Zabbix 3.0: Encryption
We continue to review the new features of 3.0, we have already managed to tell you about the capabilities of the new version, separately dwelled on the possibility of predicting problems based on the collected statistics, and today we will talk about encryption.
Encryption was one of the most long-awaited and expected innovations in Zabbix, and during this time we had time to discuss several options for its implementation: from authentication using a pre-PSK key to full support for TLS and Kerberos. A year ago, it was decided to stop at TLS.
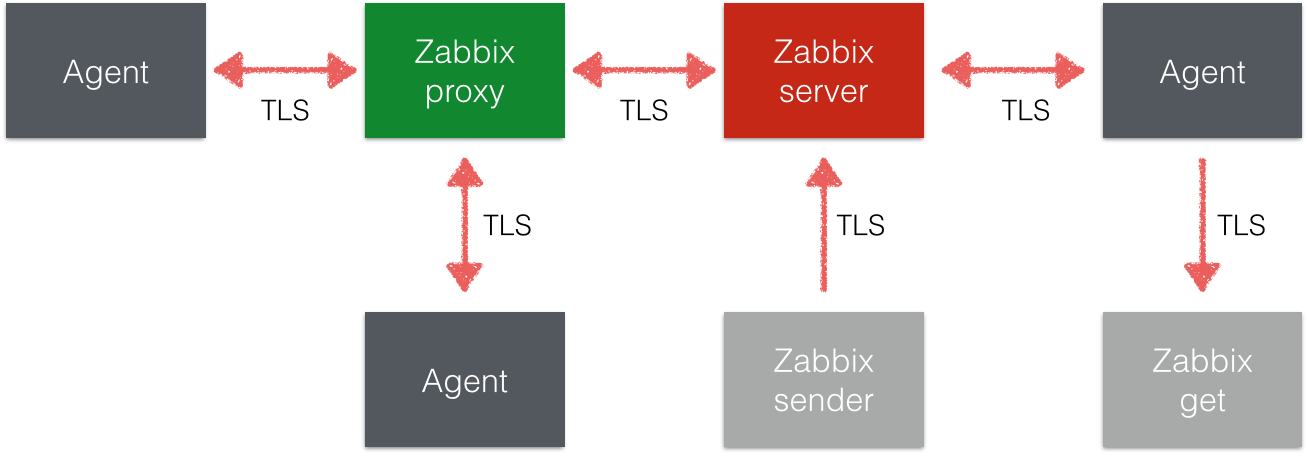
And now in Zabbix 3.0 all components, such as server, agent and proxy, can be configured to use encryption, or can continue to communicate openly, as before. All this makes it possible to use Zabbix in those systems where encryption between nodes is imperative. In addition, support for secure connections has been added for command line utilities, such as zabbix_sender and zabbix_get.
Zabbix can use one of the following libraries for encryption: OpenSSL , GnuTLS or mbedTLS (PolarSSL). Such a decision was first made in order to always be able to change the library, if a critical vulnerability is found in the one used, the license type changes, or the development and support ends. Another advantage is the neutrality of Zabbix to any of the listed sets.
')
TLS is supported by version 1.2 - previous versions of the SSL / TLS protocol contained vulnerabilities, so we considered using them a bad idea.
In addition to hiding transmitted messages from outsiders, authentication is also implemented. Now it is possible to get answers to the questions “Can I trust the data source” or “Do we send a file with a list of passwords to our server?” You can choose from for authentication: using a certificate (for those who have a public key infrastructure or high security requirements) or a PSK key (for small installations).
There is no need to open any new ports - only the standard for Zabbix TCP / 10050-10051 are still used.
If the user is not interested in encryption, then you can continue to use Zabbix as before. At the same time, the updated Zabbix components will support the new feature, so you can start setting up secure connections at any time convenient for you.
It is also important to note that we have added several new fields in the Zabbix database tables in order to store additional settings, made it possible to modify them via the web (logically) or API, and also added new parameters in the configuration files.
An example of setting encryption is shown in the following screenshot.

Two parameters define how the server or proxy connects to the agent (for passive checks, "Connections to host") and a separate parameter that determines which types of connections are allowed from the agent (active checks and zabbix_sender, "Connections from host"). “Connections from host” is also used to limit server connections from those who got a stolen certificate or found out PSK.
On the part of agents and utilities zabbix_get, zabbix_sender, the encryption setting is performed through the new parameters of the configuration files or command line arguments.
At the time of testing, it is possible to allow several types of connections at once (ie, open and secure), further configure encryption and authentication based on a certificate or PSK, make sure everything works, and, finally, prohibit unencrypted connections.
At the same time, of course there is still something to work on, for example:
Support for encryption and mutual authentication in Zabbix enables users to gradually and selectively improve the security of the monitoring system components. We suggest you try it yourself and other innovations . The full specification on encryption can be found in the documentation , well, and read about the other innovations in Zabbix on Habré, if you suddenly missed it.
Translation of an article from our blog.
Encryption was one of the most long-awaited and expected innovations in Zabbix, and during this time we had time to discuss several options for its implementation: from authentication using a pre-PSK key to full support for TLS and Kerberos. A year ago, it was decided to stop at TLS.

And now in Zabbix 3.0 all components, such as server, agent and proxy, can be configured to use encryption, or can continue to communicate openly, as before. All this makes it possible to use Zabbix in those systems where encryption between nodes is imperative. In addition, support for secure connections has been added for command line utilities, such as zabbix_sender and zabbix_get.
Technical details
Zabbix can use one of the following libraries for encryption: OpenSSL , GnuTLS or mbedTLS (PolarSSL). Such a decision was first made in order to always be able to change the library, if a critical vulnerability is found in the one used, the license type changes, or the development and support ends. Another advantage is the neutrality of Zabbix to any of the listed sets.
')
TLS is supported by version 1.2 - previous versions of the SSL / TLS protocol contained vulnerabilities, so we considered using them a bad idea.
In addition to hiding transmitted messages from outsiders, authentication is also implemented. Now it is possible to get answers to the questions “Can I trust the data source” or “Do we send a file with a list of passwords to our server?” You can choose from for authentication: using a certificate (for those who have a public key infrastructure or high security requirements) or a PSK key (for small installations).
There is no need to open any new ports - only the standard for Zabbix TCP / 10050-10051 are still used.
If the user is not interested in encryption, then you can continue to use Zabbix as before. At the same time, the updated Zabbix components will support the new feature, so you can start setting up secure connections at any time convenient for you.
It is also important to note that we have added several new fields in the Zabbix database tables in order to store additional settings, made it possible to modify them via the web (logically) or API, and also added new parameters in the configuration files.
An example of setting encryption is shown in the following screenshot.

Two parameters define how the server or proxy connects to the agent (for passive checks, "Connections to host") and a separate parameter that determines which types of connections are allowed from the agent (active checks and zabbix_sender, "Connections from host"). “Connections from host” is also used to limit server connections from those who got a stolen certificate or found out PSK.
On the part of agents and utilities zabbix_get, zabbix_sender, the encryption setting is performed through the new parameters of the configuration files or command line arguments.
At the time of testing, it is possible to allow several types of connections at once (ie, open and secure), further configure encryption and authentication based on a certificate or PSK, make sure everything works, and, finally, prohibit unencrypted connections.
Subsequent improvements
At the same time, of course there is still something to work on, for example:
- Currently, reusing TLS sessions via caching is not supported, so now every connection initiates a connection from scratch, which is naturally slower.
- Add encryption support for Zabbix Java gateway.
- Support for X.509 certificates with RSA keys is now implemented. ECDSA certificate support should help improve performance.
- Revoked certificates can only be checked through CRL files, the online verification of the publisher is not currently implemented.
Support for encryption and mutual authentication in Zabbix enables users to gradually and selectively improve the security of the monitoring system components. We suggest you try it yourself and other innovations . The full specification on encryption can be found in the documentation , well, and read about the other innovations in Zabbix on Habré, if you suddenly missed it.
Translation of an article from our blog.
Source: https://habr.com/ru/post/277739/
All Articles