Anatomy of ransomware for Android, part 2
In May 2014, ESET specialists discovered the first extortionist with the Android file encryption feature called Simplocker. Similar malware for Windows has previously gained widespread popularity and has been successfully used by hackers to extort large sums from their victims. Among the brightest representatives are such families as Cryptolocker, Cryptowall, CTB-Locker, Torrentlocker.

After its launch on the device, the extortionist displays a message to the user requesting a ransom, as shown in the figure below. File encryption is carried out by Simplocker in a separate program stream. The Android / Simplocker.A malware scans certain types of files on the SD card, such as images, documents, videos with the following extensions: JPEG, JPG, PNG, BMP, GIF, PDF, DOC, DOCX, TXT, AVI, MKV, 3GP, MP4. Files are encrypted using the AES symmetric cipher.
')
The encryption key itself was rigidly sewn into the body of the extortionist, with it being in an open form. Thus, it was not difficult to decrypt files and access them. For this reason, we called the family of the extortionists namely Simplocker (a simple blocker). We also believe that due to the simplicity of its implementation, it was either a proof-of-concept (PoC) threat, or an earlier version of its more complex counterpart.

Fig. Messages demanding the purchase of Android / Simplocker first versions.

Fig. For intimidation of the victim, the extortionist uses pictures of the front camera of the device.
The text of the message of the extortionist was written in Russian, and payment was required in rubles or in Ukrainian hryvnia, which indicates the orientation of the attackers to users in Ukraine. The message also told the victim how to pay the ransom. MoneXy or QIWI were indicated as payment systems, since in this case it was not as easy to track the payee as if it were made using a credit card.
Some modifications of Simplocker also displayed in the message demanding a ransom photo of the victim, which was captured by accessing the device’s camera. This method was used by attackers to increase the negative impact on the victim.
Simplocker Spread Vectors
Cybercriminals who earned Simplocker used an effective scheme to disguise a malicious application into a legitimate or known one to spread it. As a rule, the disguise was performed under an application that was related to porn, it could be an application for viewing it or the porn movie itself. In another case, the application was disguised as a game, for example, Grand Theft Auto: San Andreas or for such common applications as Flash Player.
Simplocker was distributed using a less well-known method, such as a downloader or downloader. The use of downloaders is very common in the malware world for Windows, however, for Android, this method was not popular with cybercriminals. The loader is very compact in size and is used by hackers to download the content they need (malware) onto a compromised device.
Using downloaders to distribute malware provides attackers with some advantages for hiding malicious activity from inspectors, in particular, from the program validation program for legitimacy on the part of Google Play’s Bouncer tool. This is achieved by the following properties of the loaders.
In addition, the attackers use another special trick to hide the true functions of the loader, the above URL does not directly point to the APK file. Instead, the link leads to an intermediate server, and from there it is redirected to the file download.
We did not observe the proliferation of the extortionist Simplocker by the attackers through the Google Play app store.
Simplocker in English
A month after the discovery of the first variants of Simplocker, we began to discover new versions of this extortionist, which contained several significant improvements. One of the most notable was the change in the language of the text message to display on the lock screen. English was chosen for this purpose.
To motivate the ransom payment by the user, the FBI’s blocking device was chosen for unlawful actions: using pirated software, viewing child pornography, etc. The ransom amount in the new version ranged from 200 to 500 dollars, and as a means of payment MoneyPak payment system selected. As in the previous version of Simplocker, the new modification also used pictures of the user's camera to intimidate him. This modification is detected by our anti-virus products like Android / Simplocker.I .

Fig. Messages demanding the purchase of Android / Simplocker subsequent versions in English.
Recent options for the ransomware also contained some changes. Instead of the FBI, an NSA service was chosen (NSA), which accused the victim of visiting “banned pornographic sites” and demanded $ 500 in ransom.

Fig. Messages demanding the redemption of Android / Simplocker from the NSA.
In addition to the list of files that are encrypted, various archives were included for this: ZIP, 7z, RAR. This “update” of the extortionist became very unpleasant for users, because it deprives them of access to archives with the contents of the backup data of the device, which are stored in the format of such archives. After losing access to such files, the user will not be able to recover their data from there.
More advanced options for Simplocker require the user to administer the device for their installation, which makes their further removal a difficult task. Before removing the extortionist, the user will need to revoke his extended rights. This operation is difficult because the device screen is locked.
Another notable change in the new version of the extortioner was the transfer of the attackers to the Jabber XMPP (Extensible Messaging and Presence Protocol) protocol for interacting with their C & C server manager. This protocol helps cybercriminals significantly complicate the process of tracking the transfer of traffic between the extortionist and the remote server. The extortioner Android / Simplocker uses it to send information about an infected device to a C & C server and receive commands for execution. Some modifications of this extortionist also used Tor's anonymous network .onion domains for the same purpose.
The most important step in the evolution of Simplocker was the transfer of attackers to a new encryption key storage mechanism that is used to encrypt files. A few months after the first versions appeared, we discovered new modifications of the malware using the unique encryption keys that Simplocker received from the remote server. This step marked the transition of the authors from the stage of testing the ransomware to get real profit from it, because in this case decoding the files becomes almost impossible.
Lockerpin
In previous versions of the ransomware for Android, the ability to lock the screen, as a rule, was realized by constantly drawing a window with a message about the redemption in an endless loop. Thus, the user was deprived of the opportunity to work with the device. It was possible to regain control of the device using the Android Debug Bridge (ADB) interface or disabling the administrator mode and then removing the malicious application in Safe Mode.
In the case of Android / Lockerpin , virus writers have resorted to a new sophisticated method of blocking a device by changing its PIN code. To perform this reception, the extortioner must obtain device administrator rights during his installation. After changing the PIN, the user has little chance to regain access to the device. He can access it if the device previously used a root operation (root), or the MDM tool is installed on the device. Another method of returning control over a device is its factory reset, which will destroy all data on it.
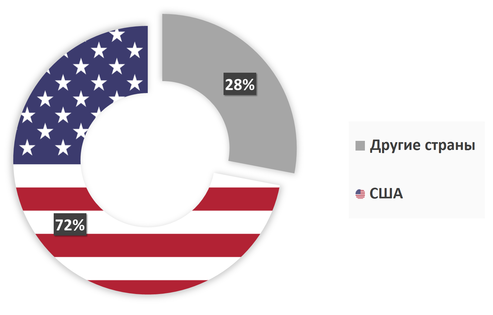
Fig. The geography of the spread of Android / Lockerpin .
According to statistics from ESET LiveGrid, the largest number of device infections falls on the United States and makes up 72% of the total number of infections. This distribution of Lockerpin infections across countries is a trend according to which attackers move from infecting users in Russia and Ukraine to the United States, where they can get more profit. The attackers disguise Lockerpin as an application for viewing porn.
Earlier versions of the Android / Locker family received device admin rights, like many other Android Trojans, which use this mechanism as protection against deletion from the OS. In doing so, they rely on the user agreeing to raise the privileges of the application to such a level when it is installed.
The latest versions of the ransomware contain a clever trick to getting device administrator rights. Lockerpin shows the user a special window asking for an “update” that overlaps the Android system window asking for confirmation of the granting of extended rights to the application. The extortion window is designed in such a way that the “Continue” button exactly coincides with the “Activate” button of the system window. Thus, the user does not initiate the installation of the update, but confirms the provision of extended rights on the device to the malicious application.

Fig. Demonstration of the used Android / Lockerpin reception by tricking a user to confirm receipt of administrator rights.
After successful installation in the system, Android / Lockerpin acts as a police extortionist. A message is displayed to the user from “law enforcement agencies” demanding a ransom of $ 500 for viewing and storing prohibited pornographic materials.
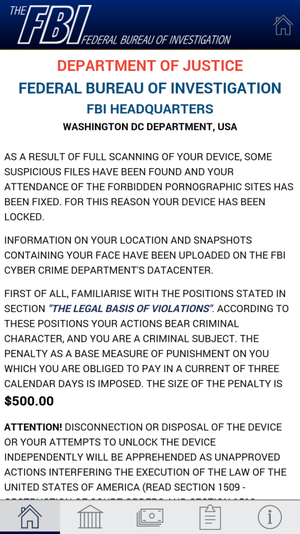
Fig. Message demanding ransom from Android / Lockerpin .
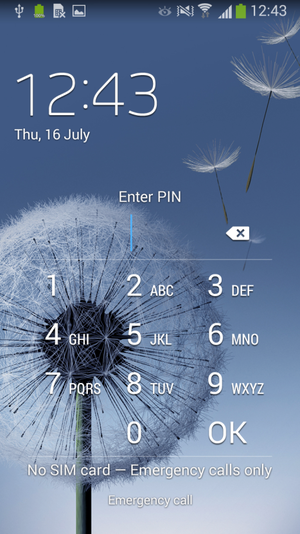
Fig. Screen lock extortioner Android / Lockerpin on a compromised device.
After a certain timeout, which follows the display of the text of the extortionist to the user, the malicious program changes the PIN code or sets it in case of absence. This PIN is a randomly generated four-digit value that is not sent to the server to attackers. Some modifications of Lockerpin are equipped with the function of resetting the set PIN code.
Lockerpin self-defense mechanisms
In addition to obtaining extended device administrator rights on the system, Android / Lockerpin also uses aggressive self-defense methods to maintain its presence on the system. To do this, the extortionist registers a callback function (callback) to re-acquire administrator rights immediately after attempting to remove them. At the same time, the user is again shown a fake window asking to install the update.
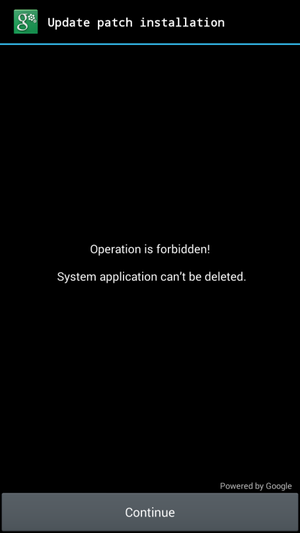
Fig. The extortionist blocks the user's attempts to revoke his administrator rights.
As an extra measure of self-defense, Lockerpin is also trying to terminate all running antivirus processes in Android. This happens when a user tries to revoke administrator rights from a malicious application. Lockerpin has the function of terminating the processes of three anti-virus programs: ESET Mobile Security, Avast and Dr.Web.
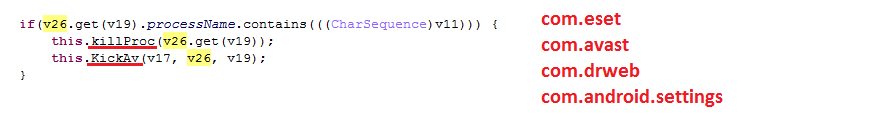
Fig. Lockerpin specializes in killing running processes.
The malicious program will not be able to terminate ESET Mobile Security processes or remove it from the system, however, it also tries to kill the com.android.settings process in order to prevent the built-in application manager from deleting the malicious application.
Jisut
The ransomware family, which ESET antivirus products detect as Android / LockScreen.Jisut , is rather strange. Unlike other ransomware who were created to gain financial gain, this modification is used as a prank. It has received the greatest distribution in China and, most likely, is the result of the work of a teenager from China.
Most extortionists require a ransom through the payment system, in which the transaction can not be traced. Malefactors choose such systems as MoneyPak, MoneXy or Bitcoin. However, the authors of Jisut have adopted a different approach, which does not imply anonymity. The extortioner's lock screen text contains the attacker's contact information for the Chinese QQ social network. The message calls the user to contact the attacker to get their files back. If the information in the QQ profiles is correct, then the age of the attackers varies from 16 to 21 years.
The first Android / LockScreen.Jisut variants began to appear in the first half of 2014. Since then, we have discovered hundreds of modifications of this malicious program that behave a little differently or display different text on the lock screen, but they are all based on the same code base. The whole family of ransomware Jisut differs from other famous ransomware type LockScreen.
One of the modifications Jisut specializes in creating a full-screen window (Activity), which overlaps all other windows. At the same time, this window is a black background, so for the user it looks as if the device is locked or turned off. In case the user calls the Android menu to shut down or reboot the device, a message is displayed in a joking way. Some modifications of the extortionist also play the music from the Psycho film by famous film director Alfred Hitchcock, causing the device to vibrate in an endless loop.
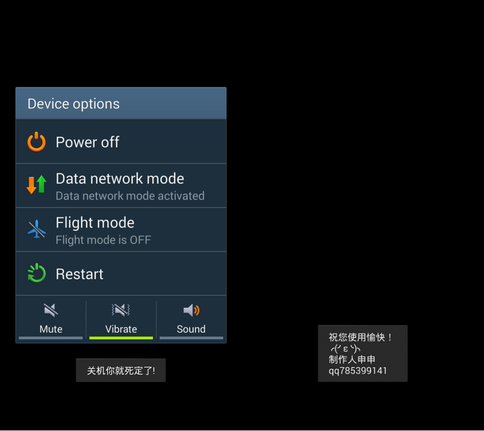
Fig. Jisut's humorous messages in Chinese: left: “Turn off, you're dead!”, Right: “I hope you have fun! Producer Shen Shen.
Another modification of Jisut asks the user to click on the button that says: “I am an idiot” a thousand times. In the case of an operation, the extortioner takes no action, while resetting the touch counter to zero.
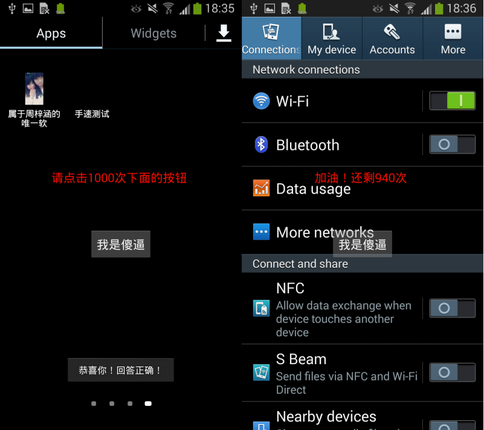
Fig. Message with the words: "Please press the button below a thousand times."
In addition to the stupid behavior of the extortioner to rally the victim, mentioned above, some of its modifications contain malicious functions. One of these functions is the ability to change the PIN-code or user password in the same way as it is done in Android / Lockerpin . Jisut can display a fake lock screen to the user, which simulates a legitimate lock screen. This latest feature has also been found in the Android / Locker and Android / Koler ransomware families .
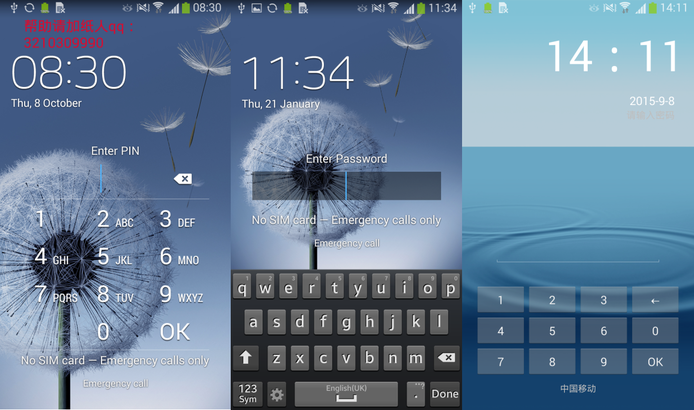
Fig. The device is locked with a change of PIN-code or password by extortioner Android / LockScreen.Jisut .
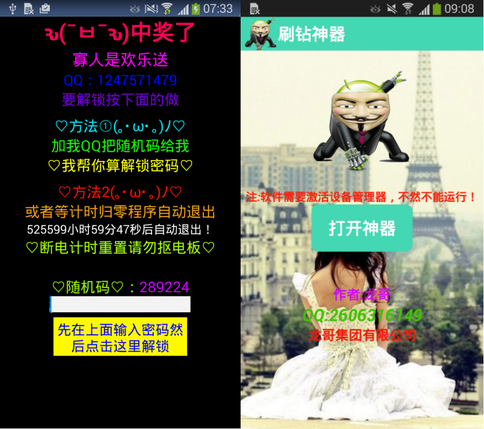
Fig. Other examples of the ransom screen lock screen.
We observed variants of Jisut, which also specialized in sending SMS messages with URL links in the text to the user's contacts.
How to protect a device running Android
For users of the Android mobile OS, it is important to be aware of information about the threat that extortionists pose, as well as about appropriate preventive measures to prevent infection. In order to protect against malware, you should avoid installing applications from informal stores, install anti-virus software on your device, and regularly update your OS and applications. In addition, the user should regularly back up important device data.
Following these rules users are unlikely to face the threat of installing malware or losing their data. Even if, for any reason, the device will be blocked by the extortioner, the current copy of the encrypted data can always be restored from a backup. In addition, you can use the following useful ways to deal with them.
For most simple families of ransomware who specialize in blocking a user's screen, loading a device in safe mode is an easy way to remove a malicious application. Since loading in this mode blocks the launch of third-party applications, malware also loses the possibility of its launch. Ways to boot the device in safe mode may vary in different models. If the extortionist uses administrative rights in the system, they must be revoked before removing the malicious application.
In the event that an extortioner with device administrator rights has locked the device using an Android PIN or password, the situation with unlocking it becomes much more complicated. In this case, it is possible to unlock the device using the Google Android Device Manager or alternatively MDM (Mobile Device Management). Devices with the root feature activated have more options for recovery in this case. As a last resort, you can use the factory reset of the device, which will delete all data on it.
When an ransomware infects you with a file encryption feature such as Android / Simplocker, we recommend that the user contact the technical support provider for the security solution they use. Depending on the specific version of the ransomware, the decryption of the files may or may not be possible.
We advise users not to fall for the bait of attackers and not to pay the required ransom amount for the following reasons. While some cybercrime groups have reached a high level of professionalism and actually decrypt user files after paying the ransom, this is not always the case. For example, authors of extortionists-cryptographers for Android try to copy many techniques of similar families for Windows (Filecoder), and they do it rather badly. For the user, this has two implications: first, even if the ransom is paid, he will not be able to decrypt the files. Secondly, in some cases, the files can be decrypted without paying the ransom.
Some of the ransomware options for Android, which we analyzed, did not contain the file decryption code and removal of the lock screen, so the ransom payment in this case also can not help.
The perception of a situation of infection with an extortioner for a single user or a corporate unit is reduced to the issue of trust. Can cybercriminals be trusted and will they really return the device and the files on it to the state prior to the infection? Obviously, no one can provide such guarantees. Even if the ransom is paid, and the data is returned, there is no guarantee that it will be compromised again. Thus, going on about the attackers of the attackers, the victim only plays the game proposed by the cybercriminals, which he will still lose.
As mentioned above, the observance of preventive measures based on basic security rules, which consist in using updated anti-virus and other software on Android, as well as data backup is the best security measure. Since there is nothing complicated about these safety rules, we see no reason why they should not be followed.


After its launch on the device, the extortionist displays a message to the user requesting a ransom, as shown in the figure below. File encryption is carried out by Simplocker in a separate program stream. The Android / Simplocker.A malware scans certain types of files on the SD card, such as images, documents, videos with the following extensions: JPEG, JPG, PNG, BMP, GIF, PDF, DOC, DOCX, TXT, AVI, MKV, 3GP, MP4. Files are encrypted using the AES symmetric cipher.
')
The encryption key itself was rigidly sewn into the body of the extortionist, with it being in an open form. Thus, it was not difficult to decrypt files and access them. For this reason, we called the family of the extortionists namely Simplocker (a simple blocker). We also believe that due to the simplicity of its implementation, it was either a proof-of-concept (PoC) threat, or an earlier version of its more complex counterpart.

Fig. Messages demanding the purchase of Android / Simplocker first versions.

Fig. For intimidation of the victim, the extortionist uses pictures of the front camera of the device.
The text of the message of the extortionist was written in Russian, and payment was required in rubles or in Ukrainian hryvnia, which indicates the orientation of the attackers to users in Ukraine. The message also told the victim how to pay the ransom. MoneXy or QIWI were indicated as payment systems, since in this case it was not as easy to track the payee as if it were made using a credit card.
Some modifications of Simplocker also displayed in the message demanding a ransom photo of the victim, which was captured by accessing the device’s camera. This method was used by attackers to increase the negative impact on the victim.
Simplocker Spread Vectors
Cybercriminals who earned Simplocker used an effective scheme to disguise a malicious application into a legitimate or known one to spread it. As a rule, the disguise was performed under an application that was related to porn, it could be an application for viewing it or the porn movie itself. In another case, the application was disguised as a game, for example, Grand Theft Auto: San Andreas or for such common applications as Flash Player.
Simplocker was distributed using a less well-known method, such as a downloader or downloader. The use of downloaders is very common in the malware world for Windows, however, for Android, this method was not popular with cybercriminals. The loader is very compact in size and is used by hackers to download the content they need (malware) onto a compromised device.
Using downloaders to distribute malware provides attackers with some advantages for hiding malicious activity from inspectors, in particular, from the program validation program for legitimacy on the part of Google Play’s Bouncer tool. This is achieved by the following properties of the loaders.
- The application specializes in performing only one function - opening a URL. In itself, such an action cannot qualify as malicious.
- The loader does not require special permissions to work in Android, as is done by “potentially dangerous applications”. Therefore, the user who controls the rights requested by the application during the installation process will not be able to recognize its true functions.
In addition, the attackers use another special trick to hide the true functions of the loader, the above URL does not directly point to the APK file. Instead, the link leads to an intermediate server, and from there it is redirected to the file download.
We did not observe the proliferation of the extortionist Simplocker by the attackers through the Google Play app store.
Simplocker in English
A month after the discovery of the first variants of Simplocker, we began to discover new versions of this extortionist, which contained several significant improvements. One of the most notable was the change in the language of the text message to display on the lock screen. English was chosen for this purpose.
To motivate the ransom payment by the user, the FBI’s blocking device was chosen for unlawful actions: using pirated software, viewing child pornography, etc. The ransom amount in the new version ranged from 200 to 500 dollars, and as a means of payment MoneyPak payment system selected. As in the previous version of Simplocker, the new modification also used pictures of the user's camera to intimidate him. This modification is detected by our anti-virus products like Android / Simplocker.I .

Fig. Messages demanding the purchase of Android / Simplocker subsequent versions in English.
Recent options for the ransomware also contained some changes. Instead of the FBI, an NSA service was chosen (NSA), which accused the victim of visiting “banned pornographic sites” and demanded $ 500 in ransom.

Fig. Messages demanding the redemption of Android / Simplocker from the NSA.
In addition to the list of files that are encrypted, various archives were included for this: ZIP, 7z, RAR. This “update” of the extortionist became very unpleasant for users, because it deprives them of access to archives with the contents of the backup data of the device, which are stored in the format of such archives. After losing access to such files, the user will not be able to recover their data from there.
More advanced options for Simplocker require the user to administer the device for their installation, which makes their further removal a difficult task. Before removing the extortionist, the user will need to revoke his extended rights. This operation is difficult because the device screen is locked.
Another notable change in the new version of the extortioner was the transfer of the attackers to the Jabber XMPP (Extensible Messaging and Presence Protocol) protocol for interacting with their C & C server manager. This protocol helps cybercriminals significantly complicate the process of tracking the transfer of traffic between the extortionist and the remote server. The extortioner Android / Simplocker uses it to send information about an infected device to a C & C server and receive commands for execution. Some modifications of this extortionist also used Tor's anonymous network .onion domains for the same purpose.
The most important step in the evolution of Simplocker was the transfer of attackers to a new encryption key storage mechanism that is used to encrypt files. A few months after the first versions appeared, we discovered new modifications of the malware using the unique encryption keys that Simplocker received from the remote server. This step marked the transition of the authors from the stage of testing the ransomware to get real profit from it, because in this case decoding the files becomes almost impossible.
Lockerpin
In previous versions of the ransomware for Android, the ability to lock the screen, as a rule, was realized by constantly drawing a window with a message about the redemption in an endless loop. Thus, the user was deprived of the opportunity to work with the device. It was possible to regain control of the device using the Android Debug Bridge (ADB) interface or disabling the administrator mode and then removing the malicious application in Safe Mode.
In the case of Android / Lockerpin , virus writers have resorted to a new sophisticated method of blocking a device by changing its PIN code. To perform this reception, the extortioner must obtain device administrator rights during his installation. After changing the PIN, the user has little chance to regain access to the device. He can access it if the device previously used a root operation (root), or the MDM tool is installed on the device. Another method of returning control over a device is its factory reset, which will destroy all data on it.

Fig. The geography of the spread of Android / Lockerpin .
According to statistics from ESET LiveGrid, the largest number of device infections falls on the United States and makes up 72% of the total number of infections. This distribution of Lockerpin infections across countries is a trend according to which attackers move from infecting users in Russia and Ukraine to the United States, where they can get more profit. The attackers disguise Lockerpin as an application for viewing porn.
Earlier versions of the Android / Locker family received device admin rights, like many other Android Trojans, which use this mechanism as protection against deletion from the OS. In doing so, they rely on the user agreeing to raise the privileges of the application to such a level when it is installed.
The latest versions of the ransomware contain a clever trick to getting device administrator rights. Lockerpin shows the user a special window asking for an “update” that overlaps the Android system window asking for confirmation of the granting of extended rights to the application. The extortion window is designed in such a way that the “Continue” button exactly coincides with the “Activate” button of the system window. Thus, the user does not initiate the installation of the update, but confirms the provision of extended rights on the device to the malicious application.

Fig. Demonstration of the used Android / Lockerpin reception by tricking a user to confirm receipt of administrator rights.
After successful installation in the system, Android / Lockerpin acts as a police extortionist. A message is displayed to the user from “law enforcement agencies” demanding a ransom of $ 500 for viewing and storing prohibited pornographic materials.

Fig. Message demanding ransom from Android / Lockerpin .

Fig. Screen lock extortioner Android / Lockerpin on a compromised device.
After a certain timeout, which follows the display of the text of the extortionist to the user, the malicious program changes the PIN code or sets it in case of absence. This PIN is a randomly generated four-digit value that is not sent to the server to attackers. Some modifications of Lockerpin are equipped with the function of resetting the set PIN code.
Lockerpin self-defense mechanisms
In addition to obtaining extended device administrator rights on the system, Android / Lockerpin also uses aggressive self-defense methods to maintain its presence on the system. To do this, the extortionist registers a callback function (callback) to re-acquire administrator rights immediately after attempting to remove them. At the same time, the user is again shown a fake window asking to install the update.

Fig. The extortionist blocks the user's attempts to revoke his administrator rights.
As an extra measure of self-defense, Lockerpin is also trying to terminate all running antivirus processes in Android. This happens when a user tries to revoke administrator rights from a malicious application. Lockerpin has the function of terminating the processes of three anti-virus programs: ESET Mobile Security, Avast and Dr.Web.

Fig. Lockerpin specializes in killing running processes.
The malicious program will not be able to terminate ESET Mobile Security processes or remove it from the system, however, it also tries to kill the com.android.settings process in order to prevent the built-in application manager from deleting the malicious application.
Jisut
The ransomware family, which ESET antivirus products detect as Android / LockScreen.Jisut , is rather strange. Unlike other ransomware who were created to gain financial gain, this modification is used as a prank. It has received the greatest distribution in China and, most likely, is the result of the work of a teenager from China.
Most extortionists require a ransom through the payment system, in which the transaction can not be traced. Malefactors choose such systems as MoneyPak, MoneXy or Bitcoin. However, the authors of Jisut have adopted a different approach, which does not imply anonymity. The extortioner's lock screen text contains the attacker's contact information for the Chinese QQ social network. The message calls the user to contact the attacker to get their files back. If the information in the QQ profiles is correct, then the age of the attackers varies from 16 to 21 years.
The first Android / LockScreen.Jisut variants began to appear in the first half of 2014. Since then, we have discovered hundreds of modifications of this malicious program that behave a little differently or display different text on the lock screen, but they are all based on the same code base. The whole family of ransomware Jisut differs from other famous ransomware type LockScreen.
One of the modifications Jisut specializes in creating a full-screen window (Activity), which overlaps all other windows. At the same time, this window is a black background, so for the user it looks as if the device is locked or turned off. In case the user calls the Android menu to shut down or reboot the device, a message is displayed in a joking way. Some modifications of the extortionist also play the music from the Psycho film by famous film director Alfred Hitchcock, causing the device to vibrate in an endless loop.

Fig. Jisut's humorous messages in Chinese: left: “Turn off, you're dead!”, Right: “I hope you have fun! Producer Shen Shen.
Another modification of Jisut asks the user to click on the button that says: “I am an idiot” a thousand times. In the case of an operation, the extortioner takes no action, while resetting the touch counter to zero.

Fig. Message with the words: "Please press the button below a thousand times."
In addition to the stupid behavior of the extortioner to rally the victim, mentioned above, some of its modifications contain malicious functions. One of these functions is the ability to change the PIN-code or user password in the same way as it is done in Android / Lockerpin . Jisut can display a fake lock screen to the user, which simulates a legitimate lock screen. This latest feature has also been found in the Android / Locker and Android / Koler ransomware families .

Fig. The device is locked with a change of PIN-code or password by extortioner Android / LockScreen.Jisut .

Fig. Other examples of the ransom screen lock screen.
We observed variants of Jisut, which also specialized in sending SMS messages with URL links in the text to the user's contacts.
How to protect a device running Android
For users of the Android mobile OS, it is important to be aware of information about the threat that extortionists pose, as well as about appropriate preventive measures to prevent infection. In order to protect against malware, you should avoid installing applications from informal stores, install anti-virus software on your device, and regularly update your OS and applications. In addition, the user should regularly back up important device data.
Following these rules users are unlikely to face the threat of installing malware or losing their data. Even if, for any reason, the device will be blocked by the extortioner, the current copy of the encrypted data can always be restored from a backup. In addition, you can use the following useful ways to deal with them.
For most simple families of ransomware who specialize in blocking a user's screen, loading a device in safe mode is an easy way to remove a malicious application. Since loading in this mode blocks the launch of third-party applications, malware also loses the possibility of its launch. Ways to boot the device in safe mode may vary in different models. If the extortionist uses administrative rights in the system, they must be revoked before removing the malicious application.
In the event that an extortioner with device administrator rights has locked the device using an Android PIN or password, the situation with unlocking it becomes much more complicated. In this case, it is possible to unlock the device using the Google Android Device Manager or alternatively MDM (Mobile Device Management). Devices with the root feature activated have more options for recovery in this case. As a last resort, you can use the factory reset of the device, which will delete all data on it.
When an ransomware infects you with a file encryption feature such as Android / Simplocker, we recommend that the user contact the technical support provider for the security solution they use. Depending on the specific version of the ransomware, the decryption of the files may or may not be possible.
We advise users not to fall for the bait of attackers and not to pay the required ransom amount for the following reasons. While some cybercrime groups have reached a high level of professionalism and actually decrypt user files after paying the ransom, this is not always the case. For example, authors of extortionists-cryptographers for Android try to copy many techniques of similar families for Windows (Filecoder), and they do it rather badly. For the user, this has two implications: first, even if the ransom is paid, he will not be able to decrypt the files. Secondly, in some cases, the files can be decrypted without paying the ransom.
Some of the ransomware options for Android, which we analyzed, did not contain the file decryption code and removal of the lock screen, so the ransom payment in this case also can not help.
The perception of a situation of infection with an extortioner for a single user or a corporate unit is reduced to the issue of trust. Can cybercriminals be trusted and will they really return the device and the files on it to the state prior to the infection? Obviously, no one can provide such guarantees. Even if the ransom is paid, and the data is returned, there is no guarantee that it will be compromised again. Thus, going on about the attackers of the attackers, the victim only plays the game proposed by the cybercriminals, which he will still lose.
As mentioned above, the observance of preventive measures based on basic security rules, which consist in using updated anti-virus and other software on Android, as well as data backup is the best security measure. Since there is nothing complicated about these safety rules, we see no reason why they should not be followed.

Source: https://habr.com/ru/post/277927/
All Articles