Security Week 52-53: Juniper backdoor with a thick layer of cryptography, vintage Java, gopo-bug bounty
 At that moment, when the tree is already standing, but the salads have not yet been cut, it's time for the last time this year to talk about security news. Last week, I reported on the “non-standard” best news of the year, and in general, nothing much happened during the remaining time. Although no, there is one news that is worthy of a separate story. The two backdoors found on December 17th in the Juniper network device software could fill up a long but unreleased list of bugs, exploits, and incorrect configurations in routers and home routers. But later it turned out that there are a lot of nuances in this story, it affects not only the topic of secure coding, but also encryption, and even hints of the involvement of special services.
At that moment, when the tree is already standing, but the salads have not yet been cut, it's time for the last time this year to talk about security news. Last week, I reported on the “non-standard” best news of the year, and in general, nothing much happened during the remaining time. Although no, there is one news that is worthy of a separate story. The two backdoors found on December 17th in the Juniper network device software could fill up a long but unreleased list of bugs, exploits, and incorrect configurations in routers and home routers. But later it turned out that there are a lot of nuances in this story, it affects not only the topic of secure coding, but also encryption, and even hints of the involvement of special services.In general, the interesting was the end of the year. In addition to Juniper, two more popular news more go to the topic of near-security policy. Traditional rules: Every week, the editors of the news site Threatpost selects the three most significant news, to which I add an extended and merciless comment. All episodes of the series can be found by tag . The first episode of the new year will be released on the screens of the country on January 8!
Two backdoors were discovered in Juniper devices: non-trivial and completely non-trivial
News Shocking details . The newly discovered circumstances . An article in the Knowledge Base Juniper.
On December 17, a message appears on Juniper's website about the successful closure of two serious vulnerabilities in the ScreenOS operating system - a proprietary OS that runs the network firewalls of the enterprise class Netscreen . These are such high-performance hardware that provides traffic filtering, VPN, protection from DDoS on channels with a capacity of 10 gigabits per second and higher. Both vulnerabilities are very dangerous, but each individually threatens the security of transmitted data in its own way. Therefore, they can be divided into "simply non-trivial" and "completely non-trivial."
')
Just a nontrivial vulnerability.
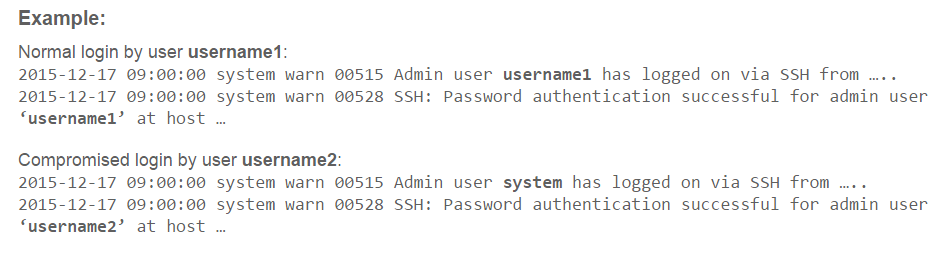
Healthy person log and smoker log
Find ten differences. The only difference between a normal login and an unauthorized username is that in the second case, an entry appears on the login on behalf of the user system. Not the best indicator of hacking, especially as the Juniper correctly notes, the attacker will rub these two lines first. That is, we are talking about a tab in the code that allows you to log in to a user that the device administrator did not create - this is a fairly typical situation. In fact, everything is somewhat more complicated, or easier - this is how to look. Actually, there were no details in the Juniper message: “we found two holes, here are the patches, thank you”. Given the risk of vulnerabilities, they cannot be blamed for trying to hide some information. The problem is that comparing the code of the two versions “before and after the patch” and finding out exactly how the backdoor works is not a particular problem.
This analysis was done by many, including the company Rapid7. It turned out that we are not talking about a secret pair “user-password-password”, but only about a password, and it is coded so that when viewing the source code, it looks either as a comment, or as a debugging code. In general, if a vulnerable network screen is visible “outside”, then connecting to it with full access rights is easy. The data from the specialized search engine Shodan are cited: at the time of the publication of the study, he saw 26,000 NetScreen devices (but not necessarily vulnerable) to which you can connect via SSH from the outside. The backdoor is available presumably from 2013 - it was then that the version in which this tab appeared appeared.
Totally nontrivial vulnerability
The second vulnerability is present in ScreenOS a little longer - since 2012, and it allows you to decrypt VPN traffic. What this means for companies using NetScreen complexes for secure communication between units across open networks, I think it is not necessary to explain. As rightly noted in the initial communication of the company, it is not possible to determine whether this vulnerability was exploited. How did it happen? To understand, it is necessary to plunge into a jungle of questions of enciphering again. A normal person in these wilds looks like this:

But I still try, relying on the post of Matthew Green, the famous cryptographer. The article begins positively: “we will not go into much detail”. Yeah, we will not. The bottom line is that ScreenOS uses the Dual_EC_DRBG pseudo-random generation algorithm. The fact that this algorithm is unreliable with a certain implementation, I wrote earlier in the story about the communique (ui!) NSA regarding encryption algorithms that are resistant to quantum computing. I will quote:
“There is a backdoor in it or not, it is not fully known, but in the early 2000s the NSA actively campaigned for the standardization of the algorithm, in 2007 there were suspicions of a backdoor, and in 2013 Snowden’s leaks confirmed that some program the introduction of bookmarks, or by propaganda of deliberately weakened algorithms, existed. Whether this applied to a specific code is not clear, but the sediment remained. ”
In response to many years already expressed doubts about the robustness of the algorithm, Juniper once issued a statement : even so, ScreenOS is not affected, because it uses its own implementation of the algorithm, in which the Dual_EC_DRBG output is transmitted for further processing to another algorithm - FIPS / ANSI X.9.31 PRNG. According to Matthew Green, such a pipeline really removes all questions about vulnerability, but with one condition: if the attacker does not have access to the original sequence of numbers generated using Dual_EC_DRBG. And the whole sequence is not required - just the first 30 bytes or so. So, the information obtained through the analysis and reverse engineering of patches indicates that this is exactly the (raw output of the first 32 bytes of the algorithm)! Having received 32 bytes of output, it becomes possible to predict what will happen next with this data, and finally to get the key to encrypted traffic.
Matthew Green does not draw conclusions about the “customer” of backdoors, but once again raises the topic of the danger of intentionally weakening cryptography. The one who leaves (introduces without the vendor’s knowledge, or with his help, it doesn’t matter) a loophole only for himself cannot guarantee that others cannot use it. I will add that in the documents received from Edward Snowden, the Dual_EC_DRBG algorithm, and specifically the Juniper devices with some kind of backdoor, are mentioned more than once.
So it goes.
Oracle agreed with the US Trade Commission that Java’s security is so-so
News
Oracle has entered into a settlement agreement with the US Federal Trade Commission on the Java platform security dispute. It would seem, where is Java, and where is FTC, and why does the local Ministry of Trade worry about software vulnerabilities? Although yes, there is something to worry about, this is the traditional selection of news for the year: one , two , three , and so on. Java regularly competes with Adobe Flash for the title of the software itself being exploited by hackers, and recently Flash wins (that is, loses) - it is most often attacked. According to our statistics , in 2015, Java vulnerabilities were used in 13% of attacks using exploits, although a year earlier there were 45%. Virtually all Java exploit packs are no longer used at all. In general, everything seems to be not so bad?
Well, the news is not about it :) The FTC is still a state structure, and it is ... not quickly responding to the rapidly changing landscape of threats. The trial dealt with older versions of Java, and Oracle statements: well, when the company calls on users to be updated in order to protect themselves. At least until August 2014, the Java update worked in such a way that it didn’t completely “secure” users: in some cases, old versions of Java remained somewhere in the system’s depths and could still be attacked. The problem was solved only by completely removing the old version before installing the new one. Many people know how “convenient” and “transparent” updates have been implemented until recently. In general, we agreed that the company will notify users "more better."

An important nuance of the news is the sending of some internal Oracle correspondence, analyzed during the investigation. From it became known that the problems with the updates were not a secret for the employees, but the company could not do something useful for them for a long time. In this connection, I cannot help reminding about the August PR failure of Oracle, when CSO recommended them to independent researchers and customers to keep their disassembler with them - they say that the vendor will cope with security audit.
Facebook accuses researcher of immoral bag-hunting
News Researcher's blog.
Nothing foreshadowed trouble when security expert Wesley Weinberg posted to Facebook information about vulnerabilities in the Instagram server infrastructure. They responded to his message, thanked him and said that he was qualified to receive $ 2500 under the bug bounty program. Further events evolved outside the box: Weinberg continued research, managed to break almost the entire Instagram - in the sense of getting to the servers with the source code and user data - and Facebook accused him of unethical behavior.
The testimony of the participants contradict each other. According to Weinberg, he dug up a whole series of vulnerabilities, thanks to which he was able to get access to Instagram virtual servers in Amazon S3. According to Alex Stamos, CSO Facebook, the entry point was one, thanks to Weinberg for the report, but it was unethical to go on: it’s impossible to break down servers and steal employee and user data, and call it security. Outraged Stamos called Weinberg's employer, Synack, and thus added new players and dramas to the story. Weinberg himself in response hinted that Facebook was trying to delay the publication of information about vulnerabilities, which is the sacred right of the researcher.
In general, it is difficult to make out who is right in this story and who is not. It is only clear that there were no specific rules for interaction between researchers and vendors, let alone such non-algorithmic tasks as ethical code. And it would be nice to come up with these rules. First, it will benefit the industry as a whole - after all, Instagram eventually closed the hole before the attackers could take advantage of it. Secondly, it is better for the industry to come up with these rules on its own, while professional lawmakers have not taken it up for them - in this situation, you understand, anything can happen.
 Antiquities:
Antiquities:"Stone-a, -b, -c, -d"
When booting from an infected floppy disk with a probability of 1/8, the message “Your PC is now Stoned!” Appears on the screen. In addition to this, contain the string "LEGALISE MARIJUANA!". The Stone-c virus destroys the partition table (Disk Partition Table) when infecting the MBR of the hard drive, after which the computer can only be booted from a floppy disk. "Stone-d" October 1 destroys information on the hard drive.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 97.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/274211/
All Articles