Microsoft and Adobe have fixed vulnerabilities in their products.
Microsoft has released updates for its products that cover 25 unique vulnerabilities (6 updates with Critical status and 3 more Important). The various components and drivers of Windows, Internet Explorer and Edge web browsers, Office, and the Exchange Server product were updated. Updates do not close any vulnerabilities that have been used in cyber attacks on users. For Internet Explorer and Edge, only two vulnerabilities were closed.

In turn, Adobe released the update APSB16-02 , which fixes 17 vulnerabilities in Reader and Acrobat products, which are used to view and create PDF files. Most of the closed vulnerabilities allow attackers to remotely execute code using a special malicious PDF file.
')
Update MS16-001 closes two vulnerabilities CVE-2016-0002 and CVE-2016-0005 in Internet Explorer 7-11 on Windows Vista +. The first vulnerability relates to the VBScript Scripting Engine (vbscript.dll) engine and allows attackers to remotely execute code using special malicious content (included in MS16-003 ). The second vulnerability allows attackers to elevate their privileges in the system to the level of the current user, bypassing the restrictions of the Low IL sandbox (Integrity Level). Critical.
Update MS16-002 fixes two vulnerabilities CVE-2016-0003 and CVE-2016-0024 in the Edge web browser on Windows 10. Both vulnerabilities allow attackers to remotely execute code in a web browser using a specially crafted web page. The only difference is that the first vulnerability is located in the web browser itself, and the second in the JavaScript engine (jscript.dll) Critical.
Update MS16-004 fixes five vulnerabilities in Office 2007+ products. Two of the five vulnerabilities can be used by attackers for remote code execution using specially crafted Office files. Two more vulnerabilities are related to the Security Feature Bypass type and are present in the SharePoint server product. One vulnerability with identifier CVE-2016-0012 allows you to bypass the ASLR defense mechanism by using an insecure library from the Visual Basic 6.0 Runtime in Office. Critical.
Update MS16-005 fixes two vulnerabilities with identifiers CVE-2016-0008 and CVE-2016-0009. They are present in the components of the Windows Vista + GUI-subsystem (win32k.sys and gdi32.dll). The first vulnerability in gdi32.dll allows attackers to bypass the ASLR defense mechanism, and the second execute the code remotely in the system when visiting a malicious website. Critical.
The MS16-006 update fixes the RCE vulnerability CVE-2016-0034 in Silverlight 5 environment. Using the vulnerability, attackers can remotely execute code on the user's system using the malicious Silverlight application hosted on a web resource. Critical.
Update MS16-007 fixes six different vulnerabilities in Windows Vista + components. The update affects such libraries as Advapi32.dll, Rpcrt4.dll, Qedit.dll, Ksuser.dll. Drmk.sys driver and others. One of the RCE vulnerabilities CVE-2016-0015 is present in the multimedia framework DirectShow, its operation is possible when the user opens a special malicious file. Two more RCE vulnerabilities are related to improper loading of DLL into memory (DLL Loading Remote Code Execution), their exploitation is possible under a similar scenario, while the attackers will get the rights of the current account in the system. Vulnerability CVE-2016-0019 is present in the Remote Desktop Service (RDP) component only on Windows 10 (Windows Remote Desktop Protocol Security Bypass Vulnerability). Using this vulnerability and the RDP client version less than on Windows 10, an attacker can connect to the system using an account that does not have a password, despite the default policy on the remote system to prohibit the use of such accounts for remote connection. Important.
Update MS16-008 fixes two vulnerabilities with identifiers CVE-2016-0006 and CVE-2016-0007, which can be used by attackers to elevate their privileges to a high SYSTEM level on Windows Vista +. Vulnerabilities are present in the so-called code. Windows Mount Point subsystems and are located in the OS kernel files: Winload.efi, Winload.exe, Ntdll.dll, Ntoskrnl.exe, Smss.exe, etc. To exploit the vulnerability, an attacker must run a special application on it that uses operations with such file system objects as reparse points. Important.
The MS16-010 update closes four vulnerabilities like Spoofing in Exchange Server 2013+ software. Vulnerabilities in processing Outlook Web Access (OWA) requests allow an attacker to obtain confidential information from the user by stealthily redirecting the user to a phishing resource. Important.
This patch tuesday was the latest for Windows 8 and Internet Explorer versions 7-10. At the same time, users of these versions of the web browser on the next versions of the OS will continue to receive updates until the end of the OS support.

We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Five use-after-free (UAC) vulnerabilities (CVE-2016-0932, CVE-2016-0934, CVE-2016-0937, CVE-2016-0940, CVE-2016-0941) were closed for Reader and Acrobat used by attackers for remote code execution using a special PDF file. 11 more vulnerabilities related to memory corruption can also be used for the same purposes.
Vulnerability CVE-2016-0943 allows you to bypass the security restrictions when using the Javascript API. The latest vulnerability, CVE-2016-0947, is present in the Adobe Download Manager and allows attackers to execute code due to an error in the implementation of the directory listing mechanism.
Updates for Reader and Acrobat can be obtained using the mechanism for checking for updates in this software, menu “Help-> Check for updates ...”.
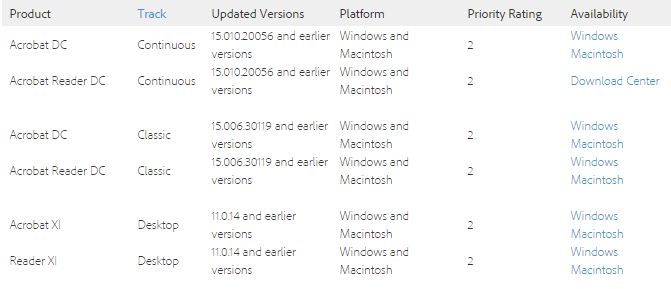
Current program versions are listed below.

be secure.

In turn, Adobe released the update APSB16-02 , which fixes 17 vulnerabilities in Reader and Acrobat products, which are used to view and create PDF files. Most of the closed vulnerabilities allow attackers to remotely execute code using a special malicious PDF file.
')
Update MS16-001 closes two vulnerabilities CVE-2016-0002 and CVE-2016-0005 in Internet Explorer 7-11 on Windows Vista +. The first vulnerability relates to the VBScript Scripting Engine (vbscript.dll) engine and allows attackers to remotely execute code using special malicious content (included in MS16-003 ). The second vulnerability allows attackers to elevate their privileges in the system to the level of the current user, bypassing the restrictions of the Low IL sandbox (Integrity Level). Critical.
Update MS16-002 fixes two vulnerabilities CVE-2016-0003 and CVE-2016-0024 in the Edge web browser on Windows 10. Both vulnerabilities allow attackers to remotely execute code in a web browser using a specially crafted web page. The only difference is that the first vulnerability is located in the web browser itself, and the second in the JavaScript engine (jscript.dll) Critical.
Update MS16-004 fixes five vulnerabilities in Office 2007+ products. Two of the five vulnerabilities can be used by attackers for remote code execution using specially crafted Office files. Two more vulnerabilities are related to the Security Feature Bypass type and are present in the SharePoint server product. One vulnerability with identifier CVE-2016-0012 allows you to bypass the ASLR defense mechanism by using an insecure library from the Visual Basic 6.0 Runtime in Office. Critical.
Update MS16-005 fixes two vulnerabilities with identifiers CVE-2016-0008 and CVE-2016-0009. They are present in the components of the Windows Vista + GUI-subsystem (win32k.sys and gdi32.dll). The first vulnerability in gdi32.dll allows attackers to bypass the ASLR defense mechanism, and the second execute the code remotely in the system when visiting a malicious website. Critical.
The MS16-006 update fixes the RCE vulnerability CVE-2016-0034 in Silverlight 5 environment. Using the vulnerability, attackers can remotely execute code on the user's system using the malicious Silverlight application hosted on a web resource. Critical.
Update MS16-007 fixes six different vulnerabilities in Windows Vista + components. The update affects such libraries as Advapi32.dll, Rpcrt4.dll, Qedit.dll, Ksuser.dll. Drmk.sys driver and others. One of the RCE vulnerabilities CVE-2016-0015 is present in the multimedia framework DirectShow, its operation is possible when the user opens a special malicious file. Two more RCE vulnerabilities are related to improper loading of DLL into memory (DLL Loading Remote Code Execution), their exploitation is possible under a similar scenario, while the attackers will get the rights of the current account in the system. Vulnerability CVE-2016-0019 is present in the Remote Desktop Service (RDP) component only on Windows 10 (Windows Remote Desktop Protocol Security Bypass Vulnerability). Using this vulnerability and the RDP client version less than on Windows 10, an attacker can connect to the system using an account that does not have a password, despite the default policy on the remote system to prohibit the use of such accounts for remote connection. Important.
Update MS16-008 fixes two vulnerabilities with identifiers CVE-2016-0006 and CVE-2016-0007, which can be used by attackers to elevate their privileges to a high SYSTEM level on Windows Vista +. Vulnerabilities are present in the so-called code. Windows Mount Point subsystems and are located in the OS kernel files: Winload.efi, Winload.exe, Ntdll.dll, Ntoskrnl.exe, Smss.exe, etc. To exploit the vulnerability, an attacker must run a special application on it that uses operations with such file system objects as reparse points. Important.
The MS16-010 update closes four vulnerabilities like Spoofing in Exchange Server 2013+ software. Vulnerabilities in processing Outlook Web Access (OWA) requests allow an attacker to obtain confidential information from the user by stealthily redirecting the user to a phishing resource. Important.
This patch tuesday was the latest for Windows 8 and Internet Explorer versions 7-10. At the same time, users of these versions of the web browser on the next versions of the OS will continue to receive updates until the end of the OS support.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Five use-after-free (UAC) vulnerabilities (CVE-2016-0932, CVE-2016-0934, CVE-2016-0937, CVE-2016-0940, CVE-2016-0941) were closed for Reader and Acrobat used by attackers for remote code execution using a special PDF file. 11 more vulnerabilities related to memory corruption can also be used for the same purposes.
Vulnerability CVE-2016-0943 allows you to bypass the security restrictions when using the Javascript API. The latest vulnerability, CVE-2016-0947, is present in the Adobe Download Manager and allows attackers to execute code due to an error in the implementation of the directory listing mechanism.
Updates for Reader and Acrobat can be obtained using the mechanism for checking for updates in this software, menu “Help-> Check for updates ...”.
Current program versions are listed below.


be secure.
Source: https://habr.com/ru/post/274981/
All Articles