Zabbix 3.0 released
The long-awaited version of the open monitoring system Zabbix promises us a whole heap of new features, taking the path of a visual update.
Today I want to share with you what brought the release, and what you can start to use today, download the new version from the site. We will also be happy to invite everyone to Zabbix Meetup in Moscow, details of which you will find at the end of the article.

The first thing that catches your eye is a faded web interface. The new design got rid of the superfluous, piled up elements, various unnecessary frames of graphs and so on.
')

Also, the interface is designed from the point of view of convenience, for example, now for any network node or template you can always see how your own macros overlap with inherited ones. Available in several designs, light and dark. Be sure to try the darkside of the topic!

About the rest of the interface changes can be read here .
and also in the separate mini-review on Habré.
Now Zabbix supports encryption of all messages, if necessary - all communication between the server, proxy and agent can be encrypted and protected from prying eyes of prying eyes.
Encryption also provides authentication - only if you have a trusted certificate or a pre-shared key, components will be able to communicate with Zabbix. Authentication is mutual, that is, not only Zabbix Server verifies the certificate of the agent, but also the agent can be configured to check the server certificate: who issued it and whether they can be trusted.

Encryption is completely optional, and can be configured for each component separately (that is, some agents and proxies can use encryption, while others continue to communicate openly as before)

If you do not need encryption or you are not morally prepared for it, then just use Zabbix as before (taking other new features into account, of course! :)) At the same time, all 3.0 components will support encryption, and it can be gradually enabled for individual components at your own pace.
And no new ports - as before 10050/10051 are used for all types of communications in Zabbix.
All the details about encryption in Zabbix here , as well as in our separate mini-review on Habré.
Anticipate a problem before it happens? - Now yes, in Zabbix 3.0.
They say that in 2016 the disks still run out of space sometimes. Zabbix can foresee such a situation and save the application from falling, warning everyone in advance and giving time to add or free space just before problems start.
Just look at an example where Zabbix predicts how quickly a place on / home will end, analyzing historical values lately.

Suppose we need 10 hours to react and add or clean a place (as in the screenshot above). And suppose that 1 hour of collected data on free space is enough to make a correct forecast. The real problem for us is when the space on the / (vfs.fs.size [/, free]) section is completely finished, i.e. 0 bytes Then Zabbix should raise the crash when the forecast for 10 hours ahead, based on the collected data for the previous 1 hour, will be 0, or:
or you can swap the forecast horizon (10h) and threshold (0 bytes) and use another trigger function:
The statistical analysis under the hood of these functions is the same, so just choose the expression that is more convenient.
Learn about prediction in Zabbix here and here .
And also in our separate article on Habré on forecasting.
The new proc.cpu.util data item, available on Linux and Solaris, allows you to monitor CPU usage by each individual process or group of processes.
For example, it may be interesting for the server administrator to control how different users use the CPU. With the key:
he can see the CPU usage of all processes running under john. And if suddenly John is only interested in java:
In addition to the user name and process, you can specify the type of utilization of the CPU (system, user), the name of the process with the path and other parameters.
Full specifications can be found here .


In 3.0, we didn't forget about performance optimization. For example, the history data cache (History Cache) has been seriously reworked. Thanks to the reworking of the structure, the cache works quickly at any items / values ratio, even if only a few data elements fill the server with a large number of historical values.
An index (History index) has been added to keep track of this cache. You can monitor it using the new internal counter zabbix [wcache, index,]

For example, the graph clearly shows how long the processing of eight history syncers of 500000 values for 100 data elements before 3.0 and after took place.
More on this and other internal checks here .
In 3.0, the actions themselves and their conditions are also stored in the cache, so as not to disturb the database once again. This innovation will be very useful in large installations and when there is a large amount of events in the system.

If something was enough to check once a day, it was impossible to choose the exact time. The check could have happened both at night and at lunch, and this could not be influenced in any way.
Well, now you can.
For example, if you need to collect data from office computers, simply set the collection schedule from 9 to 6 on weekdays:

This will allow us to avoid unnecessary accidents about the inaccessibility of shut down computers at night.
In the example above, checks will occur every five minutes (m / 5) only on working days (wd1-5) from 8 to 18 (h9-18), that is, at 9:00, 9:05, 9:10, and so on .

Or would you like to do LLD discovery late at night to minimize the impact on the network? Yes, it can be done in the same way.
Read more about scheduled intervals here .
In Zabbix appeared personal maps, complex screens (screens) and slides.
This allows each user to create their own views of the information that will be convenient for him. And admin rights are not needed.
In this case, the map or screen can be easily shared, making it available to all users, or only to members of a particular group:

Interesting? more here .
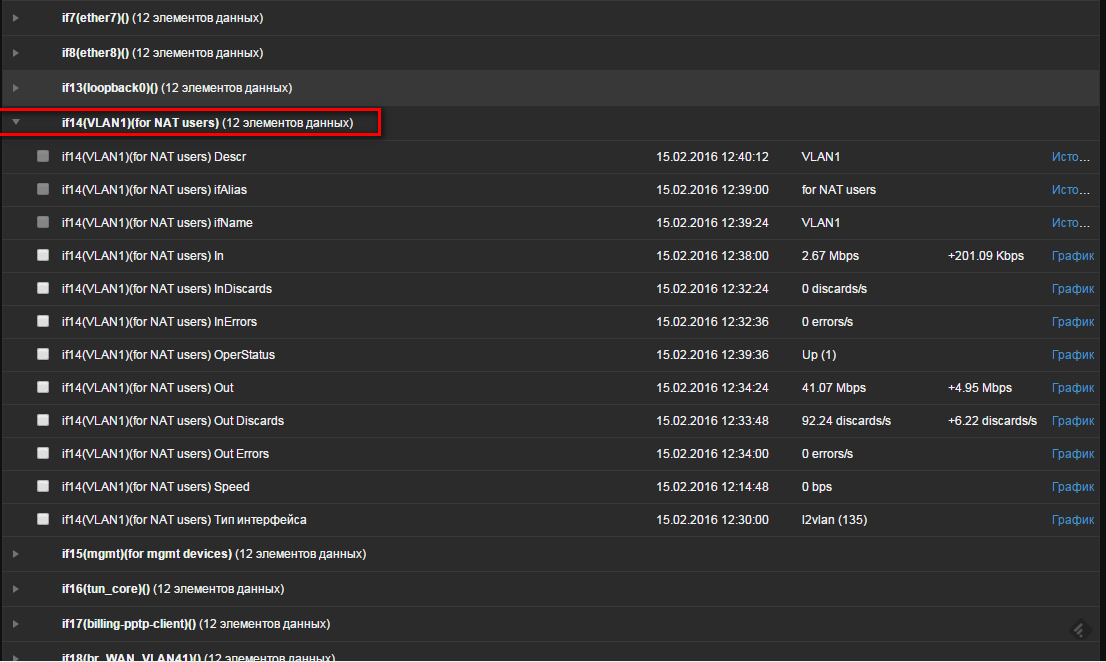
Long ago, people asked about the possibility of using low-level detection (LLD) macros in the name in groups of data elements? Yes, now please and this - prototypes of groups of data elements (Applications) are now available along with prototypes of data elements, triggers, graphs and complex screens.
For example, for network interfaces:
The database cleanup procedure is necessary to remove old historical data. If you really need to delete a lot, you will need a large amount of system resources, which may adversely affect other Zabbix processes that are occupied with something more important and more useful.
In 3.0, added the ability to cancel the launch of the cleaning procedure on a schedule and run it manually when necessary. The new feature is supported by both Zabbix proxy and Zabbix server. To use it, you need to disable the scheduled execution of the cleanup in the config file:
And then it is possible to start database cleaning via the command line:
About the execution of this and other administrative functions (runtime-control) from the command line, read here .
The main Zabbix processes can now be started not only as daemons, if you use the -f (--foreground) switch. In addition to other advantages, this can be useful, for example, when using Zabbix components in Docker.
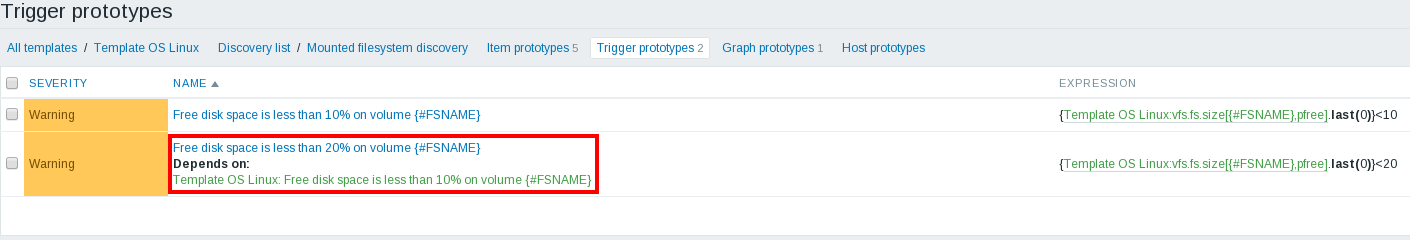
Dependencies between triggers that allow you to get only one accident from a router, instead of a dozen crashes from devices that are located behind it - in Zabbix for quite some time. But unfortunately, this did not work for prototype triggers. Again, in 3.0 this limitation goes away. This will allow, for example, to create a group of triggers from prototypes that have different threshold values and the level of importance (warning and accident) when monitoring the amount of free disk space:

Details can be found here .

Those who monitor Windows servers through Zabbix should evaluate the following innovation - the ability to find all available services in Windows through the LLD service.discovery key, and create data elements and triggers for each new service. Found services can also always be filtered through a standard filter mechanism, which is in low-level detection.


More details on how to configure this can be viewed again in the updated LLD documentation .
It is finished! Now it is possible to send notifications easily and without problems: through the Zabbix interface, you configure the connection to the mail server using the login password, as well as encryption, if necessary. No more additional postfix in smarthost mode or uncomprehending views from the administrator of mail servers whom you asked to allow from the Zabbix IP server to send mail anonymously.

Read more here .
Grown up and patterns. Now when loading / unloading in XML, they include all of the value mappings used (value mappings). You can load / unload transformations separately. And still it is possible to download value mappings via API.

There was a great opportunity to make a decision on detection via SNMP based on not one, but several OIDs.
For example, for interfaces, we can search immediately for ifName, ifAlias, ifDescr, and ifOperStatus:
And if in the description of the prototype of the trigger specify, for example, here is the following list:
then in case of a crash on the trigger, we can see a detailed description of the port.

You can use the values of additional OIDs in LLD filters, decide whether to set an interface for monitoring or not, as well as use the values in the names of triggers, graphs and data elements. Or, as mentioned above in the names of groups of data elements (Applications).
Read more in the updated LLD manual .
Zabbix 3.0 offers more than 50 new features to explore, with all that did not fall into this article, such as the trends API or the addition of additional parameters for custom alert scripts, can be found in the release here .
We invite everyone to try the updated Zabbix system today and share with us their impressions on the network or in person at the Zabbix meetup in Moscow, which will take place on March 12, 2016, at 11:00, at the metro address Trubnaya, Tsvetnoy Boulevard 2. Registration for the meeting will be access in two weeks.
Today I want to share with you what brought the release, and what you can start to use today, download the new version from the site. We will also be happy to invite everyone to Zabbix Meetup in Moscow, details of which you will find at the end of the article.

Interface
The first thing that catches your eye is a faded web interface. The new design got rid of the superfluous, piled up elements, various unnecessary frames of graphs and so on.
')

Also, the interface is designed from the point of view of convenience, for example, now for any network node or template you can always see how your own macros overlap with inherited ones. Available in several designs, light and dark. Be sure to try the dark

About the rest of the interface changes can be read here .
and also in the separate mini-review on Habré.
Encryption
Now Zabbix supports encryption of all messages, if necessary - all communication between the server, proxy and agent can be encrypted and protected from prying eyes of prying eyes.
Encryption also provides authentication - only if you have a trusted certificate or a pre-shared key, components will be able to communicate with Zabbix. Authentication is mutual, that is, not only Zabbix Server verifies the certificate of the agent, but also the agent can be configured to check the server certificate: who issued it and whether they can be trusted.

Encryption is completely optional, and can be configured for each component separately (that is, some agents and proxies can use encryption, while others continue to communicate openly as before)

If you do not need encryption or you are not morally prepared for it, then just use Zabbix as before (taking other new features into account, of course! :)) At the same time, all 3.0 components will support encryption, and it can be gradually enabled for individual components at your own pace.
And no new ports - as before 10050/10051 are used for all types of communications in Zabbix.
All the details about encryption in Zabbix here , as well as in our separate mini-review on Habré.
Prediction and forecasting
Anticipate a problem before it happens? - Now yes, in Zabbix 3.0.
They say that in 2016 the disks still run out of space sometimes. Zabbix can foresee such a situation and save the application from falling, warning everyone in advance and giving time to add or free space just before problems start.
Just look at an example where Zabbix predicts how quickly a place on / home will end, analyzing historical values lately.

Suppose we need 10 hours to react and add or clean a place (as in the screenshot above). And suppose that 1 hour of collected data on free space is enough to make a correct forecast. The real problem for us is when the space on the / (vfs.fs.size [/, free]) section is completely finished, i.e. 0 bytes Then Zabbix should raise the crash when the forecast for 10 hours ahead, based on the collected data for the previous 1 hour, will be 0, or:
{host:vfs.fs.size[/,free].forecast(1h,,10h)}<=0 or you can swap the forecast horizon (10h) and threshold (0 bytes) and use another trigger function:
{host:vfs.fs.size[/,free].timeleft(1h,,0)}<=10h The statistical analysis under the hood of these functions is the same, so just choose the expression that is more convenient.
Learn about prediction in Zabbix here and here .
And also in our separate article on Habré on forecasting.
Monitoring CPU usage by a specific process or application
The new proc.cpu.util data item, available on Linux and Solaris, allows you to monitor CPU usage by each individual process or group of processes.
For example, it may be interesting for the server administrator to control how different users use the CPU. With the key:
proc.cpu.util[,john] he can see the CPU usage of all processes running under john. And if suddenly John is only interested in java:
proc.cpu.util[java,john] In addition to the user name and process, you can specify the type of utilization of the CPU (system, user), the name of the process with the path and other parameters.
Full specifications can be found here .


Performance improvements
History cache
In 3.0, we didn't forget about performance optimization. For example, the history data cache (History Cache) has been seriously reworked. Thanks to the reworking of the structure, the cache works quickly at any items / values ratio, even if only a few data elements fill the server with a large number of historical values.
An index (History index) has been added to keep track of this cache. You can monitor it using the new internal counter zabbix [wcache, index,]

For example, the graph clearly shows how long the processing of eight history syncers of 500000 values for 100 data elements before 3.0 and after took place.
More on this and other internal checks here .
Action cache
In 3.0, the actions themselves and their conditions are also stored in the cache, so as not to disturb the database once again. This innovation will be very useful in large installations and when there is a large amount of events in the system.

Running checks at a specific time
If something was enough to check once a day, it was impossible to choose the exact time. The check could have happened both at night and at lunch, and this could not be influenced in any way.
Well, now you can.
For example, if you need to collect data from office computers, simply set the collection schedule from 9 to 6 on weekdays:

This will allow us to avoid unnecessary accidents about the inaccessibility of shut down computers at night.
In the example above, checks will occur every five minutes (m / 5) only on working days (wd1-5) from 8 to 18 (h9-18), that is, at 9:00, 9:05, 9:10, and so on .

Or would you like to do LLD discovery late at night to minimize the impact on the network? Yes, it can be done in the same way.
Read more about scheduled intervals here .
Custom maps, screens and slides
In Zabbix appeared personal maps, complex screens (screens) and slides.
This allows each user to create their own views of the information that will be convenient for him. And admin rights are not needed.
In this case, the map or screen can be easily shared, making it available to all users, or only to members of a particular group:

Interesting? more here .
The names of groups of data elements using macros
Long ago, people asked about the possibility of using low-level detection (LLD) macros in the name in groups of data elements? Yes, now please and this - prototypes of groups of data elements (Applications) are now available along with prototypes of data elements, triggers, graphs and complex screens.
For example, for network interfaces:

Forced start of database cleanup procedure
The database cleanup procedure is necessary to remove old historical data. If you really need to delete a lot, you will need a large amount of system resources, which may adversely affect other Zabbix processes that are occupied with something more important and more useful.
In 3.0, added the ability to cancel the launch of the cleaning procedure on a schedule and run it manually when necessary. The new feature is supported by both Zabbix proxy and Zabbix server. To use it, you need to disable the scheduled execution of the cleanup in the config file:
HousekeepingFrequency=0 And then it is possible to start database cleaning via the command line:
zabbix_server -R housekeeper_execute About the execution of this and other administrative functions (runtime-control) from the command line, read here .
Ability to work Zabbix component in the foreground
The main Zabbix processes can now be started not only as daemons, if you use the -f (--foreground) switch. In addition to other advantages, this can be useful, for example, when using Zabbix components in Docker.
Dependencies between trigger prototypes
Dependencies between triggers that allow you to get only one accident from a router, instead of a dozen crashes from devices that are located behind it - in Zabbix for quite some time. But unfortunately, this did not work for prototype triggers. Again, in 3.0 this limitation goes away. This will allow, for example, to create a group of triggers from prototypes that have different threshold values and the level of importance (warning and accident) when monitoring the amount of free disk space:


Details can be found here .
Windows service discovery

Those who monitor Windows servers through Zabbix should evaluate the following innovation - the ability to find all available services in Windows through the LLD service.discovery key, and create data elements and triggers for each new service. Found services can also always be filtered through a standard filter mechanism, which is in low-level detection.


More details on how to configure this can be viewed again in the updated LLD documentation .
SMTP with authentication
It is finished! Now it is possible to send notifications easily and without problems: through the Zabbix interface, you configure the connection to the mail server using the login password, as well as encryption, if necessary. No more additional postfix in smarthost mode or uncomprehending views from the administrator of mail servers whom you asked to allow from the Zabbix IP server to send mail anonymously.

Read more here .
Import and export value conversions
Grown up and patterns. Now when loading / unloading in XML, they include all of the value mappings used (value mappings). You can load / unload transformations separately. And still it is possible to download value mappings via API.

Low-level SNMP detection across multiple OIDs
There was a great opportunity to make a decision on detection via SNMP based on not one, but several OIDs.
For example, for interfaces, we can search immediately for ifName, ifAlias, ifDescr, and ifOperStatus:
discovery[{#SNMPVALUE},ifOperStatus,{#IFALIAS},1.3.6.1.2.1.31.1.1.1.18,{#IFNAME},1.3.6.1.2.1.31.1.1.1.1,{#IFDESCR},.1.3.6.1.2.1.2.2.1.2,{#IFTYPE},ifType] And if in the description of the prototype of the trigger specify, for example, here is the following list:
Last Discovery Interface info: ifAlias:{#IFALIAS} ifName:{#IFNAME} ifDescr:{#IFDESCR} ifType:{#IFTYPE} then in case of a crash on the trigger, we can see a detailed description of the port.

You can use the values of additional OIDs in LLD filters, decide whether to set an interface for monitoring or not, as well as use the values in the names of triggers, graphs and data elements. Or, as mentioned above in the names of groups of data elements (Applications).
Read more in the updated LLD manual .
And that's not it
Zabbix 3.0 offers more than 50 new features to explore, with all that did not fall into this article, such as the trends API or the addition of additional parameters for custom alert scripts, can be found in the release here .
We invite everyone to try the updated Zabbix system today and share with us their impressions on the network or in person at the Zabbix meetup in Moscow, which will take place on March 12, 2016, at 11:00, at the metro address Trubnaya, Tsvetnoy Boulevard 2. Registration for the meeting will be access in two weeks.
Source: https://habr.com/ru/post/277265/
All Articles