Trojan Remtasu is a tool for hacking Facebook
Almost a year ago, we warned our users about the proliferation of Remtasu malware. To date, its activity has not diminished at all and we have managed to fix numerous modifications of this threat, which is being used by attackers.

Analysts of our office in Latin America have recorded the most active modifications of Win32 / Remtasu.Y in Latin America, mainly in Colombia, as well as in Turkey, Thailand, and other countries. One of the latest campaigns was associated with a malicious tool, supposedly designed to get passwords from Facebook accounts.
')
Until last year, we quite often encountered malicious campaigns in which attackers appeared to be specialists from various organizations, including DIAN, Avianca and Falabella. E-mails sent, ostensibly, from these companies contained fake Microsoft Office documents with the so-called. invoices or other official documents.
In recent malicious campaigns, we discovered new social engineering mechanisms that use the Facebook theme and the desire of users to access other people's accounts.
Fig. Remtasu is a malicious application.
Although the above malware belongs to the same malware family, its distribution differs from previous ones. Attackers no longer use email distribution, but instead switched to downloading malicious objects from sites. As soon as a user downloads a suspicious file from a phishing or compromised web resource and launches it for execution, the system will be compromised.
The malicious application uses the UPX wrapper to compress its content.
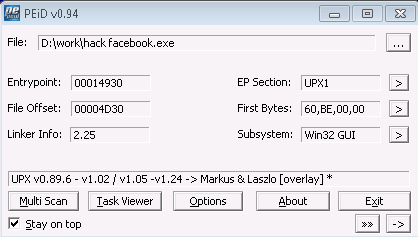
Fig. Malicious file is packed by UPX.
After unpacking the content, we can see the imports of the executable file, which will provide us with information about its purpose.

Fig. Import functions of the Remtasu file, which are responsible for working with the clipboard.
As seen in the screenshot above, the malicious file accesses the functions for working with the clipboard. By accessing this data, the malicious code can save the contents of the clipboard and keys pressed by the user to a separate file, and then send them to the server via FTP. The screenshot below shows the imports for working with FTP.

Fig. Remtasu Imports, which are responsible for obtaining information about keystrokes and working with FTP.
To ensure its startup in the system, the malware uses a special registry key. It also clones its file in the file system and stores it in a directory called InstallDir , which is hidden and created in the system32 system directory.

Fig. The malicious system registers itself in the registry key for autoload.
Remtasu creates its copy in a file with a name that can mislead the user about the functions they perform. Since many users are looking for the names of executable program files on the Internet, they will receive incorrect information about the purpose of the application. Previous modifications of Remtasu used the name of one of the Windows system processes csrss.exe as the name of their file. Unlike the previous name, in our case it is quite general.
It is important to note that in the first weeks of 2016 we recorded 24 different modifications of this malware family, with a quarter of all these detections falling on Win32 / Remtasu.Y, and then Win32 / Remtasu.O followed with 23% of detections. This means that almost half of the modifications found in this family fall within the above two options.
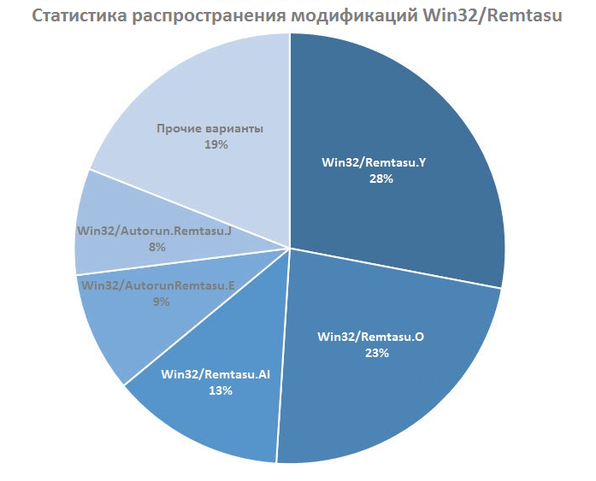
Fig. Detection statistics for various modifications of Remtasu.
In addition, it is worth noting that 65% of all Win32 / Remtasu detections are in Colombia. Colombia is followed by Thailand with a detection rate of 6%, most of which occur in the Win32 / AutoRun.Remtasu.E modification. They are followed by Mexico and Peru with 3% and 2% respectively.
We advise users not to follow suspicious links, as this will significantly reduce the risk of system infection even with an anti-virus product installed. Our research laboratory constantly monitors the appearance of such threats and performs their analysis to inform users in a timely manner and ensure their protection.
The analyzed sample file was obtained with the name “hack facebook.exe”, had a SHA1 hash: 03AA8D8BFDF54BF390B03D1886E34C71865592EA and is detected by ESET antivirus products as Win32 / Remtasu.Y.

Analysts of our office in Latin America have recorded the most active modifications of Win32 / Remtasu.Y in Latin America, mainly in Colombia, as well as in Turkey, Thailand, and other countries. One of the latest campaigns was associated with a malicious tool, supposedly designed to get passwords from Facebook accounts.
')
Until last year, we quite often encountered malicious campaigns in which attackers appeared to be specialists from various organizations, including DIAN, Avianca and Falabella. E-mails sent, ostensibly, from these companies contained fake Microsoft Office documents with the so-called. invoices or other official documents.
In recent malicious campaigns, we discovered new social engineering mechanisms that use the Facebook theme and the desire of users to access other people's accounts.
Fig. Remtasu is a malicious application.
Although the above malware belongs to the same malware family, its distribution differs from previous ones. Attackers no longer use email distribution, but instead switched to downloading malicious objects from sites. As soon as a user downloads a suspicious file from a phishing or compromised web resource and launches it for execution, the system will be compromised.
The malicious application uses the UPX wrapper to compress its content.

Fig. Malicious file is packed by UPX.
After unpacking the content, we can see the imports of the executable file, which will provide us with information about its purpose.

Fig. Import functions of the Remtasu file, which are responsible for working with the clipboard.
As seen in the screenshot above, the malicious file accesses the functions for working with the clipboard. By accessing this data, the malicious code can save the contents of the clipboard and keys pressed by the user to a separate file, and then send them to the server via FTP. The screenshot below shows the imports for working with FTP.

Fig. Remtasu Imports, which are responsible for obtaining information about keystrokes and working with FTP.
To ensure its startup in the system, the malware uses a special registry key. It also clones its file in the file system and stores it in a directory called InstallDir , which is hidden and created in the system32 system directory.

Fig. The malicious system registers itself in the registry key for autoload.
Remtasu creates its copy in a file with a name that can mislead the user about the functions they perform. Since many users are looking for the names of executable program files on the Internet, they will receive incorrect information about the purpose of the application. Previous modifications of Remtasu used the name of one of the Windows system processes csrss.exe as the name of their file. Unlike the previous name, in our case it is quite general.
It is important to note that in the first weeks of 2016 we recorded 24 different modifications of this malware family, with a quarter of all these detections falling on Win32 / Remtasu.Y, and then Win32 / Remtasu.O followed with 23% of detections. This means that almost half of the modifications found in this family fall within the above two options.

Fig. Detection statistics for various modifications of Remtasu.
In addition, it is worth noting that 65% of all Win32 / Remtasu detections are in Colombia. Colombia is followed by Thailand with a detection rate of 6%, most of which occur in the Win32 / AutoRun.Remtasu.E modification. They are followed by Mexico and Peru with 3% and 2% respectively.
We advise users not to follow suspicious links, as this will significantly reduce the risk of system infection even with an anti-virus product installed. Our research laboratory constantly monitors the appearance of such threats and performs their analysis to inform users in a timely manner and ensure their protection.
The analyzed sample file was obtained with the name “hack facebook.exe”, had a SHA1 hash: 03AA8D8BFDF54BF390B03D1886E34C71865592EA and is detected by ESET antivirus products as Win32 / Remtasu.Y.
Source: https://habr.com/ru/post/276889/
All Articles