Anatomy of ransomware for Android, part 1
Extortionists (ransomware) are a special type of malware for mobile devices, the number of which is constantly growing. The extortionists can be divided into two large groups: the former specialize in locking the screen of the user's device (lock-screen ransomware), and the latter encrypt data on it (crypto-ransomware). For several years of their activity, both of these types have already led to significant financial losses for users, as well as the loss of their personal data.

Like other types of malware for Android, such as SMS Trojans, for example, extortionists have evolved significantly over the past few years, while VX authors have adapted many malicious techniques that have proven effective in similar malware for desktop systems.
')
General information
Extortionists for both Windows and Android use the theme of “police ransomware” (police ransomware) as the theme for the lock screen. This topic is quite effective, as the attackers use the user's guilt feeling, accusing him of viewing or storing illegal content on the device. Mobile extortionists have similar features with the infamous family of such malicious programs for Windows as Cryptolocker, for example, they use strong cryptographic algorithms to encrypt files in such a way that the user does not have a way to restore access to encrypted files. Since the user stores a much larger amount of personal data on a smartphone, the risk of losing a significant amount of user data increases significantly.
One of the interesting observations that we managed to do was to change the geographical orientation of the attackers from Eastern European countries to other countries. For example, the vast majority of ransomware victims of the Android / Simplocker and Android / Lockerpin families are located in the USA.
Both of the aforementioned types of ransomware were a very common problem for Windows users since 2013, when the popularity of these malicious programs among cybercriminals began to increase significantly, despite the fact that they were distributed much earlier. Infection extortionists brought serious trouble for both ordinary users and corporate users.
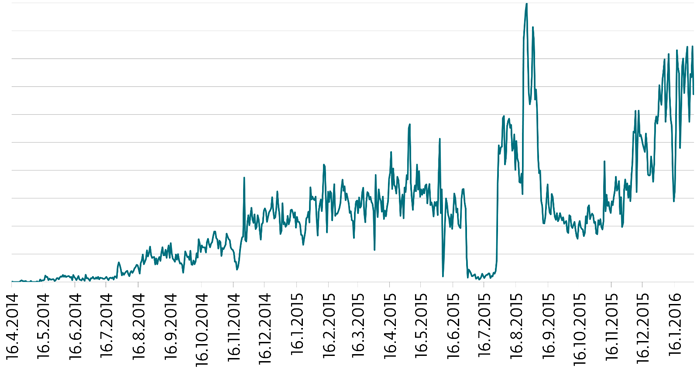
Fig. Statistics of ransomware for Android according to ESET LiveGrid.
The use of ransomware by the attackers specifically for Android is not an accident. Since the number of smartphones on this OS is growing from year to year, users are increasingly choosing them to store personal and valuable data. Accordingly, such a business will bring them the maximum amount of benefits.
Possible vectors of infection
Attackers use the same disguise for extortionists Android, as well as for other malicious programs, which is that the user is convinced of the legitimacy of the application. Various popular applications, such as games, as well as porn-related applications, are often chosen as a cover and to increase the likelihood of a potential victim being compromised. In some cases, malicious APK files are provided with an icon and the name of a legitimate application. Another scenario involves the direct use by the attackers of a legitimate application into which the malicious code is inserted, while the original functions of the application are preserved. The behavior of the malicious program may be imperceptible to the user of the device, this happens when the authors do not rely on the screen lock mechanism or file encryption, as is the case with backdoors or SMS trojans. It should be noted that such a change in a legitimate application will lead to its violation of the integrity and inconsistency of the data specified in the digital signature.
It should be noted that none of the ransomware described by us was found in the Google Play app store. However, there are cases of successful crawling by malware of constantly improving Google security measures for the Play Store. Our analysts found and sent to Google hundreds of examples of malware for Android, including such malicious software as Fake AV, spyware with credential theft functions, click-click trojans, backdoors, potentially unwanted applications (PUA) with advertisements, and other PUA- applications and others. Virus writers also use special methods of infecting the device in such a way as to postpone the actual payload by using loaders (downloaders), as well as droppers. On the other hand, the use of such advanced techniques as the automatic installation of drive-by download malware is not common in Android.
Interaction with the C & C Server Manager
After successful installation on the system, most of the malware for Android reports this to "home", i.e., to a remote C & C server. Typically, this sent message includes some basic information about the device, such as the device model, IMEI number, language used, etc. If a permanent connection is established between the C & C server and the bot, the attacker can send him commands to execute . Thus, the attacker can control the botnet of devices running Android.
Some examples of remote commands that support extortionists for Android are listed below:
Typically, the HTTP protocol is used to communicate with the remote server, but in some cases we also observed using a public service such as Google Cloud Messaging to interact with C & C. This service allows Android applications on smartphones to share data. Baidu Cloud Push is also used for malicious purposes. Some of the malware samples that we analyzed used the anonymous Tor service (.onion domains) and the XMPP protocol (jabber). Trojans for Android can receive commands and send data remotely using SMS messages.
Self defense methods
The task of infecting a user's device running Android with a malicious program is not a trivial task for attackers. Even for users without an established anti-virus solution, such as ESET Mobile Security , there are mechanisms to protect against the malware of the OS itself. After the attackers bypass the defense mechanisms, they are interested in the malware remaining there as long as possible.
We observed the use by Android malware of various self-defense mechanisms that prevented disruption or removal from the system. For example, the extortioner Android / Lockerpin could freelance complete the process of antivirus solutions. One of the most universal methods that we observe in using virus writers, and more and more, is obtaining Device Administrator privileges. Despite the fact that this mode of operation is not as dangerous as obtaining root rights, it still provides attackers with extended privileges after being acquired on the device.
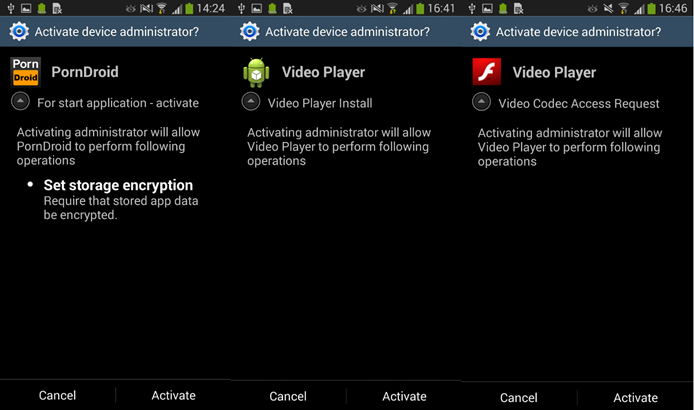
Fig. Examples of malware for Android that requests administrator rights in the system.
Legitimate applications with device administrator privileges use such extended permissions in the OS for various purposes, which are usually related to security. Malicious applications, in contrast, use them to protect themselves from being removed from the system. Before removing such an application from Android, its Administrator rights must be revoked. Some malicious programs, such as Android / Lockerpin , use their privileges to set or change the PIN of the lock screen.

Fig. Chronology of the appearance of ransomware for Android.
The first cases of the appearance of ransomware for Android were accompanied by the addition of malicious functions to fake antivirus programs. Such fake antiviruses have been distributed for a long time, starting in 2012 for Android and since 2004 for computers. As the name implies, such programs show the user fake messages about scanning files on the device, and then try to deceive him by displaying a message demanding payment for further anti-virus actions to neutralize the threat. These programs are also called “scareware” because they extort money from the victim after being intimidated by the presence of an active infection of the device.
Most ransomware with a screen lock feature for Windows use the theme of law enforcement (police ransomware) when intimidating a user. The attackers began using a similar method in extortionists and for Android. This type of extortionists significantly increases the possibility of successfully extorting money from the user, since the victim is addressed on behalf of law enforcement agencies, and they are informed that illegal actions were detected on the device.
The first version of the extortionist cryptographer for Android was a family of malware called Simplocker in May 2014. For the past three years, extortionists for Android have continued their development, during which time several new families of this malware have been discovered.
Android Defender
This malware was first detected in mid-2013 and is an example of a fake antivirus for Android, as well as, in fact, the first extortionist for Android. As can be seen in the figure below, the user interface of the malicious application attempts to imitate its legitimate counterpart. Malefactors provide such function for belief of the user in legitimacy of an antivirus. It is interesting to note that during a fake scan of files on a disk, the trojan displays the names of files actually present on the memory card, which makes this process even more plausible in the eyes of the user. The names of the malware families are also indicated as existing, however, they have nothing to do with the user's device.
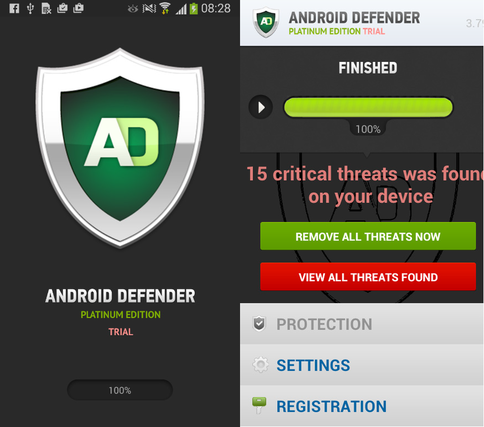
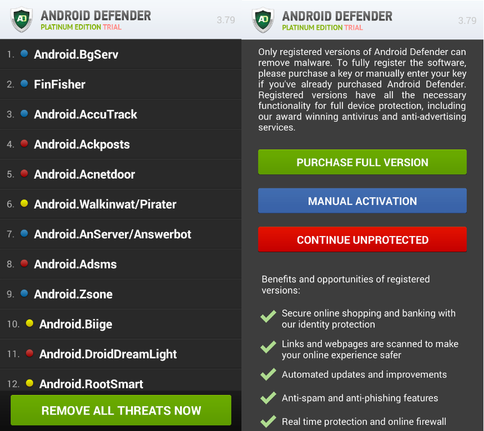
Fig. The appearance of a fake antivirus Android Defender (Fake AV).
At this stage, the user still has access to the setting called “continuing unprotected”, and can also close the application. However, running an auxiliary OS service, which belongs to a fake antivirus, makes the smartphone almost unusable, constantly displaying special warning windows every time a user tries to launch an application. By selecting the “Stay unprotected” setting, the user will only save himself from the current pop-up window, while immediately receiving a new one.
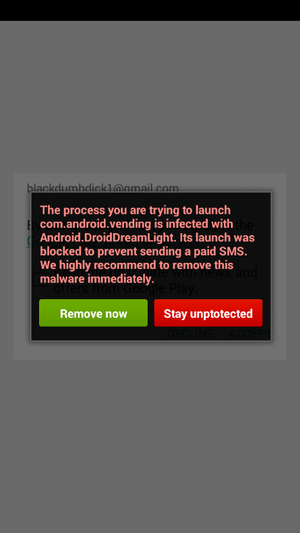
Fig. The message fixed by malicious program deprives the user of possibility of normal work with the device.
In the event that the smartphone owner gives in to the trick of the intruders and decides to pay the required amount to upgrade to the “full version of the antivirus”, his disappointments do not end there. Six hours after its launch in the system, the malware will display a window with pornographic pictures on the entire screen of the device, which cannot be closed.
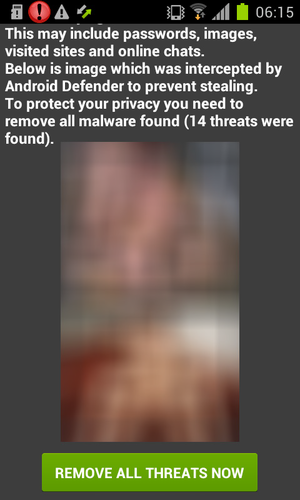
Fig. Android Defender lock screen with porn picture.
When paying, the owner of the smartphone also leaves the attackers with their credit card information, which can be used to conduct fraudulent transactions. As indicated in the screenshot, scammers offer the user a discount, reducing the amount to $ 89.99.
Antivirus product ESET Mobile Security detects Android Defender as Android / FakeAV.B .
Extortionist with fake anti-virus and porn features
Another type of extortionist in the form of a fake antivirus does not copy the interface of the Android Defender product, but the name of the legitimate Avast security application. This is a malicious program that is detected by ESET antivirus products like Android / FakeAV.E . She uses the brand of the famous PornHub resource to find her audience among the visitors of this resource.

Fig. Extortionist disguised as an application for viewing porn.
After starting the application, the user receives a message instead of viewing pornographic clips that his device needs to be checked for viruses. After clicking on the OK button, a fake antivirus that looks like Avast starts a pseudo-scan.


Fig. Extortionist Android / FakeAV.E disguises itself as a fake Avast antivirus application.
The information that fraudsters display to the user is rather strange. First, the message itself shows that "the device is in danger and has been blocked for security reasons." Further, it is proposed to purchase an enhanced version of pseudo-security software. This behavior gives the user the true intentions of the software he received, since the blocking of the device is clearly not consistent with the functions of a legitimate antivirus. The message screen displayed to the user requires him to pay a fine of $ 100 to avoid possible legal consequences.

Fig. Payment redemption for Android / FakeAV.E .
We got the impression that the authors of this extortioner copied the text of a message demanding ransom from another malicious program, since the text contains the same grammatical errors.
Police Extortionists
Extortionists for Windows used various themes to demonstrate as a lock screen. Some earlier patterns used the blue screen theme of death (BSOD) or the Windows activation message. We found various topics that the attackers used for the screen lock, however, the most common of these was the topic of law enforcement (police).
Such police extortionists claimed that the device was blocked by local law enforcement agencies, as illegal content was found on it, or illegal activities were carried out from the device. As the text for the lock screen was used, sometimes, taken from the article of the criminal code. The text also stated that if you pay the appropriate amount, the user is discharged. This type of ransomware often uses IP-based geolocation to select the desired banner with the law enforcement icon of the desired state.

Fig. The first police extortionist was aimed at Russian-speaking Android users.
The first copies of police extortionists for Android appeared in the first half of 2014 and were directed against Russian-speaking users. Shortly thereafter, variants in English were discovered.


Fig. The extortioner Android / Locker uses camera images and geolocation to intimidate the user, with examples of lock screens for Russia, Ukraine, and Kazakhstan.


Fig. Extortionist Android / Koler switched to compromising English-speaking users.
ESET antivirus products detect instances of the above ransomware like Android / Koler and Android / Locker .

Like other types of malware for Android, such as SMS Trojans, for example, extortionists have evolved significantly over the past few years, while VX authors have adapted many malicious techniques that have proven effective in similar malware for desktop systems.
')
General information
Extortionists for both Windows and Android use the theme of “police ransomware” (police ransomware) as the theme for the lock screen. This topic is quite effective, as the attackers use the user's guilt feeling, accusing him of viewing or storing illegal content on the device. Mobile extortionists have similar features with the infamous family of such malicious programs for Windows as Cryptolocker, for example, they use strong cryptographic algorithms to encrypt files in such a way that the user does not have a way to restore access to encrypted files. Since the user stores a much larger amount of personal data on a smartphone, the risk of losing a significant amount of user data increases significantly.
One of the interesting observations that we managed to do was to change the geographical orientation of the attackers from Eastern European countries to other countries. For example, the vast majority of ransomware victims of the Android / Simplocker and Android / Lockerpin families are located in the USA.
Both of the aforementioned types of ransomware were a very common problem for Windows users since 2013, when the popularity of these malicious programs among cybercriminals began to increase significantly, despite the fact that they were distributed much earlier. Infection extortionists brought serious trouble for both ordinary users and corporate users.

Fig. Statistics of ransomware for Android according to ESET LiveGrid.
The use of ransomware by the attackers specifically for Android is not an accident. Since the number of smartphones on this OS is growing from year to year, users are increasingly choosing them to store personal and valuable data. Accordingly, such a business will bring them the maximum amount of benefits.
Possible vectors of infection
Attackers use the same disguise for extortionists Android, as well as for other malicious programs, which is that the user is convinced of the legitimacy of the application. Various popular applications, such as games, as well as porn-related applications, are often chosen as a cover and to increase the likelihood of a potential victim being compromised. In some cases, malicious APK files are provided with an icon and the name of a legitimate application. Another scenario involves the direct use by the attackers of a legitimate application into which the malicious code is inserted, while the original functions of the application are preserved. The behavior of the malicious program may be imperceptible to the user of the device, this happens when the authors do not rely on the screen lock mechanism or file encryption, as is the case with backdoors or SMS trojans. It should be noted that such a change in a legitimate application will lead to its violation of the integrity and inconsistency of the data specified in the digital signature.
It should be noted that none of the ransomware described by us was found in the Google Play app store. However, there are cases of successful crawling by malware of constantly improving Google security measures for the Play Store. Our analysts found and sent to Google hundreds of examples of malware for Android, including such malicious software as Fake AV, spyware with credential theft functions, click-click trojans, backdoors, potentially unwanted applications (PUA) with advertisements, and other PUA- applications and others. Virus writers also use special methods of infecting the device in such a way as to postpone the actual payload by using loaders (downloaders), as well as droppers. On the other hand, the use of such advanced techniques as the automatic installation of drive-by download malware is not common in Android.
Interaction with the C & C Server Manager
After successful installation on the system, most of the malware for Android reports this to "home", i.e., to a remote C & C server. Typically, this sent message includes some basic information about the device, such as the device model, IMEI number, language used, etc. If a permanent connection is established between the C & C server and the bot, the attacker can send him commands to execute . Thus, the attacker can control the botnet of devices running Android.
Some examples of remote commands that support extortionists for Android are listed below:
- open the required URL in a web browser;
- send an SMS message to all contacts;
- lock or unlock the device;
- send SMS messages from the device to attackers;
- send the attackers contact information to the victim;
- select the desired text message with a ransom request;
- upgrade to the new version;
- enable or disable storage of data on the device;
- enable or disable Wi-Fi connection;
- Track the user's geographic location using GPS.
Typically, the HTTP protocol is used to communicate with the remote server, but in some cases we also observed using a public service such as Google Cloud Messaging to interact with C & C. This service allows Android applications on smartphones to share data. Baidu Cloud Push is also used for malicious purposes. Some of the malware samples that we analyzed used the anonymous Tor service (.onion domains) and the XMPP protocol (jabber). Trojans for Android can receive commands and send data remotely using SMS messages.
Self defense methods
The task of infecting a user's device running Android with a malicious program is not a trivial task for attackers. Even for users without an established anti-virus solution, such as ESET Mobile Security , there are mechanisms to protect against the malware of the OS itself. After the attackers bypass the defense mechanisms, they are interested in the malware remaining there as long as possible.
We observed the use by Android malware of various self-defense mechanisms that prevented disruption or removal from the system. For example, the extortioner Android / Lockerpin could freelance complete the process of antivirus solutions. One of the most universal methods that we observe in using virus writers, and more and more, is obtaining Device Administrator privileges. Despite the fact that this mode of operation is not as dangerous as obtaining root rights, it still provides attackers with extended privileges after being acquired on the device.

Fig. Examples of malware for Android that requests administrator rights in the system.
Legitimate applications with device administrator privileges use such extended permissions in the OS for various purposes, which are usually related to security. Malicious applications, in contrast, use them to protect themselves from being removed from the system. Before removing such an application from Android, its Administrator rights must be revoked. Some malicious programs, such as Android / Lockerpin , use their privileges to set or change the PIN of the lock screen.

Fig. Chronology of the appearance of ransomware for Android.
The first cases of the appearance of ransomware for Android were accompanied by the addition of malicious functions to fake antivirus programs. Such fake antiviruses have been distributed for a long time, starting in 2012 for Android and since 2004 for computers. As the name implies, such programs show the user fake messages about scanning files on the device, and then try to deceive him by displaying a message demanding payment for further anti-virus actions to neutralize the threat. These programs are also called “scareware” because they extort money from the victim after being intimidated by the presence of an active infection of the device.
Most ransomware with a screen lock feature for Windows use the theme of law enforcement (police ransomware) when intimidating a user. The attackers began using a similar method in extortionists and for Android. This type of extortionists significantly increases the possibility of successfully extorting money from the user, since the victim is addressed on behalf of law enforcement agencies, and they are informed that illegal actions were detected on the device.
The first version of the extortionist cryptographer for Android was a family of malware called Simplocker in May 2014. For the past three years, extortionists for Android have continued their development, during which time several new families of this malware have been discovered.
Android Defender
This malware was first detected in mid-2013 and is an example of a fake antivirus for Android, as well as, in fact, the first extortionist for Android. As can be seen in the figure below, the user interface of the malicious application attempts to imitate its legitimate counterpart. Malefactors provide such function for belief of the user in legitimacy of an antivirus. It is interesting to note that during a fake scan of files on a disk, the trojan displays the names of files actually present on the memory card, which makes this process even more plausible in the eyes of the user. The names of the malware families are also indicated as existing, however, they have nothing to do with the user's device.


Fig. The appearance of a fake antivirus Android Defender (Fake AV).
At this stage, the user still has access to the setting called “continuing unprotected”, and can also close the application. However, running an auxiliary OS service, which belongs to a fake antivirus, makes the smartphone almost unusable, constantly displaying special warning windows every time a user tries to launch an application. By selecting the “Stay unprotected” setting, the user will only save himself from the current pop-up window, while immediately receiving a new one.

Fig. The message fixed by malicious program deprives the user of possibility of normal work with the device.
In the event that the smartphone owner gives in to the trick of the intruders and decides to pay the required amount to upgrade to the “full version of the antivirus”, his disappointments do not end there. Six hours after its launch in the system, the malware will display a window with pornographic pictures on the entire screen of the device, which cannot be closed.

Fig. Android Defender lock screen with porn picture.
When paying, the owner of the smartphone also leaves the attackers with their credit card information, which can be used to conduct fraudulent transactions. As indicated in the screenshot, scammers offer the user a discount, reducing the amount to $ 89.99.
Antivirus product ESET Mobile Security detects Android Defender as Android / FakeAV.B .
Extortionist with fake anti-virus and porn features
Another type of extortionist in the form of a fake antivirus does not copy the interface of the Android Defender product, but the name of the legitimate Avast security application. This is a malicious program that is detected by ESET antivirus products like Android / FakeAV.E . She uses the brand of the famous PornHub resource to find her audience among the visitors of this resource.

Fig. Extortionist disguised as an application for viewing porn.
After starting the application, the user receives a message instead of viewing pornographic clips that his device needs to be checked for viruses. After clicking on the OK button, a fake antivirus that looks like Avast starts a pseudo-scan.


Fig. Extortionist Android / FakeAV.E disguises itself as a fake Avast antivirus application.
The information that fraudsters display to the user is rather strange. First, the message itself shows that "the device is in danger and has been blocked for security reasons." Further, it is proposed to purchase an enhanced version of pseudo-security software. This behavior gives the user the true intentions of the software he received, since the blocking of the device is clearly not consistent with the functions of a legitimate antivirus. The message screen displayed to the user requires him to pay a fine of $ 100 to avoid possible legal consequences.

Fig. Payment redemption for Android / FakeAV.E .
We got the impression that the authors of this extortioner copied the text of a message demanding ransom from another malicious program, since the text contains the same grammatical errors.
Police Extortionists
Extortionists for Windows used various themes to demonstrate as a lock screen. Some earlier patterns used the blue screen theme of death (BSOD) or the Windows activation message. We found various topics that the attackers used for the screen lock, however, the most common of these was the topic of law enforcement (police).
Such police extortionists claimed that the device was blocked by local law enforcement agencies, as illegal content was found on it, or illegal activities were carried out from the device. As the text for the lock screen was used, sometimes, taken from the article of the criminal code. The text also stated that if you pay the appropriate amount, the user is discharged. This type of ransomware often uses IP-based geolocation to select the desired banner with the law enforcement icon of the desired state.

Fig. The first police extortionist was aimed at Russian-speaking Android users.
The first copies of police extortionists for Android appeared in the first half of 2014 and were directed against Russian-speaking users. Shortly thereafter, variants in English were discovered.


Fig. The extortioner Android / Locker uses camera images and geolocation to intimidate the user, with examples of lock screens for Russia, Ukraine, and Kazakhstan.


Fig. Extortionist Android / Koler switched to compromising English-speaking users.
ESET antivirus products detect instances of the above ransomware like Android / Koler and Android / Locker .
Source: https://habr.com/ru/post/277747/
All Articles