Processing a temporary or permanent replacement of a 1C: Enterprise 8.2-8.3 authentication password
Simple processing on managed and common forms for platform 8.2-8.3, which allows you to change the password of 1C: Enterprise authentication and return it. It will be useful to administrators, programmers associated with 1C.
Recently I ran into a problem that required a simple solution. Actually, the problem can fit in one question: how to help the user without knowing or resetting his password?
In many offices, to reproduce the error, administrators, programmers and other technical specialists used 1C: Enterprise authentication. That is, the user "complained" about the error, experts came by and tried to reproduce the error. Received an error and corrected it in the code.
')
With the development of the mobile platform and mobile clients, 1C: Enterprise authentication becomes “busy” by the user, since it is synchronized through it. That is, not every user will want to disclose their passwords or use the password that he was “assigned”. Our office is also more and more tied to mobile clients. This is where the question mentioned earlier arose.
I rummaged through the Internet, found a bunch of descriptions how to break passwords in a file database or in server versions.
In the case of the file version, you do not need any rights to install the program for viewing the * .1CD database files and change the passwords in the V8USERS table. It is worth noting that passwords are not stored there in pure form, but the password hash is stored. Actually, the hash of an unknown password is changed to the hash of a known password. In the case of server databases, you need to know the database administrator login and there it is no longer a tricky thing to change the password. But how to explain to the user an authentication error after such hacks? And why such difficulties?
I found the same processing, which selects passwords while requiring the same rights as my processing. Well, it picks up a password of 123 or even 123456 is fast, but what if the password is real? She writes about 90 days will pick up. This is not what gate! This situation may come out while picking up the password, the user has changed the password. Yes, and not once can change.
In general, I suggest a small processing that changes the hash of an unknown password to the hash of the desired password, and then replaces it back. It works in managed forms as well as under regular forms. It can be built in through "additional processing and reports", the procedure is added to the object module with a description of processing.

Well, or you can embed it through “Configuration Extensions” - a very useful feature, at the moment it allows you to add processing and reports to the configuration without removing it from support. That is, the typical configuration remains typical even when adding processing.
Principle of operation:
According to the user get the password hash.
// User directory reference Users
UserID = Users of the Information Base. Find a Unique Identifier (User. User Identifier IB);
// Saved Password Value Stores Password Hash
User Password = UserID.SavedPassword Value;
// Name stores user login
LoginUser = UserID.Name;
Enter the desired password and get its hash.

Change the user hash to the desired password hash.
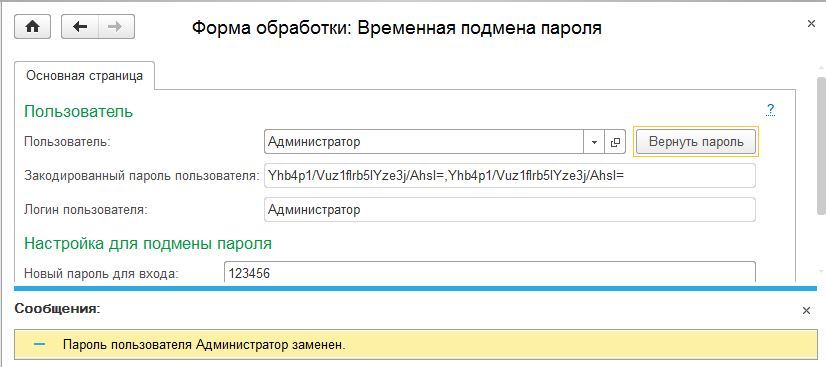
Log in to the system with a new password. We change everything back.

Link to download processing
Recently I ran into a problem that required a simple solution. Actually, the problem can fit in one question: how to help the user without knowing or resetting his password?
In many offices, to reproduce the error, administrators, programmers and other technical specialists used 1C: Enterprise authentication. That is, the user "complained" about the error, experts came by and tried to reproduce the error. Received an error and corrected it in the code.
')
With the development of the mobile platform and mobile clients, 1C: Enterprise authentication becomes “busy” by the user, since it is synchronized through it. That is, not every user will want to disclose their passwords or use the password that he was “assigned”. Our office is also more and more tied to mobile clients. This is where the question mentioned earlier arose.
I rummaged through the Internet, found a bunch of descriptions how to break passwords in a file database or in server versions.
In the case of the file version, you do not need any rights to install the program for viewing the * .1CD database files and change the passwords in the V8USERS table. It is worth noting that passwords are not stored there in pure form, but the password hash is stored. Actually, the hash of an unknown password is changed to the hash of a known password. In the case of server databases, you need to know the database administrator login and there it is no longer a tricky thing to change the password. But how to explain to the user an authentication error after such hacks? And why such difficulties?
I found the same processing, which selects passwords while requiring the same rights as my processing. Well, it picks up a password of 123 or even 123456 is fast, but what if the password is real? She writes about 90 days will pick up. This is not what gate! This situation may come out while picking up the password, the user has changed the password. Yes, and not once can change.
In general, I suggest a small processing that changes the hash of an unknown password to the hash of the desired password, and then replaces it back. It works in managed forms as well as under regular forms. It can be built in through "additional processing and reports", the procedure is added to the object module with a description of processing.
Well, or you can embed it through “Configuration Extensions” - a very useful feature, at the moment it allows you to add processing and reports to the configuration without removing it from support. That is, the typical configuration remains typical even when adding processing.
Principle of operation:
According to the user get the password hash.
// User directory reference Users
UserID = Users of the Information Base. Find a Unique Identifier (User. User Identifier IB);
// Saved Password Value Stores Password Hash
User Password = UserID.SavedPassword Value;
// Name stores user login
LoginUser = UserID.Name;
Enter the desired password and get its hash.
Change the user hash to the desired password hash.
Log in to the system with a new password. We change everything back.
Link to download processing
Source: https://habr.com/ru/post/275999/
All Articles