Simple removal of the "tricked" protection kraftway credo vv18
According to the state program, we have been allocated several such thin clients to the enterprise.
Many were glad that it takes up little space (mounted on the back of the monitor), it works absolutely silently in the absence of fans and works relatively quickly compared to old computers that were before. The most interesting thing started later when users started losing eToken keys.


Without it, the launch of the device was not possible, at startup the computer asked for the key, disabling the TSL protection is also not possible, access to the BIOS is also prohibited (if the keys are lost / locked).
It is not allowed to disable TSM protection at all for security reasons. The documents remaining in the memory of the device are also not possible to get, as the password was put on the drive (and without having PC3000 I think it would not work to remove them from there) and other computers did not identify it. 2 eTokens were supplied to this terminal station, one was granted administrative rights by the other. The users who lost their key were given admin keys on receipt, which they attached to the device body with a rope, so as not to lose, but successfully forgot the keys of the keys and, if entered incorrectly (15 times!), Blocked the key and, accordingly, the device itself.
There is nothing to do, I had to go on the Internet to look for ways to unlock, of which there was no, to read a mountain of reviews, which stated how great the protection of this thin client was, that's just a piece of description.
')

Note that data cannot be retrieved even with full access to the terminal station hardware.
I had to call their company, where they gave several numbers of authorized centers in our city. Almost all call centers did not work with computers anymore, but someone had closed at all. Finally, stumbled upon a worker, came to their office and gave the station a repair. After 2 weeks, they called and told her to pick it up. As it turned out, they had not repaired it, and since the non-warranty case gave the number of those specialist from Kraft.
By calling this specialist, he set the price for repairs at 12t.r. (!!!) which included the replacement of the motherboard (!) plus it was necessary to pay for its return shipping. A bit ofigev from the price, and this new station is not much more expensive than the boss said to throw it into the far corner, like buy a new one, but later.
Of course, I did not throw it into the corner, but I wondered if it was a good idea that it would be nice to try to unlock it, and if it doesn’t work out, let it be for parts.
Having opened the case, I found a completely ordinary motherboard for nettops, but instead of a tin one there was a 4GB gd drive.

Device motherboard

She also removed the radiator (photo before soldering)


Flash drive is not readable for the reason described above.
Having some experience in repairing computer equipment, I decided to first flash the trained eye to detect this chip almost immediately.

Covered with plastic foil
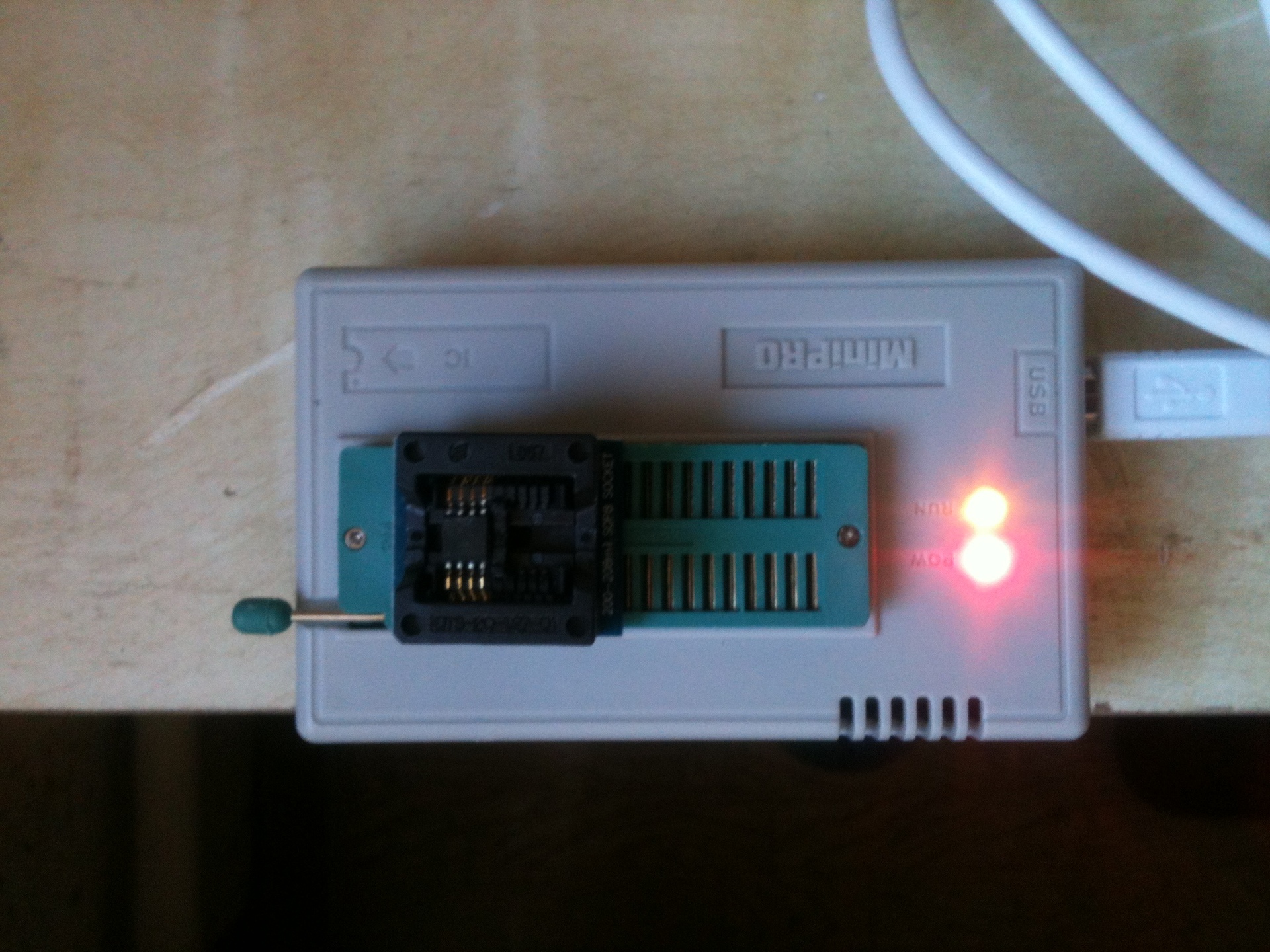
He disengaged the microchip (cFeon q16-100hip) with a hair dryer, inserted it into the programmer and saved the native firmware.
I did not find the firmware for this microcircuit in tyrnet, I had to gut a worker, having taken the exact same station from the user under the guise of a virus check.
After a successful flashing, flash soldered into place and launched the station, which asked for eToken, had to run again to that user and take the key from him. Recognizing the key, the station started up as new.
This was how the myth about the protection of this station was broken, in the description of which, by the way, it was said that even with full hardware access to the computer, the attacker could not read the data. And of course, such a repair doesn’t pull on 12t.r.
If someone got into the same situation, below I put out a clean firmware with the TSM protection removed, after reflashing the station will work with it without keys. Passwords to eToken can be changed in the eToken PKI Client 5.1 program. Having such an adapter, you can not dispense a microcircuit

There is also another way to remove TSM protection in the bin file to replace the firmware (in red)

On

In this case, the key information will remain and, if the security is not carefully turned on in the BIOS, the terminal station will block again
I hope the article was useful, if anyone has little experience in soldering or similar repairs, I can later make a video on the replacement and flashing of this type of chip.
For any manipulations with flash, be sure to save the firmware.
Thank you all for your attention!
PS - I apologize for the quality of the pictures taken on an old phone, but I think it does not matter.
Below, some frames of the firmware process were specially carried to the bottom since they are not of practical value.


The firmware with the Feon q16-100hip is completely removed TSM protection, reflash it with flash and, if necessary, configure eTocken again for TSM.
PS: the article was lying in the sandbox for 2 years and to be honest, I already scored on it. Hardly found photos and restored
access to the account (thanks to the guys with technical support), I will add the article with photos later as I can’t find some. Dump with flash memory updated, you can download it.
Many were glad that it takes up little space (mounted on the back of the monitor), it works absolutely silently in the absence of fans and works relatively quickly compared to old computers that were before. The most interesting thing started later when users started losing eToken keys.

Without it, the launch of the device was not possible, at startup the computer asked for the key, disabling the TSL protection is also not possible, access to the BIOS is also prohibited (if the keys are lost / locked).
It is not allowed to disable TSM protection at all for security reasons. The documents remaining in the memory of the device are also not possible to get, as the password was put on the drive (and without having PC3000 I think it would not work to remove them from there) and other computers did not identify it. 2 eTokens were supplied to this terminal station, one was granted administrative rights by the other. The users who lost their key were given admin keys on receipt, which they attached to the device body with a rope, so as not to lose, but successfully forgot the keys of the keys and, if entered incorrectly (15 times!), Blocked the key and, accordingly, the device itself.
There is nothing to do, I had to go on the Internet to look for ways to unlock, of which there was no, to read a mountain of reviews, which stated how great the protection of this thin client was, that's just a piece of description.
')

Note that data cannot be retrieved even with full access to the terminal station hardware.
I had to call their company, where they gave several numbers of authorized centers in our city. Almost all call centers did not work with computers anymore, but someone had closed at all. Finally, stumbled upon a worker, came to their office and gave the station a repair. After 2 weeks, they called and told her to pick it up. As it turned out, they had not repaired it, and since the non-warranty case gave the number of those specialist from Kraft.
By calling this specialist, he set the price for repairs at 12t.r. (!!!) which included the replacement of the motherboard (!) plus it was necessary to pay for its return shipping. A bit ofigev from the price, and this new station is not much more expensive than the boss said to throw it into the far corner, like buy a new one, but later.
Of course, I did not throw it into the corner, but I wondered if it was a good idea that it would be nice to try to unlock it, and if it doesn’t work out, let it be for parts.
Having opened the case, I found a completely ordinary motherboard for nettops, but instead of a tin one there was a 4GB gd drive.
Device motherboard
She also removed the radiator (photo before soldering)
Flash drive is not readable for the reason described above.
Having some experience in repairing computer equipment, I decided to first flash the trained eye to detect this chip almost immediately.
Covered with plastic foil
He disengaged the microchip (cFeon q16-100hip) with a hair dryer, inserted it into the programmer and saved the native firmware.
I did not find the firmware for this microcircuit in tyrnet, I had to gut a worker, having taken the exact same station from the user under the guise of a virus check.
After a successful flashing, flash soldered into place and launched the station, which asked for eToken, had to run again to that user and take the key from him. Recognizing the key, the station started up as new.
This was how the myth about the protection of this station was broken, in the description of which, by the way, it was said that even with full hardware access to the computer, the attacker could not read the data. And of course, such a repair doesn’t pull on 12t.r.
If someone got into the same situation, below I put out a clean firmware with the TSM protection removed, after reflashing the station will work with it without keys. Passwords to eToken can be changed in the eToken PKI Client 5.1 program. Having such an adapter, you can not dispense a microcircuit
There is also another way to remove TSM protection in the bin file to replace the firmware (in red)

On

In this case, the key information will remain and, if the security is not carefully turned on in the BIOS, the terminal station will block again
I hope the article was useful, if anyone has little experience in soldering or similar repairs, I can later make a video on the replacement and flashing of this type of chip.
For any manipulations with flash, be sure to save the firmware.
Thank you all for your attention!
PS - I apologize for the quality of the pictures taken on an old phone, but I think it does not matter.
Below, some frames of the firmware process were specially carried to the bottom since they are not of practical value.
The firmware with the Feon q16-100hip is completely removed TSM protection, reflash it with flash and, if necessary, configure eTocken again for TSM.
PS: the article was lying in the sandbox for 2 years and to be honest, I already scored on it. Hardly found photos and restored
access to the account (thanks to the guys with technical support), I will add the article with photos later as I can’t find some. Dump with flash memory updated, you can download it.
Source: https://habr.com/ru/post/275123/
All Articles