Researchers have found many critical vulnerabilities in payment protocols
German information security researchers Karsten Nohl, dexter and Fabian Braunlein at the Chaos Computing Club conference told about the critical vulnerabilities of payment protocols that could be used by attackers to steal data from customers' bank cards and money from sellers.
What is the problem
Users should be able to believe payment systems: payment terminals can now be found everywhere, and payment by bank cards is becoming more and more popular, and in some countries the volume of cashless transactions exceeds cash payments.
')
However, most of this payment infrastructure relies on proprietary protocols from the 90s of the last century - in practice this means that there are a large number of security holes. Payment terminals and processors are increasingly becoming the target of intruders.
Theft of financial data
Using the vulnerabilities of payment protocols, criminals can access information from a large number of bank cards and then select PIN codes for them.
For example, in Germany, the main communication protocol for communication between payment terminals and cash registers is ZVT. It simply allows hackers to read information from bank cards, gaining access to the local store network.
Worse, the protocol implements a mechanism for remotely reading card PIN codes. It is protected by a cryptographic signature (MAC). However, the symmetric encryption key is stored in the so-called Hardware Security Modules (HSM), some of which are subject to a simple timing attack — this allows attackers to gain access to the key.
The important point is that the same key is used in multiple payment terminals, which opens up wide opportunities for attackers to commit attacks (and contradicts the basic principles of designing secure systems).
Compromising Seller Accounts
In addition, the lack of security for financial protocols opens up opportunities for attackers to steal money from merchant accounts.
Payment terminals communicate with special payment processors (which, in turn, interact with banks) via the Internet, using the ISO 8583 standard. There are various “dialects” of this standard - Poseidon is popular in Germany. And it also contains critical vulnerabilities.
In particular, one of the authentication errors is described as follows. The terminal uses a secret key to execute a cryptographic authentication protocol. So far, all is well. But then we again see the repetition of the error ZVT - many terminals store the same key. Replacing a single number (Terminal ID) in any particular terminal allows access to the merchant's account to which this terminal is linked. Worse, the Terminal ID is printed on every check - this makes it even easier to carry out the attack.
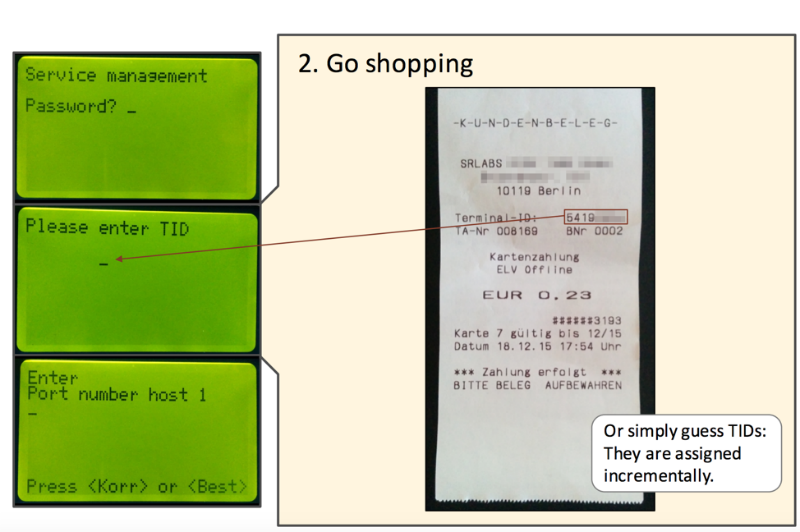
As a result, attackers can make a return (refund) or pay promotional codes for cellular communication (top-up codes).
A detailed description of the attacks presented can be found in this PDF .
Not so bad
The problems of security of payment protocols discovered by German researchers mainly concern technologies used in Germany and are not so common in other countries.
Nevertheless, Russian information security researchers also published information about serious vulnerabilities in the systems of banks operating in our country and possible attacks on ATMs and payment terminals themselves.
Source: https://habr.com/ru/post/276219/
All Articles