ARP: Cisco equipment features and interesting cases. Part 1

Hi habr! Each future engineer in the process of studying network technologies gets acquainted with the ARP protocol (Address Resolution Protocol, hereinafter referred to as ARP). The main task of the protocol is to obtain the L2 address of the device at the known L3 address of the device. At the dawn of a professional career, a novice specialist, it seems to me, rarely faces situations where you need to recall the existence of ARP. It seems that ARP is some kind of autonomous service that does not require any intervention in its work, and if there are any problems with communication, many people who have inexperience may forget to check ARP operation.
I remember my order of thoughts when I started working as a network engineer: “So, the interface has risen, there are no errors in physics, it seems. The route where to send the packages, I registered. There are no access lists. So why not traffic? What is still not enough for the router? ”Sooner or later, every network engineer will face a problem, the cause of which will lie precisely in the peculiarities of ARP operation / configuration on network equipment. The simplest example: changing the gateway at the edge of the network (for example, we install a router instead of an MS TMG server). In this case, the configuration of the router was tested in advance in the laboratory. And here, when connecting to the provider, no connection works. Return MS TMG - everything works. Where to look after checking the channel and physical layer? The most likely answer is to check ARP operation.
')
In this article I will not describe in detail the principles of operation of ARP and protocols of this family (RARP, InARP, UnARP, etc.). There are already lots of articles on this topic on the Internet (for example, ARP variants are not well described here ). The only theoretical point on which I will focus a little more attention is the Gratuitous ARP (GARP) mechanism.
The article will consist of two parts. In the first part there will be some theory and features of ARP operation on Cisco routers related to NAT rules and the Proxy ARP feature. In the second part I will describe the differences in ARP work between Cisco routers and Cisco ASA firewalls, and I will also share several interesting cases from practice related to ARP work.
A little bit of theory
ARP request / ARP response
Below is an example of exchanging an ARP request / ARP response in the Wireshark sniffer program:
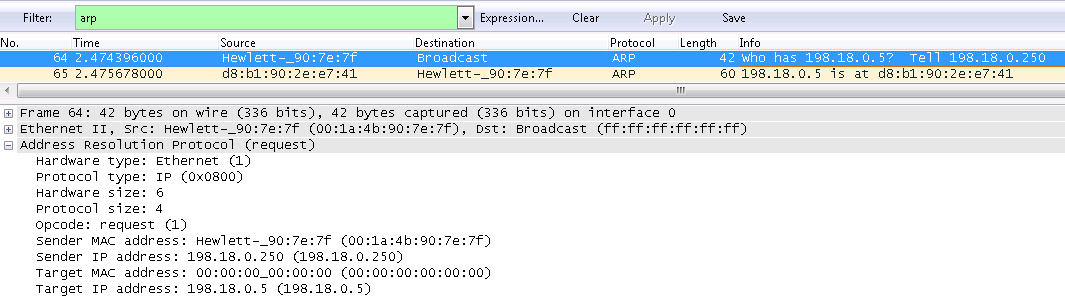
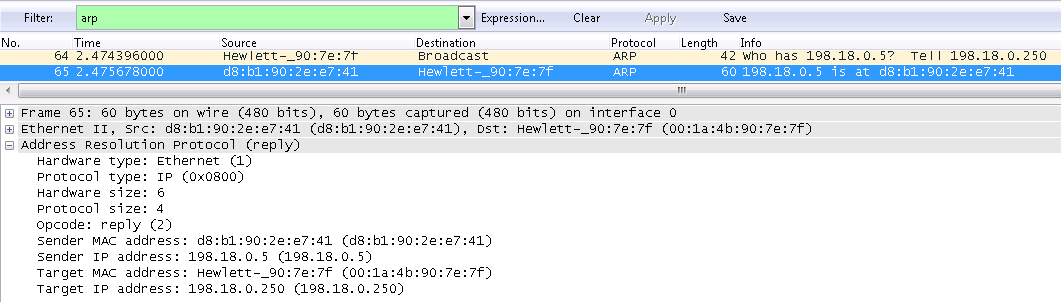
The ARP request is sent to the broadcast MAC address ff: ff: ff: ff: ff: ff. In the body of an ARP request, the field with the unknown value of the Target MAC Address is filled with zeros.
The ARP reply is sent to the MAC address of the recipient who sent the ARP request. The Sender MAC Address field indicates the requested MAC address of the device.
The opcode field in the ARP header may take the value 1 for the ARP request and the value 2 for the ARP response.
In order for two devices to start sending traffic between each other, there must be a corresponding neighboring device entry in their ARP tables. It is logical to assume that the ARP entry appears in the tables; for each device, the ARP request / ARP response should be worked out. That is, before sending traffic to the networks, two ARP requests and two ARP responses (ARP request / ARP response for the first computer and ARP request / ARP response for the second computer) must pass through. However, this assumption is not true for all cases. Cisco networking equipment adds a new entry to the ARP table immediately after an ARP request arrives from the remote device.
Consider an example. A new device is added to the broadcast domain with the address 198.18.0.200. Start the ping from the new device and see debug arp on the Cisco router:
019383: Feb 4 10:38:55 UTC: IP ARP: rcvd req src 198.18.0.200 64e9.50c8.d6cd, dst 198.18.0.1 GigabitEthernet0/0/1.7 019384: Feb 4 10:38:55 UTC: IP ARP: creating entry for IP address: 198.18.0.200, hw: 64e9.50c8.d6cd 019385: Feb 4 10:38:55 UTC: IP ARP: sent rep src 198.18.0.1 d8b1.902e.e741, dst 198.18.0.200 64e9.50c8.d6cd GigabitEthernet0/0/1.7 As you can see, immediately after the arrival of an ARP request from an unknown IP address (rcvd req src 198.18.0.200), the router creates a corresponding entry in its ARP table (creating entry for IP address: 198.18.0.200, hw: 64e9.50c8.d6cd ).
For the current article, I did not conduct a detailed study on what kind of network equipment adds an ARP entry at the onset of an ARP request. However, I assume that the described behavior is inherent not only to Cisco network equipment, but also to network equipment from other manufacturers, since this mechanism allows for a significant reduction in ARP traffic on the network.
ARP request / ARP response for end equipment
The described behavior is inherent in network equipment. The end equipment, in most cases, receives an entry into the ARP table only after the full ARP request / ARP reply procedure. For example, I checked the procedure on a computer with a Windows 7 operating system. Below is a dump of ARP packets. In this example, arp-cache was cleared on the Cisco router and on the Windows computer. After that, the ping from the router to the computer was launched.
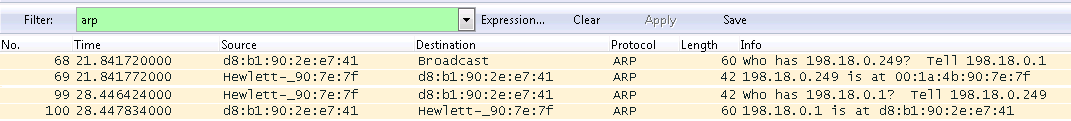
From the presented dapma, you can see that the router first sends an ARP request and receives an ARP reply. But an ARP request from the router does not result in the required entry in the ARP table of the Windows computer, therefore, in turn, the computer sends an ARP request and receives an ARP response from the router.

From the presented dapma, you can see that the router first sends an ARP request and receives an ARP reply. But an ARP request from the router does not result in the required entry in the ARP table of the Windows computer, therefore, in turn, the computer sends an ARP request and receives an ARP response from the router.
Gratuitous ARP
The Gratuitous ARP mechanism is used to notify devices within the broadcast domain about the appearance of a new IP address and MAC address binding. When the device’s network interface receives IP settings (manually or via DHCP), the device sends a Gratuitous ARP message to notify its neighbors of its presence. Gratuitous ARP message is a special kind of ARP response. The opcode field takes the value 2 (ARP response). The MAC address is obtained both in the Ethernet header and in the body of the ARP response is broadcast (ff: ff: ff: ff: ff: ff). The Target IP Address field in the body of the ARP response matches the Sender IP Address field.
The Gratuitous ARP mechanism is used for many purposes. For example, using Gratuitous ARP, you can notify about the change of the MAC address or detect IP address conflicts. Another example is the use of First Hop redundancy protocols (First Hop Redundancy Protocols), for example, HSRP from Cisco. Remember, HSRP allows you to have a virtual IP address shared between two or more network devices. In normal operation, the maintenance of the virtual IP address (responses to ARP requests, etc.) is provided by the primary device. If the primary device fails, the virtual IP address service goes to the second device. To notify about the change of the MAC address of the responsible device, a Gratuitous ARP message is being sent.
The example below shows a Gratuitous ARP message when you turn on the router's network interface with configured IP addresses 198.18.0.1.
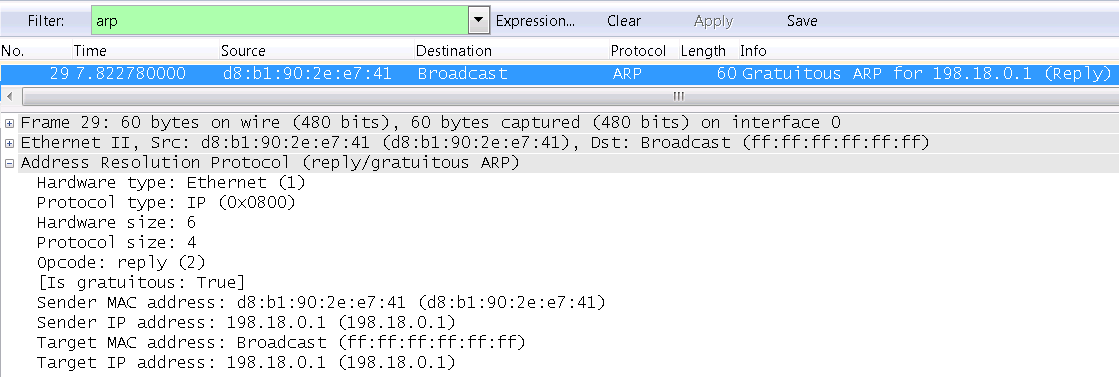
If the router has a secondary IP address configured, when the interface transitions to the UP state, Gratuitous ARP notifications will be sent for each interface IP address. The example below shows the Gratuitous ARP messages sent when the router interface with the primary IP address 198.18.0.1 and the secondary IP address 198.18.2.1 is enabled.
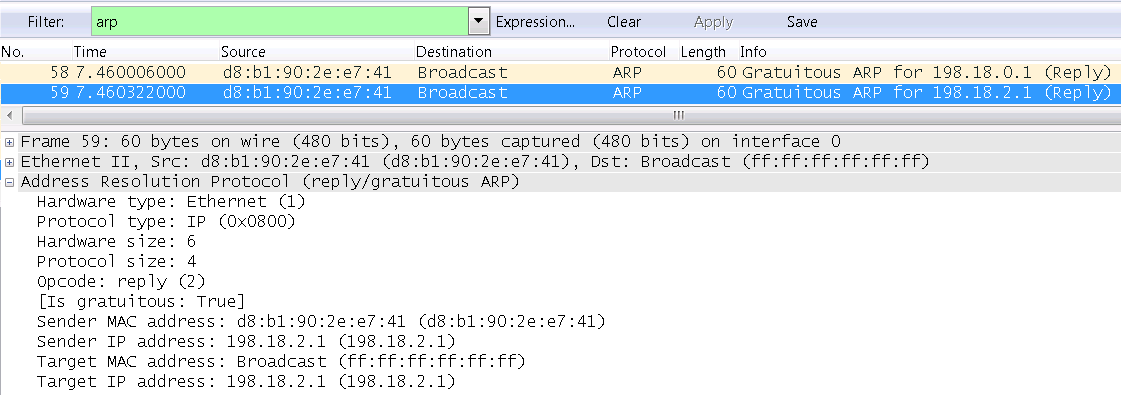
Of course, the router will respond to ARP requests for both the primary and secondary IP addresses.
It is logical to assume that as soon as the device receives Gratuitous ARP, a new entry is immediately added to the ARP table. However, it is not. If there is no ARP entry in the device table associated with the IP address from the Gratuitous ARP message, the new entry will not be added. If you need to send traffic, an ARP request will be generated and an ARP response will be received. Only after this procedure will a new entry be added to the ARP table.
An example on a Cisco router. Turn on debug arp and connect a new device with the address 198.18.0.200 to the broadcast domain. Before connecting a new device, the ARP table of the router looks like this:
cisco#sh arp | inc 198.18.0.200 < > We include the new device with the address 198.18.0.200. We receive a debug message about the arrival of Gratuitous ARP:
IP ARP: rcvd rep src 198.18.0.200 64e9.50c8.d6cd, dst 198.18.0.200 GigabitEthernet0/0/1 Check the ARP table:
cisco#sh arp | inc 198.18.0.200 < > A new entry has not appeared. We ping to the new address:
cisco#ping 198.18.0.200 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 198.18.0.200, timeout is 2 seconds: 019275: Feb 4 10:23:06 UTC: IP ARP: creating incomplete entry for IP address: 198.18.0.200 interface GigabitEthernet0/0/1 019276: Feb 4 10:23:06 UTC: IP ARP: sent req src 198.18.0.1 d8b1.902e.e741, dst 198.18.0.200 0000.0000.0000 GigabitEthernet0/0/1 019277: Feb 4 10:23:06 UTC: IP ARP: rcvd rep src 198.18.0.200 64e9.50c8.d6cd, dst 198.18.0.1 GigabitEthernet0/0/1 .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 2/2/3 ms Debug messages indicate that an ARP request / ARP response has passed. Check the ARP table:
cisoc#sh arp | i 198.18.0.200 Internet 198.18.0.200 6 64e9.50c8.d6cd ARPA GigabitEthernet0/0/1 New entry has appeared.
ARP and NAT on Cisco routers
Now let's look at how things work with ARP, if the router uses network address translation rules - NAT or PAT. In this case, we can broadcast the address or addresses of the local network either to the address of the router's interface, or to some other address, which in NAT terminology will be called an inside global address (inside global or inside mapped). If the translation happens to the interface address, there are no questions with ARP. In the case of translation to an address other than the interface address, the following rules apply:
- If the inside global address is on the same IP subnet as the router's interface address, the router will respond to ARP requests to that address. At the same time, a static entry for the internal global address is created in the router's own arp-table.
- If the inside global address is on an IP subnet other than the router's interface address, the router will not respond to ARP requests to this address. A static entry is not created in its own arp table. For the connection with such an IP address to work, additional configuration is required. We will look at this case in more detail later in the article.
We should also mention the behavior of Gratuitous ARP. I will not consider the options for generating Gratuitous ARP for various cases (transition of the interface to the UP state, changing the primary IP address of the interface, changing the Secondary IP address, etc.), since there will be too many options. I want to specify only two points. The first point: setting up a new NAT rule does not generate a Gratuitous ARP notification. The second point: using the clear arp-cache command, you can not only clear all dynamic arp entries in the router's table, but also force the router to send Gratuitous ARP for all IP addresses that the router must respond to, including the internal global addresses from the NAT rules.
Consider examples based on the following simplest topology:
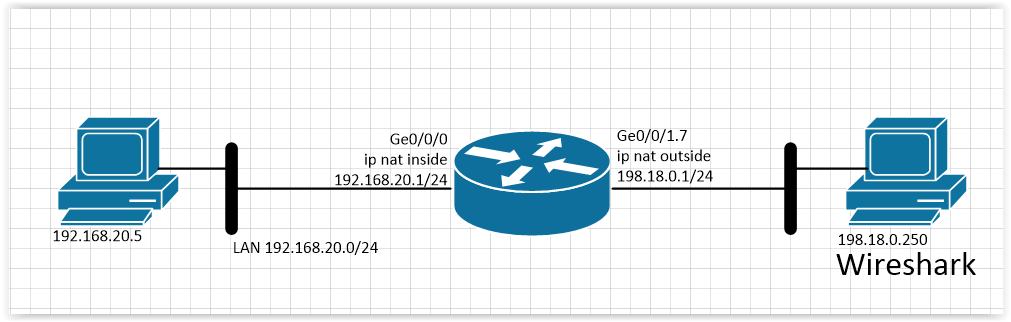
Note: The tests used a C4321 router with 15.4 (3) S3 software and a Cisco ASA5505 firewall with 9.1 (6) 6 software.
Computer Wireshark from addresses 198.18.0.250 in our case will designate connection to an external network (for example, to an Internet provider). With the help of Wireshark sniffer, we will look at the ARP messaging between the router and the computer.
Router Interface Settings:
interface GigabitEthernet0/0/0 description === inside === ip address 192.168.20.1 255.255.255.0 no ip proxy-arp ip nat inside ! interface GigabitEthernet0/0/1.7 description === outside === ip address 198.18.0.1 255.255.255.0 no ip proxy-arp ip nat outside Add a dynamic NAT rule to broadcast the address of the computer from the LAN (192.168.20.5) to the internal global address 198.18.0.5 when accessing the computer outside (Wireshark). Add a static PAT rule to publish the TCP port 3389 (RDP) of the computer from the LAN under the global address 198.18.0.2.
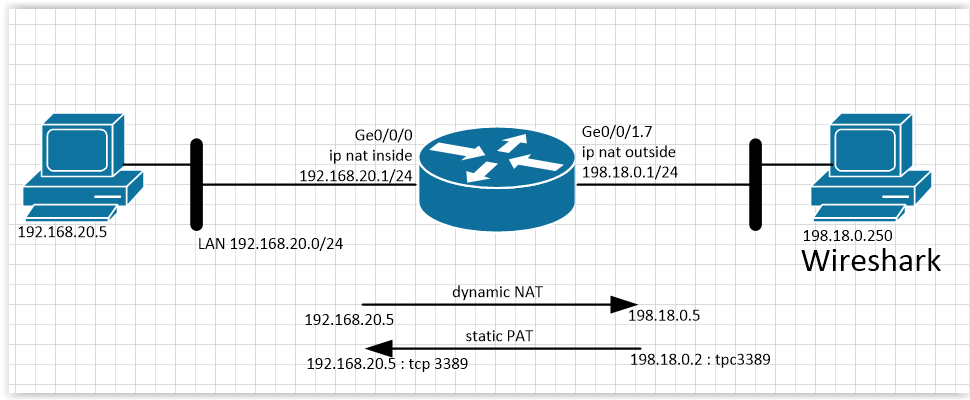
ip access-list standard acl-test-arp permit 192.168.20.5 ip nat pool test-pool 198.18.0.5 198.18.0.5 netmask 255.255.255.252 ip nat inside source list acl-test-arp pool test-pool overload ip nat inside source static tcp 192.168.20.5 3389 198.18.0.2 3389 extendable Let's look at the ARP table on the router:
cisco#sh arp Protocol Address Age (min) Hardware Addr Type Interface . . . Internet 198.18.0.1 - d8b1.902e.e741 ARPA GigabitEthernet0/0/1.7 Internet 198.18.0.2 - d8b1.902e.e741 ARPA GigabitEthernet0/0/1.7 Internet 198.18.0.5 - d8b1.902e.e741 ARPA GigabitEthernet0/0/1.7 . . . We see that the ARP table contains static entries for both the external interface of the router (198.18.0.1) and internal global addresses from the rules of dynamic and static NAT.
Make a clear arp-cache on the router and see in Wireshark which Gratuitous ARP notifications will be sent from the external interface:
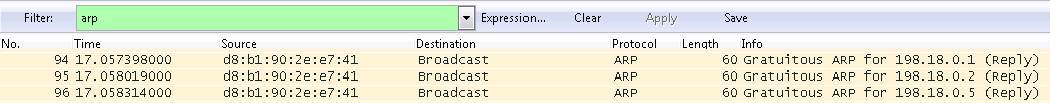
As you can see, the router indicated its readiness to maintain the interface address, the address from the dynamic NAT rule, and the address from the static NAT rule.
And now let's imagine a situation where the provider expands the pool of public addresses issued to the client at the expense of another subnet. Suppose, in addition to the IP subnet 198.18.0.0/24 on the external interface of the router, we receive from the provider a new pool 198.18.99.0/24 and want to publish our internal services under the new IP addresses. For clarity, I will give the scheme with the provider:
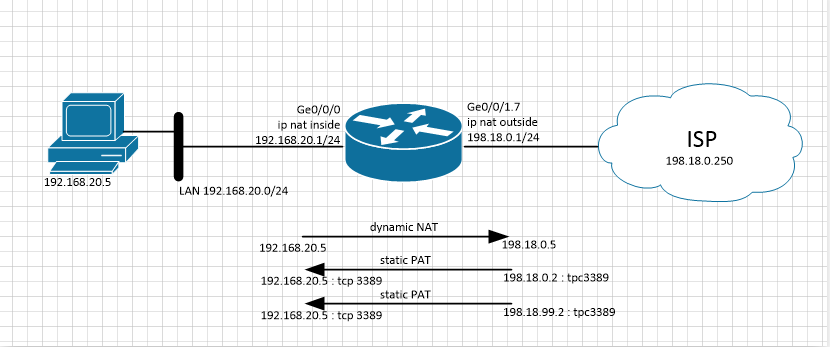
Add a static PAT rule for publishing TCP port 3389 (RDP) of a computer from the LAN under the new global address 198.18.99.2:
ip nat inside source static tcp 192.168.20.5 3389 198.18.99.2 3389 extendable If you look at the router's ARP table again with the show arp command, you will see that the static entry for the IP address 198.18.99.2 has not been added.
To be able to send ARP requests to the new network 198.18.99.0/24 from the Wireshark computer, we will expand the mask of its network settings to 255.255.0.0 (/ 16). Let me remind you that for our example, Wireshark acts as an ISP’s router.
After entering the clear arp-cache, the sniffer still shows Gratuitous ARP for only three IP addresses: 198.18.0.1, 198.18.0.2, 198.18.0.5. For the new address 198.18.99.2 Gratuitous ARP does not work. Let's try to open tcp-port 3389 of the address 198.18.99.2 and at the same time look at the sniffer:
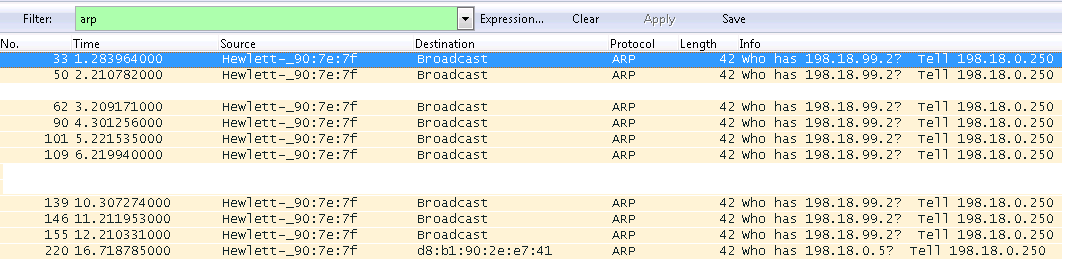
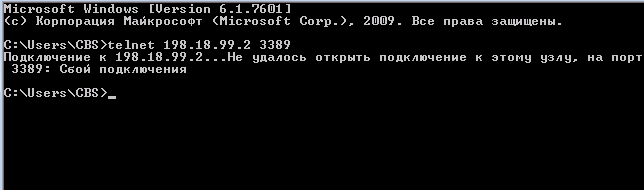
Failure. Check the ARP table:
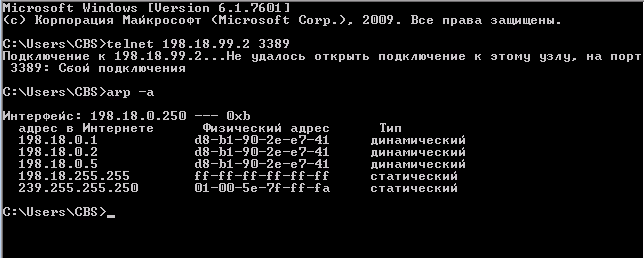
An ARP entry for the new IP address 198.18.99.2 did not appear. The reason is that the new IP address 198.18.99.2 is on an IP subnet different from the interface address of the router. How can we make the new pool of IP addresses issued by the provider work? There are four options:
- Ask the provider to register static ARP entries for each IP address in the new range. This is not very convenient if a wide range is issued as in our example.
- Ask the provider to register a static route. Often, in order to issue an additional range of white IP-addresses, the provider writes the secondary IP-address on the interface of its equipment. Instead, we can ask the provider to register a static route to the new IP subnet via the IP address of the external interface of the router. In this case, the equipment provider will know that the new subnet is available through the IP address of the router's interface, and the router, in turn, will respond to ARP requests sent to its own interface.
- Register the secondary IP address from the new range on the external interface of the router. In this case, any IP address of the new range will belong to the same subnet as the IP address (albeit secondary) of the router interface. The router will automatically add static entries to its ARP table, send Gratuitous ARP and respond to ARP requests.
- Use the Proxy Arp mechanism on the router. On this option, we dwell in more detail.
Proxy ARP on Cisco routers
Proxy ARP functionality allows the router to respond to ARP requests when the following three conditions are met:
- The target IP address of the ARP request is on an IP subnet other than the IP subnet in which the ARP request was received;
- The router has one or more routes to the target IP address of the ARP request;
- Routes to the target IP address of the ARP request indicate an outgoing interface other than the interface to which the ARP request was received.
By default, Proxy ARP is enabled on all interfaces of the router. However, the use of the Proxy ARP mechanism has several drawbacks. First of all, Proxy ARP introduces a potential vulnerability to Man-in-the-middle attacks, when an attacker gains the ability to intercept network traffic. Therefore, it is recommended to disable Proxy ARP on at least the interfaces to which external networks are connected.
Configure Proxy ARP on the router interface:
interface GigabitEthernet0/0/1.7 ip proxy-arp You can globally disable Proxy ARP on all interfaces of the router:
ip arp proxy disable This setting takes precedence over Proxy ARP settings applied on interfaces.
In addition to the ip proxy arp command, there is a ip local-proxy-arp command in the interface settings. This command only works when ip proxy arp is enabled on the interface and allows the router to respond to ARP requests, even if the target IP address is on the same IP subnet from which the ARP request came. Setup Example:
no ip arp proxy disable interface GigabitEthernet0/0/1.7 ip proxy-arp ip local-proxy-arp This setting can be useful if we want traffic within one broadcast domain to go through our router's interface. This task can be implemented using the Protected port (PVLAN edge) settings on the L2 switch ( switchport protected ).
Enabling Proxy ARP on the external interface of the router will solve the problem with the new pool of addresses issued by the provider. Let's try to open tcp-port 3389 of the address 198.18.99.2 after enabling Proxy ARP on the interface of the router and at the same time look at the sniffer:
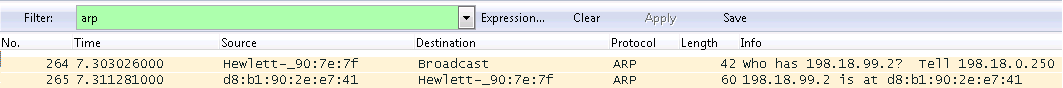
Success. The router responds to the ARP request and the port opens. Thus, the Proxy ARP functionality can also be used when address translation to a new pool is needed.
Results
I will try to summarize the main points of the first part of the article:
- Cisco networking equipment adds an ARP record of a new remote device to the ARP table immediately after an ARP request arrives from the remote device. This behavior reduces ARP traffic on the network.
- The Cisco router will respond to ARP requests to the internal global IP address of the NAT rule if this IP address belongs to the same IP subnet as the router interface. Additional settings for ARP are not required.
- If the inside global IP address of the router's NAT rule does not belong to the IP subnet of the router interface, additional configuration is required. There are four options:
- Static ARP-records on external equipment;
- Static route on external equipment;
- Configuring secondary IP addresses on the router interface;
- Using Proxy ARP.
The first and second options involve changing the settings on the “alien” network equipment and may not always be acceptable.
The third option is the most preferred.
The fourth option can be used, but it opens a vulnerability in terms of network security.
- Static ARP-records on external equipment;
- Proxy ARP functionality is enabled on the default router interfaces. It is recommended to disable Proxy ARP at least on interfaces connected to Internet service providers.
Source: https://habr.com/ru/post/276863/
All Articles