A dangerous 0day vulnerability has been discovered in the Linux kernel.
Specialists from the Israeli security company Perception Point reported finding a dangerous 0day vulnerability in the Linux kernel with the identifier CVE-2016-0728. The vulnerability is a type of Local Privilege Escalation (LPE) and covers all versions and modifications of Linux, which use the kernel version 3.8 and higher. As it is not difficult to guess, with the help of attackers can raise their privileges in the system to the maximum level of root. An exploit can be used in the system after the attackers have remote access to it and launched it for execution. It can also be used by malware to gain maximum privileges in the system.

On the Linux kernel is based and one of the most popular to date mobile OS - Android. Thus, those versions of Android that use the Linux kernel of these versions are also affected by this vulnerability. This applies to Android KitKat versions (4.4-4.4.4) and above.
')
Vulnerability CVE-2016-0728 is present in the Linux kernel subsystem called keyring, which allows applications and system components of the OS to work safely with cryptographic data stored in memory, such as encryption keys. More precisely, the vulnerability is located in the kernel function join_session_keyring , which the application can call using the keyctl API, specifying the constant KEYCTL_JOIN_SESSION_KEYRING to it. After connecting to the keyring object once again from the same process, the function increments the reference count for it, and then forgets to reduce it before leaving the reference leak. Thus, by calling the keyctl function with the identifier KEYCTL_JOIN_SESSION_KEYRING for an already created keyring object, the reference count for it will constantly grow.
The exploitation of the vulnerability is achieved by increasing the reference count (the keyring object's usage field) to the maximum possible value so as to signal to the kernel that it can already be deleted. Since the field itself is interpreted as a signed integer (int), for this it is necessary to set its most significant bit. After the kernel frees up memory for the object, and the pointer to it remains for the application, the exploit allocates another object to the same address, fills its contents with the required pointer, and then triggers its call through one of the pointers in the keyring object, which will lead to the execution of the code at the address specified by the exploit.
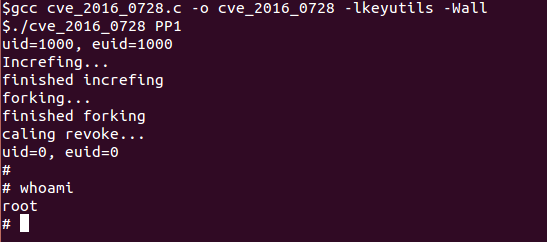
Fig. Successful PoC result for this vulnerability (Perception Point data).
According to estimates, Perception Point affects tens of millions of PCs and servers running Linux with a vulnerable kernel, as well as 66% of all Android devices. The company indicates that the vulnerability has been present in the core since 2012, that is, for about four years. Protective technologies such as SMEP and SMAP that prevent the kernel mode code (with maximum privileges from the microprocessor's point of view) from accessing the virtual memory pages of the user mode will not allow the exploit code to work out as needed.
We recommend that users install the appropriate patch for the OS immediately after it is released.

On the Linux kernel is based and one of the most popular to date mobile OS - Android. Thus, those versions of Android that use the Linux kernel of these versions are also affected by this vulnerability. This applies to Android KitKat versions (4.4-4.4.4) and above.
')
Vulnerability CVE-2016-0728 is present in the Linux kernel subsystem called keyring, which allows applications and system components of the OS to work safely with cryptographic data stored in memory, such as encryption keys. More precisely, the vulnerability is located in the kernel function join_session_keyring , which the application can call using the keyctl API, specifying the constant KEYCTL_JOIN_SESSION_KEYRING to it. After connecting to the keyring object once again from the same process, the function increments the reference count for it, and then forgets to reduce it before leaving the reference leak. Thus, by calling the keyctl function with the identifier KEYCTL_JOIN_SESSION_KEYRING for an already created keyring object, the reference count for it will constantly grow.
The exploitation of the vulnerability is achieved by increasing the reference count (the keyring object's usage field) to the maximum possible value so as to signal to the kernel that it can already be deleted. Since the field itself is interpreted as a signed integer (int), for this it is necessary to set its most significant bit. After the kernel frees up memory for the object, and the pointer to it remains for the application, the exploit allocates another object to the same address, fills its contents with the required pointer, and then triggers its call through one of the pointers in the keyring object, which will lead to the execution of the code at the address specified by the exploit.

Fig. Successful PoC result for this vulnerability (Perception Point data).
According to estimates, Perception Point affects tens of millions of PCs and servers running Linux with a vulnerable kernel, as well as 66% of all Android devices. The company indicates that the vulnerability has been present in the core since 2012, that is, for about four years. Protective technologies such as SMEP and SMAP that prevent the kernel mode code (with maximum privileges from the microprocessor's point of view) from accessing the virtual memory pages of the user mode will not allow the exploit code to work out as needed.
We recommend that users install the appropriate patch for the OS immediately after it is released.
Source: https://habr.com/ru/post/275565/
All Articles