Security Week 01: Javascript Ransommer, $ 100k for a bug in Adobe Flash, an encrypted bright future
 An important event at the end of December was the Chaos Communication Congress conference. Materials from it can be found on the keyword 32c3, where 32 is the sequence number of the event, since 1984. There were quite a few interesting studies at the Hamburg event. For example, experts Felix Domke and Daniel Lange spoke in detail about the technical side of Dieselgate, including the features of the work of modern control systems of cars. And here you can see a monumental 110-page presentation on the vulnerability of railway systems, and come to the conclusion that IT is widely used in trains, a lot, everywhere in different ways, and often using standard software (Windows XP) or typical wireless communication protocols (GSM ), whose security flaws are widely known and actively exploited (fortunately, while in other places).
An important event at the end of December was the Chaos Communication Congress conference. Materials from it can be found on the keyword 32c3, where 32 is the sequence number of the event, since 1984. There were quite a few interesting studies at the Hamburg event. For example, experts Felix Domke and Daniel Lange spoke in detail about the technical side of Dieselgate, including the features of the work of modern control systems of cars. And here you can see a monumental 110-page presentation on the vulnerability of railway systems, and come to the conclusion that IT is widely used in trains, a lot, everywhere in different ways, and often using standard software (Windows XP) or typical wireless communication protocols (GSM ), whose security flaws are widely known and actively exploited (fortunately, while in other places).But the news (presentation and link to the research work inside) that unique features of the programming style leak even into the compiled code. Although this topic is rather narrowly specialized, I see something more in it: perhaps in the near future, the picture on the right will completely lose its relevance. Not because everyone will be followed by everyone, but thanks to behavioral analysis, the user can be identified by how he interacts with the site, application, or something else, just like a programmer, by how he writes the code. By the way, Apple just yesterday acquired a startup specializing in analyzing human emotions. In general, the year 2016 begins interestingly. And we continue to observe. Previous episodes are available here .
Extortionist for JavaScript with an affiliate program, potential multiplatform, preference and poetess
News Research
This news is clearly not in the category of “we all die”: well, a new extortionist has appeared, well, a little non-standard packaging. Affiliate program is also not news. The only interesting point is the use of JavaScript and the NW.js environment, which allows you to execute code not as a sandbox in the browser, but with system rights. A side feature of this approach is the large volume of the Trojan - 22 megabytes - since it includes the Chromium browser and other utilities that are completely legitimate. Emsisoft's researchers understood the code in detail, but never mentioned the attack vectors. However, according to the currently accepted practice of the division of labor between cybercrime workers, completely different people can engage in “infection”.
')
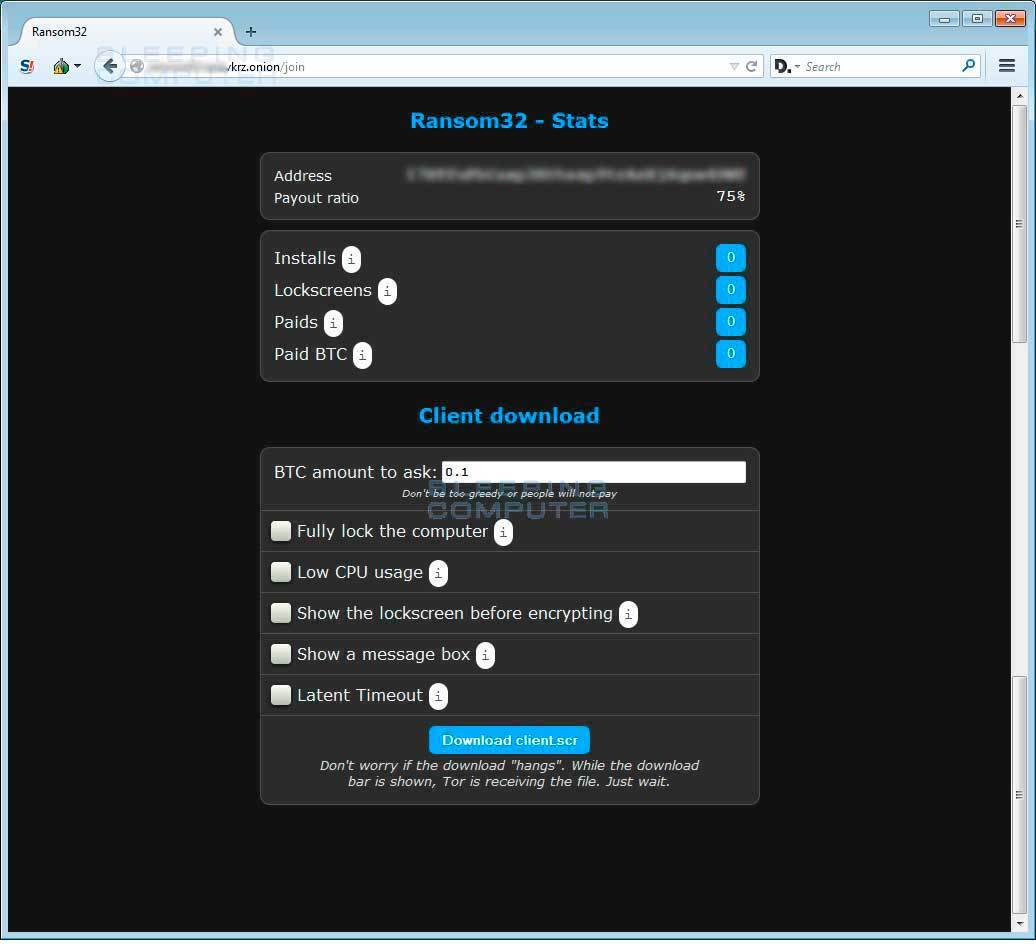
Such a non-standard approach can be compared with downloading and installing Microsoft Office for exploiting a vulnerability in this: in general, it is not the most efficient way. But interesting features of the affiliate program, organized by the authors of the Trojan. For 25% of the revenue (the Bitcoin wallet data is the only thing required during registration) who decide to go along the slippery cyber path, they are provided with a customized Trojan in which you can even set the ransom amount yourself. The results of the work are kept in the console (naturally, via Tor). In short, such an interesting example of a c2c business is from criminal to criminal. More on this (on the example of Brazil) - here .

But what the user sees as a result. Then everything is usually: the requirement of redemption, raising rates after a certain time, the ability to decrypt one file per sample, and this process is automated. As is usually the case, decrypting files due to vulnerabilities in the algorithm fails - each individual document is encrypted with its own key. It will only help the confiscation of the controlling server by law enforcement agencies with subsequent analysis of the content, as happened in the case of CoinVault .
Zerodium pays up to 100 thousand dollars for an Adobe Flash exploit
News
We already wrote about the company Zerodium - last year it announced a record reward of $ 3 million for an effective exploit for iOS. The key word here is effective, that is, it allows you to hack the device remotely, without involving the owner using any social engineering methods. In November, the company announced that the winner (one of the expected three) was found, but what exactly was found - we will not know, because of the specifics of this broker. The company uses the found holes for resale from all sides to suspicious state structures for conducting the corresponding kind of operational activity.
Zerodium’s desire to part with a decent amount is caused by changes in the Adobe Flash code. On December 21, Adobe announced the introduction of Heap Isolation, and this, in turn, made some use-after-free attacks impossible. In other words, Flash (if you, of course, updated it) has become noticeably safer. An interesting background to this innovation is that Adobe in its blog talks about the introduction of a new measure thanks to the interaction and exchange of experience with Microsoft and Google Project Zero (earlier this group presented recommendations on how to improve the security of Flash). An interesting and positive example of the interaction of experts from different companies.

And, apparently, effective enough that the "dark side" decided to fork out. By the way, last summer Adobe announced its own bug bounty program, which, however, does not provide for cash payments. Yes, and typical payments that vendors promise researchers, almost never get to the six-figure sum, announced by Zerodium and similar companies. The difference between them lies in the fact that the process of finding and publishing bugs on the good side is usually open and transparent, but what, how and to whom Zerodium pays is not known. Real amounts may well be lower. This means that the introduction of financial interest in the process of searching for bugs does not change anything - the researcher still needs to decide on the issues of the ethical-criminal plan, so to speak.
The father
News
David Chaum is a narrow-knit theorist in data encryption, network anonymity and electronic currencies. A well-known and respected member of the community, he developed the topic of information protection in the network when the network itself was not yet - one of his main works on preserving anonymity in mail correspondence published (PDF) in 1981. On January 6, Wired magazine featured an article about Chauma, the PrivaTegrity system. The system allows you to communicate on the network completely anonymously, more efficiently and safer than on existing Tor and I2P networks. Technical details were not disclosed (they are not on the Chaum website either), but for the heated debates in the community it was not necessary.
A feature of the system is an algorithm that allows depriving one of the participants of anonymity. According to Chaum, giving control over communications to one structure or state is really unsafe, and distribution of responsibility among nine “administrators” can solve the problem. This very advice of nine can bring a potential malefactor to clear water only in the event of a unanimous decision (it is assumed, apparently, that the council’s participants will be able to agree only in the case of some kind of obvious crime). Anyway, this means that in a super-secure (suppose) system, there is a backdoor by default. For this controversial part of the project, observers were not slow to be trampled down. For example :
Or so :

The Chauma initiative, therefore, is an attempt to find a compromise between the desire of ordinary users to remain anonymous and the desire of law enforcement agencies (and society as a whole) not to give criminals, terrorists and other declassed elements an invulnerable communication channel. Opinion of opponents: any originally incorporated vulnerability of the algorithm will be exploited sooner or later. You can not give access to one, and hope that no one else will not get it. Chauma even started accusing political indulgence of state structures (see Christopher Sogoyan’s quote above) - while most cryptographers are trying to prove to the state that backdoors are bad, one of the pillars of theorists gives the state a strong pro argument.

It would be interesting to see the technical details of the system (if they will ever be disclosed ever after such a “warm welcome”). So far, on the site of Chaum, one can see an excellent picture: some 25 experts who wished to remain unknown to the experts allegedly approved the concept. In general, an interesting metamorphosis continues to occur with cryptography - remaining a purely technical topic, it acquires considerable political weight. And in the future, it’s not the technologies that will determine the security of our data (everything is fine with them and without Chaum), but how the state, society, in short all the interested parties, agree among themselves.
What else happened:
An interesting vulnerability in a secure Blackphone smartphone is that data can be accessed through a communication module, which, as you know, has the highest priority in any phone, represents a state in the state and contains the devil knows what.
The states found a vulnerability in the Comcast home alarm system. The signal from the penetration sensors (2.4 GHz) turned out to be very easy to drown out - by jamming or (naturally!) With foil caps, and the system responds to such actions slowly or in no way. Quote from a Comcast representative: “Our alarm system uses the same advanced technology that complies with industry standards as other providers of similar solutions.” Yep
Holland does not approve backdoors in encryption systems. And not anyone, but the Minister of Justice!
In the Cisco XMPP client, we found a bug that can be used for the MiTM attack. Reason: the ability to force the client to transmit data in clear text, and not in a session protected by TLS.
 Antiquities:
Antiquities:"Anthrax"
Resident, infects .COM- and EXE-files, MBR of the hard drive. Files are affected as standard. The MBR is infected when the infected file is started, the continuation of the virus and the MBR sector are saved starting at address 0/0/2 (track / head / sector).
Memory is infected when booting from an infected disk. Then the virus only infects files. Intercepts int21h, contains the strings "Anthrax", "Damage, Inc".
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 105.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/274703/
All Articles