Security Week 05: difficult numbers in socat, Virustotal checks the BIOS for bookmarks, the secret life of WiFi modules
 Three of the most popular news of this week are somehow related to the topic of security intelligence - another poorly translated, and relatively recent term in the information security industry. Intelligence is the sum of knowledge that somehow helps protect users and companies from cyber threats. The quotes from the book by Evgeny Kaspersky, which I quote at the end of each issue, reflect the knowledge requirements for the beginning of the 90s of the last century: then one expert could have in his head everything necessary for protection against cyber threats. Information on typical methods of infection and distribution, methods for determining the type of threat and treatment. These were good times, but they are long gone. To understand the threats of modern, requires a huge range of knowledge - from the Lua programming language to the dialects of Chinese, from the features of hard drive firmware to data encryption theory.
Three of the most popular news of this week are somehow related to the topic of security intelligence - another poorly translated, and relatively recent term in the information security industry. Intelligence is the sum of knowledge that somehow helps protect users and companies from cyber threats. The quotes from the book by Evgeny Kaspersky, which I quote at the end of each issue, reflect the knowledge requirements for the beginning of the 90s of the last century: then one expert could have in his head everything necessary for protection against cyber threats. Information on typical methods of infection and distribution, methods for determining the type of threat and treatment. These were good times, but they are long gone. To understand the threats of modern, requires a huge range of knowledge - from the Lua programming language to the dialects of Chinese, from the features of hard drive firmware to data encryption theory.Moreover, there is no universal and effective expertise for all. Each company has a unique set of IT infrastructure elements, with its own vulnerable points and potential points of entry. Naturally, there is no single, relevant for all recipe protection. Good corporate security requires knowledge of cyber threats in general, and how they can be applied to a specific situation. If it is simpler, you need to know where the protection will be broken (or already broken!), And the further, the more expensive this knowledge will be evaluated. Finally, there are so many threats and types of attacks that it is also becoming more difficult to analyze them all by hand. It is necessary to build
All editions are available by tag .
Socat's Unix utility used a vulnerable implementation of the Diffie-Hellman algorithm to create secure connections, suspect an error or even malicious intent of the developer
News
')
Socat is an open source Unix utility that is used to transfer data between two different channels. With its help, for example, you can analyze network traffic by redirecting it to a file or forwarding tunnels between networks. Since the utility interacts with the network, it also supports secure data transfer, and therefore implements the appropriate connection setup algorithms. In particular, the Diffie-Hellman algorithm that has appeared on the pages of my digest more than once allows you to safely exchange keys and uses some basic prime number of long length for complex calculations (in this case, 1024 bits).
Well, firstly, it has already been proved earlier that 1024-bit prime numbers are already unsafe in the context of this algorithm, although hacking something using this “vulnerability” still takes a lot of time and is very expensive. Secondly, the news is that the number used in socat was not easy. In a sense, it goes into factors. You can evaluate the consequences of such an error by reading, for example, this remarkable discussion on Stackexchange. In short - to crack the encrypted data exchange using the weakened Diffie-Hellman algoritm becomes even easier, although all the same it is a question of rather complex and lengthy calculations.

Since the utility is open source, it was easy to trace the appearance of the error to a specific author. It turned out to be a certain Zhiang Wang, at the time of adding the vulnerable code, an Oracle employee who, in general, was not trying to maintain anonymity. Was there a reason to hide? Well, in general, the introduction of a deliberate vulnerability in the program code can be interpreted as an attempt to plant a backdoor. In an interview with Threatpost Maintainer socat Gerhard Rieger said that he still considers this a mistake. There are two reasons. Firstly, there was no attempt to cover the tracks, and secondly, if someone wanted to implant a backdoor, he would certainly use a less clumsy method. On the other hand, it is difficult to check (by calculations) whether a prime number is really simple. The patch in the OpenSSL library itself last week, by the way, solved a similar problem - there used “unreliable” prime numbers for Diffie-Hellman to work, which also made the attack theoretically possible.
In general, this news, like the previous ones, can be interpreted as a game of preemption by software developers and researchers of encryption algorithms: vulnerabilities are closed, the practical use of which is unlikely. This aspect of the situation is interesting: we are talking about a bug that is very difficult to detect if you don’t know exactly where to dig. Perhaps this is why not the most dangerous vulnerability in socat has received such attention - the news became the most popular on Threatpost for the week. Encryption generally dramatically raises the bar for expertise required for security audits. The problem is that such tasks of increased complexity will sooner or later begin to appear in other areas of the national economy. In the meantime, everything is not bad: the bug was closed, replacing the basic prime number with a proven and reliable 2048-bit one. But the potential vulnerability in socat was hidden in the code for exactly a year.
The microcode check service has appeared on VirusTotal.
News
VirusTotal service allows you to scan a suspicious file with antivirus engines from different manufacturers. It quite often becomes the last argument in disputes about the effectiveness of security software, and more often the results of such a “detector” are interpreted freely and not quite correctly. The service, which has been owned by Google since 2012, is also a useful tool for security researchers, giving them additional hints about the activity of malicious campaigns - for example, information about when and where a malicious element was downloaded.
The new service is on the side of the standard model of VirusTotal. It analyzes microcode, including BIOS firmware for computers and laptops, and issues a verdict on a number of parameters. Among them: analysis of the lines contained in the firmware to determine the target vendors (for which devices the firmware is intended), extract certificates, extract the Portable Executable code — that is, programs, for example, stored in the BIOS, but intended to run on Windows. The latter, in theory, are of particular interest - this is how you can safely hide the malicious code in the BIOS, run it on the installed system for some purpose with elevated rights, and reinstall it if deleted.
Attention to the firmware was attracted by the study of The Equation campaign published by the Laboratory last year. Including were found means of modifying firmware hard drives, allowing to restore unauthorized access to the attacked system, even in the case of complete deletion of data. In itself, such a discovery made it clear that with sufficient investment in development, you can create an attack model that is extremely difficult to detect and stop. In general, the BIOS and firmware of individual components in modern computers are represented to most in the form of a black hole, in which it is unclear what happens. And much can happen there. Another example, this time about the BIOS - is the methods of the anti-theft complex Absolute Computrace .
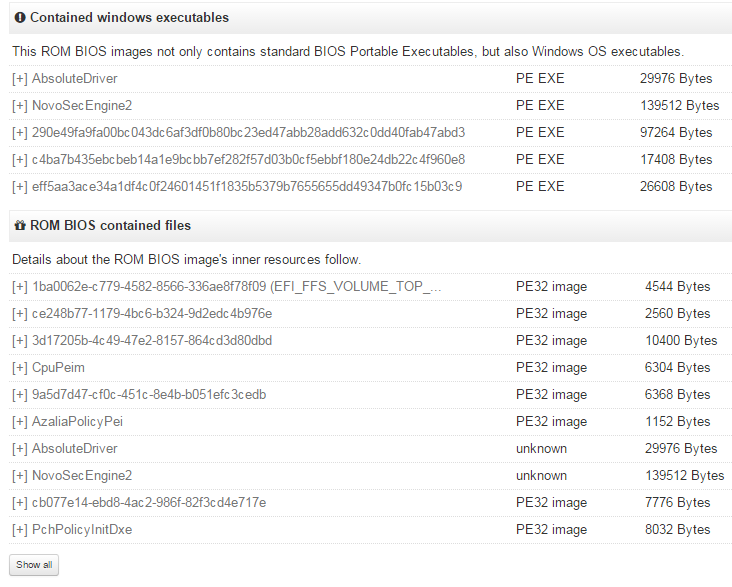
In general, it is necessary to analyze, and now VirusTotal provides tools for this, although it is very basic. But the point here is not only in the quality of tools, but also in the amount of information for research. The more often they use this functionality, the more different BIOS and other firmware will be collected, the easier it will be to carry out a comparative analysis. The higher the likelihood that somewhere will be found a new backdoor, and at the same time do not have to disassemble each firmware by hand. Actually, this is a good example of the development of information security, when experts base their research on the basis of a large amount of previously collected data. An example of parsing the firmware is here .
Android closes WiFi driver vulnerability
News Security bulletin .
The February patchset for Android, which is now available to owners of Nexus devices and sometime to everyone else, closes a vulnerability in WiFi drivers for Broadcom modules. The potential exploitation scenario for this vulnerability looks terrible. You connect to a public WiFi network, in the subway, in the office or in a hotel. An attacker on the same network sends a specially crafted network packet to your device and gets full access to the smartphone. Fortunately, the scenario is really theoretical - Google claims that no real attacks were noticed.
Another vulnerability is closed, in the infamous Mediaserver component, which previously found a Stagefright hole. As I said earlier , if there are many vulnerabilities in the software, this does not necessarily qualify the software or the platform as “insecure”. On one condition - if the vulnerabilities are closed. The Android ecosystem is studied as thoroughly as possible by everyone - both white hat researchers and crime. The introduction of monthly security updates last year was a positive change, but questions about the fragmentation of Android, the inaccessibility of patches for a large number of devices still remain. This means that a protection strategy, for example, mobile phones in a corporate network, must a priori assume that many devices are vulnerable and will remain so for a long time.
What else happened:
Oracle will no longer develop a Java plugin for browsers. The expected solution, as browser developers have long been trying with all their might to not allow such plug-ins to themselves. Google pioneered by blocking the default NPAPI interface, that is, by effectively prohibiting the work of such plug-ins as Java and Silverlight.
Found another pack of vulnerabilities in "smart" children's toys.
Anonymous hackers stole 250 gigabytes of data from NASA. Or they didn’t steal it: NASA itself claims that the “leak” was posted on the company's website for public access, and there was no attack, but unbridled PR.
 Antiquities:
Antiquities:"Ninja-1376"
Very dangerous resident virus. It infects .COM and .EXE files other than COMMAND.COM and AIDSTEST.EXE. When infected before and after the virus adds random blocks up to 255 bytes in length. Periodically kills files: writes a program to their beginning, which, when started, decodes and displays the text: "Mutant Ninja Version 2.0 Copyright © 1990,91 Virus & Worm Software". In 1992, on the 13th at 13.00, erases the FAT drive C :. It does not work correctly with int 24h. It contains the lines: "COMMAND.COM", "AIDSTEST.EXE", ".COM" and ".EXE". Intercepts int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 77.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/276629/
All Articles