We do FTP for Windows Azure Pack
The author of the article is Sergey Gruzdov (egel@egel.su), Lead Engineer, Dataline
Windows Azure Pack provides subscribers with the ability to use their own ISO and VHD (X) files located in the library's designated folder for the subscriber only. At the moment, the only way to upload files to this folder is to organize FTP with a root folder pointing to the library folder allocated to subscribers. In this article, I will demonstrate how using Service Manager Automation (SMA) to create and delete subscribers ’folders when setting up or deleting a user, and using the Microsoft FTP extension to authorize their own authentication providers and home directories directly through the Azure Pack, eliminating the need to duplicate accounts in Active Directory.
Prepare Azure Pack
You must first add SMA assets:
- VMMConnection is a Connection type variable that specifies the FQDN of the VMM server and credentials. The account must be a member of the local administrators group on the library server, the VMM server, and in VMM, the members of the Administrators group.
- VMMLibPath is a variable with a shared folder in the root directory of the subscriber library
Ranbuki sma
Handle Subscriber Creation Event
Prepare a framework for creating a subscriber directory and linking it to a VMM account. The text is below. As a bonus, the code notifies the user after entering it on the admin portal (or in any other way) about the need to change the password. This eliminates the need to generate passwords and send them in clear text to the user.
Notify-Created-User
workflow Notify-Created-User { param ( [Parameter(Mandatory=$true)] [object] $params ) $VmmConnection = Get-AutomationConnection -Name 'VmmConnection' $VmmServerName = $VmmConnection.ComputerName $SecurePassword = ConvertTo-SecureString -AsPlainText -String $VmmConnection.Password -Force $VmmCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $VmmConnection.Username, $SecurePassword $eMail = $params.Name.SubString(0, $params.Name.IndexOf("_")) $vmmLib = Get-AutomationVariable -Name 'VMMLibPath' $libServer = $vmmLib.SubString(2) $libServer = $libServer.SubString(0, $libServer.IndexOf("\")) $tenantPath = "{0}\{1}" -f $vmmLib, $eMail Write-Output "Invoke create folder on $libServer" inlinescript { try { if (!(Test-Path $Using:tenantPath)) { Write-Output "Creating folder $($Using:tenantPath)" New-Item -Type Directory -Path $Using:tenantPath -ErrorAction Stop | Out-Null } else { Write-Output "Folder $($Using:tenantPath) already exist" } } catch { Write-Output $_ } } –PSComputer $libServer –PSCredential $VmmCredential inlinescript { $tenantSite = "https://my.azureline.ru" # URL Tenant Site $authSite = "https://auth.azureline.ru" # URL Tenant Auth Site $mail = $Using:eMail $roles = Get-SCUserRole -VMMServer $Using:VmmServerName | ?{$_.Name.Contains($mail)} # UserRole SCVMM. , ( ) if (!($roles -is [System.Array])) { try { [reflection.assembly]::loadwithpartialname("System.Net.Http") | Out-Null $forget = New-Object System.Net.Http.HttpClient $getMess = $forget.GetAsync($tenantSite).Result $getMess.EnsureSuccessStatusCode() | Out-Null $authPage = $getMess.Content.ReadAsStringAsync().Result $forgRegex = [regex]'form id="__AjaxAntiForgeryForm".*?__RequestVerificationToken.*?value="(?<Token>.*?)"' $m = $forgRegex.Match($authPage); if ($m.Success) { $forget.DefaultRequestHeaders.Add("x-ms-client-antiforgery-id", $m.Groups["Token"].Value); $data = New-Object System.Net.Http.StringContent("{`"emailAddress`":`"$($Using:eMail)`"}", [System.Text.Encoding]::UTF8, "application/json") $mess = $forget.PostAsync("$authSite/Account/SendMeResetPasswordLink", $data).Result $mess.EnsureSuccessStatusCode() | Out-Null Write-Output "Successfuly sent reset password link to $($Using:eMail)" } } catch { Write-Output $_ } Write-Output "Set library share for $($roles.Name). Share path $($Using:tenantPath)" Set-SCUserRole -UserRole $roles -UserRoleDataPath $Using:tenantPath -VMMServer $Using:VmmServerName | Out-Null } else { Write-Output "Nothing to do" } } –PSComputer $VmmServerName –PSCredential $VmmCredential } ')
FTP directory cleanup
To clean the FTP directory from the remote subscriber directories, you will have to make a scheduled run, since some VMM events (we need the Delete event for the VMM UserRole object) are not implemented in the SMA at this time.
CleanUp-Ftp-Folder
workflow CleanUp-Ftp-Folder { $VmmConnection = Get-AutomationConnection -Name 'VmmConnection' $VmmServerName = $VmmConnection.ComputerName $SecurePassword = ConvertTo-SecureString -AsPlainText -String $VmmConnection.Password -Force $VmmCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $VmmConnection.Username, $SecurePassword $vmmLib = Get-AutomationVariable -Name 'VMMLibPath' $libServer = $vmmLib.SubString(2) $libServer = $libServer.SubString(0, $libServer.IndexOf("\")) $dataPaths = inlinescript { $dataPaths = Get-SCUserRole -VMMServer $Using:VmmServerName | %{ $_.UserRoleDataPath } $dataPaths } -PSComputer $VmmServerName –PSCredential $VmmCredential inlinescript { $ftpFolders = Get-ChildItem -Directory -Path $Using:vmmLib | %{ $($_.FullName + '\') } if ($Using:dataPaths -ne $null) { $diffList = $ftpFolders | ?{ $Using:dataPaths -notcontains $_ } } if ($diffList) { foreach ($diff in $diffList) { if ([String]::IsNullOrEmpty($diff)) { continue } Write-Output "Deleting $diff" Remove-Item -Recurse -Force -Confirm:$false -Path $diff } } else { Write-Output "Nothing to delete" } } –PSComputer $libServer –PSCredential $VmmCredential } These ranbuki need to import, publish, assign the “Notify-Created-User” bookbook to the SPF tag and bind to the “Create” event of the “SPF-client” object:
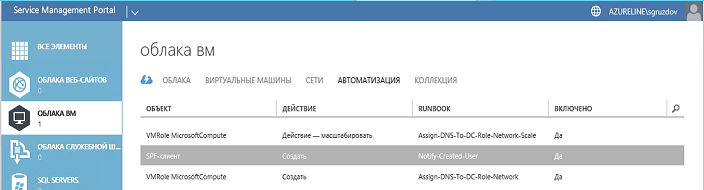
For the Cleanup-ftp-folder booklet, you need to create a schedule so that it runs once a day:

FTP preparation
Framework 2.0 / 3.5 services must be preinstalled.
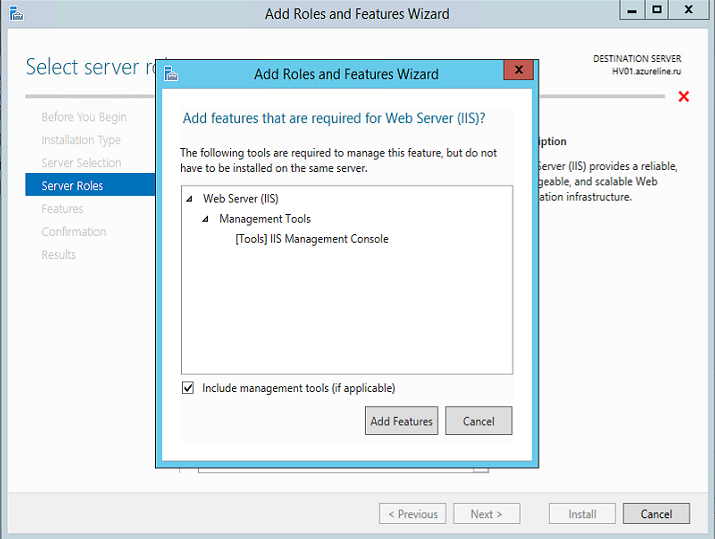
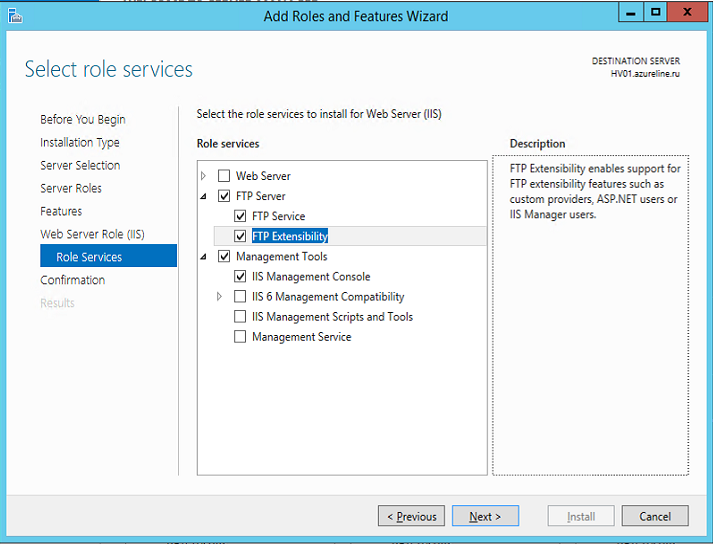
Using Server Manager, we add an FTP role with extension support:
Create an FTP server:
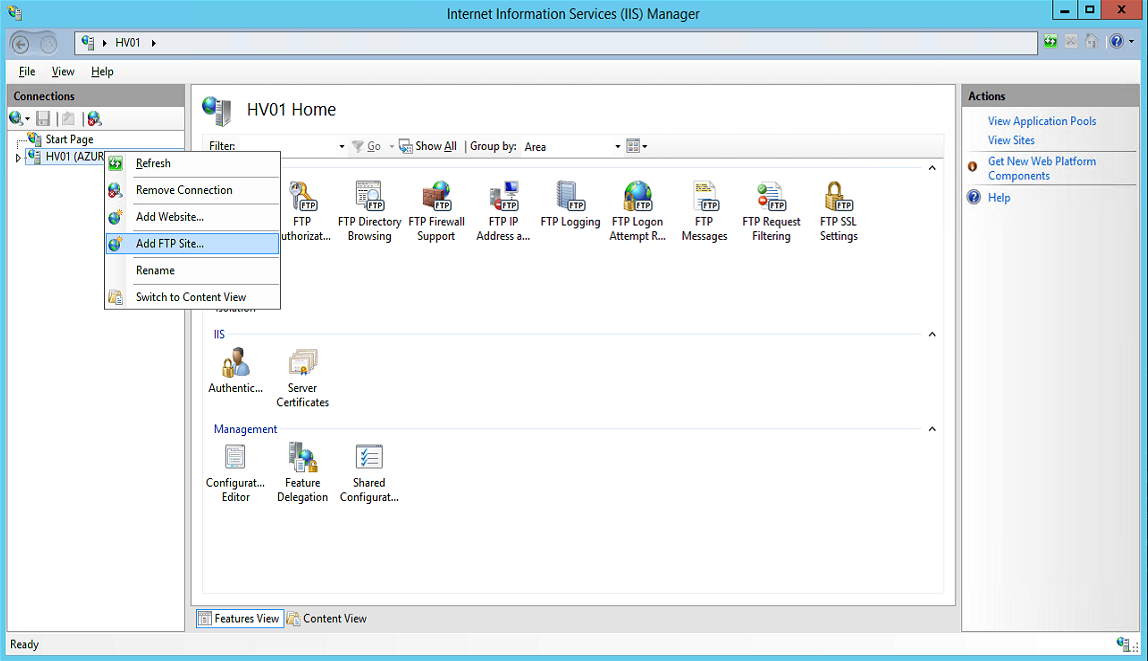
We specify the physical path to the root of the subscribers library as the path in the wizard. If the FTP server is deployed not on the library server, the best solution would be to create a symbolic link with the share, for example:
mklink /DC:\TenantsData \\vmmlibserver\TenantsData 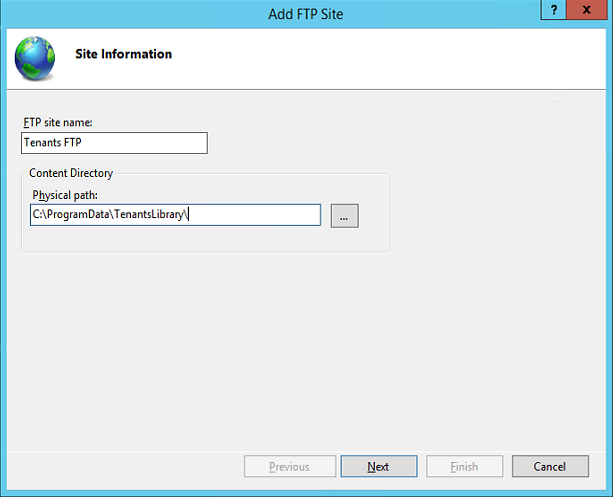
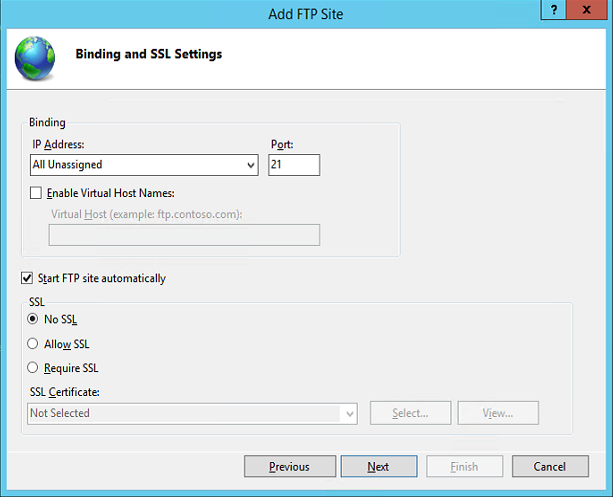
On the next page of the wizard we specify additional parameters (use SSL, port number, etc.):
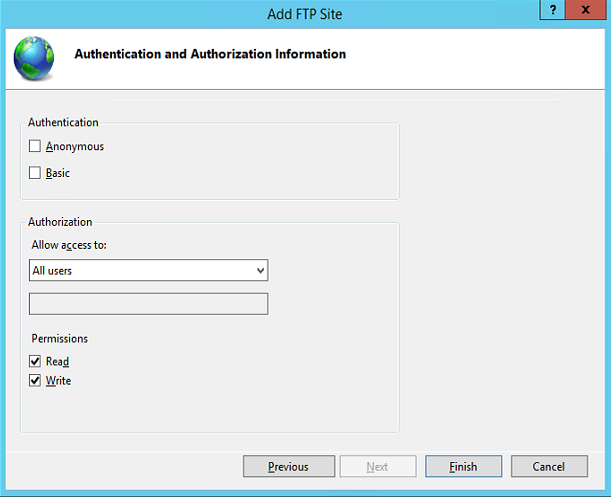
On the final page, we indicate that all users have the right to read and write, but do not indicate the supported authentication types:
This completes the initial setup. The remaining parameters will be indicated after the installation of the expansion module.
Installing an extension module and setting up FTP
Download the “Module.zip” archive attached to the article and unpack it (for example, in “C: \ Module”). Run the cmd interpreter as an administrator. Run the following commands (if your FTP is called differently, specify its name as a parameter):
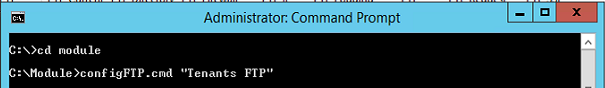
Get the following output:

After that, you need to fix the file "CustomFTPHomeDirectoryProvider.dll.config", specifying the values of the keys "auth" and "root". The “auth” key contains the URL of the TenantAuth site, the “root” key indicates the physical path to the subscriber library. Example:
<configuration> <appSettings> <add key="auth" value="https://auth.azureline.ru" /> <add key="root" value="C:\ProgramData\TenantsLibrary" /> </appSettings> </configuration> After this, the file "CustomFTPHomeDirectoryProvider.dll.config" must be copied along the physical path "C: \ Windows \ Microsoft.NET \ assembly \ GAC_MSIL \ CustomFTPHomeDirectoryProvider \ v4.0_1.0.0__a8ad38bd3b2a69ea".
Check settings
Open the IIS Management console, select the FTP site, open the “FTP Authentication” setting. The only authentication provider, CustomAuth, must be enabled:

Open the “FTP User Isolation” setting, make sure that “Custom” is enabled:

This setting indicates the user isolation level. With the help of a custom provider, the subscriber is “locked” in his own directory.
Now we are testing. I used the FTP client included in FAR. Connect:

Upload the file:
After updating the library we see the downloaded file:

On the Azure Pack portal, this image can now be connected:

Thus, with little or no additional effort, such as controlling additional accounts in AD for accessing FTP, the download point for ISO and VHD (X) files is convenient for the subscriber.
Materials (archives with a ready-made module, source code and ranbuk) can be downloaded from this link . That's all, see you soon!
Source: https://habr.com/ru/post/275555/
All Articles