Security Week 03 or patch week: Linux, OpenSSH, Cisco, Yahoo Mail, Apple
 In information security, there are periods when no special discoveries occur. Instead, the routine work of closing (or not closing) previously discovered vulnerabilities is sufficient. This week is just such a period: the most popular news is almost entirely devoted to patches. Well, this is also not bad, especially since the approach of different companies to patches is very different, and the perception of this topic is sometimes, well, somewhat strange.
In information security, there are periods when no special discoveries occur. Instead, the routine work of closing (or not closing) previously discovered vulnerabilities is sufficient. This week is just such a period: the most popular news is almost entirely devoted to patches. Well, this is also not bad, especially since the approach of different companies to patches is very different, and the perception of this topic is sometimes, well, somewhat strange.A simple example: at the end of last year, Apple (specifically Mac OS X and iOS) counted a record number of vulnerabilities in the software. Well, that is, we looked at the CVE database, and found that the most vulnerabilities were discovered in Mac OS X, iOS, and Adobe Flash. Some media even called the Apple platform "the most dangerous", which, of course, is not true. After all, the connection between “discovered vulnerability” and “users in danger” is practically not seen. On the contrary, in the context of the CVE database, “discovered” usually means “closed”. And this is, in general, good news.
Perhaps the point here is that many have jumped at the simple and understandable rating of holes, with absolute figures that give a false sense of an understanding of the landscape of threats. A good attempt to "simplify" the topic, but no, this method does not work with security. Therefore, look at the patches of this week more closely. All issues of digest - here .
Vulnerability in the Linux kernel allows you to get root-privileges
News Research company Perception Point.
')
A serious vulnerability in the Linux kernel has been discovered by experts from Perception Point, and affects all versions of the kernel from 3.8, that is, from 2012 onwards. Chances are high that your Linux-based computer is also susceptible, and at this point, Windows and Mac OS X users should breathe a sigh of relief, but don’t be in a hurry. Experience shows that Linux is found in the most unexpected places: well, of course, the company's website can work on Linux, your phone can work on Linux, and your home or SoHo router almost certainly works on Linux. Actually, this is what happened: in addition to PCs and servers, all Android smartphones are vulnerable from the KitKat version, that is, almost everything.
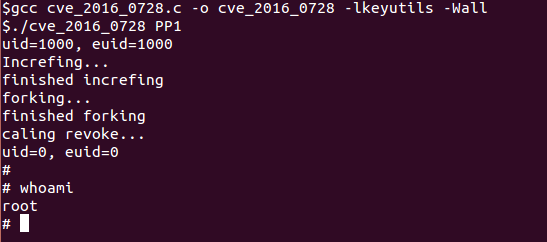
The process of exploiting a vulnerability will seem rather complicated to an incompetent, although in reality it is quite straightforward and reliable: we run the code, and in half an hour we get access with unlimited rights. Half an hour is required for the cunning process of accessing the corectl kernel function, buffer overflow, and so on. To get root privileges, you must already have access to the system: in the case of Android, this can be a malicious application, similarly for a desktop running Linux, and for servers everything is somewhat more complicated. For the main Linux-based distributions, patches have already been released (the problem is solved by adding one line to the code), but Android, as always, is much, much more difficult.
Vulnerability in OpenSSH could lead to theft of private keys
News Security Advisory .
Have you updated the kernel? Update the OpenSSH package at the same time, as its developers hint to us. In full accordance with the mantra “this is not a bug, this is a feature”, SSH clients of versions 5.4–7.1 were affected. In version 5.4, the “UseRoaming” function was added, allowing to restore an interrupted connection to the server. Interestingly, in the server part of OpenSSH the same function was never implemented, but a vulnerability was discovered in the client. The hole leads to data leakage from RAM: when connected to a specially prepared server, it is possible that the client’s private keys may even leak. In the future, the same keys can be used by an attacker to penetrate other Linux systems.
In general, a serious enough vulnerability, but, as in the case of a hole in the Linux kernel, with many reservations. For example, such a scenario does not allow stealing keys by organizing a man-in-the-middle attack. The client must connect to the server of the attackers, or to the compromised own server. The problem is solved simply - either roll up the update, or disable the most useless option UseRoaming in the client configuration. Why it was included at all by default in the absence of support in the server part is not very clear.
Apple closed the gatekeeper vulnerability twice and not both times
News
This story well shows how something can go wrong in the relationship between software developers and researchers. Back in June of last year, researcher Patrick Wardle told Apple (privately) about the vulnerability in the Gatekeeper function. Gatekeeper is the very thing in modern versions of Mac OS X that prevents you from simply taking and running a program downloaded from the network: it must be signed with the appropriate certificate. The function is aimed at improving security - there’s nothing to say that any indecency from the Internet is set up, use the software from the store. In general, this is true: this approach in iOS has made the Apple mobile ecosystem quite secure.
So, the researcher found out that the check when launching the downloaded software is too simple: in fact, only the executable file that the user clicks is checked. If it is signed with a certificate, it is executed. If this program starts another from the same location, then the second program is no longer checked. That is, the attack vector is quite understandable: we sign the code (with the help of Apple, or with our own certificate - this option is supported for companies), we plan to launch another file in it, but in it we are already doing everything that pleases.

According to Wardl, all that Apple did was add to the blacklist the files that the researcher himself sent as Proof of Concept. Naturally, such a patch can be “bypassed” in about 30 seconds, which was done. In December, Apple released a new patch, but used the exact same tactics. If it was really so, then it turns out that the vendor extinguished the fire with the help of a religious procession. But this is according to the researcher. Apple itself, in its traditional manner, does not comment on the situation. In general, there are many situations when a vendor believes that the problem has been solved, but an independent expert does not agree - but there will be more. What to do with this is not very clear, but the solution is clearly in a more open exchange of information about vulnerabilities and patches to them. I'm not even talking about the disclosure of the code of patches, but about the interaction of vendors with the community. In general, the fact that the developer of Mac OS X is not always good at it.
What else happened:
Cisco patches its own software, including software for Aironet 1800 series WiFi controllers - a password and default account were discovered there.
Yahoo! Webmail Found out ! Dangerous! Vulnerability! (excuse me). Vulnerability of the XSS type allows to manipulate someone else's email account in a wide range, if you manage to lure the user to a site with malicious JavaScript, and if he logged in to the mail in the same browser. Finnish researcher Jouko Punnönen received for his find 10 thousand dollars for the bug bounty program. But his proof of concept:
 Antiquities:
Antiquities:"Seat-1614"
Resident non-dangerous virus. It affects .COM and .EXE files (except COMMAND.COM) when they are launched. EXE-files are affected by the standard, COM-files - at the beginning. After 15 successful defeats of files, he draws a bare bottom on the screen, which, when you press any key, produces corresponding sounds (bottom). Crawls int 9, int 1Ch, int 21h. It contains the text: "VVF3.4".
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 82.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/275693/
All Articles