Attackers have targeted the BlackEnergy Trojan at Ukrainian energy companies
Yesterday, we presented information on cyber attacks on media companies in Ukraine and industrial facilities that used the BlackEnergy Trojan and a new component called KillDisk. KillDisk was used to destroy files on compromised computers and on disabling such systems. In addition to reviewing the capabilities of these two malicious programs, we managed to get interesting information that links cyber attacks using BlackEnergy with recent media reports about successful hacking of energy systems in western Ukraine, which led to a massive power outage.

According to media reports, on December 23, 2015, about half of the residents of Ivano-Frankivsk region (with a population of 1.4 million) in Ukraine were left without electricity for several hours. The TSN news portal indicates that the power outage was caused by a “hacker attack” that used a “virus”.
')
Using our telemetry system, we found that the incident mentioned in the media was not isolated and other energy companies of Ukraine at the same time underwent similar attacks. We also discovered that for this cyber attack, the attackers used malware, a detailed analysis of which we have already produced. This is a Trojan BlackEnergy and a new modification of its component KillDisk, mentioned in our previous study.
BlackEnergy Trojan has been used by attackers to perform various tasks over the past few years. At the well-known conference Virus Bulletin in 2014, we presented data on a series of cyber attacks against government and industrial facilities in Ukraine. The attackers used several methods to spread this malware and infect users, including, 0day, an exploit for PowerPoint's CVE-2014-4114 vulnerability. While the main targets of the attackers in 2014 were cyber espionage, a component capable of infecting SCADA ICS was also discovered for BlackEnergy, which allows BlackEnergy to target more dramatic goals.
In recent cyber attacks on the electric power companies of Ukraine, a Trojan with KillDisk functions destructive for the system was downloaded and executed on computers compromised by BlackEnergy. The link between BlackEnergy and KillDisk was first established by the CERT-UA organization in November. According to these data, some Ukrainian news companies were attacked during the local elections in this country. The report indicated that the result of a cyber attack was the destruction of a large number of video materials and other documents.
We have information about several energy companies in Ukraine (except for the company “Prikarpattyaoblenergo”), which were the targets of cyber attacks using BlackEnergy. We can confirm that this Trojan, along with the KillDisk component, was used to compromise the computers of these companies on the eve of the Catholic Christmas 2015. We also have information that BlackEnergy was used in cyber attacks on energy companies earlier in 2015, but In their case, we did not observe the use of a KillDisk component for data corruption by attackers. It can be assumed that at that moment the attackers were in the preliminary stages of preparing more substantial operations.
The Microsoft Office files containing malicious macros were used as a vector for infecting users in the cyber attacks mentioned above. Such methods of infection were also used by other attackers, for example, the Dridex gang and other attackers in 2015.
In this case, the attack scenario is quite simple, the alleged victim receives a phishing email, which contains a malicious document as an attachment. Ukrainian security company CyS Centrum has published two screenshots of such letters, which were used to deliver BlackEnergy droppers. The attackers used special fake addresses as the sender's address, which were similar to the addresses of the Ukrainian parliament - Rada. A phishing document sent by cybercriminals contains text that urges the user to launch a malicious macro embedded in it. Such a case is an example of the delivery of malware to a victim using social engineering, instead of exploiting any vulnerabilities in the software. After the macro is executed, the user is infected with a modification of BlackEnergy Lite .
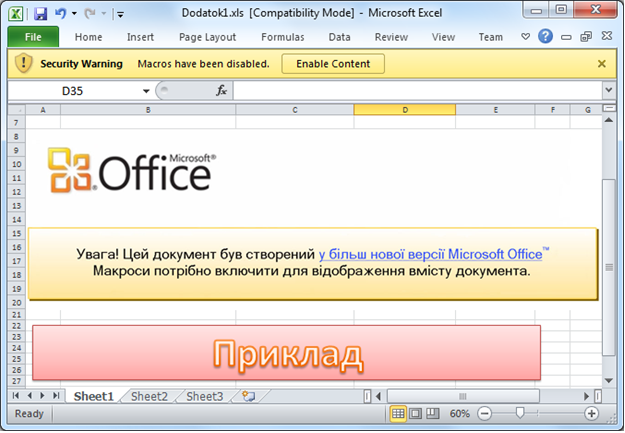
Fig. An example of a malicious document.
As indicated in our presentation of VirusBulletin, BlackEnergy is a modular trojan and is used by attackers to deploy various downloadable components to perform the required tasks. As we have already indicated, the Win32 / KillDisk component also loaded BlackEnergy and was found on computers it had compromised in the cyber attacks mentioned above.
The KillDisk malware specializes in the destruction of files in the system, as well as the corruption of system files, which causes the OS to become inoperable. Some of the KillDisk modifications that we found in energy companies contained in their structure additional capabilities for sabotaging industrial systems. The first such possibility is the installation of a timeout or delay on the triggering of its main destructive mechanism. The second possibility is the completion of two non-standard processes with the names of komut.exe and sec_service.exe. The name of the second process may refer to software called ELTIMA Serial to Ethernet Connector or ASEM Ubiquity, the ICS industrial software platform. In case of detection of the activity of processes in the system, the malware will terminate them, and also destroy their executable files on the disk.
Conclusion
Malware with destructive functions is not a new phenomenon. Despite the fact that some of the early viruses contained such possibilities, they were used for entertainment purposes, unlike modern cybercriminals, who use them to achieve various kinds of goals, from sabotage and hacktivism to cyber espionage. Another infamous example of such malware is Flamer (aka Flame or sKyWIper). Another destructive malware called Destover was previously used in cyber attacks on Sony Pictures. It should be mentioned once again that this kind of destructive malware is not unique and if we take into account the vague naming scheme of malware, we should not associate completely different incidents only by the names of their detections (for example, the name Wiper or its derivatives).
In 2014, BlackEnergy used a more outdated modification of the destructive component called dstr, which we described in a previous post. There are differences between KillDisk and dstr, which indicate that the latter was used as a tool for the complete destruction of data in the system.
Our analysis of the KillDisk component, which was discovered on compromised computers of energy companies in Ukraine, indicates its theoretical focus on disabling critical industrial systems. However, there is another explanation for this. BlackEnergy itself, like the SSH backdoor, which was also used in these malicious campaigns and was described by us in a previous post, gives attackers remote access to the compromised system. After successfully infecting the system, the attackers also, theoretically, can manually use the destructive component to damage the system. In this case, KillDisk can be used by them as a component, with the help of which it is possible to make the recovery of a damaged system a very time-consuming process. With a high degree of probability, we assume that it was the above set of malicious programs that was used to damage the energy infrastructure in the Ivano-Frankivsk region.
Although in Ukraine Christmas is usually not celebrated on December 24 and 25, cybercriminals have chosen this particular time of year to turn off the light to several hundred thousand people. Attackers are also lucky that this malware was not detected in the system in a timely manner.
Other technical information about the incident can be found on the SANS Industrial Control Systems website. Indicators of compromise (IoC) can be found in our previous post .

According to media reports, on December 23, 2015, about half of the residents of Ivano-Frankivsk region (with a population of 1.4 million) in Ukraine were left without electricity for several hours. The TSN news portal indicates that the power outage was caused by a “hacker attack” that used a “virus”.
')
Using our telemetry system, we found that the incident mentioned in the media was not isolated and other energy companies of Ukraine at the same time underwent similar attacks. We also discovered that for this cyber attack, the attackers used malware, a detailed analysis of which we have already produced. This is a Trojan BlackEnergy and a new modification of its component KillDisk, mentioned in our previous study.
BlackEnergy Trojan has been used by attackers to perform various tasks over the past few years. At the well-known conference Virus Bulletin in 2014, we presented data on a series of cyber attacks against government and industrial facilities in Ukraine. The attackers used several methods to spread this malware and infect users, including, 0day, an exploit for PowerPoint's CVE-2014-4114 vulnerability. While the main targets of the attackers in 2014 were cyber espionage, a component capable of infecting SCADA ICS was also discovered for BlackEnergy, which allows BlackEnergy to target more dramatic goals.
In recent cyber attacks on the electric power companies of Ukraine, a Trojan with KillDisk functions destructive for the system was downloaded and executed on computers compromised by BlackEnergy. The link between BlackEnergy and KillDisk was first established by the CERT-UA organization in November. According to these data, some Ukrainian news companies were attacked during the local elections in this country. The report indicated that the result of a cyber attack was the destruction of a large number of video materials and other documents.
We have information about several energy companies in Ukraine (except for the company “Prikarpattyaoblenergo”), which were the targets of cyber attacks using BlackEnergy. We can confirm that this Trojan, along with the KillDisk component, was used to compromise the computers of these companies on the eve of the Catholic Christmas 2015. We also have information that BlackEnergy was used in cyber attacks on energy companies earlier in 2015, but In their case, we did not observe the use of a KillDisk component for data corruption by attackers. It can be assumed that at that moment the attackers were in the preliminary stages of preparing more substantial operations.
The Microsoft Office files containing malicious macros were used as a vector for infecting users in the cyber attacks mentioned above. Such methods of infection were also used by other attackers, for example, the Dridex gang and other attackers in 2015.
In this case, the attack scenario is quite simple, the alleged victim receives a phishing email, which contains a malicious document as an attachment. Ukrainian security company CyS Centrum has published two screenshots of such letters, which were used to deliver BlackEnergy droppers. The attackers used special fake addresses as the sender's address, which were similar to the addresses of the Ukrainian parliament - Rada. A phishing document sent by cybercriminals contains text that urges the user to launch a malicious macro embedded in it. Such a case is an example of the delivery of malware to a victim using social engineering, instead of exploiting any vulnerabilities in the software. After the macro is executed, the user is infected with a modification of BlackEnergy Lite .

Fig. An example of a malicious document.
As indicated in our presentation of VirusBulletin, BlackEnergy is a modular trojan and is used by attackers to deploy various downloadable components to perform the required tasks. As we have already indicated, the Win32 / KillDisk component also loaded BlackEnergy and was found on computers it had compromised in the cyber attacks mentioned above.
The KillDisk malware specializes in the destruction of files in the system, as well as the corruption of system files, which causes the OS to become inoperable. Some of the KillDisk modifications that we found in energy companies contained in their structure additional capabilities for sabotaging industrial systems. The first such possibility is the installation of a timeout or delay on the triggering of its main destructive mechanism. The second possibility is the completion of two non-standard processes with the names of komut.exe and sec_service.exe. The name of the second process may refer to software called ELTIMA Serial to Ethernet Connector or ASEM Ubiquity, the ICS industrial software platform. In case of detection of the activity of processes in the system, the malware will terminate them, and also destroy their executable files on the disk.
Conclusion
Malware with destructive functions is not a new phenomenon. Despite the fact that some of the early viruses contained such possibilities, they were used for entertainment purposes, unlike modern cybercriminals, who use them to achieve various kinds of goals, from sabotage and hacktivism to cyber espionage. Another infamous example of such malware is Flamer (aka Flame or sKyWIper). Another destructive malware called Destover was previously used in cyber attacks on Sony Pictures. It should be mentioned once again that this kind of destructive malware is not unique and if we take into account the vague naming scheme of malware, we should not associate completely different incidents only by the names of their detections (for example, the name Wiper or its derivatives).
In 2014, BlackEnergy used a more outdated modification of the destructive component called dstr, which we described in a previous post. There are differences between KillDisk and dstr, which indicate that the latter was used as a tool for the complete destruction of data in the system.
Our analysis of the KillDisk component, which was discovered on compromised computers of energy companies in Ukraine, indicates its theoretical focus on disabling critical industrial systems. However, there is another explanation for this. BlackEnergy itself, like the SSH backdoor, which was also used in these malicious campaigns and was described by us in a previous post, gives attackers remote access to the compromised system. After successfully infecting the system, the attackers also, theoretically, can manually use the destructive component to damage the system. In this case, KillDisk can be used by them as a component, with the help of which it is possible to make the recovery of a damaged system a very time-consuming process. With a high degree of probability, we assume that it was the above set of malicious programs that was used to damage the energy infrastructure in the Ivano-Frankivsk region.
Although in Ukraine Christmas is usually not celebrated on December 24 and 25, cybercriminals have chosen this particular time of year to turn off the light to several hundred thousand people. Attackers are also lucky that this malware was not detected in the system in a timely manner.
Other technical information about the incident can be found on the SANS Industrial Control Systems website. Indicators of compromise (IoC) can be found in our previous post .
Source: https://habr.com/ru/post/274503/
All Articles