Trojan-Dropper.Win32.Agent.rek: "legal" rootkit
This note describes the driver that is loaded by the virus described in the previous section . The driver works at the kernel level of the operating system, and provides a “privileged” cover for the main functionality of the Trojan, which works in user mode (the authors name of the component is winnt32.dll. For more information, see habrahabr.ru/blog/virus/43787.html ).
Short description.
The program is an nt-driver (also known as legacy drivers, that is, not associated with any physical device). Is a rootkit: using the mechanisms of the OS kernel, it deprives other programs of access to certain files and registry keys.
Detected by Kaspersky as Trojan-Dropper.Win32.Agent.rek . The size is 27,548 bytes.
File system
Using the IoRegisterFsRegistrationChange kernel function, the driver signs up to receive a file system enable / disable event. That is, the OS itself notifies the driver, and it also passes it the DEVICE_OBJECT structure, which describes the “device” of the file system and its driver. A “file system device” is, roughly speaking, the way in which a user sees data on a disk organized as folders and files.
In the DEVICE_OBJECT structure that describes the device, the driver replaces the IRP_MJ_CREATE request handler with its own. The IRP_MJ_CREATE request is generated from within NtCreateFile when the file is opened. The new handler compares the requested name with the file name of the driver itself (which is set by the dropper in the form of Wwwdd.sys, for example Jer24.sys), and, in case of coincidence, returns the error code STATUS_ACCESS_DENIED.
')
Registry keys
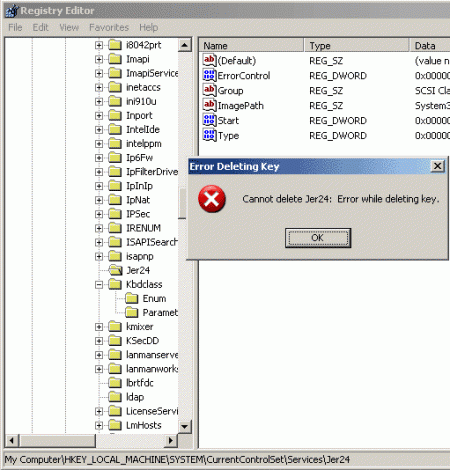
Accessing registry keys is no less legal: using the CmRegisterCallback function, the driver signs up for notification of all registry entries. Is it worth talking about how the computer starts to slow down?
When accessing registry keys:
driver returns error code STATUS_ACCESS_DENIED.
Slides
Prevent file deletion:
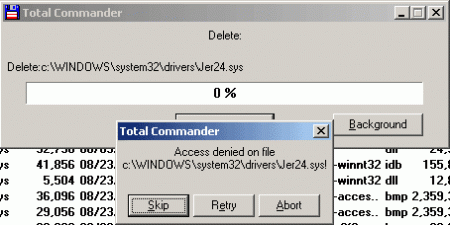
The ban on deleting the registry key:
Here the system sends the CDFS information to the rootkit:
Conclusion.
In the invisible anti-virus viruses, when everything is intercepted and intercepted, the method used by this rootkit is legal , and therefore the most dangerous. From my big bell tower, I can assume that it’s impossible to remove such a hook in practice. Or intercept the actual registration procedures for such notifications (such as CmRegisterCallback), prohibiting calling it without getting caught.
On the other hand, the line separating viruses and antiviruses is getting thinner and the territory is barely noticeable. They use the same mechanisms to hide data or track the work of ordinary programs. And by the way, the steps to this are done more by the dark side.
Short description.
The program is an nt-driver (also known as legacy drivers, that is, not associated with any physical device). Is a rootkit: using the mechanisms of the OS kernel, it deprives other programs of access to certain files and registry keys.
Detected by Kaspersky as Trojan-Dropper.Win32.Agent.rek . The size is 27,548 bytes.
Lyrical omission . A “regular” rootkit can use flaws in the OS implementation to hide objects: files, network connections, and so on down to the hard disk sectors. For this, in the simplest case, the system call is intercepted. A system call is essentially a function call, and a function call is the transfer of control to a specified address. The rootkit writes down its code at this address, which transforms the result of the original function. For example, it checks if someone is trying to open a file with the body of a virus, and returns some error code, for example, “access is denied”.The rootkit intercepts requests from the registry and files using the legal methods of the OS itself.
File system
Using the IoRegisterFsRegistrationChange kernel function, the driver signs up to receive a file system enable / disable event. That is, the OS itself notifies the driver, and it also passes it the DEVICE_OBJECT structure, which describes the “device” of the file system and its driver. A “file system device” is, roughly speaking, the way in which a user sees data on a disk organized as folders and files.
The reference book says: The system registers or unregisters itself.
In the DEVICE_OBJECT structure that describes the device, the driver replaces the IRP_MJ_CREATE request handler with its own. The IRP_MJ_CREATE request is generated from within NtCreateFile when the file is opened. The new handler compares the requested name with the file name of the driver itself (which is set by the dropper in the form of Wwwdd.sys, for example Jer24.sys), and, in case of coincidence, returns the error code STATUS_ACCESS_DENIED.
')
Registry keys
Accessing registry keys is no less legal: using the CmRegisterCallback function, the driver signs up for notification of all registry entries. Is it worth talking about how the computer starts to slow down?
A driver calls a registry call register to register a registry call register.
When accessing registry keys:
HKLM \ System \ CurrentControlSet \ Sevices \ DRIVER-NAME
HKLM \ System \ ControlSet001 \ Sevices \ DRIVER-NAME
HKLM \ System \ ControlSet002 \ Sevices \ DRIVER-NAME
HKLM \ System \ CurrentControlSet \ Control \ SafeBoot \ Minimal \ DRIVER-NAME
HKLM \ System \ CurrentControlSet \ Control \ SafeBoot \ Network \ DRIVER-NAME
HKLM \ System \ ControlSet001 \ Control \ SafeBoot \ Minimal \ DRIVER-NAME
HKLM \ System \ ControlSet001 \ Control \ SafeBoot \ Minimal \ DRIVER-NAME
HKLM \ System \ ControlSet002 \ Control \ SafeBoot \ Network \ DRIVER-NAME
HKLM \ System \ ControlSet002 \ Control \ SafeBoot \ Network \ DRIVER-NAME
driver returns error code STATUS_ACCESS_DENIED.
Slides
Prevent file deletion:

The ban on deleting the registry key:

Here the system sends the CDFS information to the rootkit:
kd> kb
ChildEBP RetAddr Args to Child
f9dfbc10 80568d01 818158b8 00000001 818cff38 Qvk71 + 0x1970
f9dfbc2c f9d3d10b 818cff38 f9d3d970 f9dfbc7c nt! IoRegisterFsRegistrationChange + 0xab
f9dfbc3c f9d3cdb0 818cff38 00000000 00000000 Qvk71 + 0x110b
f9dfbc7c 805757dc 818cff38 815dd000 00000000 Qvk71 + 0xdb0
f9dfbd4c 805758eb 000005b8 00000001 00000000 nt! IopLoadDriver + 0x66c
f9dfbd74 80533fe6 000005b8 00000000 819ca3c8 nt! IopLoadUnloadDriver + 0x45
f9dfbdac 805c4cce f7e48cf4 00000000 00000000 nt! ExpWorkerThread + 0x100
f9dfbddc 805411c2 80533ee6 00000001 00000000 nt! PspSystemThreadStartup + 0x34
00000000 00000000 00000000 00000000 00000000 nt! KiThreadStartup + 0x16
kd> dt -r1 _DEVICE_OBJECT poi (esp + 4)
nt! _DEVICE_OBJECT
+ 0x000 Type: 3
+ 0x002 Size: 0xb8
+ 0x004 ReferenceCount: 1
+ 0x008 DriverObject: 0x817eba20 _DRIVER_OBJECT
+ 0x000 Type: 4
+ 0x002 Size: 168
+ 0x004 DeviceObject: 0x8172e020 _DEVICE_OBJECT
+ 0x008 Flags: 0x92
+ 0x00c DriverStart: 0xf9c0c000
+ 0x010 DriverSize: 0xf900
+ 0x014 DriverSection: 0x818c9960
+ 0x018 DriverExtension: 0x817ebac8 _DRIVER_EXTENSION
+ 0x01c DriverName: _UNICODE_STRING "\ FileSystem \ Cdfs"
+ 0x024 HardwareDatabase: 0x8066ecd8 _UNICODE_STRING "\ REGISTRY \ MACHINE \ HARDWARE \ DESCRIPTION \ SYSTEM"
+ 0x028 FastIoDispatch: 0xf9c0e400 _FAST_IO_DISPATCH
+ 0x02c DriverInit: 0xf9c19a85 long Cdfs! GsDriverEntry + 0
+ 0x030 DriverStartIo: (null)
+ 0x034 DriverUnload: 0xf9c0fca5 void Cdfs! CdUnload + 0
+ 0x038 MajorFunction: [28] 0xf9c0c400 long Cdfs! CdFsdDispatch + 0
+ 0x00c NextDevice: (null)
+ 0x010 AttachedDevice: (null)
+ 0x014 CurrentIrp: (null)
+ 0x018 Timer: (null)
+ 0x01c Flags: 0x10840
+ 0x020 Characteristics: 0
+ 0x024 Vpb: (null)
+ 0x028 DeviceExtension: (null)
+ 0x02c DeviceType: 3
+ 0x030 StackSize: 1 ''
+ 0x034 Queue: __unnamed
+ 0x05c AlignmentRequirement: 0
+ 0x060 DeviceQueue: _KDEVICE_QUEUE
+ 0x074 Dpc: _KDPC
+ 0x094 ActiveThreadCount: 0
+ 0x098 SecurityDescriptor: 0xe139df00
+ 0x09c DeviceLock: _KEVENT
+ 0x0ac SectorSize: 0x800
+ 0x0ae Spare1: 0
+ 0x0b0 DeviceObjectExtension: 0x81815970 _DEVOBJ_EXTENSION
+ 0x0b4 Reserved: (null) Conclusion.
In the invisible anti-virus viruses, when everything is intercepted and intercepted, the method used by this rootkit is legal , and therefore the most dangerous. From my big bell tower, I can assume that it’s impossible to remove such a hook in practice. Or intercept the actual registration procedures for such notifications (such as CmRegisterCallback), prohibiting calling it without getting caught.
On the other hand, the line separating viruses and antiviruses is getting thinner and the territory is barely noticeable. They use the same mechanisms to hide data or track the work of ordinary programs. And by the way, the steps to this are done more by the dark side.
Source: https://habr.com/ru/post/27444/
All Articles