GlassRAT: Trojan analysis from China using RSA Security Analytics and RSA ECAT

RSA Research specialists discovered a GlassRAT Trojan program for Remote Administration (RAT) with a “zero detection level”, signed with a certificate that was stolen or received from a popular Chinese software developer. This malware could have avoided detection for several years. Telemetry and limited reports that do not withstand any criticism indicate that the purpose of GlassRAT were Chinese citizens associated with transnational corporations. Being completely “transparent” to most anti-virus products, the GlassRAT Trojan can be detected using detailed examination, as well as using the final threat detection tools, such as RSA Security Analytics and / or RSA ECAT. It also presents evidence that the method of organizing the team infrastructure of the GlassRAT network has much in common with other malicious campaigns that were previously aimed at Asian organizations of geopolitical and strategic importance. More information about this information can be found here: http://blogs.rsa.com/peering-into-glassrat/ .
What is actually GlassRAT?
GlassRAT is a remote access trojan (RAT). Apparently, he remained unnoticed for almost 3 years. GlassRAT uses many features and boasts in its own way a very effective, malicious design. His dropper was signed with the help of a compromised certificate from a trusted and well-known publisher (the Certification Center, which issued this certificate, after an independent examination confirming the malicious intent of the code signed by it, subsequently revoked it). Dropper removes himself after successfully completing his tasks. Once installed, the malicious .dll file, so to say, “flies below the radar detection level” of the antivirus, provides an attacker with access to the shell-code of the infected victim.
GlassRat first caught the attention of RSA Research in February 2015, when the RSA Incident Respons team, specializing in proactively preventing threats of intrusion into large corporate networks, detected malicious traffic while investigating an incident in a multinational corporation based in the United States. The sample DLL was detected using RSA ECAT on a Chinese citizen's PC residing in mainland China.
')
Usually, the organizers of the attack simply replace such low-level tools as the RAT, immediately after detection, without changing tactics, procedures, infrastructure, or even the attack targets themselves. However, in this case, the facts suggest otherwise. The objectives of the attack differed both in quantity (there were much more) and in characteristics (geopolitical, instead of traditional commercial ones).
RSA Research looked for possible similarities with other malicious programs and methods described earlier. Some similarity of the code with other malicious programs, such as Taidoor, was found ( http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/papers/wp_the_taidoor_campaign.pdf )
and Taleret ( https://www.fireeye.com/blog/threat-research/2013/09/evasive-tactics-taidoor-3.html ), but the most interesting coincidence was found in the infrastructure management system used in attacks on the organization of geopolitical values (about this below), which were recorded several years ago.
GlassRAT Analysis with RSA Security Analytics and RSA ECAT
GlassRAT Infection Scheme
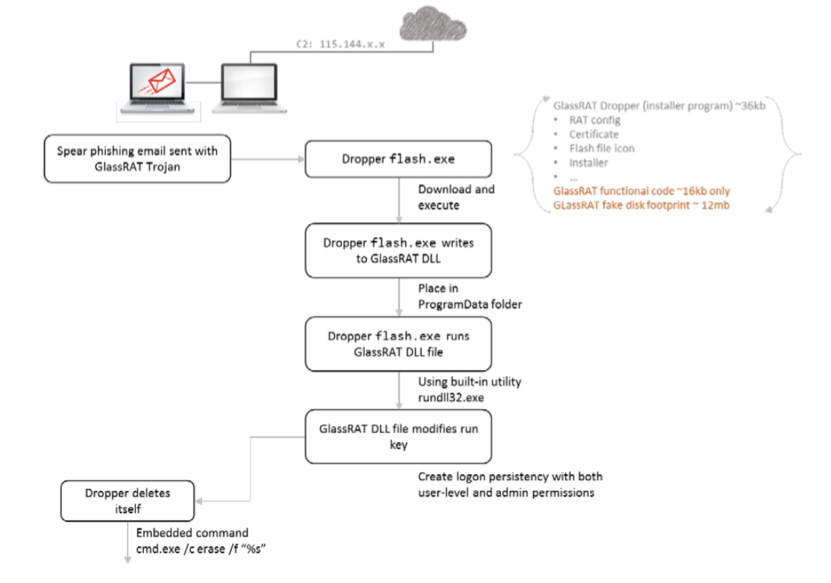
By starting an investigation of the attack after dropping and infecting, ECAT automatically increases the danger level for the machine and the corresponding module from zero to one of the maximum values in the analysis queue.

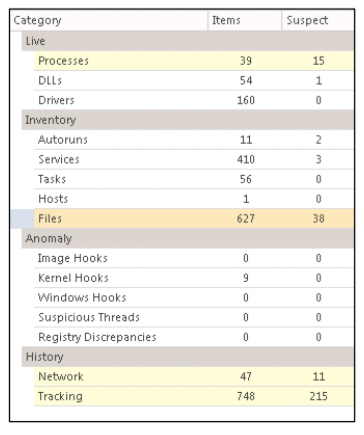
Let's analyze the rest of the ECAT information. We have access to statistics about current memory contents, data stored on the disk, anomalies, and network traffic. All this allows the analyst to instantly turn his attention to any of the suspicious entities during the investigation of the incident.
Dropper GlassRAT
There were two samples of the GlassRAT malware installer, known as “droppers”. According to the results of the analysis presented on the VirusTotal website, 57 different antiviruses were not able to detect both of these droppers during normal testing.
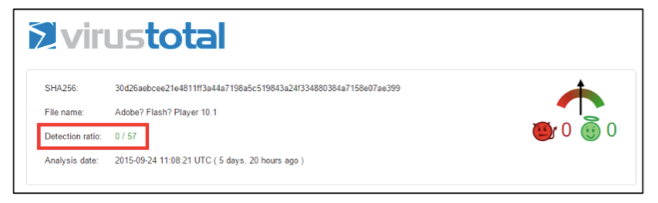
Both samples of the GlassRAT dropper were almost identical in their functions and code . The first sample was uploaded to VirusTotal about four hours before the second.
GlassR droppers used the proprietary Adobe Flash Player icon and were called “flash.exe” when they were first downloaded to VirusTotal on September 17, 2015.
Double clicking on the Trojan causes the launch of the dropper. Once ECAT found it to be a potentially malicious file, it was automatically uploaded to ECAT ConsoleServer for further investigation. Through ECAT Modules view, we see the following:
ECAT detects a dropper and increases the danger level of InstantIOC (Indicator of Compromise Score), given the code signature with a revoked certificate.
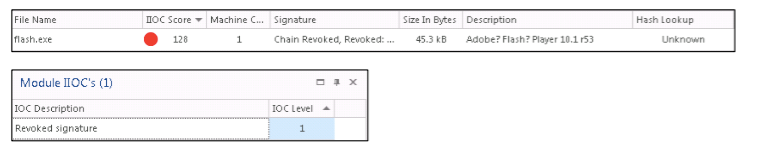
In addition, ECAT uses the session tracking module to identify and establish links to other potentially suspicious files or machines in your environment that have established connections and performed other suspicious actions:
SVCHOST.exelaunchesflash.exeflash.exelaunches the “Write to Exectuable” event for updatef.dll
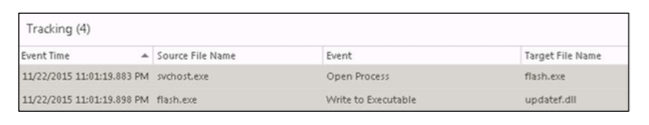
During the installation of the Trojan, the dropper self-destructs using the built-in command:
“cmd.exe /c erase /F "%s",”After detecting a new malicious
updatef.dll file, we began to analyze it. As can be seen from the list of files sorted by ECAT Risk Score, the dropper has two different processes used when installing in user and privileged modes: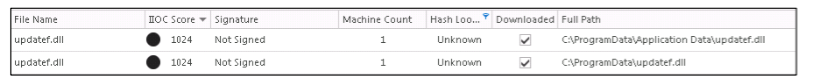
These two different DLL files were immediately marked as suspicious and uploaded to the server after being detected by the ECAT agent, and received a risk rating of 1024 points each.
The mechanism of unprivileged persistence GlassRAT
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Image path: c:\programdata\updatef.dllNote: the DLL file is actually written to the root of
C:\ProgramData , but due to the C:\ProgramData to Windows Vista and later versions of Windows, the path C:\ProgramData\Application Data\ will be displayed in the Autoruns registry key.This is how the GlassRAT unprivileged persistence looks when viewed through the Autoruns tool:
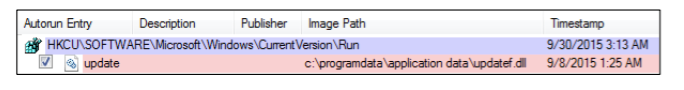
When you manually start UAC, by clicking the right mouse button, the metadata associated with the dropper is displayed:
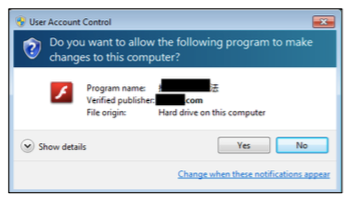
Note: The program name specified in the User Account Control (UAC) dialog box is the same as the name of this application “500 million-user” developed by the certificate holder.
GlassRAT Preferred Persistence Mechanism
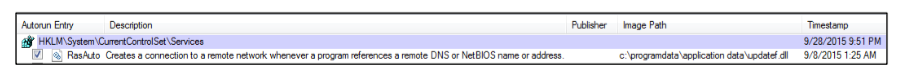
The persistence of the GlassRAT Trojan is ensured by the installation of “Remote Access Manager” as a service, which is usually disabled by default in Windows.
HKLM\System\CurrentControlSet\Services
RasAuto image path: c:\programdata\application data\updatef.dllThe GlassRAT persistence mechanism when installed with administrator privileges:
Using ECAT module investigation, you can instantly determine
updatef.dll as an autoloader, assign the appropriate level of risk, and detect the file and registry entry: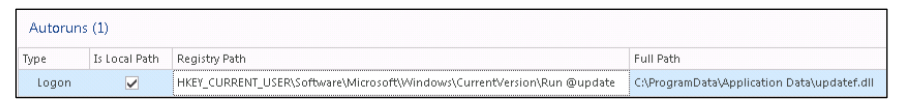
updatef.dll malicious file in updatef.dll , we decided to study its characteristics better: what it is, what it does, what its distinctive features, etc. To do this, use the module InstantIOC (IIOCs).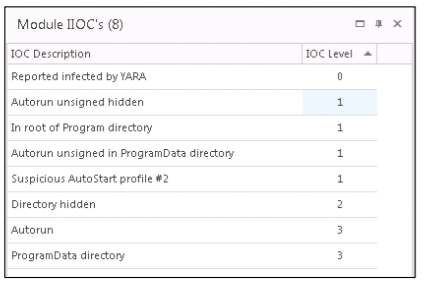
YARA is a tool to help researchers identify and classify malicious samples. The YARA IIOC infection message was initiated by a separate YARA rule created for GlassRAT, which is indicated under the module properties.
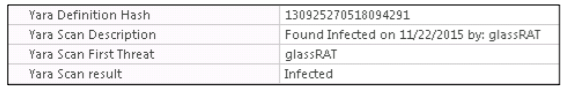
After the dropper and the associated DLL files were identified and executed, we assumed that the Trojan was loaded using
svchost.exe as a RasAuto service, and when installed in the unprivileged mode, rundll32.exe runs updatef.dll .Through monitoring ECAT network traffic, we identified suspicious connections to qx.rausers.com through ports 53, 80, and 443. In this case, ECAT was able to determine that it was a
rundll32.exe module that was alerting (and not just establishing communication with svchost.exe ).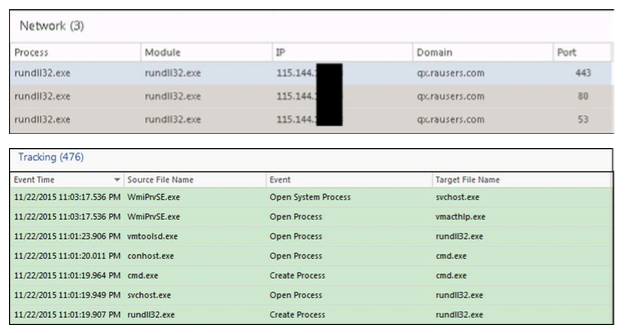
In addition, ECAT IIOC flagged
rundll32.exe , reporting potential signaling, suspicious network access, and actual DNS traffic from this process.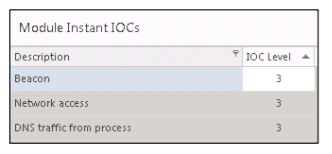
Network Analysis of the GlassRAT Command Center with ECAT Security Analytics
The management structures of GlassRAT were somewhat similar to the command centers that were discovered in 2012 in other malicious campaigns aimed at governments and military organizations in the Pacific. In addition, a static analysis of several GlassRAT DLL files revealed that the command center host configuration was confusing in all detected patterns.
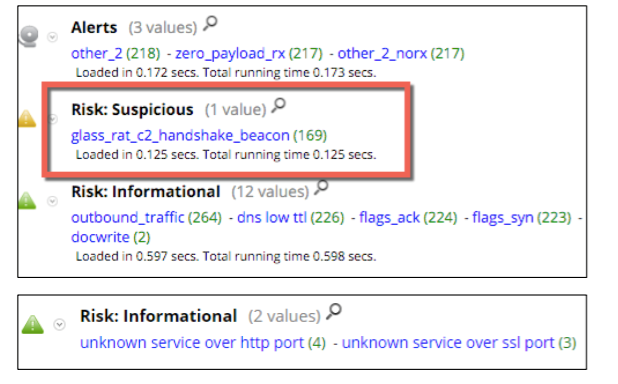
003/064/50/60 : 112.175.xxchur/gnsxntrdd/odu : bits.foryousee.net012/31/084/353 : 103.20.xxpy/s`trdsr/bnl : qx.rausers.comly/s`trdsr/bnl : mx.rausers.comyy/s`trdsr/bnl : xx.rausers.comA handshake between the attacker and the victim was discovered using Security Analytics and the new separate Glass RAT Trojan parser parser, available out of the box via RSA Live. When network traffic was
glass_rat_c2_handshale_beacon , a new meta-value “Risk: Suspicious” was assigned to the glass_rat_c2_handshale_beacon parameter.Connections to the direct access socket, marked as “
unknown service over http port ” and “ unknown service over ssl port ” with the meta value “Risk: Informational” with meta value, also testify to the handshake.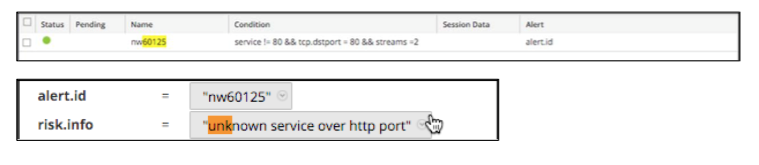
RSA Security Analytics sent a hard-coded value of
0x cb ff 5d c9 ad 3f 5b a1 54 13 fe fb 05 c6 22 during the execution of the handshake between the infected node and the command server. Definition of traffic and destination IP addresses (dst.ip):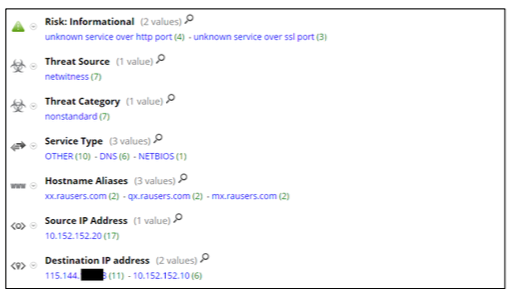
When interacting with the Windows command shell (but not in signaling), you can also use the following application rule:
service = 0 && tcp.dstport = 80 && risk.warning = 'windows command shell'You can detect malicious activity thanks to console messages (risk.warning: 'windows command shell' using an unknown protocol (service = 0) and a popular port (tcp.dstport = 80)). But here false positives are possible.
Source: https://habr.com/ru/post/274245/
All Articles