.net/traffic_shaping.htm for additional information. # ######################################################################################################## #INTERFACE: SOURCE DEST PROTO DEST SOURCE TOS LENGTH PRIORITY #CLASS PORT(S) PORT(S) # , ! # tcfilters , 6:6 - - tcp - 22 # DNS 6:8 - - udp - 53 6:8 - - tcp - 53 # PING 6:9 - - icmp echo-request,echo-reply # RDP 6:12 - - tcp - 3389 6:12 - - udp - 3389 # IAX2 6:B - - udp - 4569 # SIP VPN ( ) 6:C - - udp - 40032 # VPN ( ) 6:F - - udp - 1194 # , -, , # . HTTP(S) 6:13 - - tcp - 80,443 # 6:14 - - tcp - 25,110,143,465,587,993,995,2525,4190 # ( , Webinar, 32765) 6:16 - - tcp - 32765 After restarting, shaping will work!
Strange crutches
OSPF , ! VoIP . VPN , , ( OSPF), VoIP, , - , , , , ( Cisco )? VoIP , ( IAX2 ). VoIP ! OSPF, ( ), , ( , ).
:
/usr/local/bin/ospf_alt_route.sh
#!/bin/bash METRIC_BOOST=$1 IP_INTERVAL=$2 IPROUTE='/usr/sbin/ip' function search_and_del() { # $1 - TABLE # $2 - DST # $3 - VIA # $4 - METRIC TABLE=$1 declare -a DST=("${!2}") declare -a VIA=("${!3}") declare -a METRIC=("${!4}") # , OSPF IFS=$'\n' for line in $(${IPROUTE} route show table $TABLE);do IFS=$' \t' read -r -a line_ <<< "$line" CONT=0 for i in "${!DST[@]}"; do if [ "${line_[0]}" = "${DST[$i]}" ]; then if [ "${line_[6]}" -eq "${METRIC[$i]}" ] && [ "${line_[2]}" = "${VIA[$i]}" ];then CONT=1 continue fi fi done [ "$CONT" -eq "0" ] && eval "${IPROUTE} route del $line table $TABLE" done } DST_='' METRIC_='' DEV_='' DST='' VIA_PRIM='' VIA_SEC='' METRIC_PRIM='' METRCI_SEC='' TABLE_PRIM='' TABLE_SEC='' COUNT=0 # while IFS=$' \t' read -r -a line_; do if [[ $(( $(echo ${line_[4]} | sed -e 's/[a-zA-Z]*//') % 2)) == 0 ]];then TABLE_PRIM=${line_[1]} else TABLE_SEC=${line_[1]} fi done < <(grep tap /etc/shorewall/providers | grep loose) # , [ -z "$TABLE_PRIM" ] || [ -z "$TABLE_SEC" ] && exit 0 # OSPF while IFS=$' \t' read -r -a line_; do # ( via) if [ "${line_[3]}" == "via" ]; then # DST_=${line_[1]} METRIC_=${line_[2]} # if [ "${line_[$(( ${#line_[@]} -2 ))]}" != "inactive," ]; then DEV_=$(echo ${line_[$(( ${#line_[@]} -2 ))]} | sed -e "s/,//") if [[ $(( $(echo $DEV_ | sed -e 's/[a-zA-Z]*//') % 2)) == 0 ]];then DST[$COUNT]=$(echo ${line_[1]} | sed -e "s/\/32//") VIA_PRIM[$COUNT]=$(echo ${line_[$(( ${#line_[@]} -3 ))]} | sed -e "s/,//") METRIC_PRIM[$COUNT]=$(echo ${line_[2]} | sed -e "s/\[[0-p]*\///" | sed -e "s/\]//") # OpenVPN , , # , 128 ( /25) IFS=$'.' read -r -a IP <<< ${VIA_PRIM[$COUNT]} VIA_SEC[$COUNT]="${IP[0]}.${IP[1]}.${IP[2]}.$(( ${IP[3]} + $IP_INTERVAL ))" METRIC_SEC[$COUNT]=$(( ${METRIC_PRIM[$COUNT]} + $METRIC_BOOST )) COUNT=$(($COUNT + 1 )) fi fi else # , if [ "${line_[$(( ${#line_[@]} -2 ))]}" != "inactive," ]; then DEV_=$(echo ${line_[$(( ${#line_[@]} -2 ))]} | sed -e "s/,//") if [[ $(( $(echo $DEV_ | sed -e 's/[a-zA-Z]*//') % 2)) == 0 ]];then DST[$COUNT]=$(echo $DST_ | sed -e "s/\/32//") if [ "${line_[0]}" == "via" ]; then VIA_PRIM[$COUNT]=$(echo ${line_[1]} | sed -e "s/,//") else VIA_PRIM[$COUNT]=$(echo ${line_[2]} | sed -e "s/,//") fi METRIC_PRIM[$COUNT]=$(echo $METRIC_ | sed -e "s/\[[0-p]*\///" | sed -e "s/\]//") IFS=$'.' read -r -a IP <<< ${VIA_PRIM[$COUNT]} VIA_SEC[$COUNT]="${IP[0]}.${IP[1]}.${IP[2]}.$(( ${IP[3]} + $IP_INTERVAL ))" METRIC_SEC[$COUNT]=$(( ${METRIC_PRIM[$COUNT]} + $METRIC_BOOST )) COUNT=$(($COUNT + 1 )) fi fi fi done < <(/usr/bin/vtysh -c 'show ip route ospf' | grep via | grep tap | grep -v -e 'directly connected') # search_and_del $TABLE_PRIM DST[@] VIA_PRIM[@] METRIC_PRIM[@] search_and_del $TABLE_SEC DST[@] VIA_SEC[@] METRIC_SEC[@] # ${IPROUTE} route del default table $TABLE_PRIM >/dev/null 2>&1 ${IPROUTE} route del default table $TABLE_SEC >/dev/null 2>&1 # , for i in "${!DST[@]}"; do [ -z ${DST[$i]} ] || [ -z ${VIA_PRIM[$i]} ] || [ -z ${METRIC_PRIM[$i]} ] && continue ${IPROUTE} route replace ${DST[$i]} via ${VIA_PRIM[$i]} table $TABLE_PRIM metric ${METRIC_PRIM[$i]} >/dev/null 2>&1 # OSPF , " " if [ "${DST[$i]}" = "${VIA_SEC[$i]}" ]; then # "" ${IPROUTE} route replace ${VIA_PRIM[$i]} via ${DST[$i]} table $TABLE_SEC metric ${METRIC_SEC[$i]} >/dev/null 2>&1 else ${IPROUTE} route replace ${DST[$i]} via ${VIA_SEC[$i]} table $TABLE_SEC metric ${METRIC_SEC[$i]} >/dev/null 2>&1 fi # main ${IPROUTE} route del ${DST[$i]} via ${VIA_PRIM[$i]} metric ${METRIC_PRIM[$i]} >/dev/null 2>&1 done , OSPF , , , - , OSPF. Shorewall . - , .
policy routing :
Routing Rules 0: from all lookup local 999: from all lookup main 10000: from all fwmark 0x10000/0xff0000 lookup pr1 10001: from all fwmark 0x20000/0xff0000 lookup pr2 10002: from all fwmark 0x40000/0xff0000 lookup tap1 10003: from all fwmark 0x30000/0xff0000 lookup tap0 19001: from all lookup tap0 20000: from 192.168.10.37 lookup pr1 20000: from 192.168.10.36 lookup pr2 32765: from all lookup balance 32766: from all lookup main 32767: from all lookup default , ( ), ( ).
cron:
/etc/cron.d/ospf_alt_route
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 — 59)
# | .------------- hour (0 — 23)
# | | .---------- day of month (1 — 31)
# | | | .------- month (1 — 12) OR jan,feb,mar,apr…
# | | | | .---- day of week (0 — 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/1 * * * * root /usr/local/bin/ospf_alt_route.sh 1 128
# Example of job definition:
# .---------------- minute (0 — 59)
# | .------------- hour (0 — 23)
# | | .---------- day of month (1 — 31)
# | | | .------- month (1 — 12) OR jan,feb,mar,apr…
# | | | | .---- day of week (0 — 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/1 * * * * root /usr/local/bin/ospf_alt_route.sh 1 128
PS
:
- cron
- rtrules
- started
Source: https://habr.com/ru/post/277983/
All Articles