How graph databases help fight e-commerce fraud
We at Latera are creating billing for telecom operators . In a blog on Habré, we not only talk about the features of our system and the details of its development (for example, ensuring fault tolerance ), but also publish materials about working with infrastructure and using technologies.
An engineer at Akalak & Neo Technology, Gorka Sadakowski, wrote interesting material on how the use of graph databases can in real time prevent e-commerce fraud. We present to you the main thoughts of this article.
')
The world is rapidly becoming digitized, and an increasing number of financial transactions are taking place online. The fraudsters quickly adapted to this state of affairs and came up with a lot of ways to hack online payment systems. And this is not about lone criminals, but about criminal communities that are well-equipped technically.
Fortunately, there are technologies that are capable of detecting and stopping such threats in real time, even before fraudsters do significant damage. These include graph databases. This tool can be used to combat three types of threats:
- theft of bank data (for example, customer information);
- insurance fraud;
- e-commerce fraud.
Today we will talk about the last type of threat - fraud in the field of electronic commerce.
Standard E-commerce Fraud Scenarios
Online transactions use the following types of identifiers:
- User ID;
- IP address;
- geolocation
- tracking cookie - a label that the site leaves on the user's computer for further identification;
- Bankcard number.
It can be assumed that all these identifiers are rigidly tied to a specific person. However, sometimes things are much more complicated — for example, if several people use one computer, or, for example, members of one family pay with a single credit card, or one person uses several computers.
That is, in different cases, for a single user identifiers may vary. But, as soon as the number of such entities exceeds a certain reasonable limit, we can talk about the threat of fraud.
For example, transactions of different users can go through the same IP address, a large number of goods sent to different addresses can be paid for with one card, or the same physical address can appear in the data of a large number of cards.
In each such case, it is possible to identify the pattern inside the graph - you just need to go through the links between the various data blocks. The identification of such patterns can serve as a signal that we are dealing with fraud. The more mutual intersections between different identifiers on the diagram, the more cause for concern.
How can graph databases help?
A database can be configured to search for such suspicious patterns — appropriate checks associated with various triggers can help identify problems before serious damage is caused. Triggers can include events such as logging into the system, placing an order, or registering a new bank card.
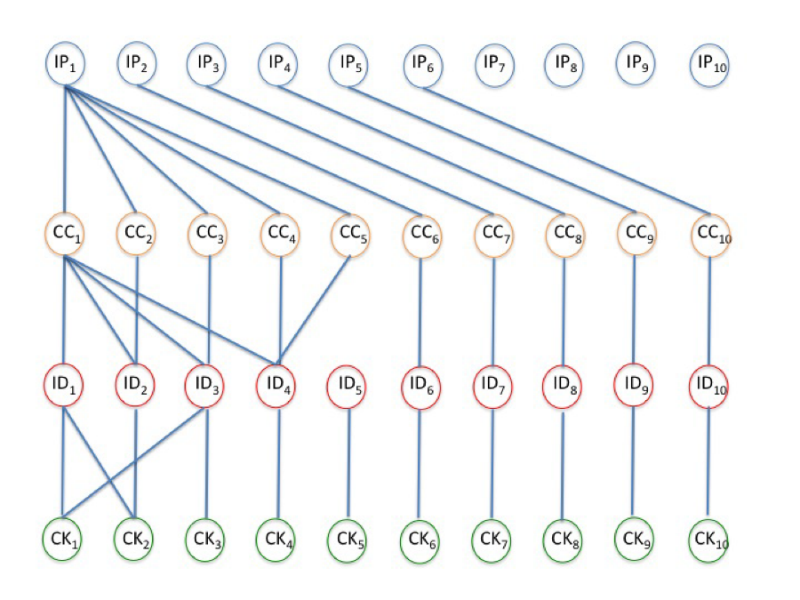
The diagram below shows a series of transactions from different IP addresses. Legend: IPx - different addresses, CCx - certain credit card numbers, IDx - these are user identifiers used for conducting transactions, CKx - specific cookies stored in the system.
In this example, with a high degree of probability, the IP1 address is involved in the fraudulent scheme - from it several transactions were performed using five bank cards. And one of the cards was used by several identifiers at once, besides, two cookies have connections with two identifiers.
Graph databases are the ideal solution for effectively detecting threats related to financial security on a network. This tool allows you to detect the activity of both fraudsters, lonely and well-equipped criminal groups - their activity somehow corresponds to certain patterns, and if they are identified in time, the possible damage can be minimized.
Other interesting articles on the Latera blog:
- Researchers have found many critical vulnerabilities in payment protocols
- How to improve resiliency of billing: The experience of "Hydra"
- Corporate GitHub: how Azure increased the number of employees on GitHub to two thousand
- Open source application architecture: How nginx works
- LinkedIn's brief history of scaling
- Large-scale migration of records in the database: how it does Stripe
Source: https://habr.com/ru/post/277233/
All Articles