BlackEnergy Trojan is used in cyber attacks on media and industrial facilities in Ukraine
BlackEnergy is a family of malware that has been active since 2007. In 2014, the Trojan continued its activity and returned to a new modification ( 1 , 2 ). BlackEnergy was also active in 2015 and was used by cybercriminals to attack users. Our analysts have recorded a new activity of this trojan, which was used against the media companies of Ukraine and the power industry enterprises. Using the Trojan, attackers delivered a special component KillDisk, specializing in the destruction of files on the disk, to the victims' computers.
In addition to BlackEnergy, cybergroup has used another tool to gain access to infected systems. It is an SSH backdoor. We continue to monitor the activities of BlackEnergy and record the new features of this trojan. For more information or to provide one, send us an email at threatintel@eset.com.
')
After its launch in the system, the dropper of the BlackEnergy Lite modification allows the operator to check the infected system for compliance with the necessary criteria. This allows attackers to determine the actual importance of the infected system. A more precise and detailed mechanism of system infection by BlackEnergy can be found in our presentation Virus Bulletin and F-Secure document .
BlackEnergy stores XML configuration data inside a dynamic payload DLL.

Fig. Sample BlackEnergy configuration data in 2015
In addition to the list of addresses of C & C servers, the BlackEnergy configuration data contains the value of the build_id parameter. The value of this parameter is a unique text string used to identify the bot-infected system. The combination of letters and numbers used by cybercriminals can sometimes reveal information about a malicious campaign and its goals. Below is a list of such identifiers that we observed in 2015.
We can assume that some of the identifiers have a special meaning. For example, the identifier string 2015telsmi may include the abbreviation SMI (Mass Media), 2015en may mean Energy (energy), and kiev_o is obvious Kiev.
In 2014, some variants of the BlackEnergy trojan contained a plugin called dstr , designed to perform destructive actions on an infected system. In 2015, the attackers began to use BlackEnergy for a new plugin to perform destructive actions in the system. It is detected by ESET antivirus products like Win32 / KillDisk.NBB, Win32 / KillDisk.NBC, and Win32 / KillDisk.NBD. The main task of this component is to corrupt files stored on disk: it overwrites documents with arbitrary data and disables the OS.
The first known case of detection of the KillDisk component was documented by the CERT-UA organization in November 2015. At the same time, a number of media outlets were subjected to cyber attacks during local elections in Ukraine in 2015. The report argues that the cyber attack resulted in the destruction of a large number of videos and other documents compromised computers.
It should be noted that the Win32 / KillDisk.NBB module used against the media is primarily focused on the destruction of documents and other file types. The malware file contains a long list of file extensions that it is trying to overwrite and delete. The full list contains more than 4 thousand file extensions.
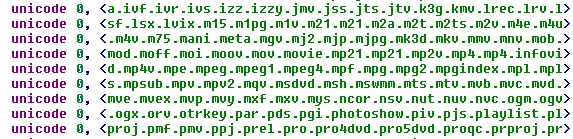
Fig. Part of the list of file extensions that KillDisk.NBB is intended to destroy.
The KillDisk component, which was used in cyber attacks on energy companies of Ukraine, is different from the previous plug-in (2014). Our analysis of the samples showed that the main changes in the new module were as follows.
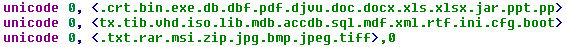
Fig. The list of file extensions that a new modification of the KillDisk component aims to destroy.
In addition to deleting user files, KillDisk specializes in corruption of system files, which leads to system malfunction and the impossibility of its subsequent download. One of the KillDisk options, which was found in companies specializing in the supply of electricity, contains additional possibilities for sabotaging industrial systems. After its launch in the system, such a modification of the KillDisk component searches for and terminates two non-standard processes with the following names: komut.exe and sec_service.exe.
We could not find any information about the name of the first process (komut.exe). The name of the second process may be related to software called ASEM Ubiquity. It is a software platform that is often used in industrial control systems (ICS). Another option is that it may refer to the ELTIMA Serial to Ethernet Connector. In case of detection of activity in the system of these processes, the malicious program not only terminates them, but also overwrites their executable files with arbitrary data.
In addition to the BlackEnergy component listed above, we discovered another sample of malware that was used by attackers in this campaign. In the course of our research of one of the compromised servers, an application was discovered on it that seemed, at first glance, a legitimate SSH server called Dropbear SSH .
To start the SSH server, the attackers created a file on VBS with the following contents.
As you can see, the SSH server is configured to accept connections to port number 6789. By launching such a server on a compromised network, attackers can return to it at any time when they need it. However, for some reason, this is not enough for them. The server executable also contains the backdoor code.

Fig. Authentication function with hard-wired password in SSH North.
As you can see in the screenshot above, this version of Dropbear SSH will successfully authenticate the user when they enter the fixed password “passDs5Bu9Te7”. The same applies to authentication by a pair of keys - the server file contains in its body a fixed public key and allows for successful login upon presentation of the private key.
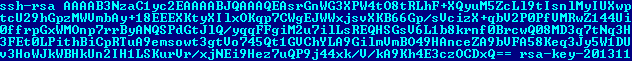
Fig. Public RSA key in SSH server executable.
ESET antivirus products detect this SSH server with backdoor functionality as Win32 / SSHBearDoor.A.
Indicators of compromise
IP addresses of BlackEnergy C & C servers:
5.149.254.114
5.9.32.230
31.210.111.154
88.198.25.92
146.0.74.7
188.40.8.72
Document ID of the SHA-1 XLS document with a malicious macro:
AA67CA4FB712374F5301D1D2BAB0AC66107A4DF1
BlackEnergy Lite Dropper SHA-1 ID:
4C424D5C8CFEDF8D2164B9F833F7C631F94C5A4C
BlackEnergy Big Dropper's SHA-1 ID:
896FCACFF6310BBE5335677E99E4C3D370F73D96
BlackEnergy Drivers SHA-1 Identifiers:
069163E1FB606C6178E23066E0AC7B7F0E18506B
0B4BE96ADA3B54453BD37130087618EA90168D72
1A716BF5532C13FA0DC407D00ACDC4A457FA87CD
1A86F7EF10849DA7D36CA27D0C9B1D686768E177
1CBE4E22B034EE8EA8567E3F8EB9426B30D4AFFE
20901CC767055F29CA3B676550164A66F85E2A42
2C1260FD5CEAEF3B5CB11D702EDC4CDD1610C2ED
2D805BCA41AA0EB1FC7EC3BD944EFD7DBA686AE1
4BC2BBD1809C8B66EECD7C28AC319B948577DE7B
502BD7662A553397BBDCFA27B585D740A20C49FC
672F5F332A6303080D807200A7F258C8155C54AF
84248BC0AC1F2F42A41CFFFA70B21B347DDC70E9
A427B264C1BD2712D1178912753BAC051A7A2F6C
A9ACA6F541555619159640D3EBC570CDCDCE0A0D
B0 excav77E002C510E7AB11B996A1CD8FE8FDADA0C
BD87CF5B66E36506F1D6774FD40C2C92A196E278
BE319672A87D0DD1F055AD1221B6FFD8C226A6E2
C7E919622D6D8EA2491ED392A0F8457E4483EAE9
CD07036416B3A344A34F4571CE6A1DF3CBB5783F
D91E6BB091551E773B3933BE5985F91711D6AC3B
E1C2B28E6A35AEADB508C60A9D09AB7B1041AFB8
E40F0D402FDCBA6DD7467C1366D040B02A44628C
E5A2204F085C07250DA07D71CB4E48769328D7DC
KillDisk component SHA-1 identifier:
16F44FAC7E8BC94ECCD7AD9692E6665EF540EEC4
8AD6F88C5813C2B4CD7ABAB1D6C056D95D6AC569
6D6BA221DA5B1AE1E910BBEAA07BD44AFF26A7C0
F3E41EB94C4D72A98CD743BBB02D248F510AD925
SHA-1 Trojan ID VBS / Agent.AD:
72D0B326410E1D0705281FDE83CB7C33C67BC8CA
Win32 / SSHBearDoor.A Trojan SHA-1 ID:
166D71C63D0EB609C4F77499112965DB7D9A51BB

In addition to BlackEnergy, cybergroup has used another tool to gain access to infected systems. It is an SSH backdoor. We continue to monitor the activities of BlackEnergy and record the new features of this trojan. For more information or to provide one, send us an email at threatintel@eset.com.
')
After its launch in the system, the dropper of the BlackEnergy Lite modification allows the operator to check the infected system for compliance with the necessary criteria. This allows attackers to determine the actual importance of the infected system. A more precise and detailed mechanism of system infection by BlackEnergy can be found in our presentation Virus Bulletin and F-Secure document .
BlackEnergy stores XML configuration data inside a dynamic payload DLL.

Fig. Sample BlackEnergy configuration data in 2015
In addition to the list of addresses of C & C servers, the BlackEnergy configuration data contains the value of the build_id parameter. The value of this parameter is a unique text string used to identify the bot-infected system. The combination of letters and numbers used by cybercriminals can sometimes reveal information about a malicious campaign and its goals. Below is a list of such identifiers that we observed in 2015.
- 2015en
- khm10
- khelm
- 2015telsmi
- 2015ts
- 2015stb
- kiev_o
- brd2015
- 11131526kbp
- 02260517ee
- 03150618aaa
- 11131526trk
We can assume that some of the identifiers have a special meaning. For example, the identifier string 2015telsmi may include the abbreviation SMI (Mass Media), 2015en may mean Energy (energy), and kiev_o is obvious Kiev.
In 2014, some variants of the BlackEnergy trojan contained a plugin called dstr , designed to perform destructive actions on an infected system. In 2015, the attackers began to use BlackEnergy for a new plugin to perform destructive actions in the system. It is detected by ESET antivirus products like Win32 / KillDisk.NBB, Win32 / KillDisk.NBC, and Win32 / KillDisk.NBD. The main task of this component is to corrupt files stored on disk: it overwrites documents with arbitrary data and disables the OS.
The first known case of detection of the KillDisk component was documented by the CERT-UA organization in November 2015. At the same time, a number of media outlets were subjected to cyber attacks during local elections in Ukraine in 2015. The report argues that the cyber attack resulted in the destruction of a large number of videos and other documents compromised computers.
It should be noted that the Win32 / KillDisk.NBB module used against the media is primarily focused on the destruction of documents and other file types. The malware file contains a long list of file extensions that it is trying to overwrite and delete. The full list contains more than 4 thousand file extensions.

Fig. Part of the list of file extensions that KillDisk.NBB is intended to destroy.
The KillDisk component, which was used in cyber attacks on energy companies of Ukraine, is different from the previous plug-in (2014). Our analysis of the samples showed that the main changes in the new module were as follows.
- The new modification can take on the command line argument, which allows you to specify the delay time for the launch of the payload with a destructive function.
- Specializes in deleting the following Windows event logs: applications, security, installation, system.
- To a lesser extent, focused on the removal of documents: the list of extensions is limited to 35 elements.

Fig. The list of file extensions that a new modification of the KillDisk component aims to destroy.
In addition to deleting user files, KillDisk specializes in corruption of system files, which leads to system malfunction and the impossibility of its subsequent download. One of the KillDisk options, which was found in companies specializing in the supply of electricity, contains additional possibilities for sabotaging industrial systems. After its launch in the system, such a modification of the KillDisk component searches for and terminates two non-standard processes with the following names: komut.exe and sec_service.exe.
We could not find any information about the name of the first process (komut.exe). The name of the second process may be related to software called ASEM Ubiquity. It is a software platform that is often used in industrial control systems (ICS). Another option is that it may refer to the ELTIMA Serial to Ethernet Connector. In case of detection of activity in the system of these processes, the malicious program not only terminates them, but also overwrites their executable files with arbitrary data.
In addition to the BlackEnergy component listed above, we discovered another sample of malware that was used by attackers in this campaign. In the course of our research of one of the compromised servers, an application was discovered on it that seemed, at first glance, a legitimate SSH server called Dropbear SSH .
To start the SSH server, the attackers created a file on VBS with the following contents.
Set WshShell = CreateObject (“WScript.Shell”)
WshShell.CurrentDirectory = “C: \ WINDOWS \ TEMP \ Dropbear \”
WshShell.Run “dropbear.exe -r rsa -d dss -a -p 6789 ″, 0, false
As you can see, the SSH server is configured to accept connections to port number 6789. By launching such a server on a compromised network, attackers can return to it at any time when they need it. However, for some reason, this is not enough for them. The server executable also contains the backdoor code.

Fig. Authentication function with hard-wired password in SSH North.
As you can see in the screenshot above, this version of Dropbear SSH will successfully authenticate the user when they enter the fixed password “passDs5Bu9Te7”. The same applies to authentication by a pair of keys - the server file contains in its body a fixed public key and allows for successful login upon presentation of the private key.

Fig. Public RSA key in SSH server executable.
ESET antivirus products detect this SSH server with backdoor functionality as Win32 / SSHBearDoor.A.
Indicators of compromise
IP addresses of BlackEnergy C & C servers:
5.149.254.114
5.9.32.230
31.210.111.154
88.198.25.92
146.0.74.7
188.40.8.72
Document ID of the SHA-1 XLS document with a malicious macro:
AA67CA4FB712374F5301D1D2BAB0AC66107A4DF1
BlackEnergy Lite Dropper SHA-1 ID:
4C424D5C8CFEDF8D2164B9F833F7C631F94C5A4C
BlackEnergy Big Dropper's SHA-1 ID:
896FCACFF6310BBE5335677E99E4C3D370F73D96
BlackEnergy Drivers SHA-1 Identifiers:
069163E1FB606C6178E23066E0AC7B7F0E18506B
0B4BE96ADA3B54453BD37130087618EA90168D72
1A716BF5532C13FA0DC407D00ACDC4A457FA87CD
1A86F7EF10849DA7D36CA27D0C9B1D686768E177
1CBE4E22B034EE8EA8567E3F8EB9426B30D4AFFE
20901CC767055F29CA3B676550164A66F85E2A42
2C1260FD5CEAEF3B5CB11D702EDC4CDD1610C2ED
2D805BCA41AA0EB1FC7EC3BD944EFD7DBA686AE1
4BC2BBD1809C8B66EECD7C28AC319B948577DE7B
502BD7662A553397BBDCFA27B585D740A20C49FC
672F5F332A6303080D807200A7F258C8155C54AF
84248BC0AC1F2F42A41CFFFA70B21B347DDC70E9
A427B264C1BD2712D1178912753BAC051A7A2F6C
A9ACA6F541555619159640D3EBC570CDCDCE0A0D
B0 excav77E002C510E7AB11B996A1CD8FE8FDADA0C
BD87CF5B66E36506F1D6774FD40C2C92A196E278
BE319672A87D0DD1F055AD1221B6FFD8C226A6E2
C7E919622D6D8EA2491ED392A0F8457E4483EAE9
CD07036416B3A344A34F4571CE6A1DF3CBB5783F
D91E6BB091551E773B3933BE5985F91711D6AC3B
E1C2B28E6A35AEADB508C60A9D09AB7B1041AFB8
E40F0D402FDCBA6DD7467C1366D040B02A44628C
E5A2204F085C07250DA07D71CB4E48769328D7DC
KillDisk component SHA-1 identifier:
16F44FAC7E8BC94ECCD7AD9692E6665EF540EEC4
8AD6F88C5813C2B4CD7ABAB1D6C056D95D6AC569
6D6BA221DA5B1AE1E910BBEAA07BD44AFF26A7C0
F3E41EB94C4D72A98CD743BBB02D248F510AD925
SHA-1 Trojan ID VBS / Agent.AD:
72D0B326410E1D0705281FDE83CB7C33C67BC8CA
Win32 / SSHBearDoor.A Trojan SHA-1 ID:
166D71C63D0EB609C4F77499112965DB7D9A51BB
Source: https://habr.com/ru/post/274469/
All Articles