Vulnerability in Trend Micro products allows any website to execute arbitrary Windows command
Tavis Ormandy of Google Project Zero discovered an amazing vulnerability in Trend Micro antivirus products for Windows, allowing any website a user visits to execute an arbitrary command on his machine.
Ormandy, an audit of popular anti-virus products, drew attention to one of the components of Trend Micro AV, a password manager written in JavaScript using node.js. It turned out that it opens several HTTP RPC ports, allowing you to execute arbitrary commands! This means that any website can run a script on the user's machine, which, for example, can erase all information on the disk, install another malicious program from the external network, or simply delete the same antivirus.
Digging even deeper, Ormandy found that the password manager is so bad that it allows for the theft of all passwords, even if they are encrypted.
')
At the moment, Trend Micro stated that it fixed the vulnerability, it is recommended that all users update their antivirus.

Ormandy, an audit of popular anti-virus products, drew attention to one of the components of Trend Micro AV, a password manager written in JavaScript using node.js. It turned out that it opens several HTTP RPC ports, allowing you to execute arbitrary commands! This means that any website can run a script on the user's machine, which, for example, can erase all information on the disk, install another malicious program from the external network, or simply delete the same antivirus.
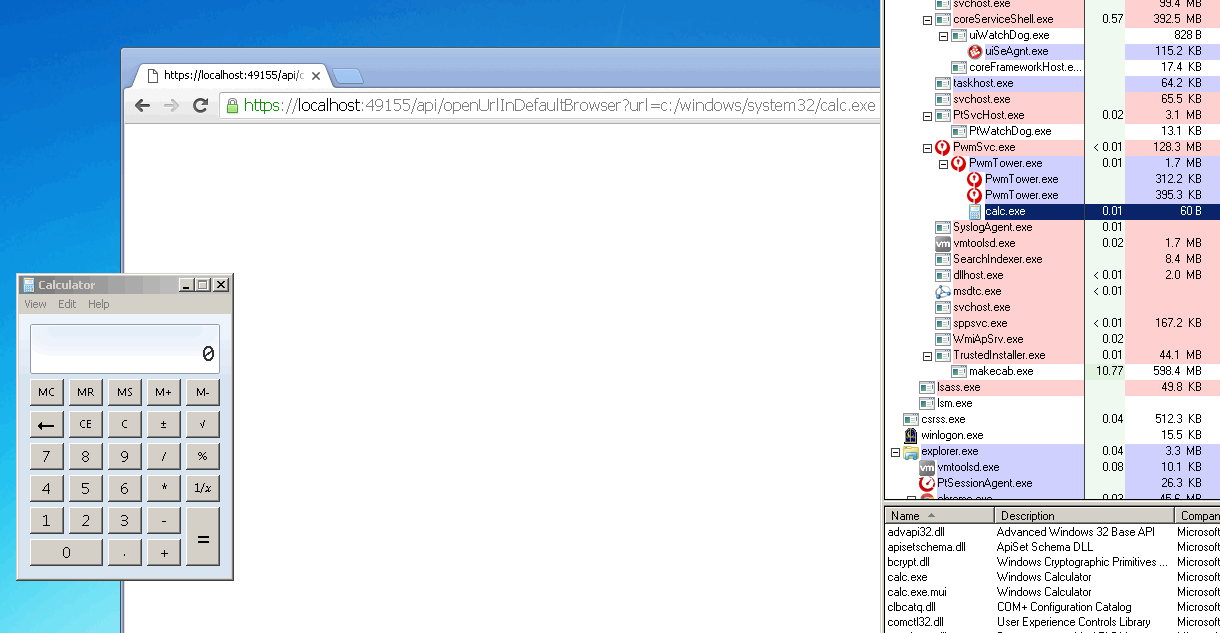
I spent about 30 seconds to realize that this allows you to execute the command, openUrlDefaultBrowser, which eventually runs ShellExecute ()
x = new XMLHttpRequest() x.open("GET", "https://localhost:49155/api/openUrlInDefaultBrowser?url=c:/windows/system32/calc.exe true); try { x.send(); } catch (e) {}; 
Digging even deeper, Ormandy found that the password manager is so bad that it allows for the theft of all passwords, even if they are encrypted.
')
At the moment, Trend Micro stated that it fixed the vulnerability, it is recommended that all users update their antivirus.
Source: https://habr.com/ru/post/274899/
All Articles