Bind additional one-time passwords to the Windows logon window
On Habré for a long time already know about one-time passwords and OTP (One Time Password) technologies. Even Yandex came up with its own solution. I want to tell you about how I screwed an interesting OTP implementation to the Windows Terminal Server login window.
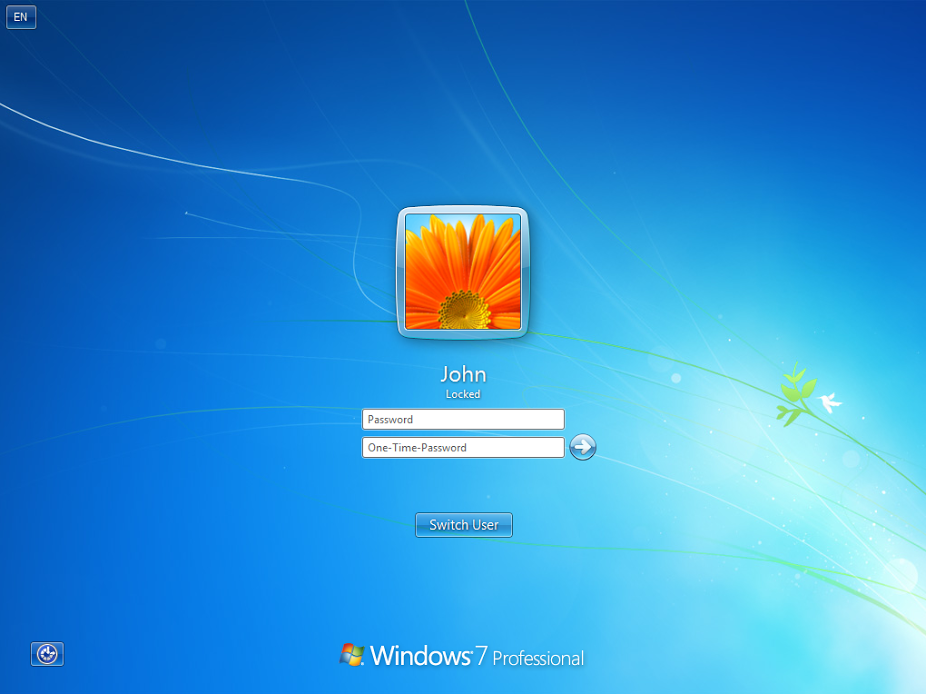
All the functionality of the solution rests on a wonderful multiotp project, an open source PHP software that can work with both TOTP and HOTP , and even with OCRA . And you can run this beauty in * nix and in Windows. There is even a web interface and releases for virtualization systems, but this is already you dig yourself, we will make the minimum necessary set of actions to start.
Binding mutltiotp to the Windows logon window is performed using the MultiOneTimePassword-CredentialProvider plugin.
The user will generate one-time passwords on his computer or mobile device.
The order of actions is indicated on the page of the plugin, but the syntax has changed in the latest version of multiotp, so I will go over all the actions for you once again.
')
Download multiotp and place it somewhere on the server. I will drop the root of the C: \ multiotp system disk.
Then you need to create a key for each user created on the server. I emphasize - we are talking about local users. Multiotp has the ability to bind to ldap, but this is too big a topic for one article.
To create users, 160-bit HEX keys (i.e., 20 characters in hexadecimal notation) are required. You can (and should) generate them on your own in a protected environment, but for laboratory purposes, I will offer you this generator . Give him the key length (20) and the number of users on your system, he will do everything himself. Save these keys somewhere, they will come in handy later.
The user creation command looks like this (of course, in cmd, go to the directory with the unpacked multiotp):
% USERNAME% - user account name in Windows;
% TOTP% - creating keys for TOTP technology (based on a time stamp);
% KEY% - the key created in the previous step;
% PIN% - additional permanent pin, which the user will write before his temporary password (it can be not used, but the command requires you to specify a key);
% LENGTH% - the length of one-time passwords (6-character are recommended, since most applications generate them);
% LIVETIME% - the validity period of one-time passwords (it is recommended to specify 30 seconds, since most applications generate them).
Example:
Now we need to somehow give users the key so that they can generate one-time passwords. The full functionality of multiotp allows us to create a QR code through a web interface, which we shoot on our phones and continue to work with them. I show minimal functionality without an interface, so I’ll have to work with my hands.
You will need the keys created in the second step to convert from 160-bit HEX to Base32. Again, it is better to do it in a protected environment, who is too lazy, here's an online converter for you . He doesn't even https, so be careful with him. It seems to work clearly, pay attention to the register when entering keys.
Converted keys must be given to the user. There are a bunch of applications for mobile OS that can generate one-time passwords. I love Google Authenticator , it works on most operating systems. Who wants to indulge and not to clog the mobile device - you can put the plugin in the browser.
The application or plugin needs to specify the key created in step four. There is nothing difficult, I think you will figure it out.
To check the correct operation of the multiotp service, test the generated keys on the command line as follows:
% GENERATED_TOKEN% - key generated by the application on a mobile device (keep track of the time, you have only 30 seconds since the password was generated)
The answer on the command line should look like this:
The only thing left is to download and install the plugin for Windows. The installer asks few questions. You need to install the Default Provider component (otherwise it will not do anything), specify the path to multiotp and write a message for the Windows logon window.
Is done. You can check the work.
1) Be sure to create passwords for everyone, including the administrator, otherwise he will not be allowed into the system.
2) Be sure to set the exact time on the server and on user devices, otherwise your keys will not work. The point is not exactly, but the fact that the time here and there must be the same.
3) Sometimes it does not show the result on the command line, but you can always read the log.
4) If you are interested in how to tie this beauty to the domain - tell me, I will try and accomplish my goal.
5) The functionality is huge, everything is on the wiki multiotp: sms, QR, synchronization, backup, binding to anything.
For those who like to perceive information this video can be useful.
Received incredibly good comments and clarifications from a friend who wished to remain anonymous:
1) At the very beginning of server setup, enter the command:
2) With this command you can adjust bantime, for users who made a mistake with the password (30 seconds by default):
3) What is written in the google Authenticator application over 6 digits, called the issuer, can be changed from the default MultiOTP to something else:
4) After the done operations, the user creation team becomes a bit simpler:
5) Each user can change the description (the text under the numbers in the Google Auth application):
6) QR codes can be created immediately in the application:
7) It is possible to use not only TOTP, but also HOTP (not the current time, but the incremental counter value is fed to the input of the hashing function):
8) If the user forgot / lost the phone, you can generate a dozen one-time codes using the command:
9) And good explanations

How it all works
All the functionality of the solution rests on a wonderful multiotp project, an open source PHP software that can work with both TOTP and HOTP , and even with OCRA . And you can run this beauty in * nix and in Windows. There is even a web interface and releases for virtualization systems, but this is already you dig yourself, we will make the minimum necessary set of actions to start.
Binding mutltiotp to the Windows logon window is performed using the MultiOneTimePassword-CredentialProvider plugin.
The user will generate one-time passwords on his computer or mobile device.
The order of actions is indicated on the page of the plugin, but the syntax has changed in the latest version of multiotp, so I will go over all the actions for you once again.
')
Installing the multiotp service
Download multiotp and place it somewhere on the server. I will drop the root of the C: \ multiotp system disk.
Key generation
Then you need to create a key for each user created on the server. I emphasize - we are talking about local users. Multiotp has the ability to bind to ldap, but this is too big a topic for one article.
To create users, 160-bit HEX keys (i.e., 20 characters in hexadecimal notation) are required. You can (and should) generate them on your own in a protected environment, but for laboratory purposes, I will offer you this generator . Give him the key length (20) and the number of users on your system, he will do everything himself. Save these keys somewhere, they will come in handy later.
Creating custom keys
The user creation command looks like this (of course, in cmd, go to the directory with the unpacked multiotp):
multiotp.exe -debug -create %USERNAME% %TOTP% %KEY% %PIN% %LENGTH% %LIVETIME% % USERNAME% - user account name in Windows;
% TOTP% - creating keys for TOTP technology (based on a time stamp);
% KEY% - the key created in the previous step;
% PIN% - additional permanent pin, which the user will write before his temporary password (it can be not used, but the command requires you to specify a key);
% LENGTH% - the length of one-time passwords (6-character are recommended, since most applications generate them);
% LIVETIME% - the validity period of one-time passwords (it is recommended to specify 30 seconds, since most applications generate them).
Example:
multiotp.exe -debug -display-log -create rdpclient1 TOTP 6696f39315f4c6388216 1234 6 30 those. created a key for user rdpclient1 with pin 1234 (command syntax requires you to specify a pin, even if we plan not to use it); multiotp.exe -debug -display-log -set user pin= those. said that pin is really not needed.Key conversion for users
Now we need to somehow give users the key so that they can generate one-time passwords. The full functionality of multiotp allows us to create a QR code through a web interface, which we shoot on our phones and continue to work with them. I show minimal functionality without an interface, so I’ll have to work with my hands.
You will need the keys created in the second step to convert from 160-bit HEX to Base32. Again, it is better to do it in a protected environment, who is too lazy, here's an online converter for you . He doesn't even https, so be careful with him. It seems to work clearly, pay attention to the register when entering keys.
Key Generation Applications
Converted keys must be given to the user. There are a bunch of applications for mobile OS that can generate one-time passwords. I love Google Authenticator , it works on most operating systems. Who wants to indulge and not to clog the mobile device - you can put the plugin in the browser.
The application or plugin needs to specify the key created in step four. There is nothing difficult, I think you will figure it out.
Check service operation
To check the correct operation of the multiotp service, test the generated keys on the command line as follows:
multiotp.exe -display-log user %GENERATED_TOKEN% where user is the username in Windows;% GENERATED_TOKEN% - key generated by the application on a mobile device (keep track of the time, you have only 30 seconds since the password was generated)
The answer on the command line should look like this:
0 OK: Token accepted Connecting the authorization plugin in Windows
The only thing left is to download and install the plugin for Windows. The installer asks few questions. You need to install the Default Provider component (otherwise it will not do anything), specify the path to multiotp and write a message for the Windows logon window.
Is done. You can check the work.
Nuances:
1) Be sure to create passwords for everyone, including the administrator, otherwise he will not be allowed into the system.
2) Be sure to set the exact time on the server and on user devices, otherwise your keys will not work. The point is not exactly, but the fact that the time here and there must be the same.
3) Sometimes it does not show the result on the command line, but you can always read the log.
4) If you are interested in how to tie this beauty to the domain - tell me, I will try and accomplish my goal.
5) The functionality is huge, everything is on the wiki multiotp: sms, QR, synchronization, backup, binding to anything.
For those who like to perceive information this video can be useful.
UPD:
Received incredibly good comments and clarifications from a friend who wished to remain anonymous:
1) At the very beginning of server setup, enter the command:
multiotp.exe -debug -config default-request-prefix-pin=0 display-log=1 after it, you do not need to enter a pin code when setting up a user, and the display of the log of each operation is included in the console.2) With this command you can adjust bantime, for users who made a mistake with the password (30 seconds by default):
multiotp.exe -debug -config failure-delayed-time=60 3) What is written in the google Authenticator application over 6 digits, called the issuer, can be changed from the default MultiOTP to something else:
multiotp.exe -debug -config issuer=other 4) After the done operations, the user creation team becomes a bit simpler:
multiotp.exe -debug -create user TOTP 12312312312312312321 6 (I do not set the update time for digits equal to 30 seconds, it seems to be 30 by default).5) Each user can change the description (the text under the numbers in the Google Auth application):
multiotp.exe -set username description=2 6) QR codes can be created immediately in the application:
multiotp.exe -qrcode username c:\multiotp\qrcode\user.png:\multiotp\qrcode\user.png 7) It is possible to use not only TOTP, but also HOTP (not the current time, but the incremental counter value is fed to the input of the hashing function):
multiotp.exe -debug -create username HOTP 12312312312312312321 6 Example
HOTP can be used in situations where the boss likes iron solutions, not software: for example, Yubikey is programmed to use HOTP and is suitable for this. We later completely abandoned Yubikey + HOTP, because if the user clicked on Yubikey in the wrong window, his subsequent codes will be inappropriate (the yubikey counter will be ahead by one) and we will have to synchronize them with the server:
multiotp.exe -resync user 061735 729371 8) If the user forgot / lost the phone, you can generate a dozen one-time codes using the command:
multiotp.exe -scratchlist username 9) And good explanations
about the stability of the solution:
It has been working for more than a year on several servers, there have never been any problems with it. If there is any problem with multiotp (we prepared for this and tested possible options), then it is enough to load the server in safe mode: in this case it will boot from the default credential provider (without the participation of multi-otp) and after that you will need to either disable multiotp provider in the registry, or temporarily uninstall it by first making a backup copy of the c: \ multitop folder
Source: https://habr.com/ru/post/276865/
All Articles