A bit about 2FA: Two-factor authentication

Today we decided to pay attention to the topic of two-factor authentication and talk about how it works.
Two-factor authentication, or 2FA, is a method of identifying a user in a service that uses two different types of authentication data. The introduction of an additional level of security provides a more efficient protection of your account from unauthorized access.
')
Two-factor authentication requires the user to have two of the three types of credentials.
These types are:
- Something known to him;
- Something he has;
- Something inherent to him (biometrics).
Obviously, the first paragraph includes various passwords, PIN codes, secret phrases, and so on, that is, something that the user memorizes and enters into the system upon request.
The second item is a token , that is, a compact device that is owned by the user. The simplest tokens do not require a physical connection to the computer - they have a display showing the number that the user enters into the system for logging in - the more complex ones are connected to computers via USB and Bluetooth interfaces.
Today, smartphones can act as tokens, because they have become an integral part of our life. In this case, the so-called one-time password is generated either by using a special application (for example, Google Authenticator), or comes via SMS - this is the most simple and user-friendly method, which some experts assess as less reliable.
In the course of the study, which was attended by 219 people of different sexes, ages and professions, it became known that more than half of the respondents use two-factor SMS authentication in social networks (54.48%) and when working with finances (69.42%) .
However, when it comes to business issues, tokens are preferred (45.36%). But what is interesting is that the number of respondents using these technologies both voluntarily and by order of the authorities (or due to other compelling circumstances) is about the same.
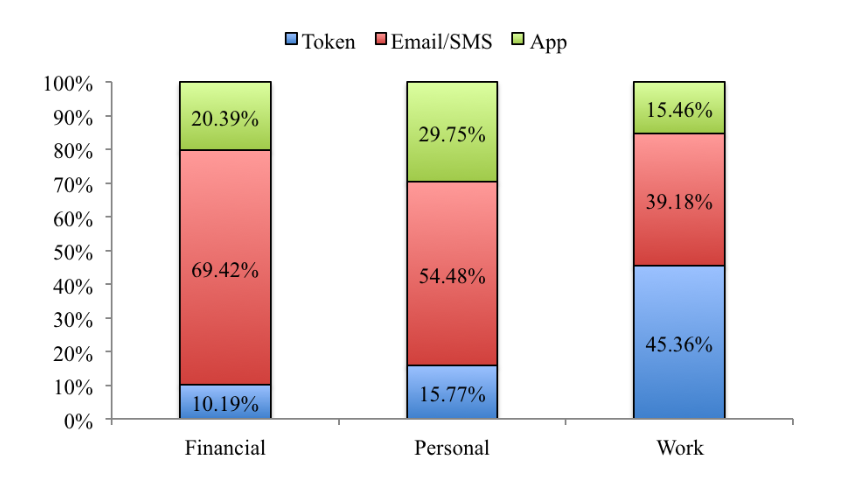
Graph of the popularity of various technologies by fields of activity
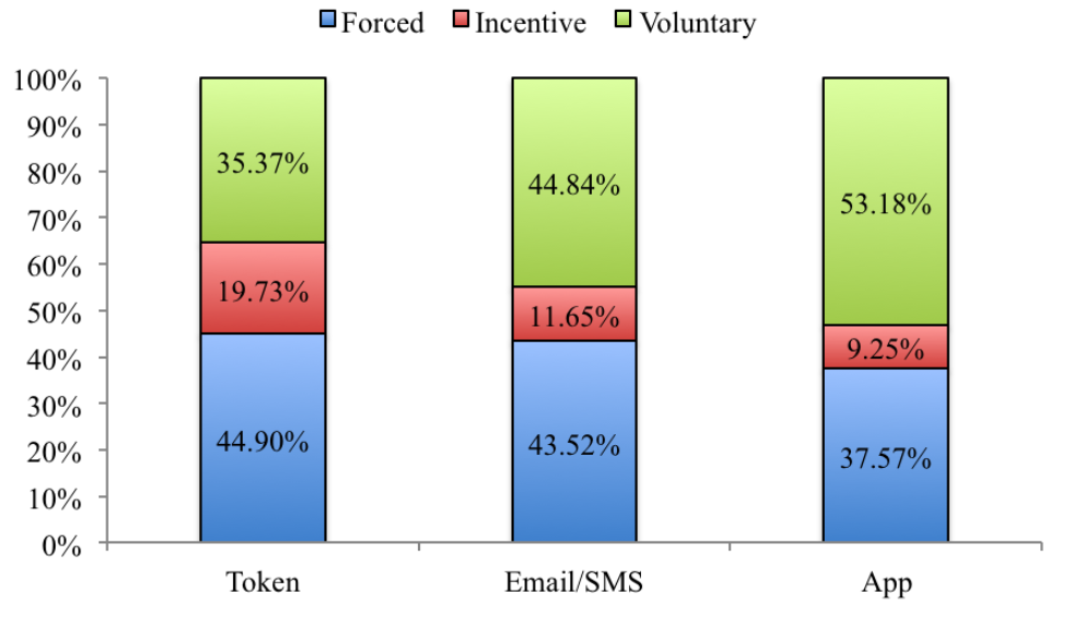
Schedule of interest of respondents in 2FA
Among the tokens can be distinguished one-time passwords synchronized in time, and one-time passwords based on a mathematical algorithm. Time-synchronized one-time passwords are constantly and periodically changed. These tokens are stored in memory the number of seconds elapsed since January 1, 1970, and display part of this number on the display.
For a user to log in, a synchronization must exist between the client token and the authentication server. The main problem is that over time they can become out of sync, however some systems, such as RSA’s SecurID, make it possible to resynchronize the token with the server by entering several access codes. Moreover, many of these devices do not have replaceable batteries, therefore they have a limited service life.
As the name implies, passwords based on a mathematical algorithm use algorithms (for example, a chain of hashes) to generate a series of one-time passwords using a secret key. In this case, it is impossible to predict what the next password will be, even knowing all the previous ones.
Sometimes 2FA is implemented using biometric devices and authentication methods (third paragraph). These can be, for example, scanners of the face, fingerprints, or retina.
The problem here is that such technologies are very expensive, although accurate. Another problem with the use of biometric scanners is the obviousness of determining the required degree of accuracy.
If you set the resolution of the fingerprint scanner to a maximum, then you risk not having access to the service or device if you have been burned or your hands are simply frozen. Therefore, for the successful confirmation of this authenticator, it is sufficient to incompletely match the print to the standard. It is also worth noting that it is physically impossible to change this “bioparol”.
How reliable is two-factor authentication?
This is a good question. 2FA is not impenetrable for intruders, but it seriously complicates their lives. “Using 2FA you exclude a fairly large category of attacks,” says Jim Fenton, director of security for OneID. In order to crack two-factor authentication, the “bad guys” will have to steal your fingerprints or gain access to cookies or codes generated by tokens.
The latter can be achieved, for example, with the help of phishing attacks or malicious software. There is another unusual way: access to Wired journalist Matt Honnan’s account (Matt Honnan) was achieved by attackers using the account recovery feature.
Account recovery serves as a tool for circumventing two-factor authentication. Fenton, after the story with Matt, personally created an account with Google, activated 2FA and pretended that he “lost” the login information. “The account recovery took some time, but after three days I received a letter that 2FA was disabled,” Fenton notes. However, this problem has solutions. At least they are working on them.
“I think biometrics is one of those ways,” says Duo Security CTO John Oberheide. - If I lose my phone, then to restore all accounts I will not have enough eternity. If there was a good biometric method, it would become a reliable and useful recovery mechanism. ” In essence, John suggests using one form of 2FA for authentication, and another for recovery.
Where 2FA is applied
Here are some of the main services and social networks that offer this feature - Facebook, Gmail, Twitter, LinkedIn, Steam. Their developers offer a choice: SMS authentication, one-time password list, Google Authenticator, etc. Recently 2FA introduced Instagram to protect all your photos.
However, there is an interesting point. It should be borne in mind that two-factor authentication adds another additional step to the authentication process, and, depending on the implementation, this can cause both minor difficulties with entering (or not causing them at all) and serious problems.
For the most part, this attitude depends on the user's patience and the desire to increase the security of the account. Fenton made the following thought: “2FA is a good thing, but it can make life difficult for users. Therefore, it makes sense to enter it only for those cases when the input is from an unknown device. ”
Two-factor authentication is not a panacea, but it helps to significantly increase the security of your account, spending a minimum of effort. Complicating the life of hackers is always good, because using 2FA is possible and necessary.
What awaits 2FA
Protection methods based on multifactor authentication methods today are trusted by a large number of companies, including high-tech organizations, financial and insurance sectors of the market, large banking institutions and public sector enterprises, independent expert organizations, and research firms.

Oberhaide notes that many users who were skeptical about two-factor authentication, very soon found that everything is not so difficult. Today 2FA is experiencing a real boom, and any popular technology is much easier to improve. Despite the presence of difficulties, it is waiting for a bright future.
PS By the way, we recently introduced two-factor authentication to increase the security of your 1cloud account . After activating this method, to enter the control panel, the user needs not only to enter an email address and password, but also a unique code received via SMS.
Source: https://habr.com/ru/post/277901/
All Articles