VirusTotal has implemented additional indicators for firmware images
The developers of the well-known VirusTotal antivirus online scanning service have implemented special malware detection mechanisms that may be located in the computer’s firmware (firmware). Now the reports on scanning such files contain various information about the potential manufacturer of the firmware, the necessary identifiers of the executable PE files that are stored in the firmware image, as well as information on the digital certificates used to sign these files.

A well-known example of a malicious program for UEFI firmware is the Hacking Team rootkit discovered last year. Successful compromise of the OS at this level is a very difficult task for attackers, but it allows you to gain complete control over the process of launching the OS at an early stage. Below is the information that the service provides for the images of the firmware. With its help, you can set the probability of compromising the firmware.

Fig. Information about the firmware image of one of the scan reports.
')
The new file analysis tool performs the following functions.
Malicious or illegitimate code can be placed exactly in PE-files, which are located in the firmware image. The analysis tool retrieves them from there and provides the client with the service information about their potential harmfulness (scan rating). The best case from the point of view of security is the one in which all files placed in the image are digitally signed and there is no detection for them (a clean file). Below is a variant in which one of the detected image files is similar to a malicious program (14/57 detection rate is present).
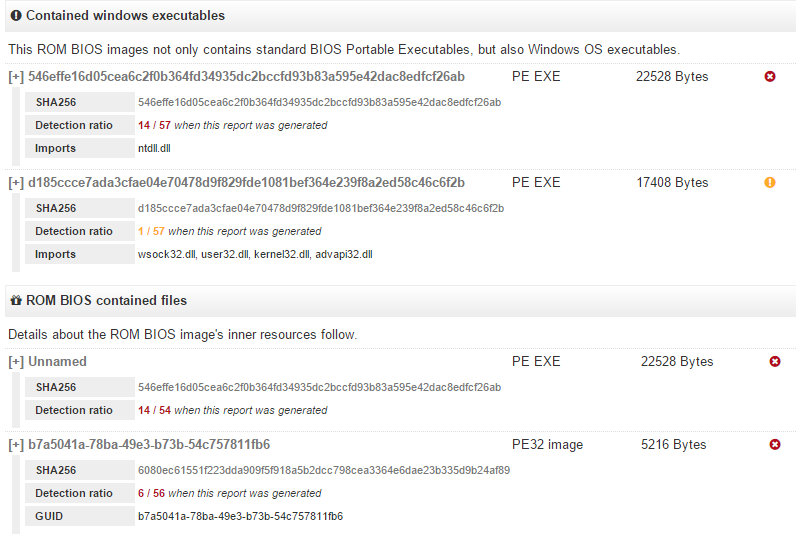
Fig. The result of scanning an image file that contains a PE file with a high detection rate from antivirus products, which may indicate that the firmware has been compromised. The service also scans the resource data of PE files for the presence of suspicious data there.
More information about the new feature here .

A well-known example of a malicious program for UEFI firmware is the Hacking Team rootkit discovered last year. Successful compromise of the OS at this level is a very difficult task for attackers, but it allows you to gain complete control over the process of launching the OS at an early stage. Below is the information that the service provides for the images of the firmware. With its help, you can set the probability of compromising the firmware.

Fig. Information about the firmware image of one of the scan reports.
')
The new file analysis tool performs the following functions.
- Allows you to identify the firmware of Apple Mac computers.
- Detects a possible manufacturer of the device and firmware based on the analysis of the lines in the image.
- Extracts from the image information about digital certificates that were used to sign the firmware itself and PE files from it.
- Allows you to identify the device class based on the analysis of the PCI code class.
- Retrieves data from ACPI system tables.
- Gets information about the NVAR variable.
- Extracts the ROM data and the code stored there, decompiling the point code I enter
- Extracts PE files from the image from the image and tries to find other PE files inside them - Windows applications.
- Gets information about SMBIOS.
Malicious or illegitimate code can be placed exactly in PE-files, which are located in the firmware image. The analysis tool retrieves them from there and provides the client with the service information about their potential harmfulness (scan rating). The best case from the point of view of security is the one in which all files placed in the image are digitally signed and there is no detection for them (a clean file). Below is a variant in which one of the detected image files is similar to a malicious program (14/57 detection rate is present).

Fig. The result of scanning an image file that contains a PE file with a high detection rate from antivirus products, which may indicate that the firmware has been compromised. The service also scans the resource data of PE files for the presence of suspicious data there.
More information about the new feature here .
Source: https://habr.com/ru/post/276065/
All Articles