Fortinet framework for protection against advanced threats
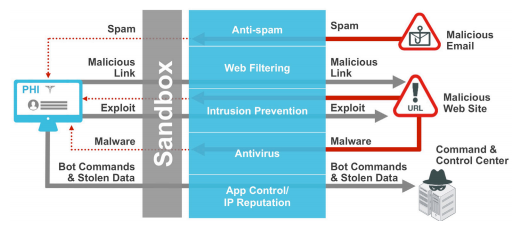
This article describes the final solution for protection against modern threats, the so-called Fortinet ATP (Advanced Threat Protection) Framework, which is positioned as a complete modular solution for cybersecurity. Below is an overview of the solution for automated identification, prevention, suppression of malware and the protection of the entire ecosystem.

')
Advanced malware can cause enormous harm to organizations, from data theft through compromised individuals to the termination of important operations. The attacks of cyber criminals are complex, constantly evolving developments aimed at creating new and cunning methods of penetration and attack.
Partly due to the ever-increasing frequency of public attacks, most organizations have realized the need to improve the IT security infrastructure. According to ESG, 37% of organizations surveyed put cybersecurity improvements at the top of their IT infrastructure development priorities for 2016.
Organizations must evaluate both the ability to identify threats to their IT infrastructure and their ability to counter them. Most of the advanced malware is hidden or zero-day software. Hidden threats are built in order to penetrate the system undetected, sometimes stored in the system in an inactive state for a certain period of time. Zero-day threats are attacks that exploit previously unknown network, operating system, or application vulnerabilities, making it difficult to control them.
Traditionally, security has been implemented on the basis of a perimeter firewall in conjunction with endpoint scanners (workstations). Perimeter firewalls blocked simple types of attacks, preventing unauthorized access to internal systems while the antivirus on the endpoints scanned user devices according to the signatures of previously known or suspected malware. Firewalls of the new generation and endpoint protection software increase the depth of inspection both at the perimeter and at the end device, but they still rely on the search for already known attacks. They are simply not designed to detect the latest, previously unknown attacks. Too often, organizations are not aware of such threats until the moment of significant damage.
Fortinet Framework for Preventing Advanced Threats
Fortinet has developed its own protection framework for advanced threats to provide comprehensive visibility of all activities on the network using existing and new methods using a modular approach to integrating its security products for the network, applications, endpoints and cloud services.

The Advanced Threat Protection Framework includes:
• FortiGate is a next-generation firewall that provides in-depth inspection of packets and the definition of network security and threat protection applications.
• FortiWeb - Web Application Firewall is designed to protect applications available from the Internet. Two-way protection against advanced threats including denial of service, SQL injection, XSS, buffer overflow, cookie poisoning and a large number of other attacks.
• FortiMail - a security gateway for mail, protects email users from incoming threats using anti-spam, anti-phishing, and malware prevention techniques. Outgoing mail protection includes information leakage prevention (DLP), identification-based encryption (IBE), and message archiving.
• FortiClient — protection for Windows, Mac, IOS, and Android endpoints, including, but not limited to, malware protection, application control, web filter, vulnerability management, two factor authentication, and remote access.
• FortiSandbox - centralized analysis and detection of potential threats using code emulation and execution of this code in a virtual protected environment. Checks activity in addition to attributes to determine unwanted behavior. Dynamically takes steps to respond to incidents and update security.
• FortiGuard — Fortinet researchers use information from global sources to research threats and attacks, and also maintain a cloud-based knowledge base about the study of threats and how to prevent them.
FortiGate, FortiWeb and FortiMail are the most common solutions, presented in both hardware and software form, in conjunction with the FortiClient application that is used on end devices that meet the needs of organizations of all sizes. Each product ATP Framework can act as a separate solution or can be combined with other products for enhanced protection due to compatibility. In a fully integrated Framework, protection against network threats and endpoints send potentially dangerous data to FortiSandbox for analysis, which in turn returns instructions for handling data to these products, as well as to FortiGuard's laboratory for distribution to Fortinet products.
Fortinet describes the three phases of its products to ensure coordinated protection: prevention, detection and mitigation.
• Prevention - prevent attacks from many known and highly suspicious threats.
• Detection - identify previously unknown threats and spread information about the threat for an accelerated response.
• Mitigation - research and analyze new data; create a signature and turn the unknown into the known for prevention in the future.
Revealing
Fortinet’s core approach to identifying advanced threats is identifying unknown threats and redirecting them to FortiSandbox to reveal the behavior, tactics, techniques and procedures used in cyber attacks. FortiSandbox uses virtual machines as tools to assess potential threats from executable files, compressed files (zip files), application data such as Adobe Flash, Adobe PDF and JavaScript, etc. However, the execution of each suspicious file on a virtual machine can be resource intensive and take some time. This can limit the total number of suspicious files that can be evaluated, with a significant impact on performance.
Fortinet uses many different techniques to increase efficiency. Prior to sandboxing, suspicious files can be pre-filtered, including screening by the antivirus engine, requests to the FortiGuard cloud service, OS-independent simulation, which is possible thanks to the patented Fortinet Compact Pattern Recognition Language (CPRL). CPRL is a system for deep code inspection and pattern recognition, which allows you to significantly expand the capabilities of protection methods against advanced threats (APT) and recognition of advanced circumvention techniques (AET) that are possible with traditional signature-based analysis.
Each threat identified on the Sandbox includes information on the method used to identify:
• AV scan - the threat was identified by associating a file with the signatures of a known FortiClient (FortiGate / FortiMail) and compliance was confirmed.
• Cloud Query - if the file signature is not known by FortiClient (FortiGate / FortiMail), then it can be matched with the signatures of FortiGuard, a Fortinet cloud service with a knowledge base of advanced threats.
• Sandboxing - the threat was identified when FortiSandbox was evaluating file behavior.
In addition to identification methods, a risk rating is also indicated (clean, low risk, high risk or malicious). The test results include many details about the code and its rating, including a summary assessment of the behavior, screen shots of the malware, and the ability to download additional information in the form of a log.
For example, behavior leading to a high risk rating includes:
• The executable file tried to connect to a remote C & C botnet server.
• Executable file deleted files.
• Executable file spawned processes.
• Users infected with an executable file will notice “http” connections to specific URLs / IP addresses.
• Users infected with the executable file will notice "DNS queries" with certain domain names.
FortiSandbox can extract objects for analysis directly from network traffic or receive from other Fortinet products that are already inspecting traffic. The configuration of the main products of the ATP Fortinet framework (FortiGate, FortiWeb and FortiMail) for integration with FortiSandbox is very simple, the administrator simply enter the FortiSandbox IP address in the sandbox configuration module. The next and final step is to authorize the connection of the Fortinet product in the FortiSandbox interface.

FortiSandbox is also an extension for FortiClient. Administrators can manually configure FortiClient or they can configure an endpoint security profile centrally on FortiGate or FortiClient EMS. This profile will be applied to the group of endpoints in the current environment.

Why this is important : it is clear that a unified approach that combines several methods for detecting and evaluating threats, in which it is possible to redirect files to the sandbox for additional analysis, can provide an important additional layer of protection and eliminate gaps that are easily exploited by new and previously unknown threats.
Softening
Fortinet's unified approach to protection is designed to mitigate previously unknown threats and attacks detected by FortiSandbox. In the context of cybersecurity, mitigation is defined as reducing the likelihood of undesirable events and / or reducing the impact and consequences. All Fortinet products that can work with FortiSandbox send objects for analysis and use data received from FortiSandbox to speed up the response and mitigate the threats identified.
For example, a snapshot of the FortiSandbox interface with a report of five facts of suspicious behavior. From the snapshot you can see that the malware behaves like a rootkit, creates copies of itself and deletes itself after execution. Since this behavior can be quite destructive, it is highlighted in red.


The Files Created section shows all the files that were created by malware with their MD5 sums check. Potentially dangerous activity, such as making a copy of yourself, is highlighted in red.
The results tab also allows the administrator to download a copy of the original file from FortiSandbox, in addition to the log with a detailed description of all the activities of the analyzed file, screenshots and all captured packets from the traffic initiated by malware.
Once a positive decision is made that the file is malicious, the mitigation action can be automatic or based on policies that can be set at each control point. The following screenshot shows the possible settings on FortiClient.

Mitigation can be applied anywhere in the ecosystem. FortiGate, FortiWeb and FortiMail provide the quarantine option. The following image shows that FortiGate has the ability to isolate both the infected device and the source. FortiWeb has the same options.

Why this is important : Fortinet's integrated security ecosystem provides consolidated mitigation and recovery from the effects of malware activity, while the administrator is able to perform an automated response to incidents requiring intervention. The interaction of Fortinet products with FortiSandbox allows such automation across all threat vectors. Based on information from control points, the infected systems are cleaned and isolated.
Prevention
The least problematic attack is the one that was prevented. The Fortinet Advanced Threat Protection framework automates and consolidates the analysis of suspicious files at all control points from several potential vectors using techniques including direct traffic inspection and interaction with FortiGate, FortiClient, FortiWeb and FortiMail. When interacting with other Fortinet products, the load on the FortiSandbox is reduced and the need for a manual, time-consuming reaction to prevent attacks is minimized.
In addition to using traditional threat prevention technologies in these products to block known threats and attacks (for example, application control, intrusion prevention, web filtering, anti-virus and anti-spam), FortiSandbox plays a very important role in preventing the most advanced and unknown threats.

FortiMail and FortiClient automatically retain unknown files and wait for analysis from FortiSandbox to allow delivery or installation, bypassing the need to mitigate threats.
FortiGate and FortiClient can be configured to receive signature updates directly from FortiSandbox. This is useful for preventing the spread of targeted attacks and multistage attacks, whose components are actively deployed by FortiSandbox before they affect end users.

Finally, FortiSandbox has the ability to optionally transfer analysis data to the FortiGuard service, allowing you to distribute signatures among the entire portfolio of Fortinet security products, and not just within a specific ecosystem. This approach strengthens the protection of the entire Fortinet user community.

Why this is important : security breaches are becoming more common, while traditional, autonomous solutions are targeting zero-day zero-day attacks. Organizations that rely on this type of decision may potentially be vulnerable to attacks with serious financial and operational implications. Prevention allows organizations to get out of the reactive mode and focus on proactive, strategic measures to enhance security. Using the advanced detection capabilities of FortiSandbox and deep knowledge about attacks from FortiGuard Labs, organizations have the tools they need to prevent attacks before they happen.
Finally
Any corporate infrastructure computing device, from smartphones and tablets to laptops, desktops, and application services, is subject to security breaches. Attacks affect organizations of any size indiscriminately, the consequences can be devastating for operations, company reputation and bank accounts. Costs arising from successful attacks can include not only the resumption of operations and the resolution of security problems, but also legal liability and regulatory fines.
The Fortinet protection framework for advanced threats is easy to understand and manage. Fortinet's modular approach with stand-alone products that can be combined to implement prevention, detection and mitigation can improve detection and protection against advanced attacks in comparison with individual security systems from other manufacturers. Integration of Fortinet products into an entire ecosystem is quite simple in terms of configuration, thanks to an intuitive interface and many publicly available documentation. After configuration, the analysis of unknown files, no matter how they got into the ecosystem, occurs automatically. The FortiSandbox graphical user interface provides intuitive access to understandable and clear information. FortiSandbox makes the understanding of the current level of security clear and easy to understand.
The Fortinet solution offers the functionality, features, and connectivity that solve the entire spectrum of an organization’s security requirements, giving security teams the ability to detect, prevent, and mitigate threats. The ability to work as stand-alone products or unite into a full framework provides the flexibility to integrate into almost any system. Companies that are looking for more flexible, effective solutions to improve security will be satisfied with the Fortinet Framework for protection against advanced threats.
Distribution of Fortinet solutions in Ukraine , Armenia , Georgia , Kazakhstan , Azerbaijan , Kyrgyzstan , Tajikistan , Turkmenistan , Uzbekistan , CIS countries .
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/277135/
All Articles