Whitelisting with Windows Firewall

If paranoia dictates that you are not sufficiently protected, and only free tools are at hand for security, then you need to satisfy this feeling! Under the cat, we will create a white list of programs for accessing the network using standard Windows firewall, including PowerShell.
Introduction
Most encoders, trojans and other bad things from the world of cyber threats for their dark business use the ability to access the network from the victim's device: getting a key to encrypt files, sending confidential information and so on. Anti-virus companies in the fight against such opponents train their proactive technologies, even produce separate products for cryptographers, and for ordinary users of free protection they can only fine-tune their frontiers on their own. Since the days of Vista, the firewall built into Windows has become quite good, but most of the time it stands idle, beating off only unwritten incoming connections at best. Not everyone knows, but he can do a bit more - filter and outgoing connections, one has only to turn on this mode and configure it correctly.
So let's get started
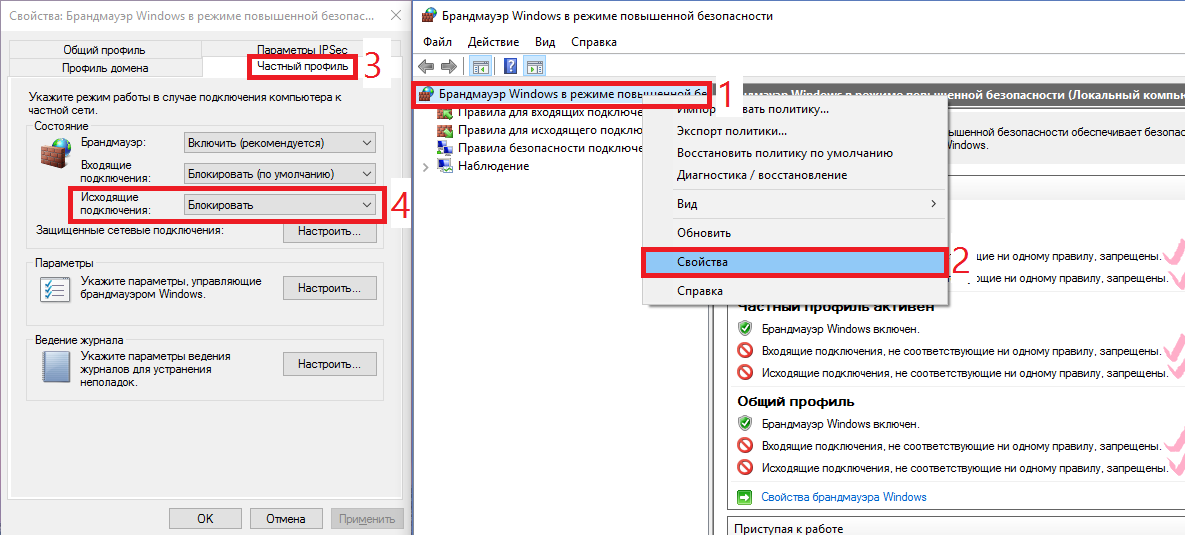
First of all, it is necessary to prohibit all outgoing connections (incoming ones, we believe, are already prohibited - the necessary software itself, as a rule, prescribes exceptions for itself). To do this, go to Control Panel -> System and Security -> Windows Firewall -> Advanced Settings. Next, select "Windows Firewall in Advanced Security Mode" and open Properties using the right mouse button. Depending on your network profile (private - local network with router, public - directly to the Internet, domain - domain network), the profile tab is selected and the “Block” mode is selected for outgoing connections (I configured the same for all profiles).
')
Screenshots


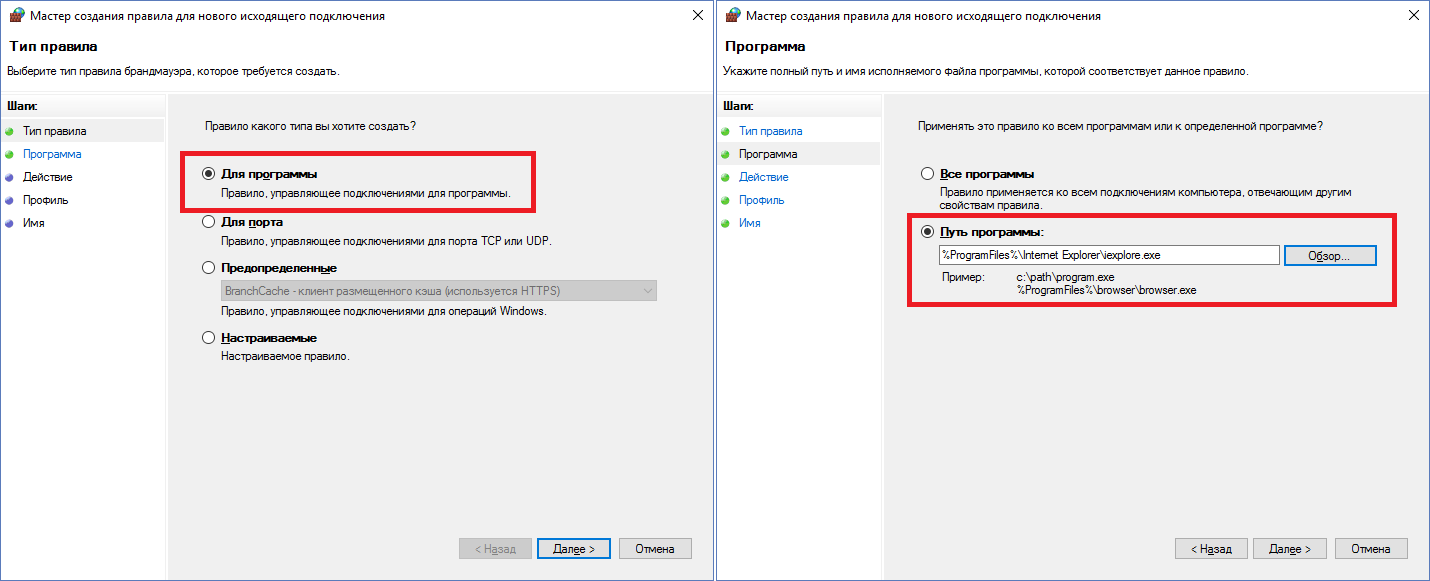
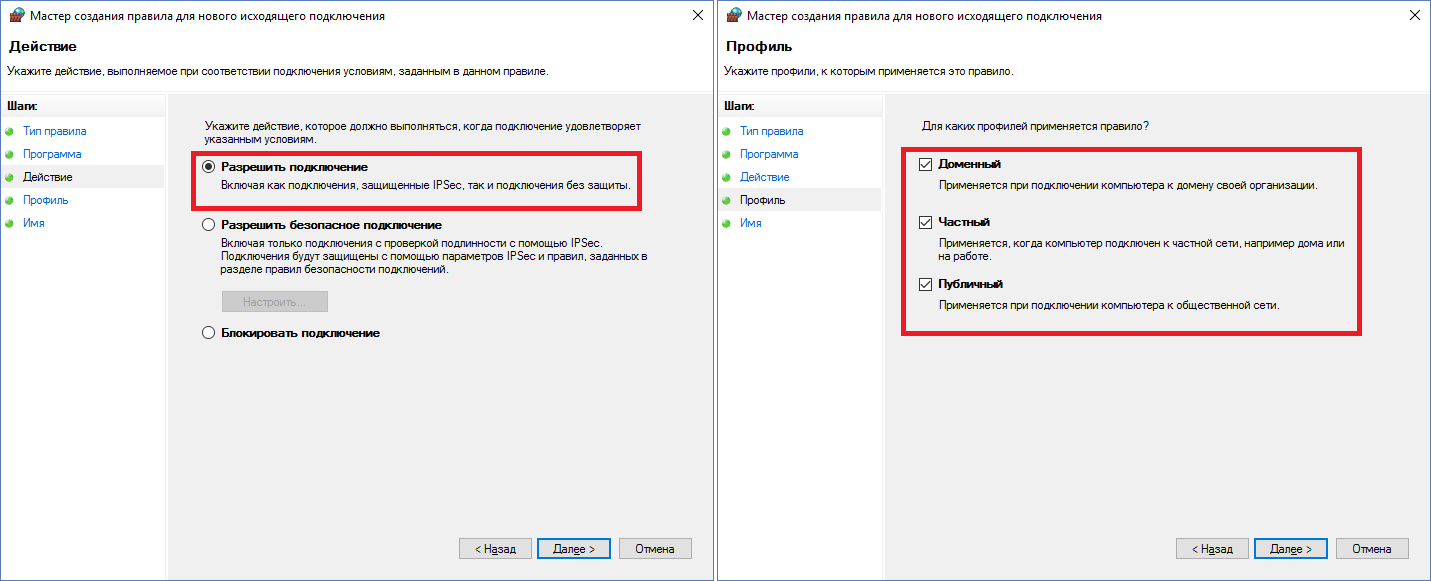
At the moment, no program can go online (except for rules that already exist). It is easy to check this by opening a browser with any site - you will certainly get a network error. To load the page you need to create a corresponding rule. Consider Internet Explorer - all have it on Windows. Right-click on “Rules for outgoing connection” -> Create a rule. A window opens with 4 types of rules, for IE the first one - “For the program”. Next you need to specify the path to the program - in our case -
C:\Program Files\Internet Explorer\iexplore.exe . Do not forget that the owners of 64-bit systems should create one more such rule, only for Program Files (x86) (IE is also installed there). After selecting a file, select the item “Allow connection”, then check the desired network profiles. It remains only to come up with a name for our rule. I recommend all the rules to write with the same word / symbol, then it will be more convenient to search. The created rule will be displayed in the general list.Screenshots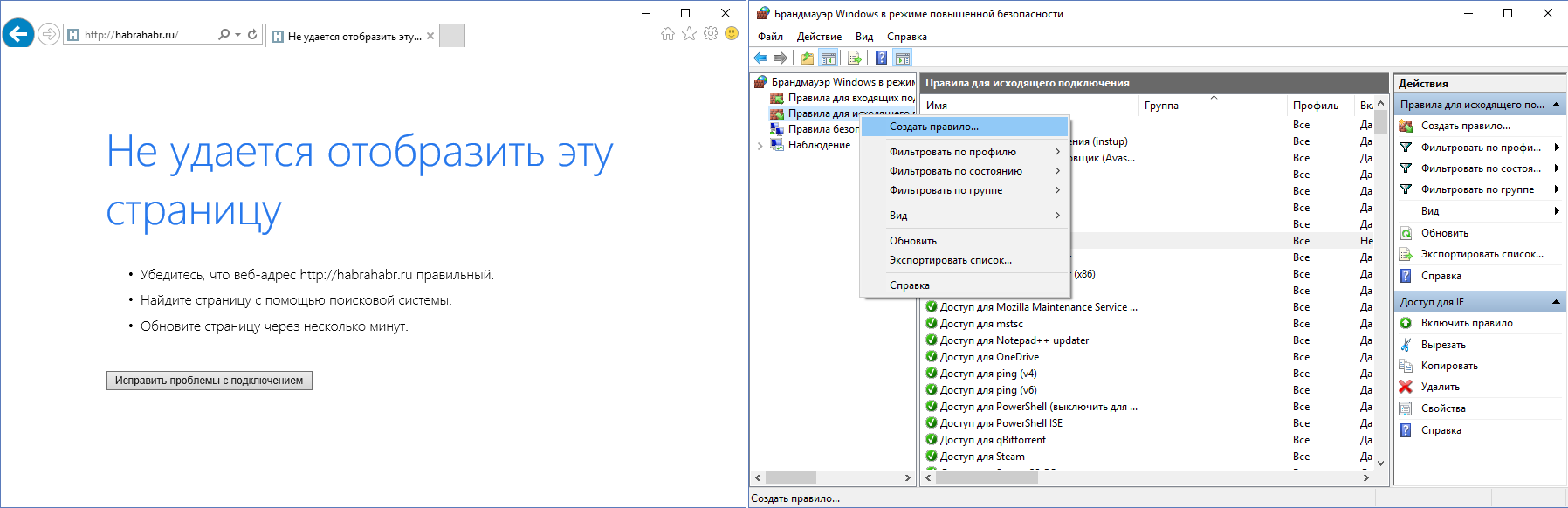





For programs, the rules have been learned to do, and what about services? Let the Mozilla Maintenance Service be added to the exceptions. Create a new rule, select the type "Custom". Next, click "Configure", select "Apply to service" and search for the desired service in the list or enter the service name manually below. Then it is proposed to configure the protocol and ports, but in this case they can be left by default - the program is trusted and the clown knows what it uses there when delivering and installing updates. We don’t touch IP addresses in the same way. Next, allow the connection, select profiles and set the name for the rule.
Screenshots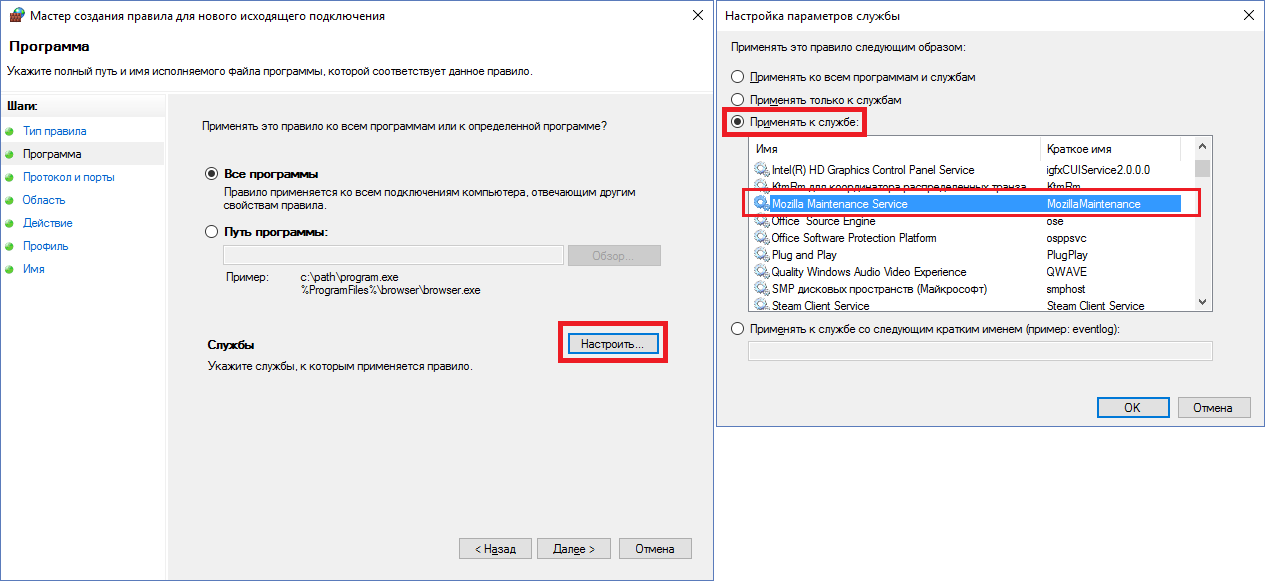
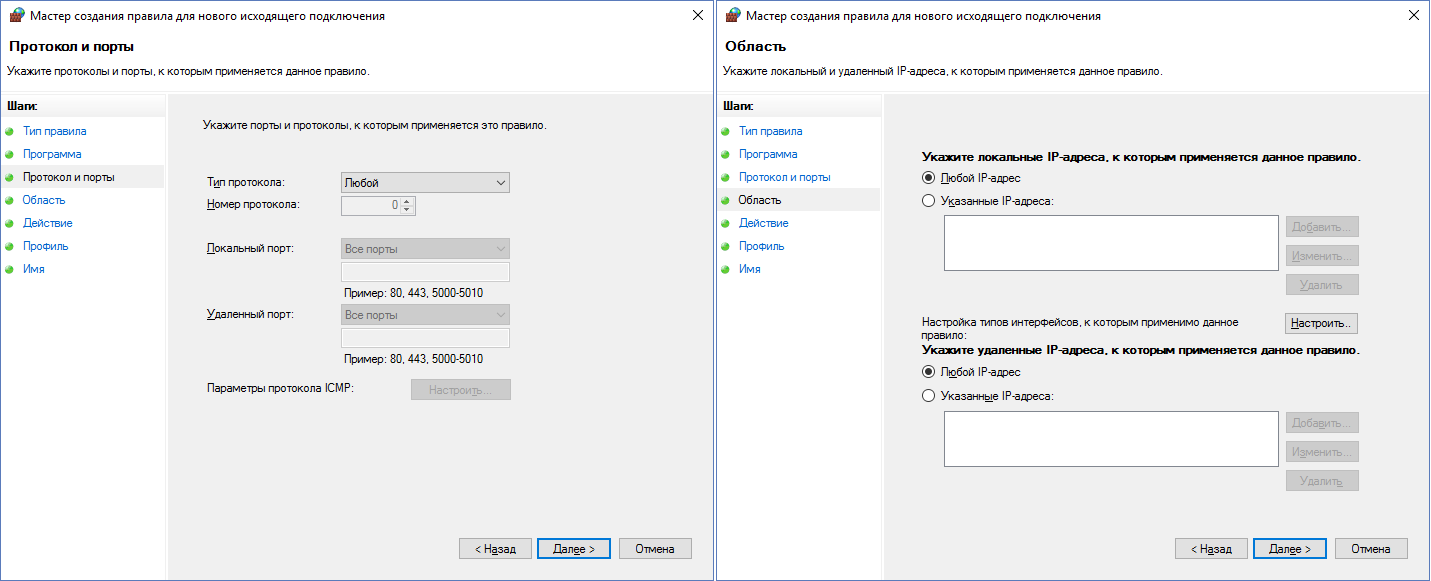


It would seem that the main points are passed, what now? And now the pitfalls. If someone uses the TeamViewer remote control program in their activities that puts the service with them, it seems to be enough to find the service in the list and add a rule for it. But it will not work. Instead of the service, you need to add the rule “For the program” and select the executable file of the service
C:\Program Files (x86)\TeamViewer\TeamViewer_Service.exe (path for a 64-bit system). This is a common situation, so do not rush to add services, start with exe. In addition, ping will stop working in our system. For it, you need to add a rule of the “Configurable” type, leave everything by default, just select the ICMPv4 protocol and click “Configure” at the bottom, where you can tick only the “Echo request” checkbox. Now ping and tracert will work. For IPv6 repeat, but already with the ICMPv6 protocol. If a rule has already been created, but something needs to be changed in it, this can be easily done by selecting the necessary rule in the list and going into its properties. On the tabs, you can customize everything for every taste - to tie the service to a specific exe, restrict the program in ports, etc.Screenshot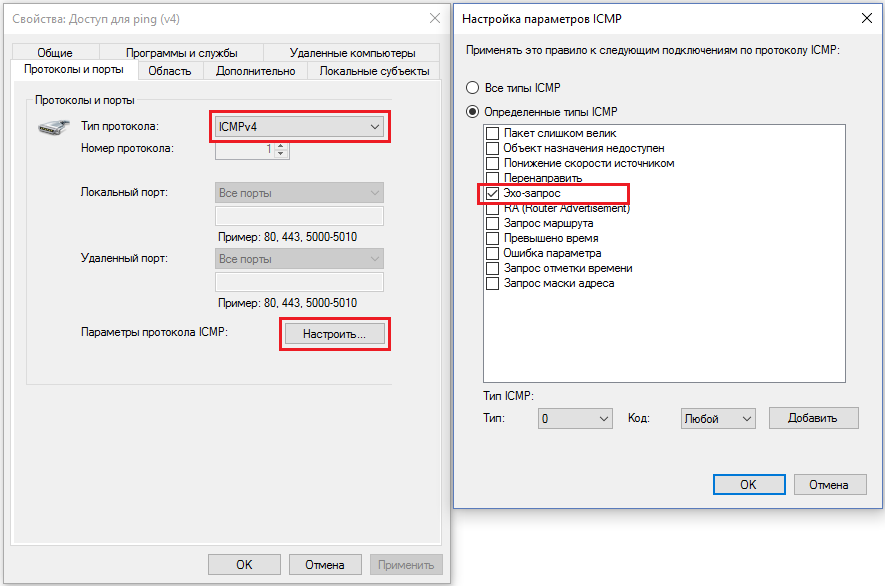
Properties of an already created rule for ping

Properties of an already created rule for ping
By upgrading from Windows 8.1 to Windows 10, I could not create a workable rule for OneDrive. It seems to be a simple rule for
%USERPROFILE%\AppData\Local\Microsoft\OneDrive\OneDrive.exe and everything should work. But, having spent several months, I came to the C:\Users\ProfileName\AppData\Local\Microsoft\OneDrive\OneDrive.exe that, it turns out, it was necessary to prescribe the direct path C:\Users\ProfileName\AppData\Local\Microsoft\OneDrive\OneDrive.exe , although in previous OS of the same family everything worked well and with the first option (riddle?).Experience and PowerShell
The list of rules accumulated over the N-th time, I will present in the form of commands for PowerShell - easier to automate. To be able to run the script for execution in PowerShell, you must give permission to this for unsigned scripts in the system (for paranoids, you can then return it to the place):
Set-ExecutionPolicy Unrestricted Set-ExecutionPolicy Default # Blocking all outgoing connections with a firewall looks like this:
Set-NetFirewallProfile -All -DefaultOutboundAction Block The command to add a rule for all profiles and outgoing directions for explorer.exe - update tiles on Windows 8.1. I believe that on the 10-ke used:
New-NetFirewallRule -Program 'C:\Windows\explorer.exe' -Action Allow -Profile Any -DisplayName ' explorer.exe' -Direction Outbound Let us have the first cell contains the name of the rule, and the second cell stores the path to the program. And we will have N such two-cell lines - how many pieces of rules. All this will be stored in
$programs . Let's start with a simple one: Internet Explorer, Google Chrome, Tor Browser, Yandex.Browser, Notepad ++, Visual Studio 2015, qBittorrent, HWMonitor, OneDrive, PowerShell, PowerShell ISE, Steam, CS GO, TeamViewer, and so on - all more or less simple applications which require access from 1-2 exe files to access the network.Filling the $ programs table
# $env - %USERPROFILE%, %SystemRoot% .. $programs = (' Internet Explorer (x86)', (${env:ProgramFiles(x86)}+'\Internet Explorer\iexplore.exe')), (' Internet Explorer', ($env:ProgramFiles+'\Internet Explorer\iexplore.exe')), (' Google Chrome', (${env:ProgramFiles(x86)}+'\Google\Chrome\Application\chrome.exe')), (' Google Update', (${env:ProgramFiles(x86)}+'\Google\Update\GoogleUpdate.exe')), (' Tor Browser', ($env:USERPROFILE+'\AppData\Local\Tor Browser\Browser\firefox.exe')), (' Tor Browser updater', ($env:USERPROFILE+'\AppData\Local\Tor Browser\Browser\updater.exe')), (' Yandex.Browser', ($env:USERPROFILE+'\AppData\Local\Yandex\YandexBrowser\Application\browser.exe')), (' Notepad++ (GUP)', (${env:ProgramFiles(x86)}+'\Notepad++\updater\GUP.exe')), (' Visual Studio 2015', (${env:ProgramFiles(x86)}+'\Microsoft Visual Studio 14.0\Common7\IDE\devenv.exe')), (' Blend (Visual Studio)', (${env:ProgramFiles(x86)}+'\Microsoft Visual Studio 14.0\Common7\IDE\Blend.exe')), (' qBittorrent', (${env:ProgramFiles(x86)}+'\qBittorrent\qbittorrent.exe')), (' HWMonitor', ($env:ProgramFiles+'\CPUID\HWMonitor\HWMonitor.exe')), (' OneDrive', ($env:USERPROFILE+'\AppData\Local\Microsoft\OneDrive\OneDrive.exe')), (' PowerShell ( )', ($env:SystemRoot+'\System32\WindowsPowerShell\v1.0\powershell.exe')), (' PowerShell ISE ( )', ($env:SystemRoot+'\System32\WindowsPowerShell\v1.0\powershell_ise.exe')), (' Steam', (${env:ProgramFiles(x86)}+'\Steam\Steam.exe')), (' steamwebhelper', (${env:ProgramFiles(x86)}+'\Steam\bin\steamwebhelper.exe')), (' Steam CS GO', ('D:\Games\SteamLibrary\steamapps\common\Counter-Strike Global Offensive\csgo.exe')), (' TeamViewer', (${env:ProgramFiles(x86)}+'\TeamViewer\TeamViewer.exe')), (' TeamViewer_Service', (${env:ProgramFiles(x86)}+'\TeamViewer\TeamViewer_Service.exe')) Also, if you wish, you can add a tricky Avast (he still needs a service) and Firefox (+ service) to the tablet.
Add to $ programs
(' AvastUI+', ($env:ProgramFiles+'\AVAST Software\Avast\AvastUI.exe')), (' AvastSvc', ($env:ProgramFiles+'\AVAST Software\Avast\AvastSvc.exe')), (' Avast (AvastEmUpdate)', ($env:ProgramFiles+'\AVAST Software\Avast\AvastEmUpdate.exe')), (' Avast (instup)', ($env:ProgramFiles+'\AVAST Software\Avast\setup\instup.exe')), (' Mozilla Firefox', (${env:ProgramFiles(x86)}+'\Mozilla Firefox\firefox.exe')) All rows of the table will be processed individually as follows:
foreach($prog in $programs) { try { New-NetFirewallRule -Program $prog[1] -Action Allow -Profile Any -DisplayName $prog[0] -Direction Outbound Write-Host ': '$prog[0] } catch { Write-Host ': '$prog[0] } Write-Host } In addition, it is necessary to deal with non-standard rules and services. For example, the update center works via svchost.exe using the TCP protocol through ports 80 and 443. And the application store uses a separate WSService service for updating. In addition, we do not forget about ping and services for the necessary applications:
try { $i = ' Windows Update/Modern Apps' New-NetFirewallRule -Program ($env:SystemRoot+'\System32\svchost.exe') -Protocol TCP -RemotePort 80, 443 -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' Avast ()' New-NetFirewallRule -Service 'avast! Antivirus' -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' Mozilla Maintenance Service' New-NetFirewallRule -Service 'MozillaMaintenance' -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' ping (v4)' New-NetFirewallRule -Profile Any -Action Allow -DisplayName $i -Protocol ICMPv4 -IcmpType 8 -Direction Outbound $i = ' ping (v6)' New-NetFirewallRule -Profile Any -Action Allow -DisplayName $i -Protocol ICMPv6 -IcmpType 8 -Direction Outbound $i = ' Windows' New-NetFirewallRule -Service 'WSService' -Action Allow -Profile Any -DisplayName $i -Direction Outbound # , ( , ) $i = ' ()' New-NetFirewallRule -Enabled False -Action Allow -Profile Private -DisplayName $i -Direction Outbound Write-Host ' ' } catch { Write-Host ' :' $i } Write-Host That's probably all. At this story you can finish. I am passing the initiative now into your hands, dare! I hope you learned something new, or at least remembered well forgotten old. The final script (.ps1) can be found under the spoiler below.
Summary script
Set-NetFirewallProfile -All -DefaultOutboundAction Block $programs = (' Internet Explorer (x86)', (${env:ProgramFiles(x86)}+'\Internet Explorer\iexplore.exe')), (' Internet Explorer', ($env:ProgramFiles+'\Internet Explorer\iexplore.exe')), (' Google Chrome', (${env:ProgramFiles(x86)}+'\Google\Chrome\Application\chrome.exe')), (' Google Update', (${env:ProgramFiles(x86)}+'\Google\Update\GoogleUpdate.exe')), (' Tor Browser', ($env:USERPROFILE+'\AppData\Local\Tor Browser\Browser\firefox.exe')), (' Tor Browser updater', ($env:USERPROFILE+'\AppData\Local\Tor Browser\Browser\updater.exe')), (' Yandex.Browser', ($env:USERPROFILE+'\AppData\Local\Yandex\YandexBrowser\Application\browser.exe')), (' Notepad++ (GUP)', (${env:ProgramFiles(x86)}+'\Notepad++\updater\GUP.exe')), (' Visual Studio 2015', (${env:ProgramFiles(x86)}+'\Microsoft Visual Studio 14.0\Common7\IDE\devenv.exe')), (' Blend (Visual Studio)', (${env:ProgramFiles(x86)}+'\Microsoft Visual Studio 14.0\Common7\IDE\Blend.exe')), (' qBittorrent', (${env:ProgramFiles(x86)}+'\qBittorrent\qbittorrent.exe')), (' HWMonitor', ($env:ProgramFiles+'\CPUID\HWMonitor\HWMonitor.exe')), (' OneDrive', ($env:USERPROFILE+'\AppData\Local\Microsoft\OneDrive\OneDrive.exe')), (' PowerShell ( )', ($env:SystemRoot+'\System32\WindowsPowerShell\v1.0\powershell.exe')), (' PowerShell ISE ( )', ($env:SystemRoot+'\System32\WindowsPowerShell\v1.0\powershell_ise.exe')), (' Steam', (${env:ProgramFiles(x86)}+'\Steam\Steam.exe')), (' steamwebhelper', (${env:ProgramFiles(x86)}+'\Steam\bin\steamwebhelper.exe')), (' Steam CS GO', ('D:\Games\SteamLibrary\steamapps\common\Counter-Strike Global Offensive\csgo.exe')), (' TeamViewer', (${env:ProgramFiles(x86)}+'\TeamViewer\TeamViewer.exe')), (' TeamViewer_Service', (${env:ProgramFiles(x86)}+'\TeamViewer\TeamViewer_Service.exe')), (' explorer.exe', ($env:SystemRoot+'\explorer.exe')), (' AvastUI+', ($env:ProgramFiles+'\AVAST Software\Avast\AvastUI.exe')), (' AvastSvc', ($env:ProgramFiles+'\AVAST Software\Avast\AvastSvc.exe')), (' Avast (AvastEmUpdate)', ($env:ProgramFiles+'\AVAST Software\Avast\AvastEmUpdate.exe')), (' Avast (instup)', ($env:ProgramFiles+'\AVAST Software\Avast\setup\instup.exe')), (' Mozilla Firefox', (${env:ProgramFiles(x86)}+'\Mozilla Firefox\firefox.exe')) foreach($prog in $programs) { try { New-NetFirewallRule -Program $prog[1] -Action Allow -Profile Any -DisplayName $prog[0] -Direction Outbound Write-Host ': '$prog[0] } catch { Write-Host ': '$prog[0] } Write-Host } try { $i = ' Windows Update/Modern Apps' New-NetFirewallRule -Program ($env:SystemRoot+'\System32\svchost.exe') -Protocol TCP -RemotePort 80, 443 -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' Avast ()' New-NetFirewallRule -Service 'avast! Antivirus' -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' Mozilla Maintenance Service' New-NetFirewallRule -Service 'MozillaMaintenance' -Action Allow -Profile Any -DisplayName $i -Direction Outbound $i = ' ping (v4)' New-NetFirewallRule -Profile Any -Action Allow -DisplayName $i -Protocol ICMPv4 -IcmpType 8 -Direction Outbound $i = ' ping (v6)' New-NetFirewallRule -Profile Any -Action Allow -DisplayName $i -Protocol ICMPv6 -IcmpType 8 -Direction Outbound $i = ' Windows' New-NetFirewallRule -Service 'WSService' -Action Allow -Profile Any -DisplayName $i -Direction Outbound # , ( , ) $i = ' ()' New-NetFirewallRule -Enabled False -Action Allow -Profile Private -DisplayName $i -Direction Outbound Write-Host ' ' } catch { Write-Host ' :' $i } Write-Host Source: https://habr.com/ru/post/275549/
All Articles