Safety means of security: ACS
Disclaimer
The materials listed below are purely research in nature. This study was conducted by the author solely for research purposes, his results are not and cannot be recognized as a guide to the commission of any illegal acts. During the study, the author acted within the framework of the legislation of the Russian Federation. The use of research results is allowed only for scientific and educational purposes. The use of research results to achieve a wrongful or any other result from scientific activity may entail criminal, administrative and (or) civil liability. The author is not responsible for information security incidents related to the research topic.
Introduction
Everyone is accustomed to allocate money to ensure the security of the company, implement ready-made solutions and assume that these ready-made solutions have completely covered certain risks. The market offers a range of different solutions from different manufacturing companies, so the buyer has a wide choice of hardware security tools and software for managing them. That's it about the information security of such software and will be discussed. Today we will talk about access control systems (ACS).
How did I come to this
Testing for penetration in different companies, I often met the open 3050 / tcp port of the Firebird database (hereinafter referred to as FB) with the default login and password: "SYSDBA; masterkey". Studying these hosts, I found out that these can be completely different solutions and programs that use FB: from accounting software and CRM systems to video surveillance and access control systems, and even RBS. Through this port, the entire database of the corresponding software is available, and by editing it, you can influence the logic of the application.
')
The database usually stores logins and passwords for accessing the functionality through the graphical interface of the program itself, which means that after reading them, you can use the full functionality of the application itself through a beautiful graphical interface, initially without knowing a single login and password for this system. Sometimes passwords can be stored in encrypted or hashed form.
Since the password encryption algorithm is “sewn up” in the software itself, the meaning of encryption is lost, because reversible encryption algorithms are used that are easy to recognize with a software sample on hand. And hashing complicates the process, but not by much.
So it became interesting to me, and how much software has such a disadvantage, if not to say "vulnerability"? And anyway, is this a software vulnerability? Maybe this is a miscalculation of users who have not configured this software correctly? One thing is clear: this situation is very common and carries threats to the business.
For the study I was interested in the access control and video surveillance systems, the remote banking system, accounting and financial software. But this article will deal only with access control. Using similar vulnerabilities for access control systems, any member of a local network can open / close any doors and violate access control. In general, everything that an ACS administrator can and even more!
Research methodology
The research process itself is very simple. I downloaded from the official sites of manufacturers of the demo version or the usual version of the software, depending on what was available on the site. If the site did not provide the ability to easily download software, then I contacted the software manufacturer via email and asked for a demo or trial version of the software for testing or benchmarking. Having collected the distributions of the most widespread access control systems on the market of the Russian Federation / CIS, I started testing.
Each software instance was installed on a virtual machine and analyzed on the opened ports. If, among other things, a 3050 \ tcp port appeared, then I tried to log in to it under the default login and password. If you failed to log in using standard credentials, i.e. When installing the FB server, the software changed the password, then I tried to figure out which one. I tried installing the software several times and looked at whether the password hash from the FB server was changed or not. If it has not changed, i.e. with several installations remained the same, I made the assumption that this password is universal for all installations of this software for anyone who uses this solution. This is no better than using well-known default credentials. Anyone who installs this solution will know the hash from all other customers, which is not the right and safe option.
After these actions were completed, I rolled back the virtual machine to its original state and proceeded to the next sample software. If the software was not installed on WindowsXP, the same thing was tried on Windows 7. And of course, if I noticed a similar situation for other databases, I also noted it, although I initially thought to look only for FB. All checks were carried out for the situation when the access control system is on the local network and is set by default. Vulnerable, I thought that the access control system to the database of which I managed to connect and see the insides of the database.
Research results
In total, the study involved 25 access control solutions:




Additionally, as a confirmation of the vulnerability screenshots of a successful connection to the database are given (by points for each access control system).
APACS 3000

ENT Control



KODOS

LyriX



Sphinx



Castle



Elsys base



Tempo reale

VANGUARD



KRONVERK Reverse

Guard



Electra-AS



Vulnerability is not always dangerous
It is also worth noting that in all cases such vulnerability is a big risk. If such vulnerable systems are used, for example, in the underground parking of a residential house / complex, where 1-2 guards sit at the checkpoint, then there is almost no risk here, since in order to take advantage of this vulnerability, you need to have access to the local network where the computer with the access control server is located. In the case of parking, there is simply no one to take advantage of such a disadvantage, except for the guards themselves, who already have authorized access to the system. Another thing when it comes to a large office or organization, where there are unprivileged users and premises where they can not go: factories, government agencies, medium and large companies, etc.
Prevalence vulnerability
In order to assess the prevalence of this vulnerability, scanning the Internet for FB will be small, because a sane person will not post an access control system to the Internet, and a normal manufacturer of an ACS will remind the client of the danger of such placement. Therefore, it is possible to judge the prevalence only by voluntary disclosures, for example, reviews of products. Of course, it is worth noting that this information cannot be 100% trusted, since it is not clear whether the solution is used now and in what form.
Also, according to reviews and thanks, it cannot be said that in general this solution is used in the company that originated the review, or on the scale of its use in the company. It can be applied all the way through one door or to a small remote office of a large corporation. In the end, the organizations themselves could change the settings of the FB server so that it was accessible only to localhost or otherwise to solve this problem, and I have such examples.
Who may have vulnerable systems with examples:
- Winter Olympic Games 2014
- GAZPROM, SYNTERRA, InfoTeCS and other large and well-known companies ...
- Banks
- Plants
- Spaceport
- Airports
- Warehouses
- Main Internal Affairs Directorate and other state structures ...
- Providers
- Religious communities
For example:
1. 1st State test space center (Mirny town)
2. AZIA Group Technology
3. BIOMAN
4. Dr. Oetker
5. DSSL »(Trassir) - Volga Region
6. EAST LINE
7. ENKA (“Enka Ishaat Ve Sanayi Anon Shirketi”)
8. Expert Security Systems
9. RB Service Home Network
10. SPAR
11. SYNTERRA
12. XCOM
13. Zoneco
14. "Sports Center"
15. Absolute Sat
16. JSC "Imperial Porcelain Factory"
17. ASB-Kit
18. Domodedovo Airport Complex
19. Airports in the cities of Murmansk, Perm
20. Bank Vis.
21. Bank of Moscow
22. Development Capital Bank
23. Bank Snezhinsky
24. Bank: Industrial and Commercial Bank
25. Safety Online
26. Business Center Ducat Place ll
27. At the central office and one of the “Atak” supermarkets
28. Gazprom
29. GAZPROMBANK
30. SEB MULINEKS Group
31. GUVD of St. Petersburg and Leningrad Region
32. Date-Perm
33. CJSC Aerofest at Sheremetyevo-2 Airport
34. CJSC Belarusian Telecommunications Network (BeST Life)
35. CJSC Kerama-Marazzi
36. 2014 Winter Olympic Games
37. ISB
38. KAMAZINSTRUMENTSPETSMASH (G. Naberezhnye Chelny)
39. Fujitsu
40. Comprehensive Security Systems
41. Cont.
42. Cube Systems project
43. Sea ice-resistant stationary platform "Prirazlomnaya"
44. MosKabelMet
45. Moscow Regional Scientific Research Clinical Institute. Mf Vladimirsky (MONIKI)
46. Moscow theater "Lenkom"
47. NPK "Bios"
48. Helicopter Service Company OJSC (100% subsidiary of OPK Oboronprom OJSC)
49. OJSC “KIROVSKIY FACTORY”.
50. OOO Gazprom drilling
51. OOO Gazpromneft-Yug
52. LLC “Danone Industry”
53. Ramenka LLC
54. LLC SVYAZSPETSPROEKT
55. Siemens Business Services LLC in Voronezh
56. VOLKSWAGEN Group Rus LLC
57. NPO Urban Systems Ltd.
58. OSMP (central office of the United Instant Payment System)
59. Belarusian Steel Works Open Joint-Stock Company
60. Parking lots of residential complexes of the company “YIT DOM” and IG “Etalon”
61. Enterprises of HC PhosAgro OJSC
62. Profautomatics
63. Raster
64. Religious Community "The Parish of the Minsk Diocese of the Belarusian Orthodox Church in honor of All Saints in Minsk"
65. Rosmorport
66. Frontier-92
67. SANTEHPROM
68. Satellite Ural
69. Satro-Palladin
70. SATURN
71. Siddhi Security
72. Warehouse logistics complexes of JSC Interterminal (St. Petersburg)
73. Perfect systems
74. Sonopress
75. Security Specialist
76. Tel
77. St. Petersburg Heating Network
78. HeatElectric Center №25
79. TNK KareliaNefteProduct
80. Triad CT-B
81. Trade Telecom
82. Ufanet
83. Financial and Settlement Center AvtoVAZ JSC
84. The Central Bank of the Russian Federation for Tomsk Region
85. Cerberus
86. Elsie
87. Eltra
88. Energy Alliance
...
And many other objects.
Operation example
And now let's see how difficult it is to exploit this vulnerability. I believe that for this you do not need to possess any special knowledge, everything is done with publicly available tools and in a couple of minutes.
Find the FireBird server
The first thing an attacker will obviously do is look for an open 3050 / tcp port in the company's internal network. To do this, you can download the nmap program ( nmap.org/download.html ) and run it with the following keys from the cmd console:
nmap -sS -p3050 --open 192.168.0.0/24 In response, after some time, nmap will display all open ports of 3050 / tcp, which it found on the network 192.168.0.0/24:

Accordingly, each network’s addressing will have its own, but the principle is the same. If you don't like nmap, you can use many other programs, most of them are graphical, which allows them to be used by an ordinary user. One of the open ports will belong to the access control server. Most likely there is only one port (as in the screenshot), but just in case, imagine that there are several.
Connect to FireBird
After we have identified ports FB, you need to connect to them. This can be done using the IBExpert program. Remember that you need the fbclient.dll library for it (you can get it by installing the FB server for yourself or by downloading from the Internet). Next, you need to consistently try to connect to each FB server. To connect to the FB, you will need to know the login, password and the path to the database on the FB server itself. We know the login and password, this is where the vulnerability lies, and the path to the database will be used with a standard one with a very high degree of probability. You can take the path from the screenshots from me, though, since my demo version is used in the screenshot, the path will be different. You can also set yourself this ACS and see which path it uses by default. It is quite simple to find out the name of an ACS, you can ask directly what ACS is used, you can ask the safety officer for advice: "Which ACS is better?" You can spy on the icon or the outlines of the interface on the monitor at the checkpoint. Sometimes there is a software manufacturer badge on a card reader. And you can just go through all the standard options, there are not many of them.

Thus, we connected to the database directly and can do everything we want, even what the official administration interface does not allow.
Understand the structure of the database used by ACS
In order to do something with the access control system through the FB-server, you need to understand the database format. How many access points, so many different data storage formats in the database.

Let's start with the simple.
Access to the official SKUD administration interface
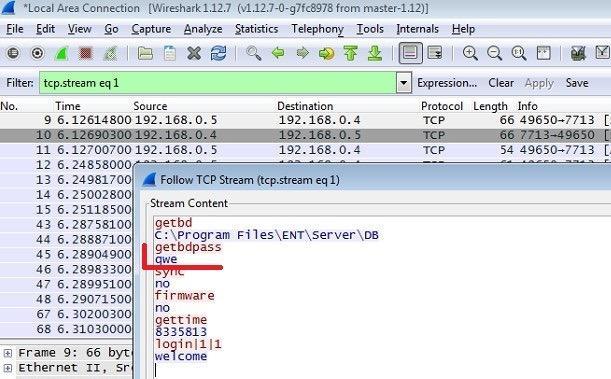
To connect to the access control server, we need a client program for a specific version. Perhaps some access control systems through the official client only support local connection, I do not know, did not check. To connect we need: ip, login, password. We already found the IP using the port scanner, but we don’t know the login and password from the access control interface, but you can find them in the access control database. For example, let us consider the example of access control ENT Control, my favorite access control system.
The “FB_UZP” table stores data for authorizing access control users:

Login is stored in clear text, and the password is in the form of a hash (md5). Here we can do in different ways:
1. Fetch hashes and learn passwords, hello, cmd5.ru:

2. Replace the existing user’s hash with a known user, for example, “c4ca4238a0b923820dcc509a6f75849b” means the password “1”.
3. Create a new user with your password / hash.
After all these actions, do not forget to make Commit so that all changes are saved:

After we connect to the server using the official client:

And we get access to the access control panel as a legal administrator:

Through the database directly you can do much more than through the interface. Through the interface, it is more convenient and faster to do what the ACS voluntarily allows you to do.
Creating false access control events
And now we will try to play the most innocuous vector - we correct ourselves the time of the visit. First we need to get our user ID using our full name, so we make a SQL request to the server:
select ID from fb_usr where LNAME='' You can execute it by clicking this button:

In response, we get a line from the database, where usually the first column contains our identifier inside the system, which is usually digital. If from the database the answer comes in a few lines, then you should understand what it means to you, by indirect signs, i.e. for the remaining columns of the result.
Now, knowing your ID, you can look at the table that keeps track of opening and closing doors: fb_evn. Here we execute the second request, which will bring us all the events related to our pass card:
select * from fb_evn where USR=(select ID from fb_usr where LNAME='') 
Here, in fact, almost everything. Notice, each passage through the door is two events. Opening and closing the door at the passage. If this is the entrance to the controlled zone, then these are events 2 and 3. If this is the exit from such a zone, these are events 4 and 5.

To imitate the exit through the door, we find the fact of the exit through the external door of the company and change the exit time for these two lines, for the time when you want to “leave”:

You can detect such a scam: in the database, the sequence number of the replaced event will be out of chronological order, but this can be noticed only through a direct connection to the database and a rigorous search, so you can not worry about it at all. And if you have remote access to your workplace, then edits can be made from outside the organization.
Threats and risks
The most banal and innocuous risk of using this vulnerability is that employees edit their work time logs . I did it myself when I worked in one of the companies where the vulnerable access control system is located. Successfully late rules and departures ahead of time, and the management knew about it, but could not control or stop it. It got to the point that the access control system could show my presence at work when I did not go to work at all that day. Accordingly, there is a risk for the employer: loss of man-hours and lack of discipline among employees.
Another likely vector is the change in the access profile of the company employee itself . For example, I had a time limit at my last job, and if I didn’t leave the building until a certain hour, you would remain locked inside. I had to call the guard and listen to curses. Therefore, I myself changed the access profile to another one that existed without time limit, or rather, without any restrictions at all, and could walk freely even to the CEO's office. Accordingly, another risk is the penetration of an employee at any time and into any room protected by an ACS for espionage, theft or other malicious acts.
Create new passes . An attacker could bring his access card and enter its identifier in the database as a new employee or, even worse, link it to an existing employee of the company. At the same time, any photo can be attached to the new card, so as not to arouse suspicion from vigilant protection at the checkpoint. Risk - penetration into the protected area of the attacker under the guise of a legal employee of the company.
Sabotage or denial of accessibility (DoS) - having access to the database, an attacker can change all passwords of all access control systems in order to remove them from control of the access control system and block all doors in the territory controlled by access control. This completely paralyzes the movement of employees between the premises and, as a result, will stop important business processes. It will not be possible to return the system to a controlled state, and disabling the access control system will completely make all the doors open. Imagine that such an attack will happen when important customers are visiting your territory, who will be locked up with you.
Integrated attack, video surveillance . Many ACSs support integration with video surveillance systems or directly connect surveillance cameras to themselves. Thus, an attacker in parallel with unauthorized entry can disable an arbitrary camera and the video surveillance system will not record the actions of the intruder. By the way, some manufacturers of access control systems have their own video surveillance systems, which are vulnerable as well as their access control systems. But since I didn’t conduct a comprehensive study of video surveillance systems, I’ll not be going to tell and list them in more detail. Also, for sure, it will be possible to replace the image from the camera, because you can replace one camera in the database with another “fake”, which will broadcast in the loop a piece of the replaced image.
In other words, the presence of such a small loophole in the security system calls into question the expediency of the entire access control system for a knowledgeable attacker, and will allow him to go unnoticed and engage in espionage inside the company when the company is confident in its full control over the situation.
Developer Reaction
The important point is how the developer responds to error reports. I informed the manufacturers of the access control system about the deficiency found in their product, and it turned out that not everything is so simple. The following describes the reaction of each of the developers. During the survey, I had to correct the questions, so they may differ slightly for different companies.
In general, most developers did not consider the situation above their problem, many ignored my questions, although they knew that I was writing an article about their product. Some perceived my call to the company as a game, tried to “get out” and lied, explaining that they only use FireBird in the free version of the software, and in paid they are fine and that they are not even interested in what I found there. As a result, of course, everything turned out to be completely different. Such “slippery” conversations were held with people who sell the product, but I understand well what I am talking about and therefore I could not get rid of it. I can imagine how difficult it is for an ordinary client of a company to bring such sellers to "clean water".
With techies everything is much easier. The technical support basically understood at once what it was about and asked to wrap everything up by mail, although most of these “turns” ended with ignoring the letters. But there were also such cases when tech support stubbornly could not realize that, in addition to the password from the access control system, there is a password from FireBird, and it can be entered not through the software interface.
It happened that the company did not respond to the letter after the first telephone contact, and when I called the company again to understand what had happened, I heard in reply: “Aah ... Yes, yes, yes. Our programmers said that we are not interested. What can not respond to such letters. ".
What it is? The desire of programmers to stop the spread of such information to their superiors? Or complete indifference to the quality of their work, anyway “no one understands how it works”?
In any case, it was already a great success when the company accepted the information and gave its comments. At the very least, such companies take their reputation seriously and it is felt that they care about their product.
Company survey results:
1. “Is the port 3050 / t open on the external interface of the network card with the login and password“ SYSDBA; masterkey ”a vulnerability or a lack of security and why?”
Answers to the first question
ENT Control
AVANGARD AND GUARD
KRONVERK Reverse
Electra-AS
APACS 3000 and LyriX
Gave a general answer (Given below)
Elsys base
REFUSED COMMENTS
KODOS
IGNORED QUESTIONS
Sphinx
IGNORED QUESTIONS
Castle
IGNORED QUESTIONS
Tempo reale
IGNORED QUESTIONS
Our software package uses port 3050 / tcp, which
required for the operation of this Firebird database. Default login and password for
The database is set to the standard "sysdba and masterkey". This APPROACH
due to the openness of our hardware and software complex for integration
with other systems and the ability to work with our third-party equipment
programmers. This solution is not a security vulnerability.
as the system user has a documented ability to change
password to connect to the database.
AVANGARD AND GUARD
Is not. This is done deliberately to connect remote clients. This will be a vulnerability if clients connect without any means of protection such as VPN. But, thank God, those who have the need for such connections, perfectly understand how to connect remote "fat clients" so as not to create problems for themselves. Password and login by default, the client can be changed, if he understands what I mean.
KRONVERK Reverse
I think no. Of course, you can always change the login and administrator password.
In addition, it is not necessary to open 3050 / tcp outside.
In early 2000, the Interbase password database scandal broke, the vulnerability has long been eliminated.
It is currently recognized that the use of Firebird is safe while observing basic precautions.
Electra-AS
It is, but it generally depends on the people operating the access control system. AT
Documentation is recommended to change the standard database password to a secret one.
APACS 3000 and LyriX
Gave a general answer (Given below)
Elsys base
REFUSED COMMENTS
KODOS
IGNORED QUESTIONS
Sphinx
IGNORED QUESTIONS
Castle
IGNORED QUESTIONS
Tempo reale
IGNORED QUESTIONS
For Shalt PRO, the first question was different:
“Is the FireBird port open on the external interface of the network card with the same password for all clients - a vulnerability or a lack of security and why?”
Answer Shalt PRO
Shelt PRO
In most cases, yes, if the network under the access control system is not physically or logically isolated and you can connect to the Firebird database server, as well as if you can install software from external media or download them from the network (global / local). In the simplest case, this can lead to data loss if there is no archival copy of the database, as well as unauthorized access to the enterprise or data corruption. For example, the accounting of working time. There are a lot of options and they all depend on the targets of the attackers.
From these answers we can draw the following conclusions and assumptions:
- Many developers imply that the access control network must be a physically isolated network, and therefore it does not need to protect its components.
My opinion: I fully agree that the access control and video surveillance network must be physically isolated. However, I do not agree that it is possible to completely launch the information security of such networks. For example, in software of the same companies, supporters of a separate physical network for access control, there is a division into access control users. Some users can receive reports from the access control system, some see the passes in real time, and only a few have administrative rights. What then is the meaning of this division into users, if it is so easy to manage. Once there is a division into users, it means that they protect against some kind of risks, but this turns out to be ineffective. In addition, many people want to use ACS through corporate computers.
- Developers shift responsibility for you to control the security of their product.
My opinion: This is partially correct, because if you want to configure the access control system is not safe - you will do it and the developer will have nothing to do with it. However, in my opinion, the developers are not informing customers that the password from the database can be changed and that it should be done immediately after installation. Indeed, on the one hand, the client may unsafely configure the access control system, and on the other hand, he doesn’t know that the out-of-the-box access control system is already vulnerable. Why users during installation are not asked to set a password from the database, but simply add to the technical documentation a line that needs (you can) change the password - I do not know.
- Part of the software, obviously, uses the FireBird port not for communication between the access control server and the database server, but for communication between the access control server and the database server. (Otherwise, how to explain that the port is needed for remote clients).
My opinion: Why then ask for a password from an ACS user, if the client software still manages the ACS via “SYSDBA; masterkey”? It turns out that this is a “screen” for averting eyes, deception. I checked that it was so or not, and I was very surprised by the results. About this below.
Let's move on to the second question:
2. “What is the use of port 3050 / tcp on the external interface of the network card in your product? Can I leave it only on localhost? ”
Answers to the second question
ENT Control
AVANGARD AND GUARD
KRONVERK Reverse
Electra-AS
Shelt PRO
APACS 3000 and LyriX
Gave a general answer (Given below)
Elsys base
REFUSED COMMENTS
KODOS
IGNORED QUESTIONS
Sphinx
IGNORED QUESTIONS
Castle
IGNORED QUESTIONS
Tempo reale
IGNORED QUESTIONS
Port 3050 / tcp is used for the Firebird network SQL database.
A feature of network databases implies simultaneous operation
several users from different workstations with data stored in the database on
remote server or arm. This is what port 3050 is used for.
AVANGARD AND GUARD
For some configurations you can, for some you can not. Our software is a distributed system with support for simultaneous operation of several clients simultaneously.
KRONVERK Reverse
Only on a localhost is not possible within the meaning of use - network software implies
several client sites to a single database.
Electra-AS
You have used a very old software version. In the modern version of the software
the complex works on a local network on different computers. therefore
The database server must be accessible from other computers.
Shelt PRO
Of course, the system can be configured to work only on the local computer. To do this, it is enough to block this port with the standard Windows Firewall to connect from outside.
APACS 3000 and LyriX
Gave a general answer (Given below)
Elsys base
REFUSED COMMENTS
KODOS
IGNORED QUESTIONS
Sphinx
IGNORED QUESTIONS
Castle
IGNORED QUESTIONS
Tempo reale
IGNORED QUESTIONS
From these answers we can draw the following conclusions and assumptions:
- For many, the port is used to connect multiple clients from different workstations.
My comment: Again, we see that clients communicate with the database not via the intermediate access control server, but directly via the FireBird port. Which means that each client must know the password from the FireBird server, and the password and username of the access control system is asked for the view. Any client can take the saved password in the access control client from the FireBird database and connect directly to the database, bypassing the graphical separation of access to the program interface.
: FireBird , , .
:
3.« «» FireBird, Embedded-, ?»
ENT
-
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
. .
. 2. Embedded Firebird « 8000»,
— , Embedded , —
. Embedded-
. , Embedded- .
-
.
.
Firebird , Firebird , UNIX.
.
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
, .
4.« ? , ?»
ENT
. : , . Very comfortably.
-
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
. : , . Very comfortably.
. . .
Yes of course. . «» «» « 8000».
-
There is.
28.3
.
– – . On
.
.
Config.ini
.
(->-> )
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
, , , . .
5.« - , ?»
ENT
-
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
, ,
. ,
. ,
,
‚ , .
, ,
, .
Time will tell. FireBird , . . . , — . . 15 . . ;)
. . 1-4.
-
.
.
1.10
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
6.« , , ?»
ENT
-
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
, , ,
,
,
.
B , .
8 20, 10 18.
8 800 505 02 30
.
IT .
: 3050/tcp , SYSDBA.
-
SYSDBA
.
APACS 3000 LyriX
( )
Elsys BASTION
KODOS
Castle
Tempo Reale
:
« , , ?»
1.
2. , .
APACS 3000 LyriX :
APACS 3000 LyriX
APACS 3000 LyriX
:
, . , “ ”, . , , , , . , .
, , , . , , . , IT . .
, , , . , . , IT, « » . , , «» , . , , - , : « !»
, :
1. SYSDBA , ?
2. , , ?
:

:
, - : -? , , .
:
— APACS 3000 LyriX
— ENT
—
— Castle
— Elsys BASTION
—
, -, .
, - SYSDBA, -, .
Elsys BASTION , .. SYSDBA . Elsys BASTION FireBird APP_ADMIN, , . Elsys BASTION APP_ADMIN. SYSDBA ( ), . , . , SYSDBA — . APP_ADMIN , SYSDBA masterkey.
, APP_ADMIN. . , , . \.
APP_ADMIN:

, ENT , Castle .
Castle mysql . , - , - .
Here's how it works:
1.
2. , , :
3. , mysql- root .
4. mysql- root .

, - . , , root , , . mysql , , mysql, .
ENT .
FireBird , . Those. SYSDBA, , .
, telnet-:

, – , . , . , .. , « ». , , -, , API. , , . , . , , .
, . , , , . , «», , Reverse Engineering, .
, «» ( ), « », . : « , , , . ». , , Reverse Engineering .
, , BugBounty , . - . , , .
, . , API , . , . , . , , , . , , «» , .
, , , , . , , , . , , .
: . 90-, 2015 . , – , . .
, , , . .
.
. . , , “” , , , , , , . , -, , . , .
– . « » , . , , , , . Wireshark – 5 IT. 5 , , . , - .
, . , «» .
, IT «» (www.acron.ru)
:
«» . «» — , , . 15 000 6 .
:
.
, , . – . - . – «» , , . .
, «» .
, VLAN, , « », , . . , , , – .
, , , « ». – , – , . « ». , , .
, , . , . , , , . – , .
, HeadHunter (hh.ru):
:
HeadHunter — -, , , , , , .
:
1. , IT , . , .
2. , .
3. , , , , .
, «» (finam.ru):
:
«» — . «» , , Forex. 90 .
:
– . , , . , . – . - , .
, , , . , , – . , . : ( , ), ( , ). , , , . , , , «» , . , , – .
, Elite Security (elite-security.ru):
:
« » , , . 25 , 5000 .
:
Firebird . , / , . . , , ( , /, , - ) «» «». , .
. , , .
, , . : Bolid, Gate, Parsec, Perco, Quest , , .
, Parsec ( parsec.ru ):
:
«1) ? ?
3- , , .
- MS SQL Server TCP/IP Named pipes. SQL- , Parsec.
, . , .
SQL Server ( ) SQL Server (sa) - – , .
– , .
, – SA Windows , , SQL, Microsoft , SQL Server.
, .
, , , . .
2) ? ?
, , – , .
, , .
3) – .
ProviderBase, .NET Framework 2.0. «» .
, «-» ( bio-smart.ru ):
:
1) ? ?
Biosmart-Studio v5 , . - , PostgreSQL, . . , , , ip , .
2) ? ?
, . , .
:
1) , . .
2) , , , legacy . .
, , . . , . , .
, «ITV | AxxonSoft» (axxonsoft.com):
:
« , / . — , . . , . , , .
, «PERCo» (perco.ru):
:
Apollo.
, , . – , .
— , , — . . , , .
. PERCo. :
MGTU them. , ,
.-, -,
,
, -,
, ,
,
,
Suleyman Demirel University, ,
.
, , , root:root .
- -
, :
:
, — . — -. — .
, «Group-IB» (group-ib.ru):
:
Group-IB — ; threat intelligence , Gartner. 7 - Business Insider. , (). uropol, .
:
, , . , (hardcoded credentials), «» , , CRM/ERP-, , - /SCADA. , .
, , , .
, , , , , , .
, :
:
- . , , , , — , , . , , , , , . , , , , . , — .
( ), . , , CCTV, – . , . , , « ». , , .
, , , , .
, Security Business Development Manager at Cisco Systems ( cisco.com ):
:
Cisco — , , . , . .
:
– - .
:
, ,
, , . , , , . , , . - , , , -.
. , , .. , , - . , . «».
, , . FB- .
. Reverse Engineering . (Reverse Engineering — ). , — . — , .
, «», . : , . , , . , 2 . , . , ? , ? .
findings
1. –
, , . , , «» . , .
2.
- , , . , , , , , . -, , , , , - .
3.
. “” , , : “ . . , ?”. , . .
4.
, , SYSDBA . IBExpert IBConsole. , .
, , IBExpert:
1. FireBird
2. Tools
3. User Manager
4. SYSDBA
5. Edit
6.
7.

, . , . , . .
«Practical Security Lab» / « »
itpsl.ru / itpsl.org
Source: https://habr.com/ru/post/277279/
All Articles