A vulnerability has been discovered in the Linux kernel that allows getting superuser rights
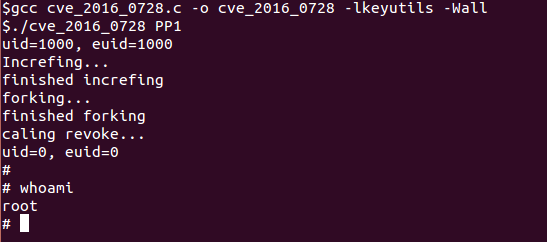
Almost all versions of the Linux kernel, from 3.8 to 4.5 (in git) are subject to a rather serious vulnerability , which allows a local user to get superuser rights. It turns out that the CVE-2016-0728 vulnerability has existed since 2012, and users of the Android OS are most at risk. The fact is that Google can’t verify the code of applications and games created using the NDK (Native Development Kit) and laid out on Google Play.
As for PCs and servers, the situation is not so complicated, especially if there is only one user in the system. In addition, this vulnerability is not too dangerous even if users are prohibited from executing code, or different OS instances are in a virtualization environment.
The vulnerability was discovered by experts in keyrings, a kernel subsystem that is responsible for caching and storing both authentication keys and certificates for encryption. If the objects are incorrectly released, it is possible to access the already freed memory area at the time when the process replaces the current session keyrings with the same instance. Interestingly, the code for exploiting the found vulnerability is quite simple and consists of only 100 lines in C. The exploit execution time is half an hour.
')
All information on the issue is available here - CVE-2016-0728 . Now updates to the kernel packages that address the vulnerability are only released by Debian developers.
Source: https://habr.com/ru/post/275543/
All Articles