50 shades of paranoia or how to store passwords without saving
Hi% username%
Each of us goes through several stages ofparanoia storing passwords. At the first stage, the process of inventing a not simple, but memorable password. On the second, a second password appears and one becomes personal (any private mailboxes), and the second is public (forums, social networks, etc.). With two passwords, additional mailboxes appear - personal and public. On the third, the thought comes that it is worth creating a password for each resource, but since human memory is limited in memorization, programs for storing passwords appear in the arsenal and master passwords are created for them, someone uses file keys that also password-protected, and amidst all this you begin to understand that you can dig in passwords and passwords for passwords infinitely deeply. If you are interested in how I solved this problem, welcome under cat.
To begin, take a look at the situation in general. There is a resource that can be identified. For example, a web resource is identified by the scheme, host and port, for example
From here you can put forward the idea of the amount of salts in the hash function: the more - the better. You can take the size of the final password, the time (hour, day, month or even year) and to the heap the geographical latitude and longitude of any point on earth. Consequently, the requirements for the complexity of the incoming password fall and you can use a simpler sequence of characters, for example, of four digits (not recommended with a paranoid level of 2 or higher).
And now, let's see what you can do about it. For experiments, I chose Google Chrome and wrote a simple extension for it. By clicking on the icon, a password generation window appears, the extension receives the address of the active tab.
')
Then we create a JavaScript
Where the sha512 function generates the hashes with the sha512 algorithm, and the Base85 function converts the hexadecimal number system to the octagonal format [A-Za-z0-9] + and 25 punctuation symbols, including punctuation symbols, so that the display of the generate function is surjective, and the password is obtained persistent (constant for the same function arguments) and hard to reproduce.
At the moment, the extension looks like this:

And the passwords themselves from the sites are not stored anywhere, and my paranoia is still sleeping peacefully.
PS If there are ideas how to improve this idea, I will be glad to see in comments.
PPS Misprints and errors please in the LAN.
PPPS In order to preempt questions about the complexity of decryption, suppose that my nickname and pin 1234 were used to generate a password, although let's assume that you do not know the pin. Then what is my password?
PPPPS Just noticed that in this case, phishing sites in the passage on my password
UPD :
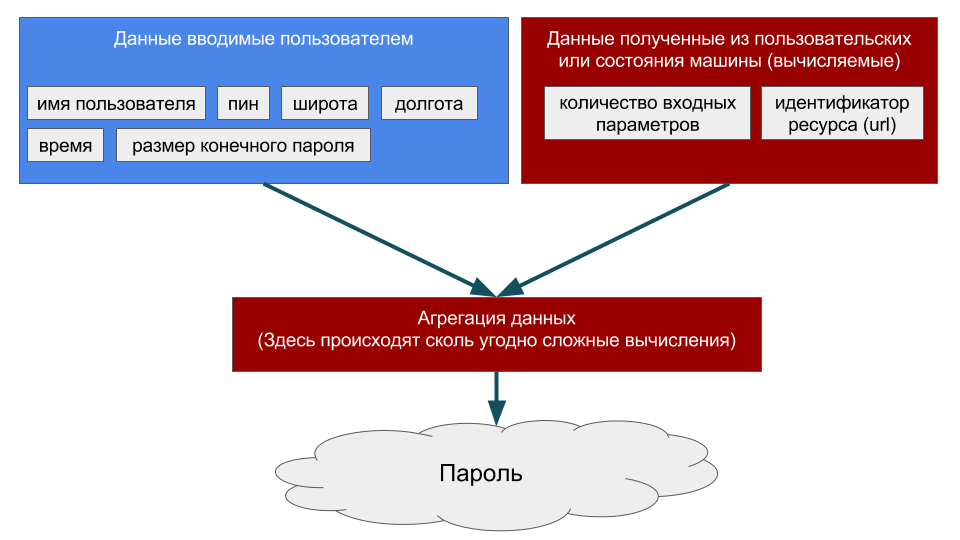
Generation scheme:
Loneliness and paranoia can be great creative stuff.
Ann Lamotte
Each of us goes through several stages of
To begin, take a look at the situation in general. There is a resource that can be identified. For example, a web resource is identified by the scheme, host and port, for example
https://login.awesome.site.com/ , in turn, the desktop application can be identified by the name of the executable file, for example awesom-app.exe or by the window title or part of it. So with the ID sorted out. Next come the login and password. The login can be either a username or his email address to identify the user. And now let's take a look at the password, but on the other hand. The password is a kind of zero salt for generating a hash. For example: hash(username + ':' + password + ':' + salt) From here you can put forward the idea of the amount of salts in the hash function: the more - the better. You can take the size of the final password, the time (hour, day, month or even year) and to the heap the geographical latitude and longitude of any point on earth. Consequently, the requirements for the complexity of the incoming password fall and you can use a simpler sequence of characters, for example, of four digits (not recommended with a paranoid level of 2 or higher).
And now, let's see what you can do about it. For experiments, I chose Google Chrome and wrote a simple extension for it. By clicking on the icon, a password generation window appears, the extension receives the address of the active tab.
')
chrome.tabs.query({active: true, currentWindow: true}, tabs => generate(tabs[0].url) ); Then we create a JavaScript
URL object and an array of parameters to generate the hash. We take exactly url.origin , which would have a scheme, host and port: const username = 'username'; const pin= '1234'; const size = 16; const expired = 2016; const latitude = 40.771426; const longitude = -73.9771395; function generate(url) { const url = new URL(url); const params = [ url.origin, username, pin, size, expired, latitude, longitude ]; const hash = sha512(params.join(':')); const password = Base85(hash).slice(-size); document.getElementById('password').value = password; } Where the sha512 function generates the hashes with the sha512 algorithm, and the Base85 function converts the hexadecimal number system to the octagonal format [A-Za-z0-9] + and 25 punctuation symbols, including punctuation symbols, so that the display of the generate function is surjective, and the password is obtained persistent (constant for the same function arguments) and hard to reproduce.
At the moment, the extension looks like this:

And the passwords themselves from the sites are not stored anywhere, and my paranoia is still sleeping peacefully.
PS If there are ideas how to improve this idea, I will be glad to see in comments.
PPS Misprints and errors please in the LAN.
PPPS In order to preempt questions about the complexity of decryption, suppose that my nickname and pin 1234 were used to generate a password, although let's assume that you do not know the pin. Then what is my password?
PPPPS Just noticed that in this case, phishing sites in the passage on my password
UPD :
Generation scheme:

Source: https://habr.com/ru/post/277649/
All Articles