The glibc library’s critical vulnerability allows remote code execution
Google researchers have discovered a critical vulnerability in the glibc library ( GNU C Library ). In the
getaddrinfo() function, which is responsible for parsing domain names, a buffer overflow occurs - an error allows attackers to perform remote code execution.The exploitation of the vulnerability, designated CVE-2015-7547 , is possible in cases when vulnerable devices or applications send requests to domains and servers controlled by hackers, as well as in the event of a man-in-the-middle attack.
')
All very seriously
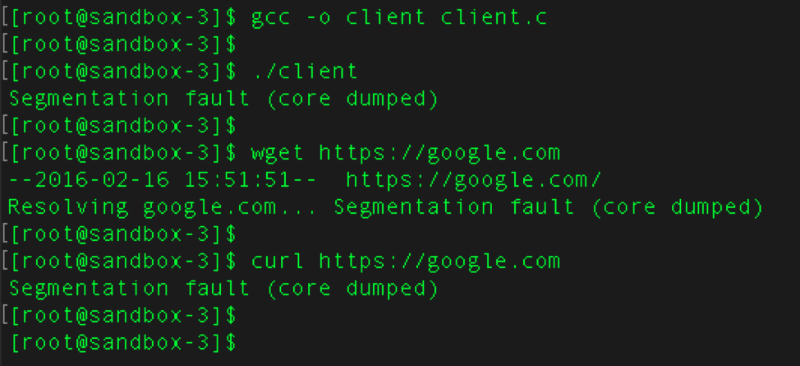
In their blog, Google researchers write that they discovered a vulnerability when a segmentation error began to occur in the SSH client they were using when trying to connect to a specific address. During the proceedings, it turned out that the whole fault was a buffer overflow in glibc, and that this error could lead to remote code execution.
The glibc library is used in a large number of popular Linux applications - according to the researchers, information about the vulnerability of the wget, SSH, sudo, and curl utilities has already been confirmed. The total number of vulnerable applications is so large that it is not possible to compile a complete list - in a conversation with Ars Technica, security researcher Ken White stated that the vulnerability is contained in all Linux distributions, as well as the programming languages Python, PHP, Ruby on Rails. There are reports that the error is contained in most of the applications for working with bitcoin cryptocurrency.
To the surprise of the researchers, it turned out that the maintainers responsible for glibc knew about the error in July last year. In addition, it turned out that in parallel with Google experts and regardless of them, the vulnerability was also discovered by Red Hat specialists - the products of this company are also vulnerable ( list ). As a result, the two teams joined forces to create a patch.
A proof-of-concept-implementation exploit is also available on Github.
How to protect
Glibc support specialists have already released a patch that fixes the bug. In some cases it is enough just to install it, however, if the software was compiled using the vulnerable version of glibc, then it will need to be recompiled with the new version.
If you install a patch for some reason is impossible, the researchers describe ways to reduce the likelihood of vulnerability exploitation. First of all, large UDP or TCP response packets (2048+ bytes) are needed for operation - one by one such packets overwrite the stack. You can counteract this by limiting the size of the packets with the responses that the local DNS resolver accepts. This can be done using DNSMasq or similar programs. In addition, you should make sure that DNS queries are sent only to DNS servers that limit the size of UDP responses.
Glibc Maintainers also gave their recommendations on countering attacks using vulnerabilities. These include using a firewall that rejects UDP DNS packets larger than 512 bytes, refusing to use AF_UNSPEC, `options edns0` in /etc/resolv.conf, and also` RES_USE_EDNS0` or `RES_USE_DNSSEC`.
There are also packages that do not contain this error - for example, in the mobile OS Android Android, instead of glibc, the Bionic library is used. In addition, many devices used by private users — for example, home routers — also work with installed alternative glibc libraries, the vulnerability of which does not currently contain information.
This is not the first time glibc has detected critical vulnerabilities that could lead to remote code execution. So in January 2015, a vulnerability was discovered CVE-2015-0235 , called GHOST. It allowed the attacker to gain remote control over the system. The users of Debian 7 (wheezy), Red Hat Enterprise Linux 6 & 7, CentOS 6 & 7, Ubuntu 12.04, as well as Zend Framework v2, Wordpress and several other popular applications were under attack.
Positive Technologies experts recommend that all users and developers whose systems may be vulnerable install a security update as soon as possible. In addition, you can reduce the risk of exploiting the vulnerability by applying the recommendations of glibc maintainers and Google researchers, as well as using special protection tools, such as MaxPatrol .
Source: https://habr.com/ru/post/277383/
All Articles