Security of web resources of banks of Russia

In our company, we constantly conduct various studies (a list ), choosing an interesting topic for us and as a result - presenting the public with pdf of the results.
This article is an article from the category of such studies. When conducting security analysis work, we usually provide very similar (common to all) tips that follow little, some best practices that either simply increase the overall security level of the system (for example, use CSP) or really prevent an attack.
Introduction
As you know, the level of system security is determined by the reliability of its weakest node. In practice, after conducting a security analysis, based on the list of found vulnerabilities, one gap or a whole chain is selected and the most problematic link is identified. We can immediately say that a properly configured system can often offset the risks of an existing vulnerability. During the study, we found out what potential attack vectors could be accessible to attackers. For example, is it easy to steal user session data in the presence of cross-site scripting vulnerabilities. We were also interested to see how easy it is to implement a phishing attack on bank users. Walking through these points and conditionally ticking the checkboxes, an attacker can build vectors for further attacks on the bank and its users.
Purpose of the study
Starting this study, we set out to find out how the top 100 banks in Russia ensure their security by applying best practices, as do the most popular sites on the Internet. The main objective of this study is to assess the level of security of publicly available banking resources: the official website, the RBS for individuals and legal entities in accordance with the best practices for setting up web resources. As part of the study, we did not interfere in any way with the work of banks; all data was collected like a normal user visit (several HTTP, SSL, DNS requests). All information analyzed by us is in the public domain, and manipulations with this data do not require serious skills and complex schemes. In other words, we decided to show that, if desired and diligent, any interested user can come to such results.
')
Testing
For testing, we took the TOP-100 banks in Russia, identified by key indicators. A complete list can be found by clicking on the link: http://www.banki.ru/banks/ratings/ (actual data for August 2015).
First, they identified all the official websites and online resources of RBS for individuals and legal entities. Further, for each bank, checks were carried out, carried out by several standard queries (via HTTP / HTTPS / DNS protocols), similar to the usual queries from bank clients. Each check was carried out for the official site, as well as for RBS for businesses and individuals. Initial data:
- Official sites - 100 pcs.
- DB for individuals - 96 pcs.
- RB for legal entities - 81 pcs.
It’s easy to explain that RBS is smaller - not all banks have RBS for individuals and / or legal entities.
In order to compare the obtained results, it was decided to carry out similar manipulations with popular sites presented below:
- wikipedia.org
- facebook.com
- twitter.com
- youtube.com
- linkedin.com
- yahoo.com
- yandex.ru
- amazon.com
- vk.com
The article will contain a description and the results of only some of the checks, the full text of the study can be found at the following link:
http://dsec.ru/ipm-research-center/research/safety_web_resources_of_banks_of_russia/
HTTP headers
The headers in the response of the web server allow you to determine the behavior of the browser in certain situations. In particular, their presence helps to avoid certain attacks or complicate their implementation. At the same time, adding a title does not require any complicated actions or settings. However, some settings (for example, CSP) are distinguished by too many settings, the incorrect use of which can either create an illusion of security, or even damage some functionality of the site.
As an example for testing the following headings were considered:
| Headline | Description |
|---|---|
| X-Frame-Options | Allows or denies displaying a site in a frame (iframe) |
| X-Content-Type-Options | This header will tell IE / Chrome that there is no need to automatically determine the Content-Type, and you must use the already-submitted Content-Type. |
| Content-Security-Policy | Allows you to explicitly specify where a particular content can be loaded from. |
| Strict-Transport-Security | Allows you to prevent the use of HTTP version of the resource for a certain time. |
| Server header | Specifies server software (such as apache, nginx, IIS, or others) |
If the first four headers are “positive” in nature and it is highly desirable to use them, then the last one “tells” the attacker what technologies are used. Naturally, it is better to refrain from such headings.
X-Frame-Options
The X-Frame-Options header allows or denies displaying the page if it is open in a frame.
The header can have three values:
- Rendering a document when opening a frame is possible only from the same domain.
- Rendering a document within a frame is not allowed.
- Enables rendering if an external document is from a specific origin. For example, Twitter allows you to show your site only on your domain.
This header allows you to protect your browser from Clickjacking attacks. Its essence is very simple - in fact, the user on the site clicks on one element of the page, but in reality the click occurs on another.
It is based on the fact that there is an invisible layer on top of the visible page, into which the page needed by the attacker is loaded, while the control element (button, link) necessary to perform the required action is combined with the visible link or button that is expected to be clicked by the user . For example, instead of going to another page, the user puts a “like” or adds some content to favorites.
In the context of RBS, this can lead to the fact that the user will make some kind of “fast” payment, which usually does not require confirmation - for example, payment for the phone.
Consider the results:
- RBS for legal entities - use 33%
- RBS for individuals - use 27%
- Official site - available at 14%
In fact, only a third of the participants in question apply this heading on the pages of RBS domains and even less on the official website. This is not a very good result, since this header, if the site does not actively use frames, does not affect the performance and can be added without problems.
Server header
This header reports on which software the web server runs on and may have the following value (for example):
Server: Apache / 2.4.12 (Unix) mod_wsgi / 3.5 Python / 2.7.5 OpenSSL / 1.0.1l
Disclosing this information does not pose a direct threat, but can shorten the attacker's time during attacks. Instead of checking this or that vulnerability, you can immediately start looking for some data on a particular software version.
- RB for legal entities - 93%
- RBS for individuals - 89%
- Official site - 95%
SSL
One of the most important points is to check the SSL settings, since this cryptographic protocol today is the most popular method of providing secure data exchange over the Internet. Among the main potential threats here it is worth noting the use of attacks to intercept traffic (without replacing the certificate), the disclosure of RAM (Heartbleed attack) and much more.
To make an SSL connection, it is necessary for the server to have an installed digital certificate. With it, it is possible to authenticate the domain and verify who owns the site. This is important so that users visit the resources they need, and not the fake pages of attackers.
An important function is the encryption of the Internet connection, which is necessary to prevent the possible theft of confidential data when it is transmitted on the Web. This option can significantly complicate the task of attackers. Suppose a user has connected to an open WiFi network and decided to pay for purchases or top up an account balance using a mobile bank or web browser. An SSL connection will be established between the client and the BOD and the data will be transferred in an encrypted form. An attacker, even if intercepts this data, will have to decipher it, which will take him many years.
Suppose that in the RB System to which the user is connected, SSL is not used, and all traffic “walks” in the open form. What then can happen? An attacker on the same network will simply “listen” on traffic, and will be able to intercept or replace data (using the active methods of MiTM) to steal users ’money or access their accounts. And if there is a Heartbleed vulnerability on the server, then the attacker will be able to access the data of users that are in the RAM of the server.
The following checks were selected:
| Check | Description |
|---|---|
| Rating | Overall SSL setting rating. It depends on many factors: certificate validity, server settings, algorithms that the server supports, and more. Gradation from 2 to 5 |
| SSL 2.0 support | The protocol has many vulnerabilities and is recommended to disable on the server side |
| SSL 3.0 support | The protocol has many architecture-related vulnerabilities. Although it was introduced as a replacement for SSL 2.0, today it is recommended to disable it. |
| RC4 support | Researchers have discovered the ability to decrypt data that was hidden using the RC4 cipher in a short time |
| Vulnerability to freak | The fact is that an attacker can force the user and the server to use “export” keys for establishing a connection and exchanging data, the length of which is strongly limited. |
| Vulnerability POODLE | Allows you to decrypt user data |
| Heartbleed Vulnerability | Accessing data that is in the memory of a client or server |
Rating
SSL has a large number of settings and features that in one way or another affect the security of both the connection itself and its participants as a whole. Using this information, you can conduct a general assessment of this setting. For this we used the functionality provided by Qualys . It allows you to create an overall rating from A to F (or a more familiar analogue, from 5 to 2 ) based on numerous parameters. Accordingly, 5+ is the best result that can be achieved in terms of security. Very few companies (even the largest Internet corporations) have it. The worst result can be obtained if the server is exposed to any critical vulnerability, supports outdated protocols and has other problems.
What results were obtained:
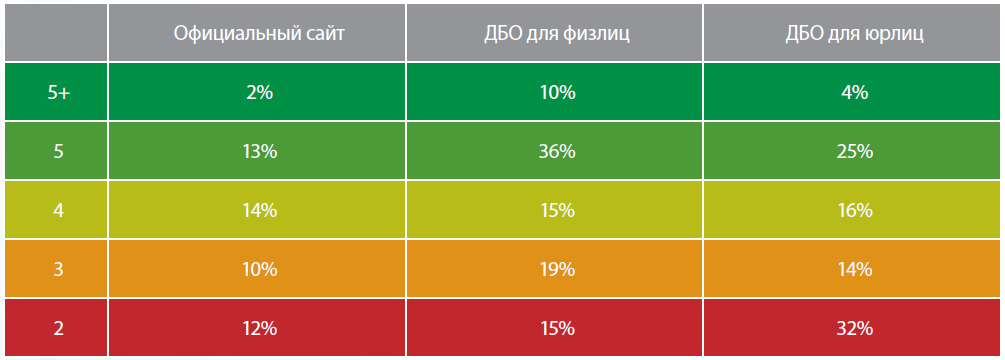
As a comparison, the results for the sites from top alexa were also obtained.

Thus, the average score is 4+ . Grades 4 at the top can be explained by a large number of users (relatively less than banks), some of which are not able to update their devices (for example, Windows XP). Approximately the same is true of RBS systems for individuals. The level of security of official sites and RBS for legal entities in terms of SSL settings is lower than that of popular sites.
Heartbleed
 Heartbleed is one of the most famous vulnerabilities of the last decade. Information about it was published in April 2014, the error has existed since the end of 2011. If we describe it in several sentences, we get the following. This is an error (buffer overflow) in the OpenSSL cryptographic software that allows unauthorized reading of memory on the server or on the client, including, for extracting the server's private key. The server does not check the validity of some requests from clients. Having established the connection, the client periodically requests the server with a request to confirm that the connection has not yet been terminated. In response, the server must return some small amount of data, and the number is determined by the client itself. So, if the client requests more data than he sent, his request will still be executed and the server will send him a piece of RAM. The size is limited to 64 KB, but you can send a lot of requests. Thus, the quantity turns into quality - sending hundreds, thousands of requests, you can read large blocks of data. Thus, complex methods for the operation of this error is not required. If a remote banking system server is vulnerable to Heartbleed, an attacker can gain access to critical data in minutes. Let's see how many participants provide this opportunity.
Heartbleed is one of the most famous vulnerabilities of the last decade. Information about it was published in April 2014, the error has existed since the end of 2011. If we describe it in several sentences, we get the following. This is an error (buffer overflow) in the OpenSSL cryptographic software that allows unauthorized reading of memory on the server or on the client, including, for extracting the server's private key. The server does not check the validity of some requests from clients. Having established the connection, the client periodically requests the server with a request to confirm that the connection has not yet been terminated. In response, the server must return some small amount of data, and the number is determined by the client itself. So, if the client requests more data than he sent, his request will still be executed and the server will send him a piece of RAM. The size is limited to 64 KB, but you can send a lot of requests. Thus, the quantity turns into quality - sending hundreds, thousands of requests, you can read large blocks of data. Thus, complex methods for the operation of this error is not required. If a remote banking system server is vulnerable to Heartbleed, an attacker can gain access to critical data in minutes. Let's see how many participants provide this opportunity.Since working exploits and examples of accessing data were demonstrated for this vulnerability (even a competition was organized!), The problems that it may entail are clear to everyone. Nevertheless, the official sites of two banks from those who have been tested, contain this error.
- RBS for legal entities - use 0%
- RBS for individuals - apply 0%
- Official site - available from 2%
Using this vulnerability, you can also get a private certificate that is actually used in MitM attacks. And if the same certificate is used for the official site and for the remote banking service (or simply Wildcard), then this will allow to conduct an attack even on a secure HTTPS connection.
Domain Check
In order for an attacker to gain access to confidential information or in an ICC, it is not necessary to try to bypass technical perimeter protection, look for “firewall gaps”, etc. One of the most effective ways is sending out letters to employees / customers with a proposal to open a resume or test a new bank service, for example. Of course, the success of such an enterprise depends on the history, content of texts and further actions on the part of the victims, but in a simplified form, the implementation of this scenario is as follows: the attacker selects a list of employees, sends them letters with official links, “correct” domain names. Next, the victims follow the link allegedly to the standard pages of the bank site (in fact, they have been replaced). For a successful attack, you need to register a domain name that would be most like the name of the bank, for example.
After the user gets on the fake page, scammers try to encourage him to enter the username and password that he uses to access a specific site. If this happens, attackers gain access to the victim’s accounts and bank accounts.
Phishing is one of the varieties of social engineering, based on the user's ignorance of the basics of network security: in particular, many are not aware that official services do not send letters asking them to provide their credentials, password, and so on.
As an example, take the fictitious name of the bank (rusomebank, RusSamBank), which will have a site - rusomebank.ru. This is how it will look in the browser.
Attackers can fake domain names by creating similar ones like this:
- In the domain of the Russian Federation, for example, instead of somebank.ru - sambank.rf.
- Use domain zones org, com and net.
- To use homoglyphs - graphically identical or similar to each other characters that have different meanings. For example, the Latin letter l may be replaced by the number 1.
- Using double characters.
- Take a subdomain with a similar name. If the RBS is located on a subdomain, it is possible to register a domain in which the dot (between the subdomain and the domain) will be replaced with a dash.
As a test of subdomains, we can recommend dnstwist , which, in addition to checking the availability of domains, also compares the similarity of sites to determine whether the site is phishing or not.
Omoglyphs
Omoglyphs are graphically identical or similar to each other characters that have different meanings. Capital letter O and the number 0 can be easily confused. Omoglyphs can appear when using different alphabets. During the test, the following table was used:
| l | one |
| o | 0 |
| i | j |
| m | rn |
| q | g |
| d | b |
Using this data, for the domain name rusomebank.ru we can get the following results:
- rus0mebank.ru
- rusornbank.ru
- rusomedank.ru
The address bar that contains the homoglyph will look like this:

During the test, only one symbol was replaced, that is, variations like rus0rnedank.ru were not tested. The results of how many bank domains have a resource that contains an omoglyph and which can be registered:
- Official website: 71%
- DB for individuals: 67%
- RBS for legal entities: 68%
And only 14% of banks do not allow registering a domain with Omoglyph. This is not a good indicator, since for the most part their domain names are not very long.
DNS zone transfer
AXFR is a DNS transaction type that allows the replication of DNS databases between servers. In fact, this is the same query as any other request, for example, in order to find out the IP address of the site. Can be performed anonymously.
But you can often find an error in setting up DNS servers when an answer comes to this request without any restrictions. This allows you to open the entire zone (all records) of the domain, including private data. These may be domains for internal use, for example, as a task tracker, internal portals or an ABS address. Why might it even be necessary? Often, the main sites of companies are very well protected and finding a serious vulnerability is not a trivial task. However, as the saying goes "The chain is as strong as its weakest link." On some subdomains, you can sometimes find test versions of sites, backups, and more. Some rather large companies were hacked in a similar way, due to the fact that testing scripts remained on some subdomain.
In this test, it is important to check all DNS servers that serve the domain, and not just the one that was set first. There are cases when the domain maintains its own DNS server and the server of the partner company that is configured with an error.
Result: for 17 banks, you can open the entire domain zone and access all records.
findings
Unfortunately, the results of the study showed that the use of obvious techniques (which are not so costly in terms of both financial and technical resources) to increase the level of security is not very popular among the study participants.
For example, only 5 participants do not allow registering a domain using omoglyphs, permutations, repetitions and changing the domain zone, which indicates a wide range of opportunities for phishing companies to be targeted to attackers. In fairness it should be noted that the domain names of these participants are short, which, in fact, does not give variability in checks. You will not be able to register a domain in the zone. Com / .net / .org /. RF for a total of 25 participants. If a participant has an RBS on a subdomain, then you can register a domain as a subdomain for all participants.
It was unexpected that for 17 participants, you can send an AXFR request to the DNS server from the outside and open all records for the bank's domain, through which you can most often determine the infrastructure, internal resources, addresses of significant servers (for example, ABS).
It was also found that two banks on the official website of the web server are vulnerable to the Heartbleed attack. If a wildcard certificate is used for the official website and for the RBS system (or just the same one issued for these domains), this will allow the attacker to steal a private SSL key and, during the man-in-the-middle attack, allow you to listen and change the traffic data transactions in the RBS, and as a result, lead to the theft of money from customer accounts.
Now, by the results, we hope that the security departments of banks will check their resources and will be even more responsible in their protection. Particularly interesting obtained statistics of this study may look at the background of the growing popularity and improvement of various protective mechanisms that allow you to protect the user of the system even with the vulnerability allowed by the developer.
The full text of the study can be found at the following link:
http://dsec.ru/ipm-research-center/research/safety_web_resources_of_banks_of_russia/
Source: https://habr.com/ru/post/274273/
All Articles